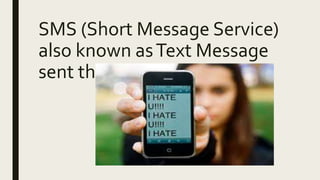
Cyberbullying is bullying that occurs online or through digital devices. It includes sending mean, harmful, or humiliating content about someone or sharing someone's private information without consent. Common places for cyberbullying are social media, text messages, and instant messages. Cyberbullying can negatively impact people's online reputations now and in the future with colleges and employers. It is also persistent, public, and difficult for adults to detect compared to traditional bullying. The document outlines 10 common forms of cyberbullying such as exclusion, harassment, outing, cyberstalking, and impersonation through fake profiles or trickery.