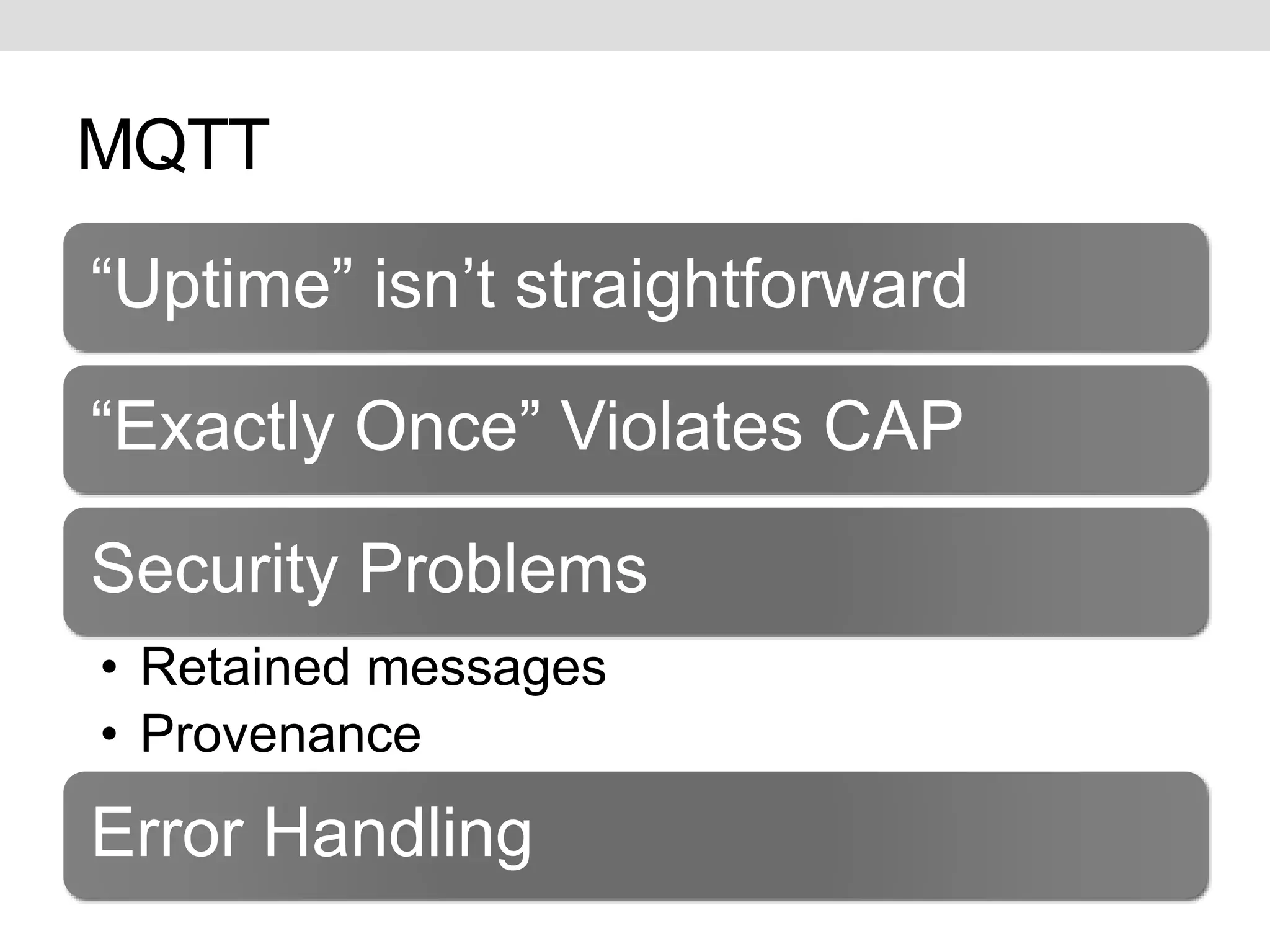
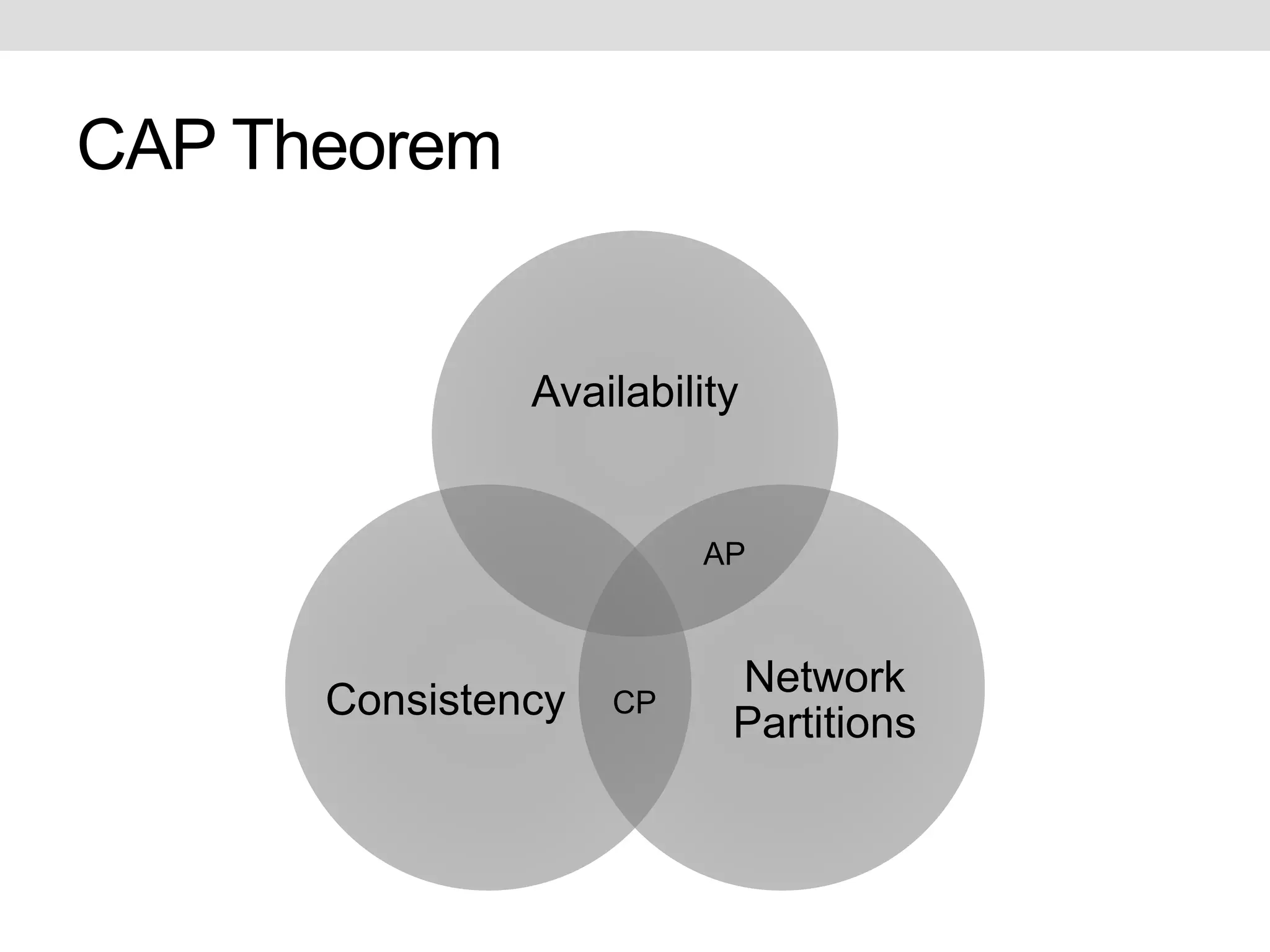
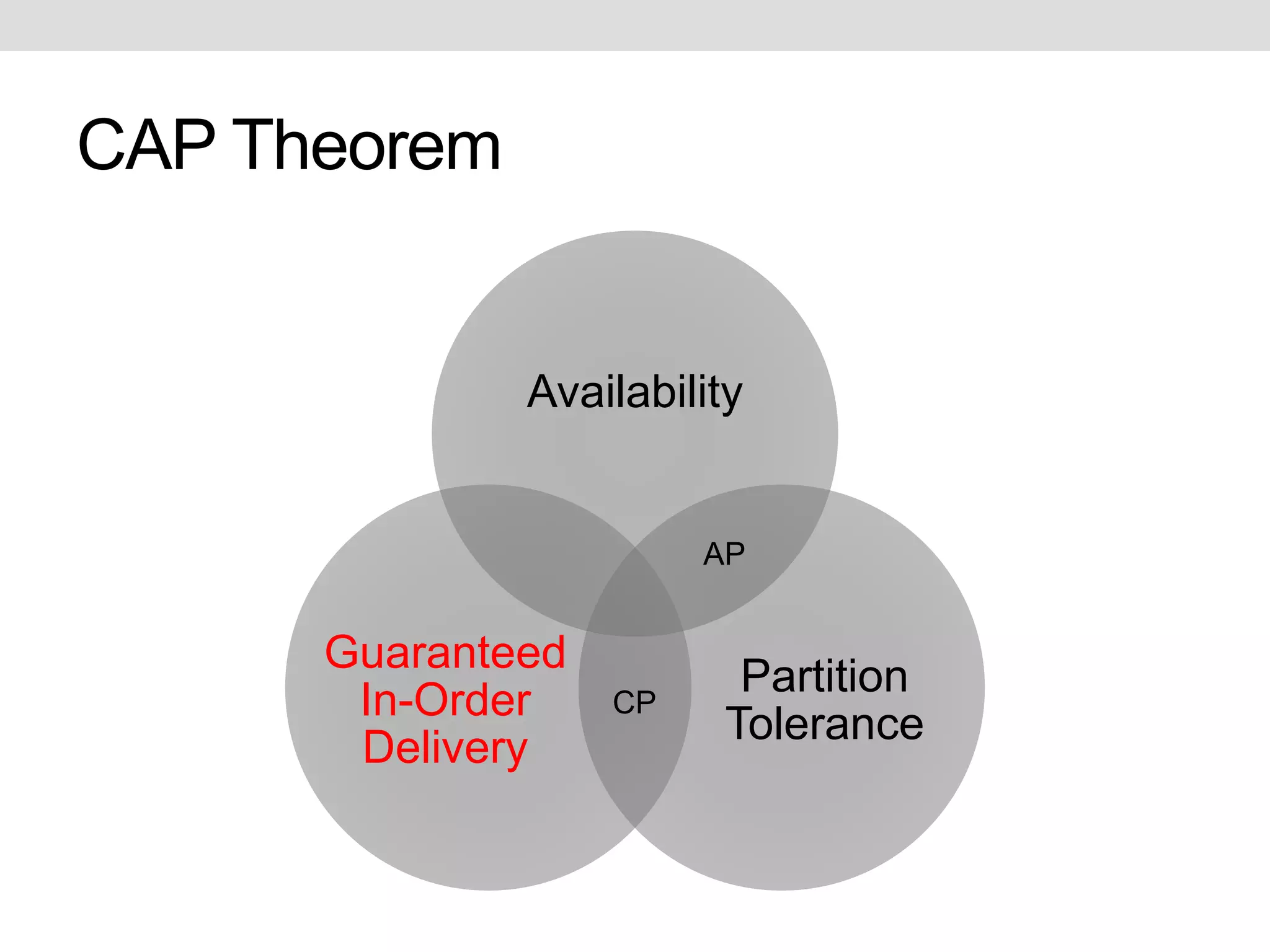
