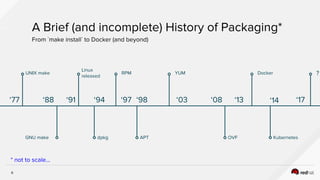
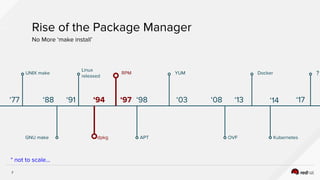
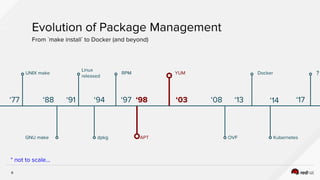
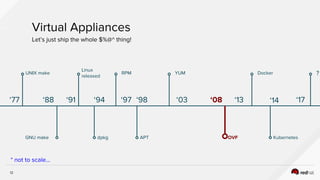
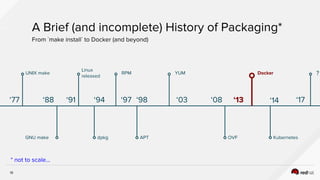
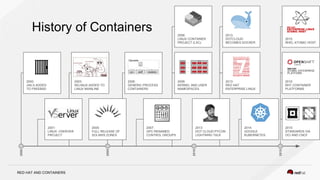
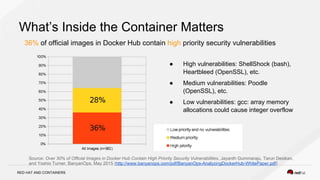
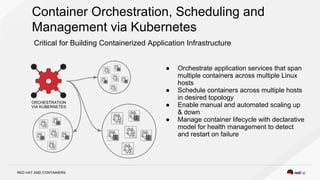
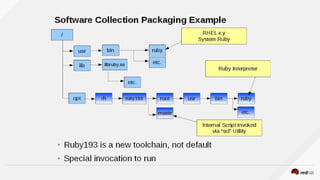
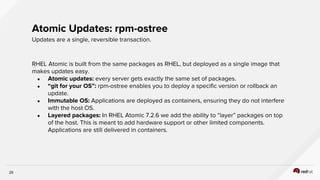
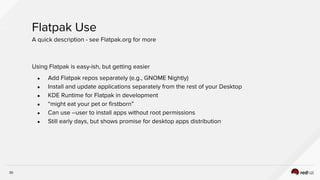
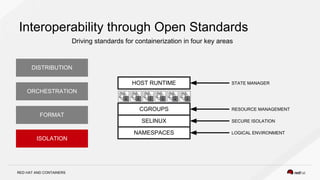
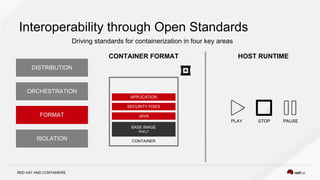
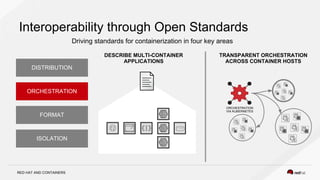
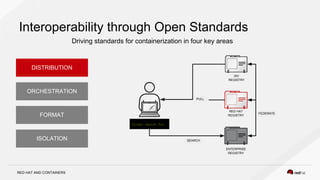
The document discusses the evolution of software packaging, highlighting challenges and solutions, including the rise of containers for application deployment. It examines the historical context of packaging practices, issues with virtual appliances, and how containers like Docker and orchestration tools like Kubernetes have transformed the process. The importance of security, interoperability, and learning from past experiences is emphasized as organizations navigate the evolving landscape of application management.