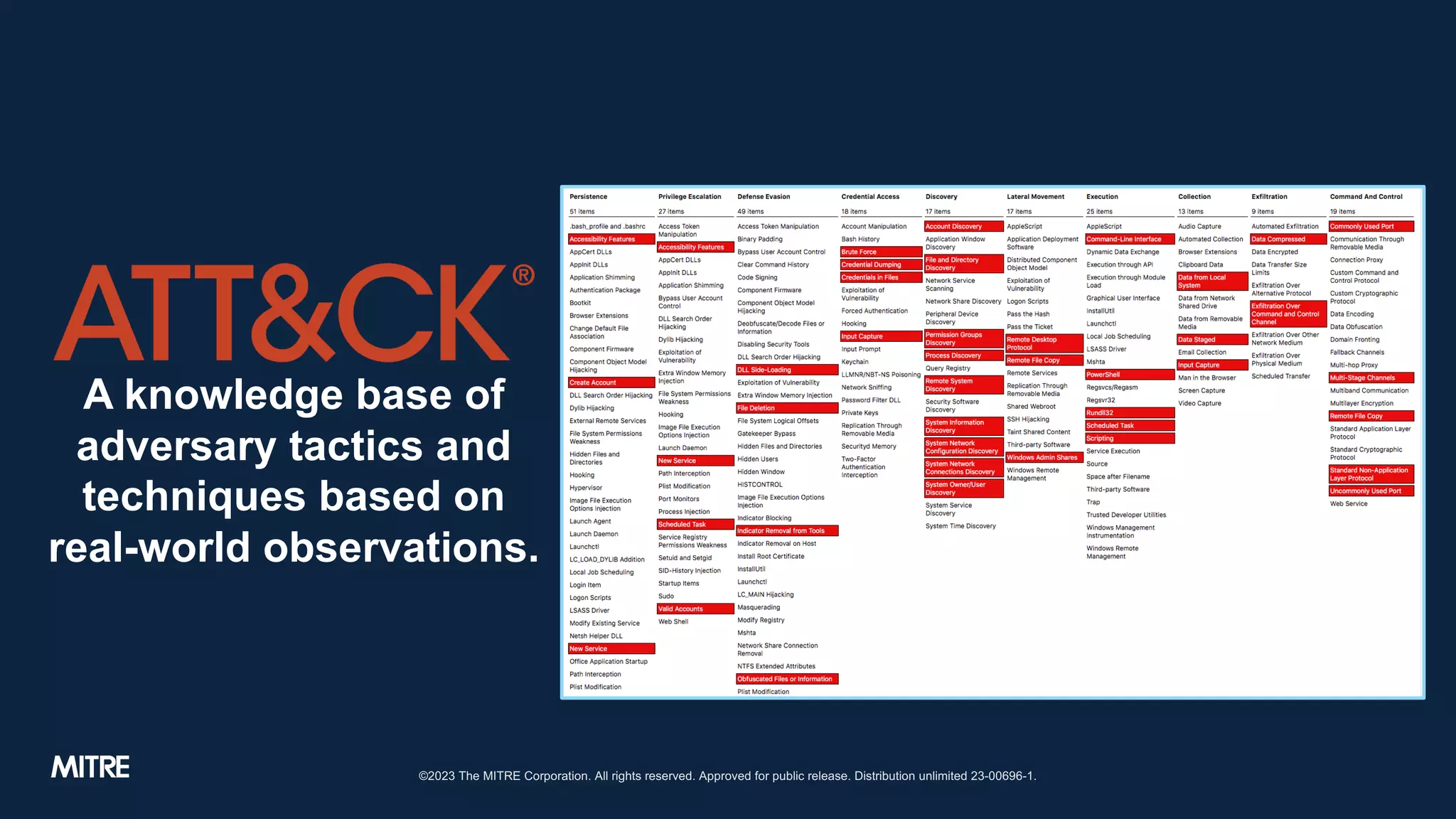
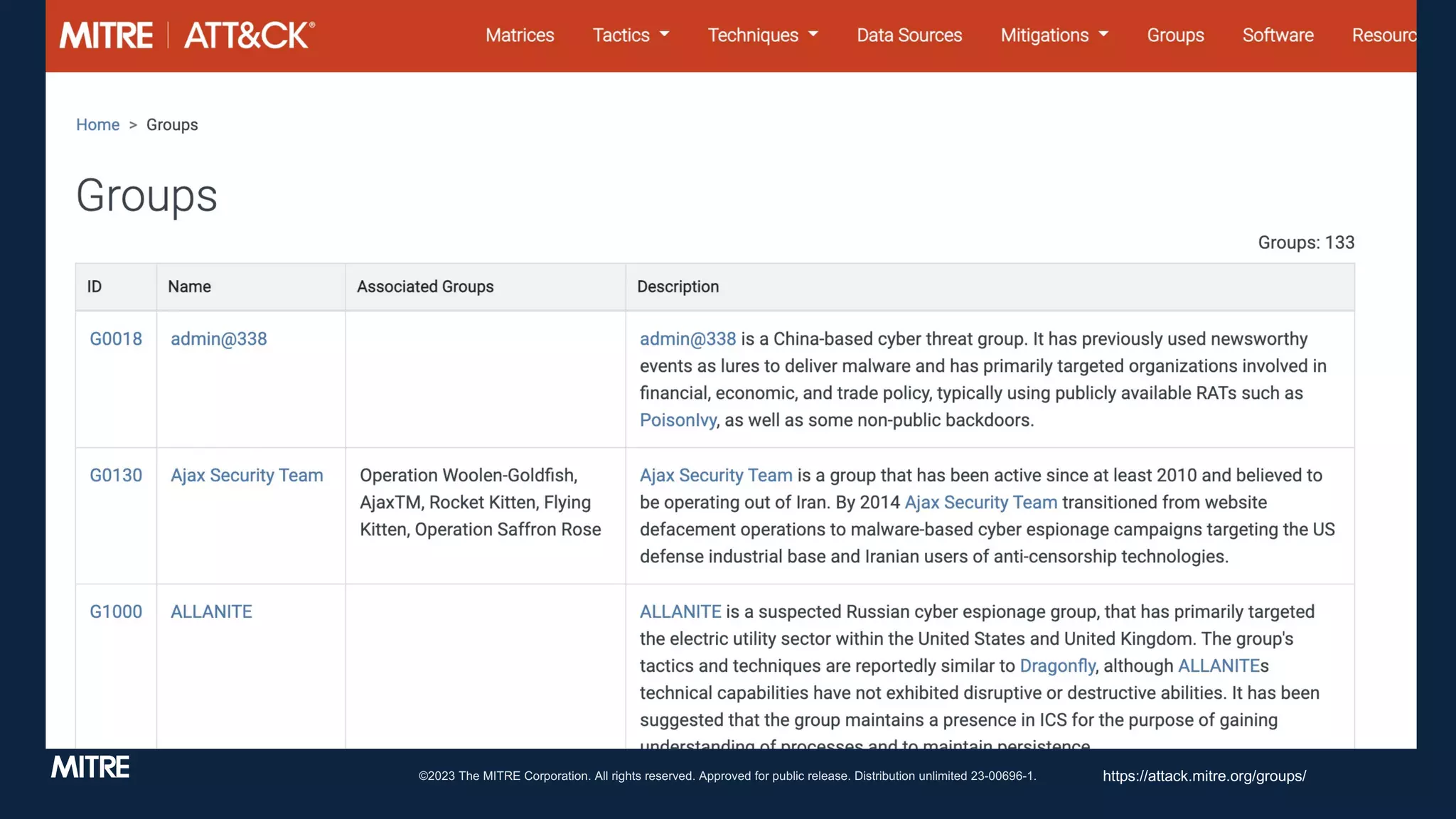
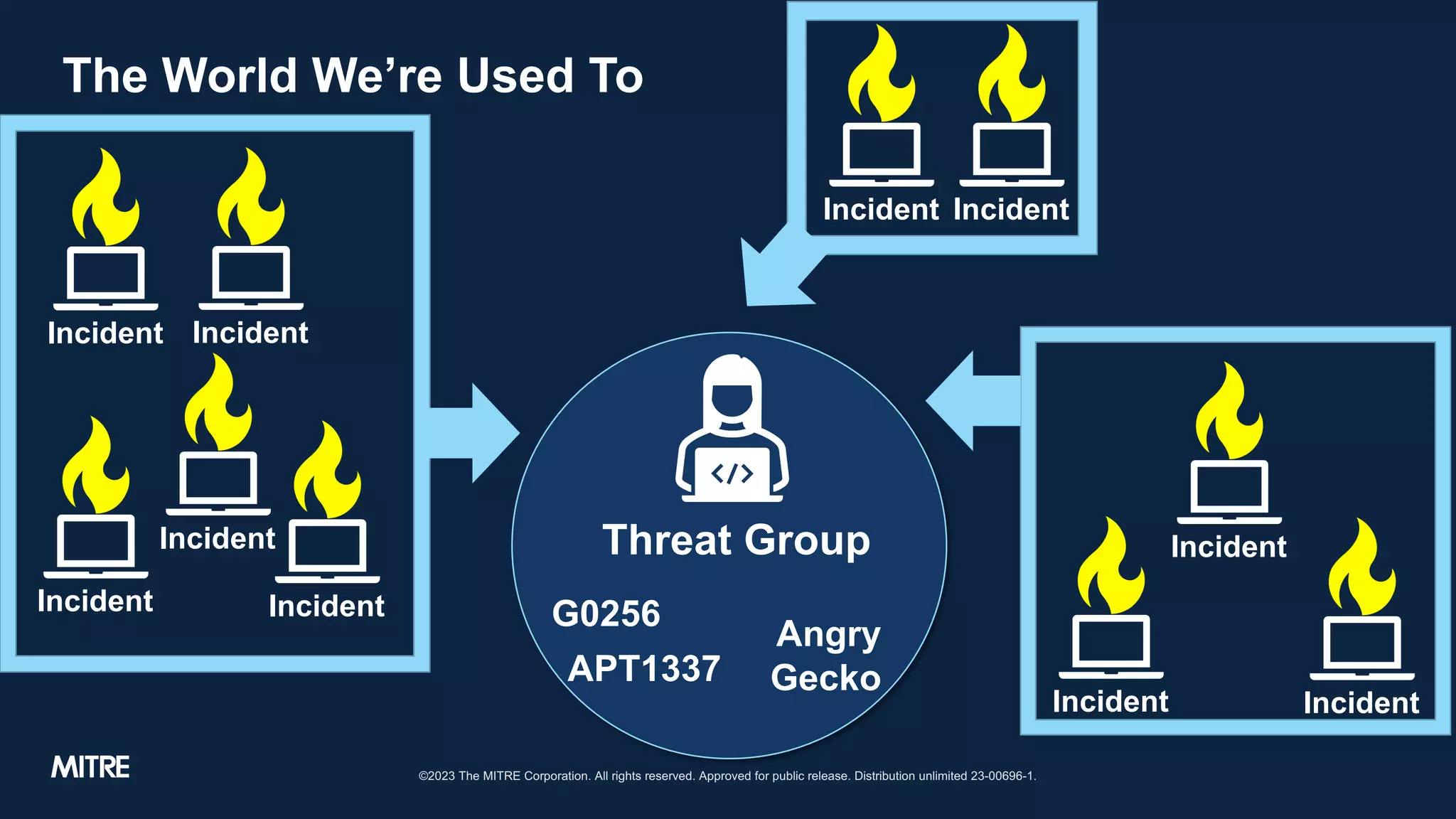