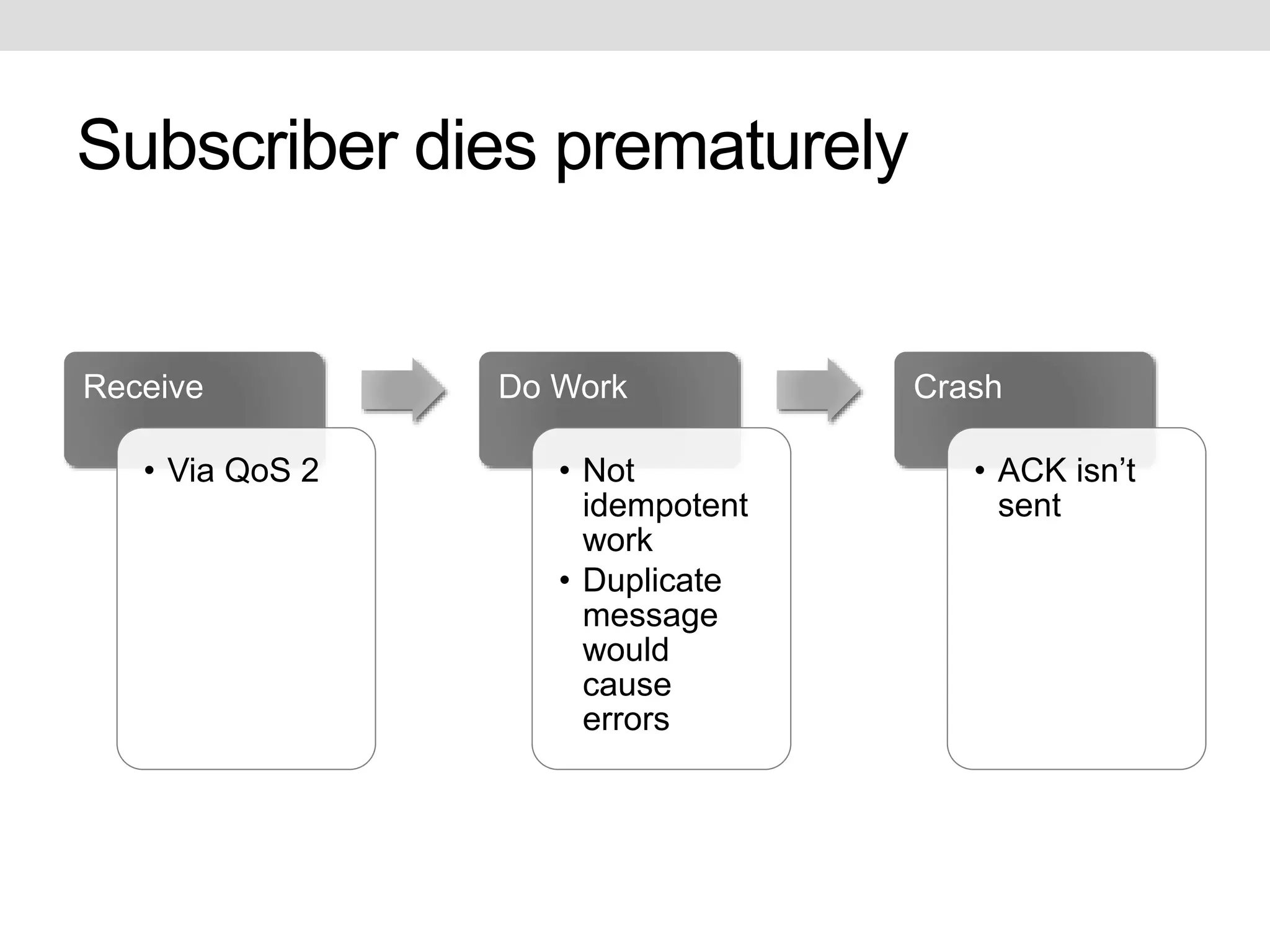
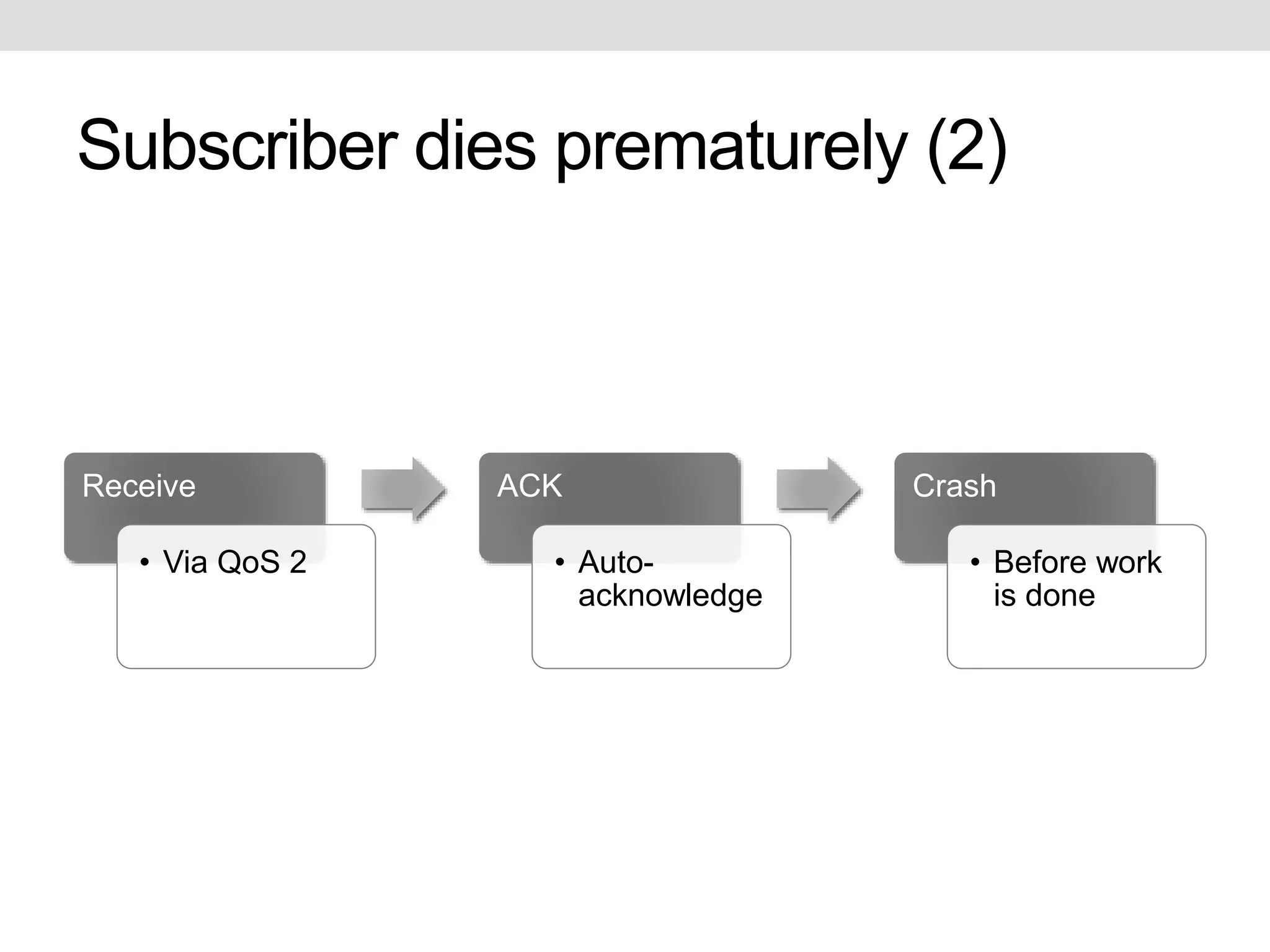
