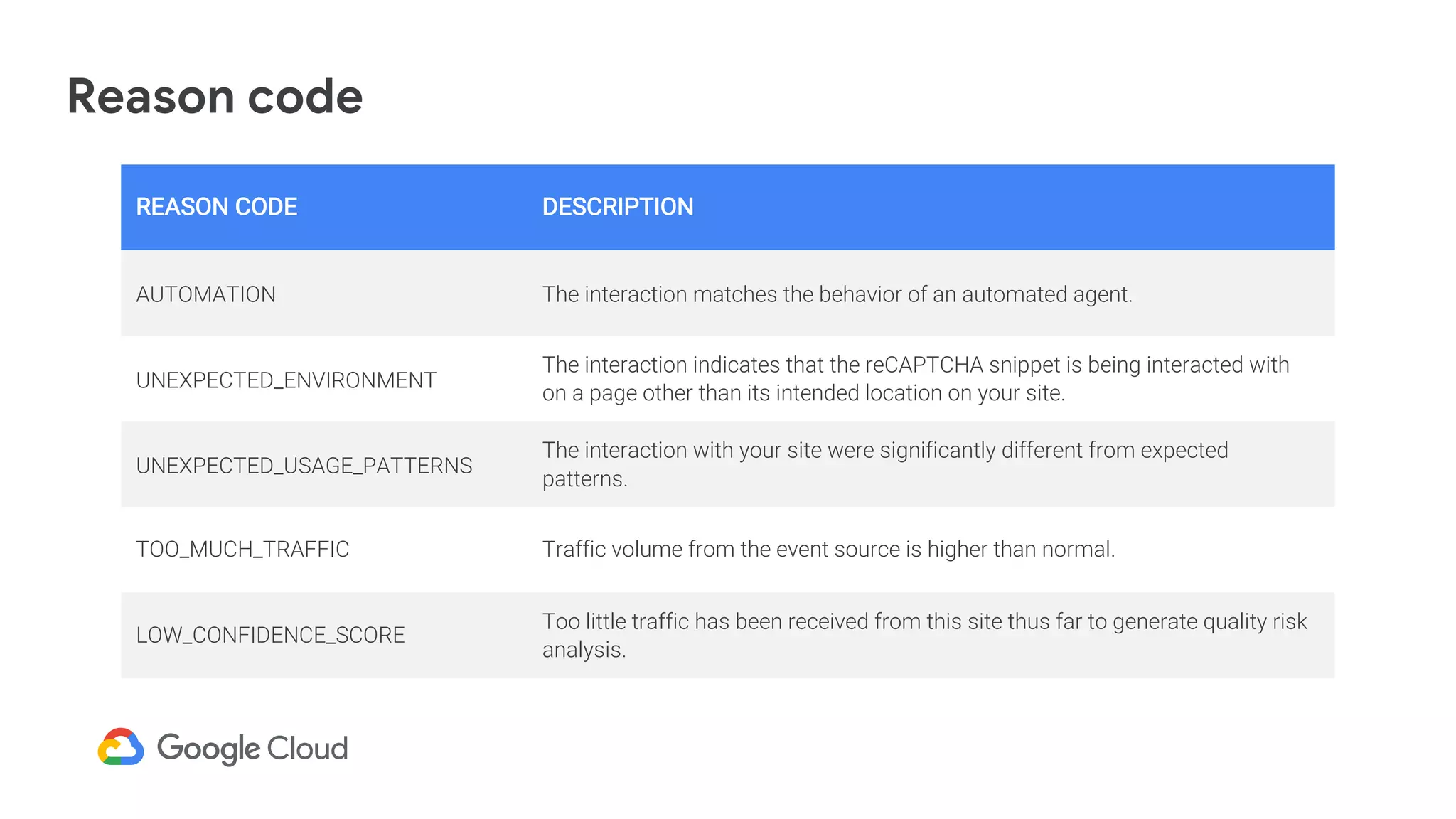
