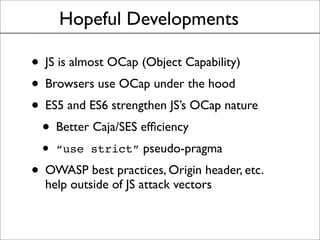
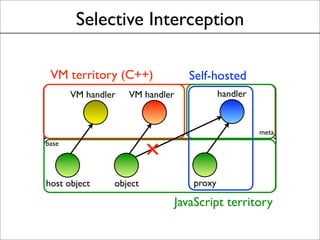
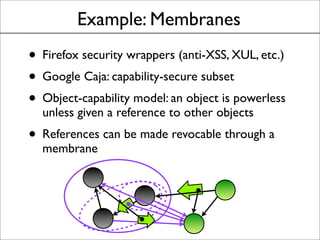
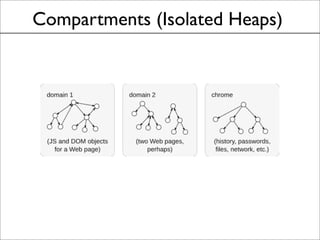
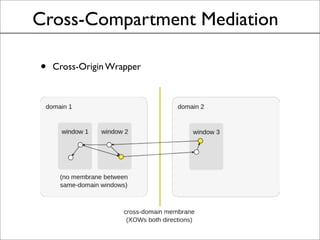
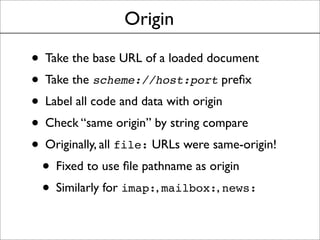
This document discusses the history and evolution of the same-origin policy in web browsers. It describes how the same-origin policy was originally implemented in Netscape 2 in the 1990s to label code and data with their origin and restrict cross-origin interactions. Over time, browsers added features like document.domain to relax the policy and allow some cross-origin communication while preventing security issues. Modern browsers now use techniques like object capabilities, isolated compartments, and cross-compartment mediation to further strengthen isolation while still supporting cross-origin interactions on the web. The document raises the question of whether a cooperative approach could be taken to label and mediate cross-site script inclusions in a more nuanced way.





![mozilla
No browser wins by taking overlarge risks
• Previous slide from Collin Jackson’s USENIX Security 2011 invited talk, titled
“Crossing the Chasm: Pitching Security Research to Mainstream Browser
Vendors” [slides]
• Features are not free
• Mozilla commissioned optional CPython integration work by Mark Hammond
• Used by only one embedder
• No CPython distribution for Windows or Mac OS X
• High sunk and recurring engineering costs
9](https://image.slidesharecdn.com/sos-140714163817-phpapp02/85/The-Same-Origin-Saga-9-320.jpg)