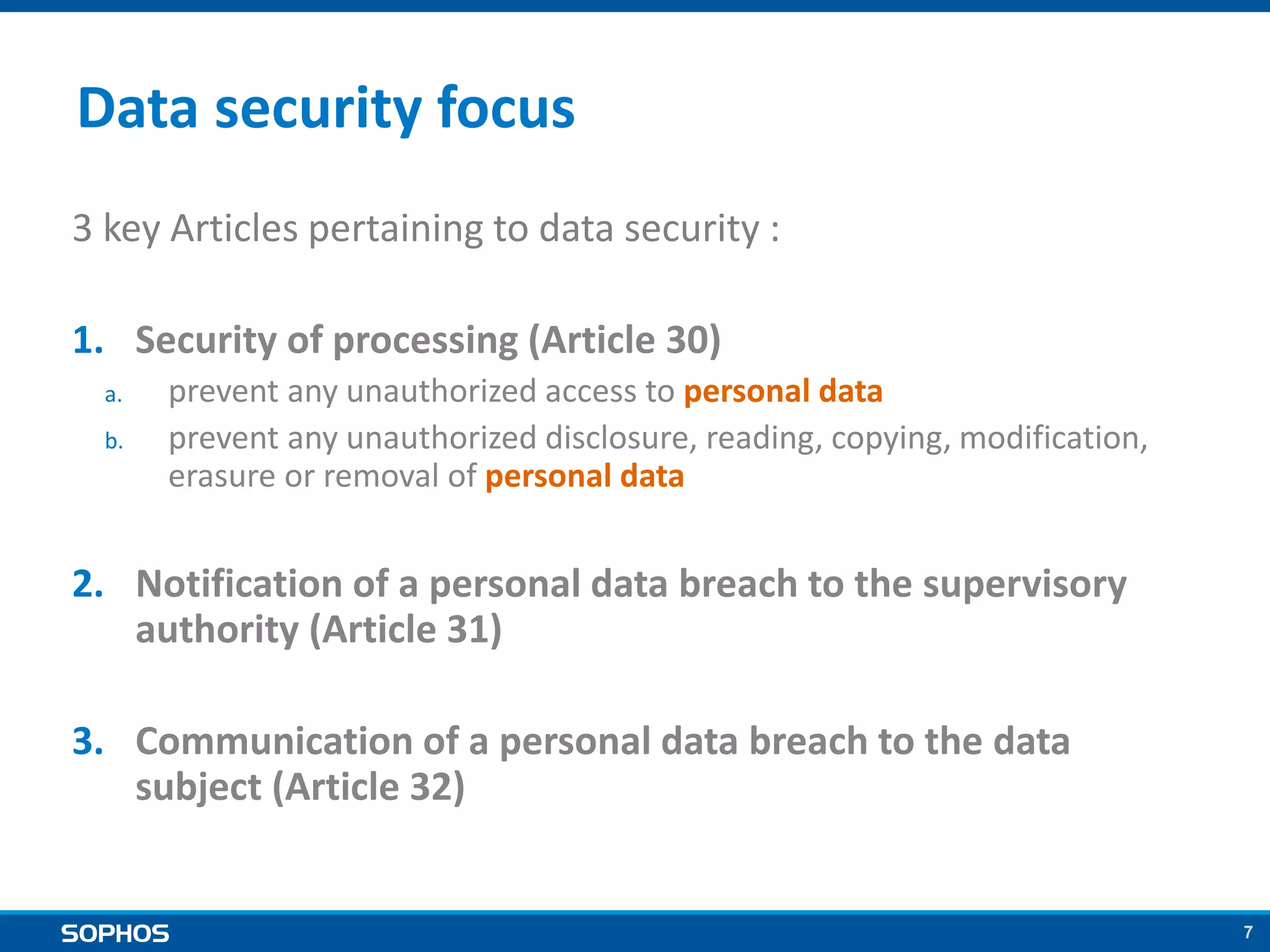
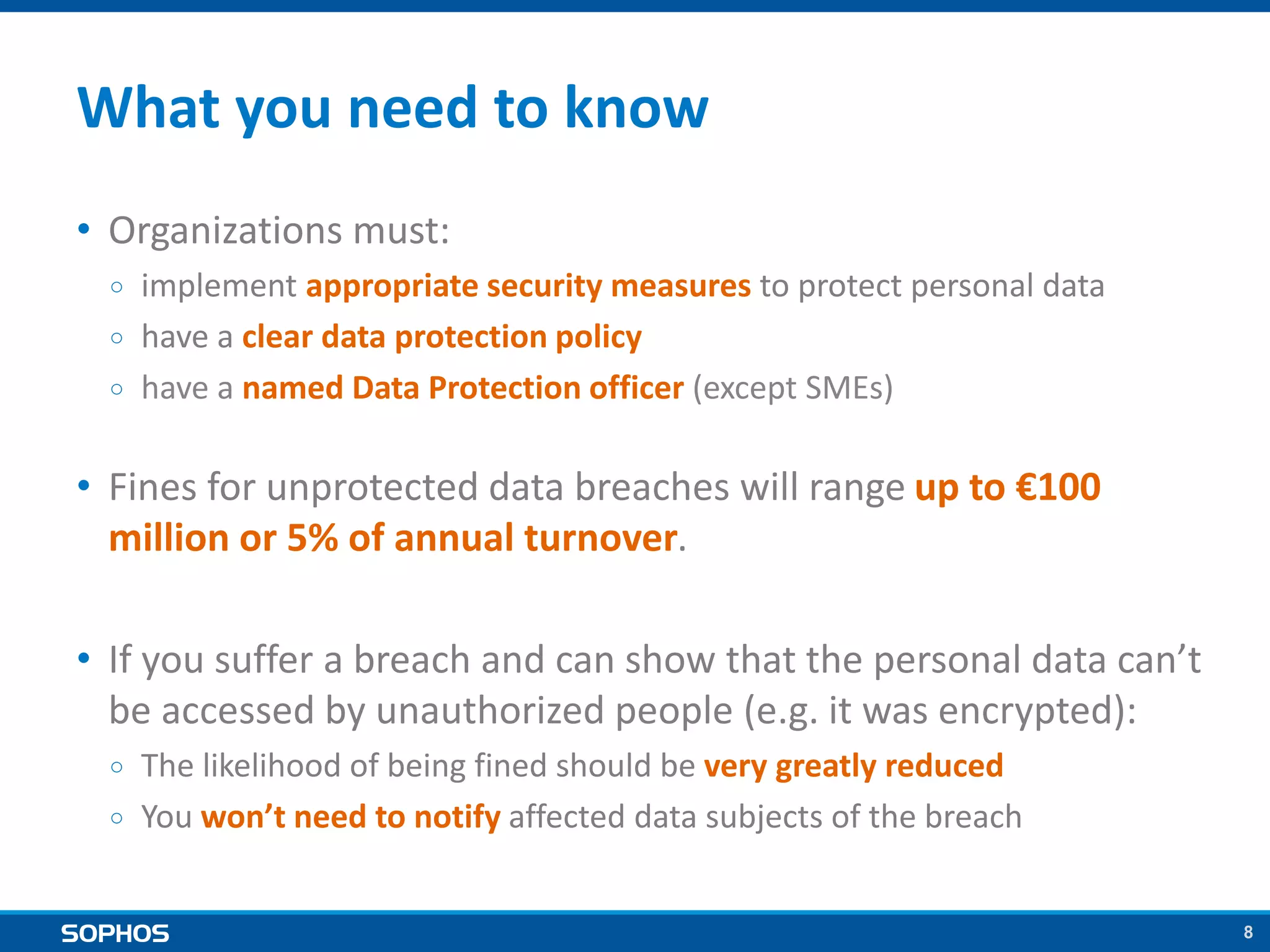
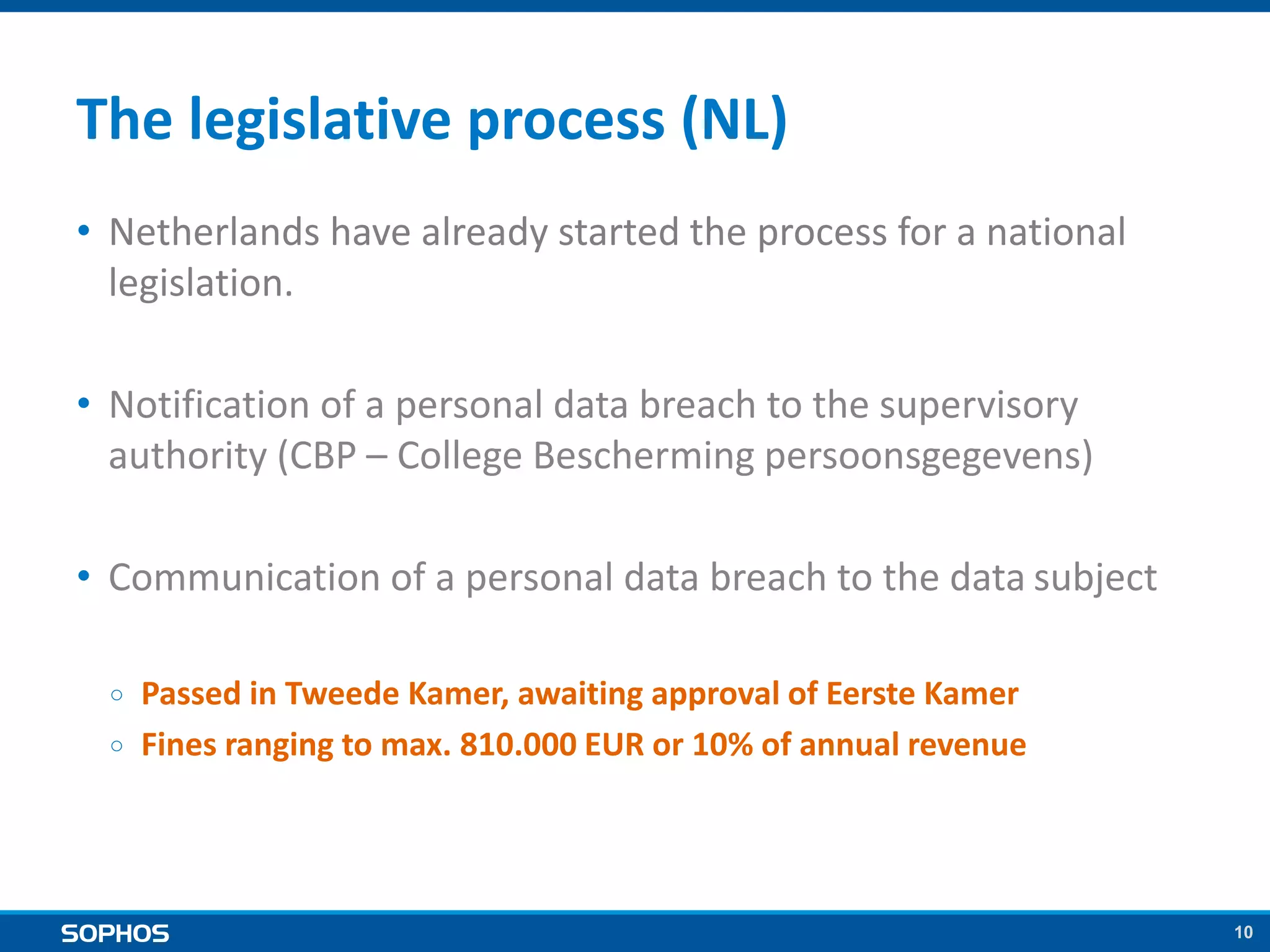
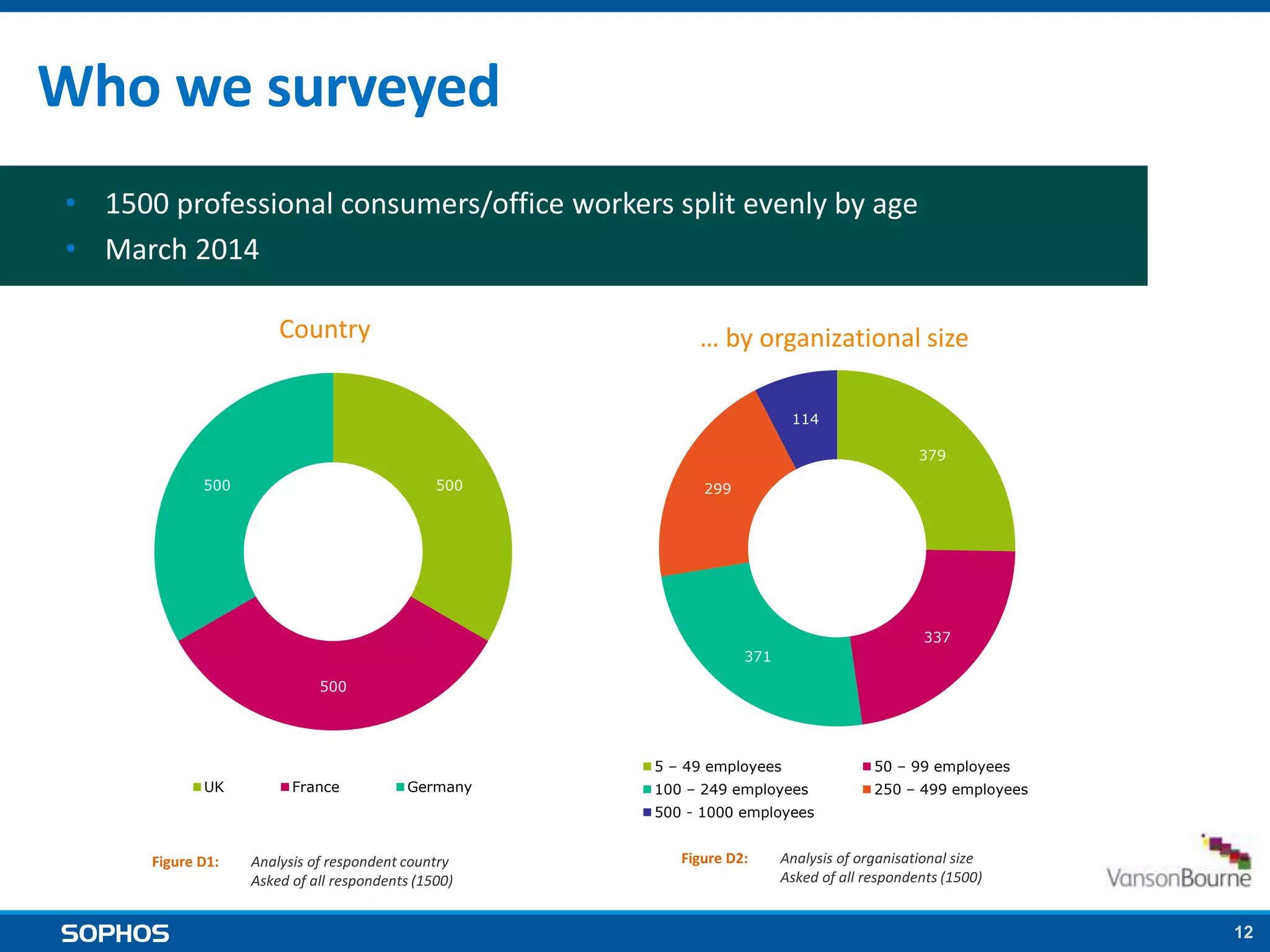
The proposed EU data protection regulation aims to unify national laws and modernize principles established in the 1995 directive, enhancing data security for businesses and individuals. Key requirements include implementing security measures, appointing data protection officers, and facing substantial fines for breaches, which can be mitigated through encryption. The legislative process is well underway with strong support, and organizations are urged to prepare by establishing data protection policies and security measures.