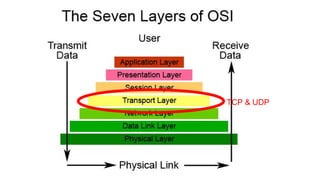
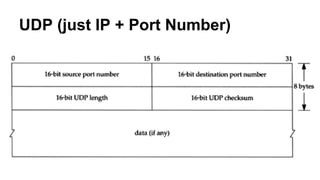
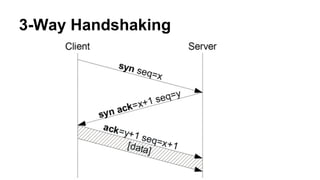
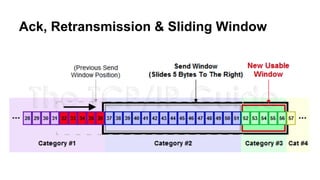
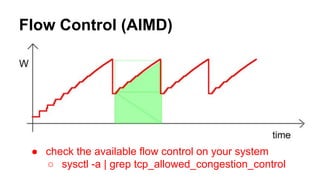
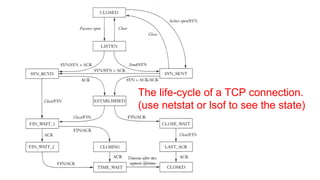
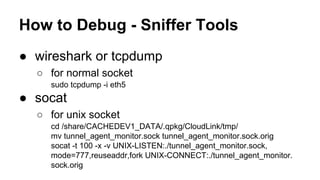
This document discusses various topics related to network programming including TCP and UDP protocols, TCP connection lifecycle states, TCP options, debugging tools like Wireshark, and methods for disconnecting connections. It provides an overview of reliable and ordered data delivery with TCP, the three-way handshake process, flow control, and TCP states like ESTABLISHED and CLOSE_WAIT. Debugging techniques like packet sniffing, ARP spoofing, and SSL interception are also covered.