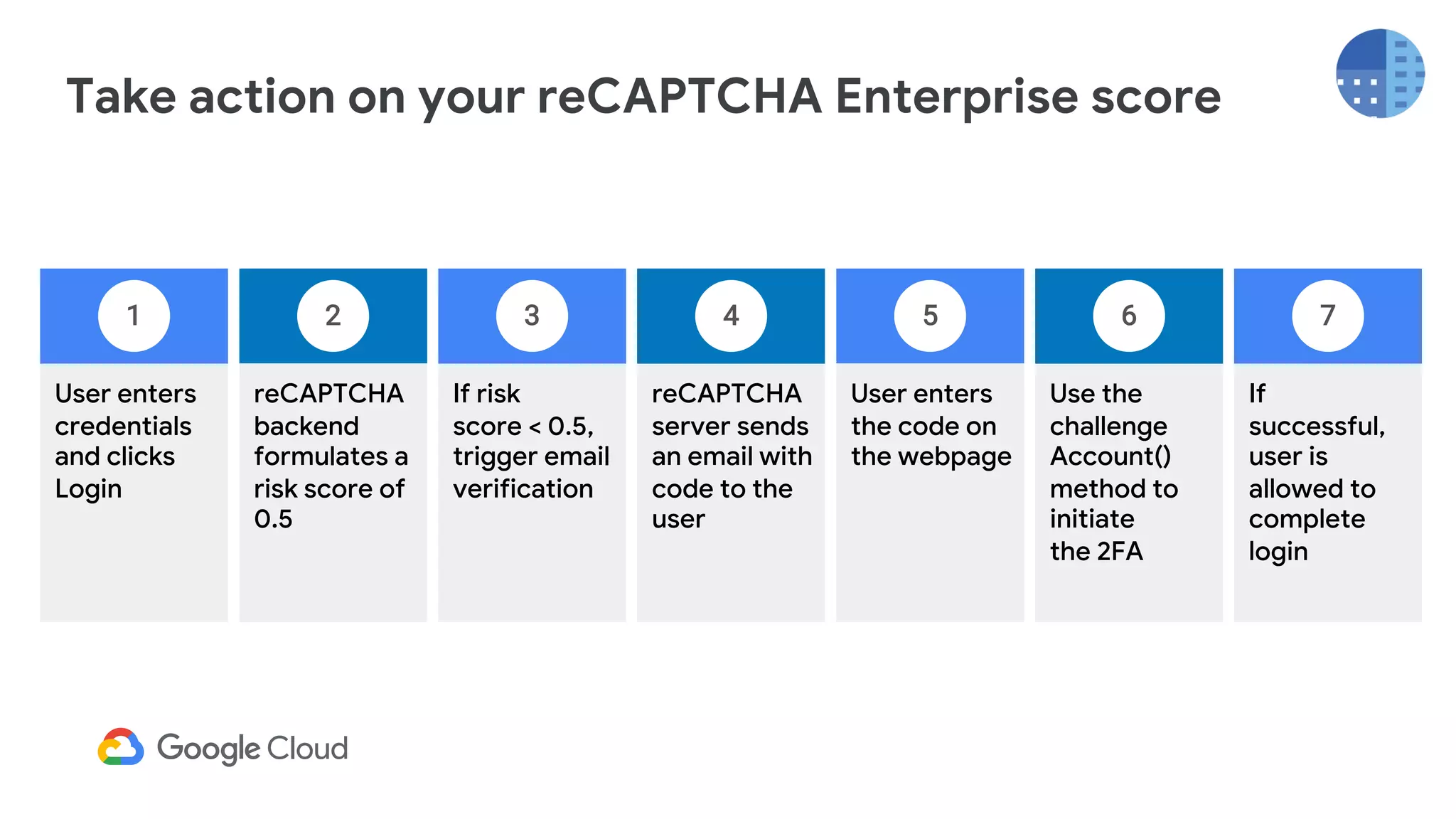