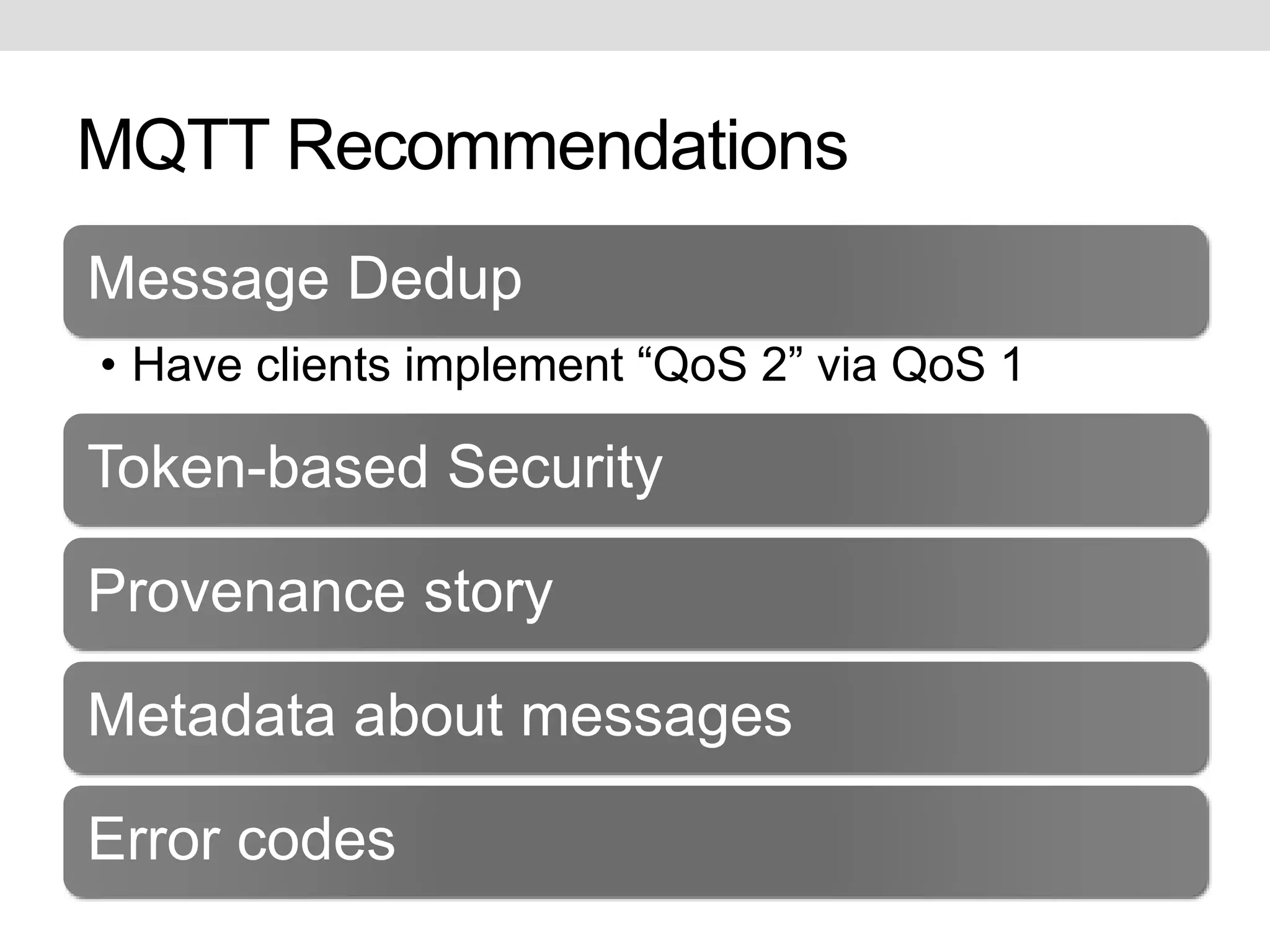
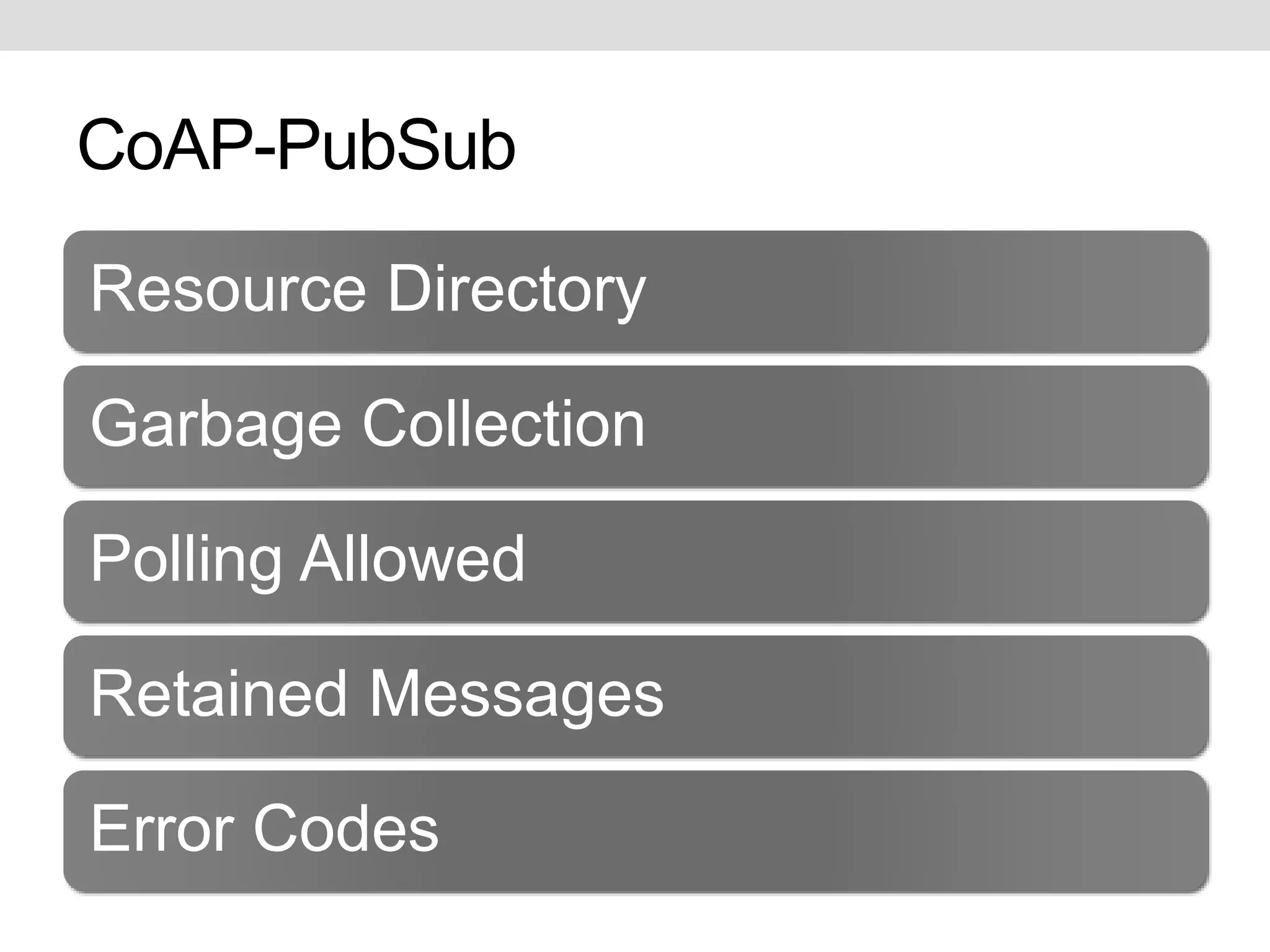
This document discusses potential improvements that could be made to the MQTT 3.1.1 protocol. It addresses issues with ensuring "exactly once" delivery, security problems with retained messages and lack of provenance, and error handling. The document recommends that clients implement "QoS 2" functionality using QoS 1 to avoid duplicate messages, adding token-based security and metadata about messages. It also compares MQTT to the CoAP-PubSub protocol.