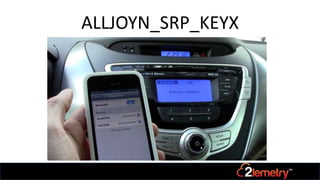
The document discusses the security implications of various incidents related to embedded systems, emphasizing the ease of hacking due to unpatched software. It outlines different encryption algorithms and security methods used in AllJoyn, a framework for building IoT applications, including asymmetric and symmetric key encryption techniques. The content highlights the importance of secure connections and the need for regular software updates in embedded systems to prevent vulnerabilities.