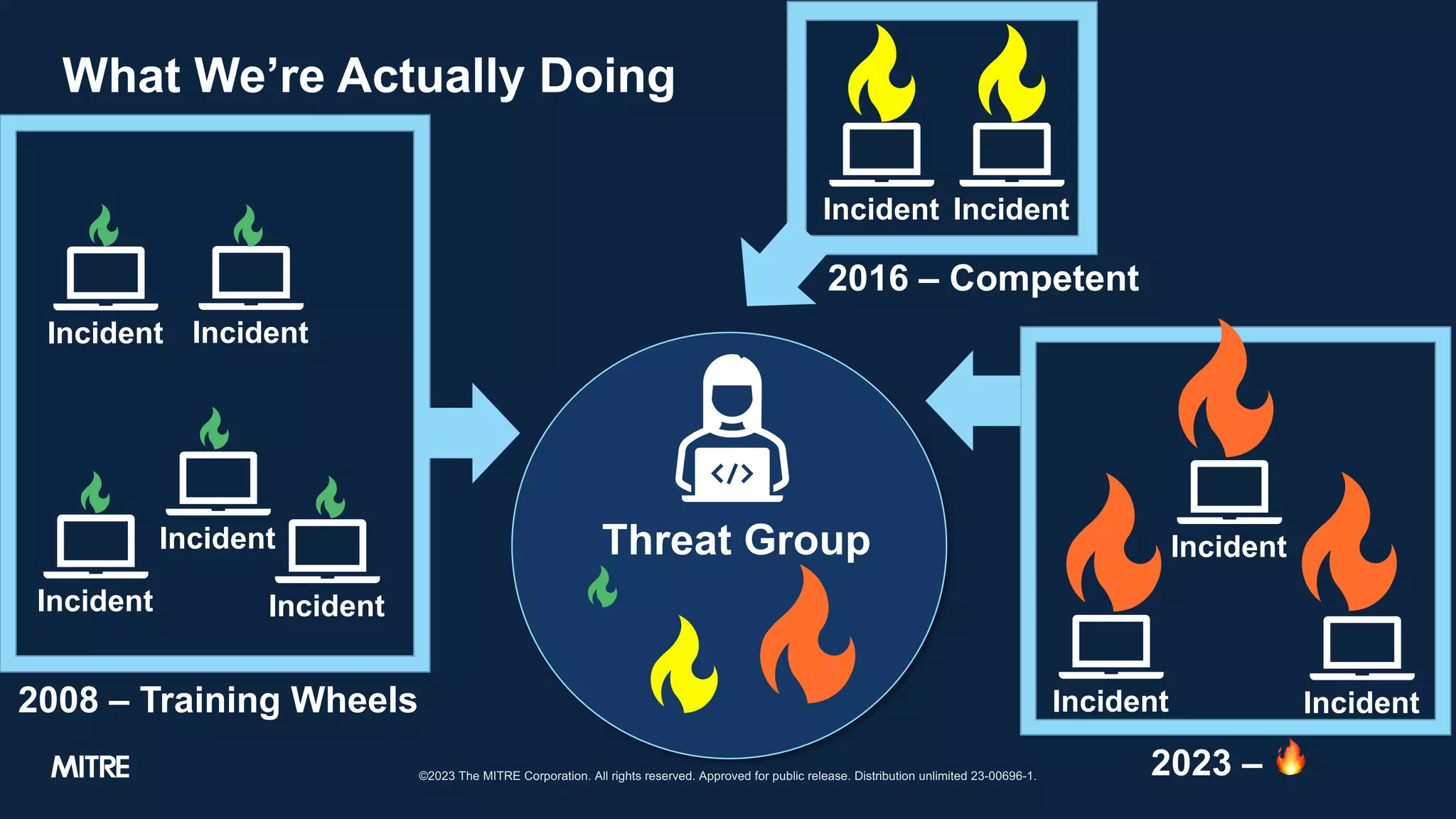
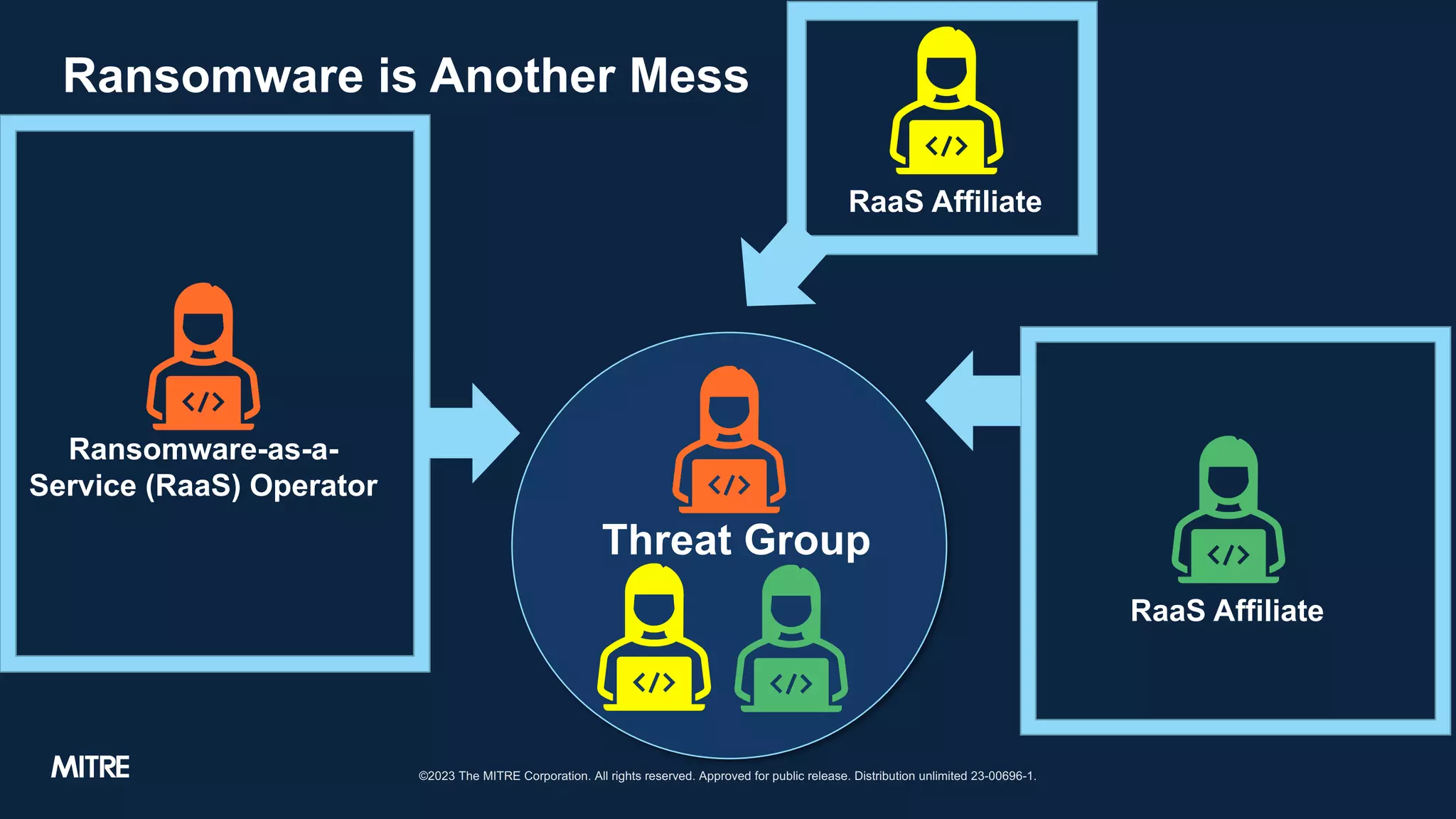
The document discusses adversary tactics and techniques observed in real-world incidents, emphasizing the evolution of threat groups over time. It highlights the importance of organizing intrusion activities into campaigns for better understanding and context. The takeaways suggest that while adversaries change behavior slowly, introducing structure can improve intelligence analysis.