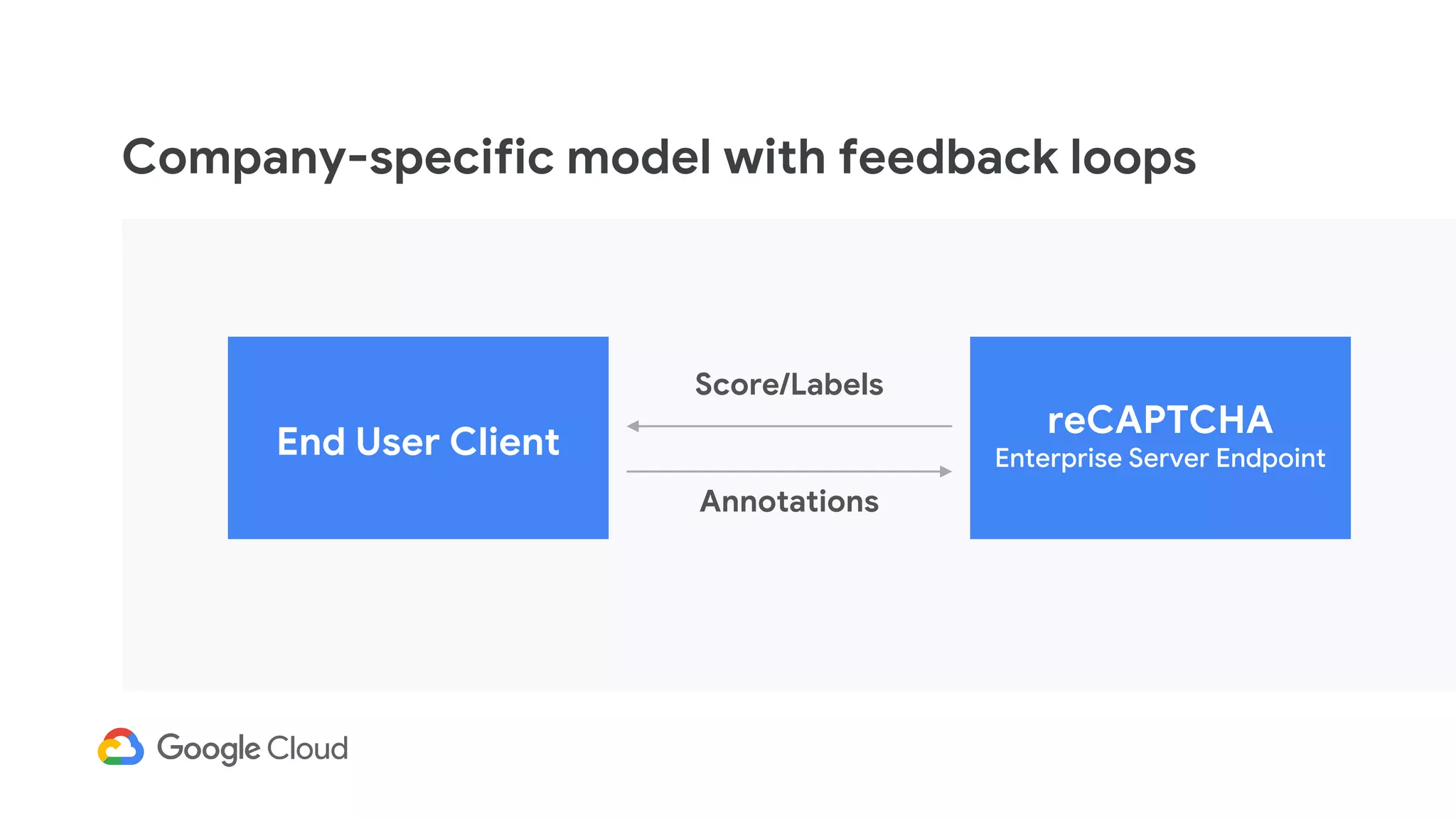
