Embed presentation
Download to read offline







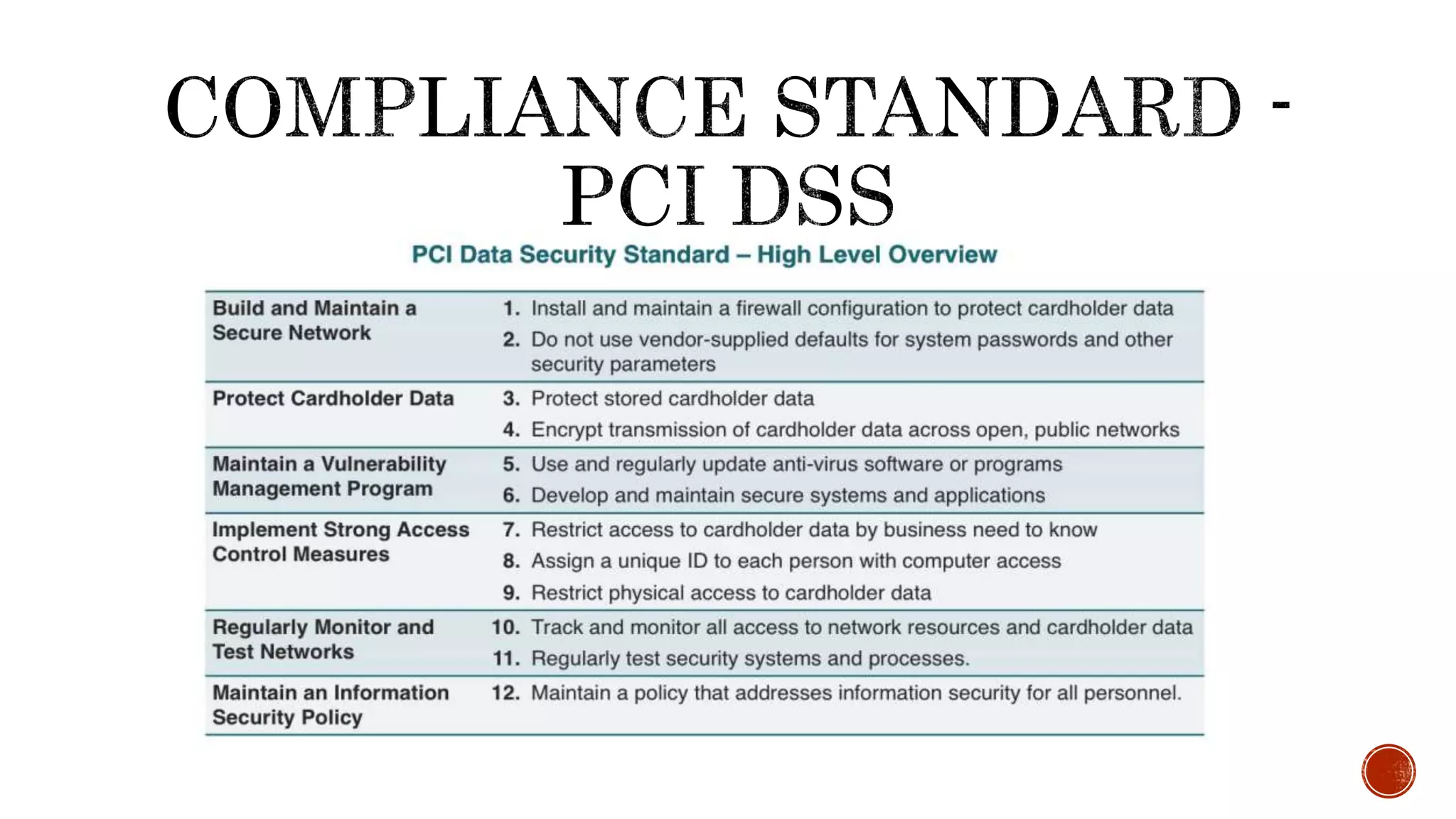
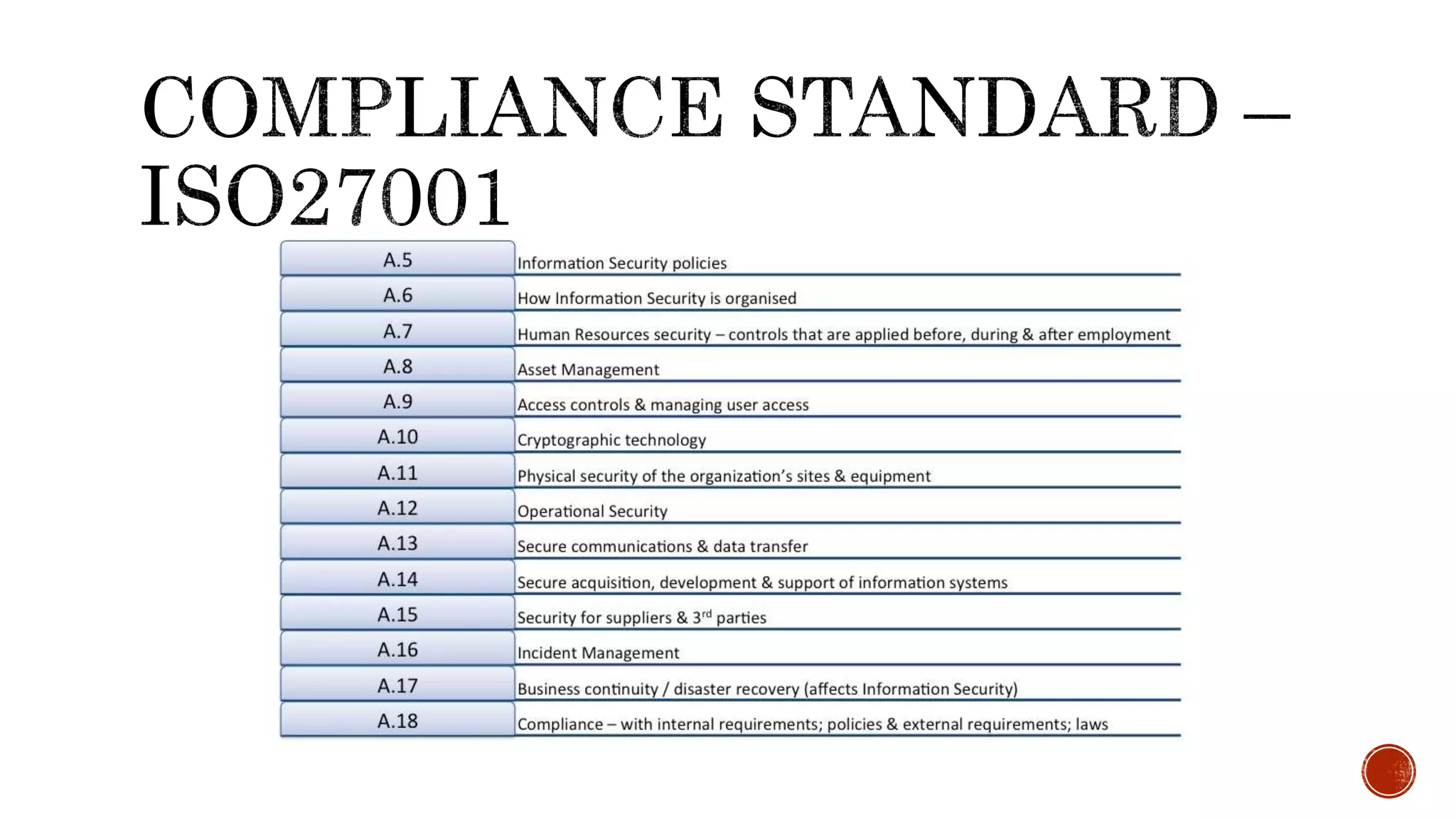

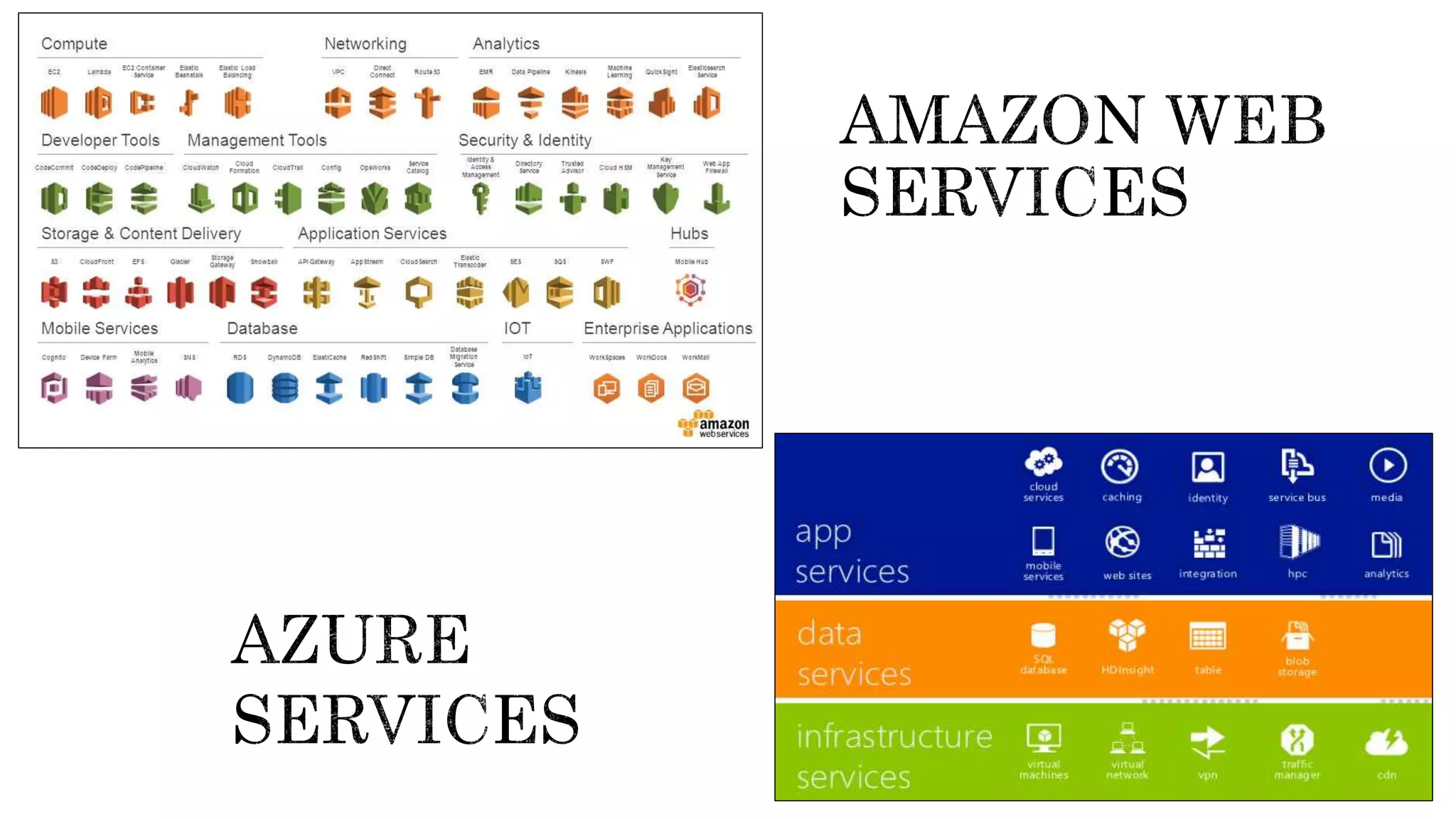






Saumya Vishnoi is an information security professional with about 6 years of experience, currently working at Freecharge. The document emphasizes the importance of compliance in security, particularly regarding PCI DSS and RBI PSS regulations, and advises organizations to verify the security policies of third-party providers. It warns against blindly trusting compliant services, urging regular audits and assessments for security assurance.
