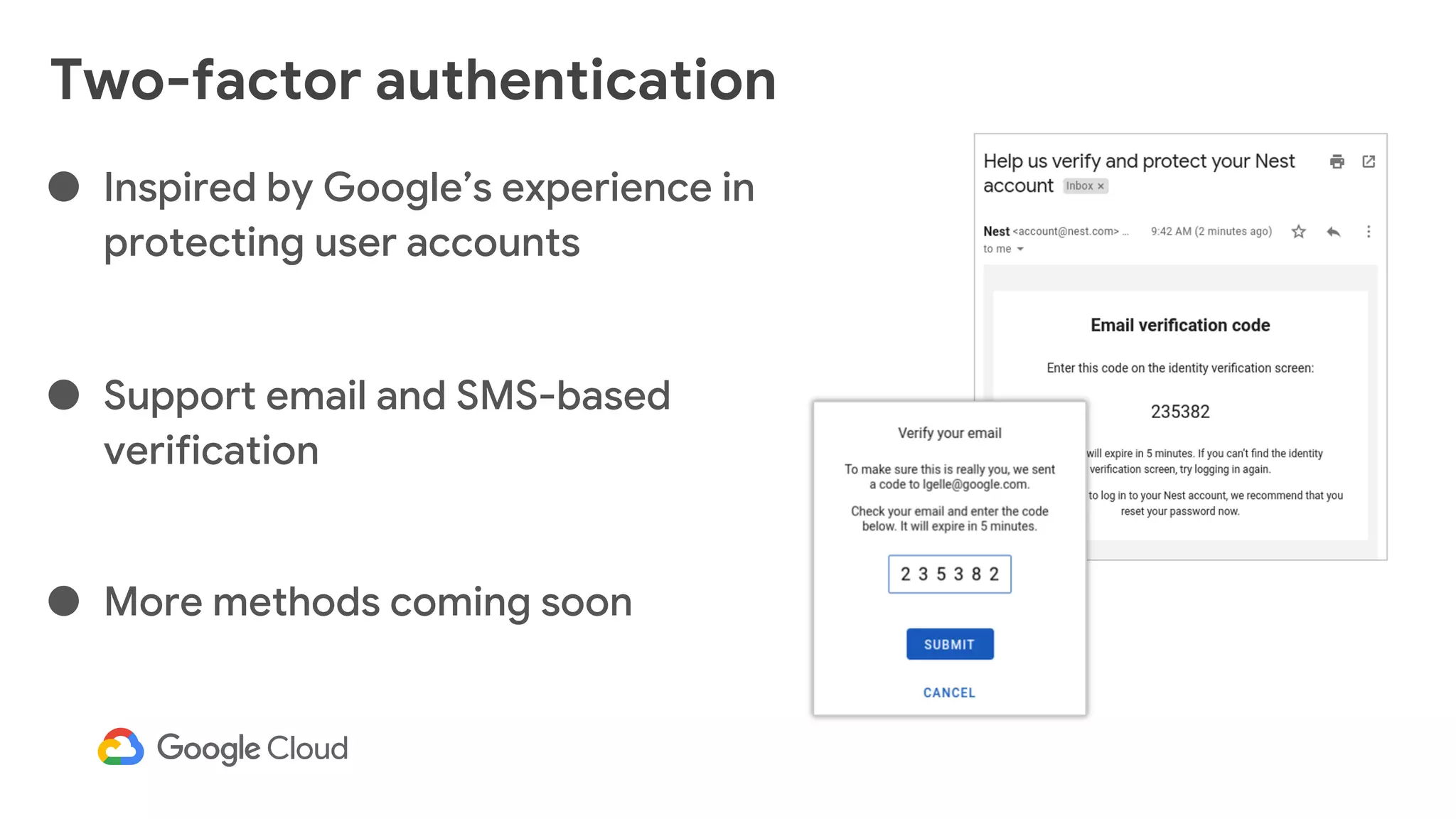
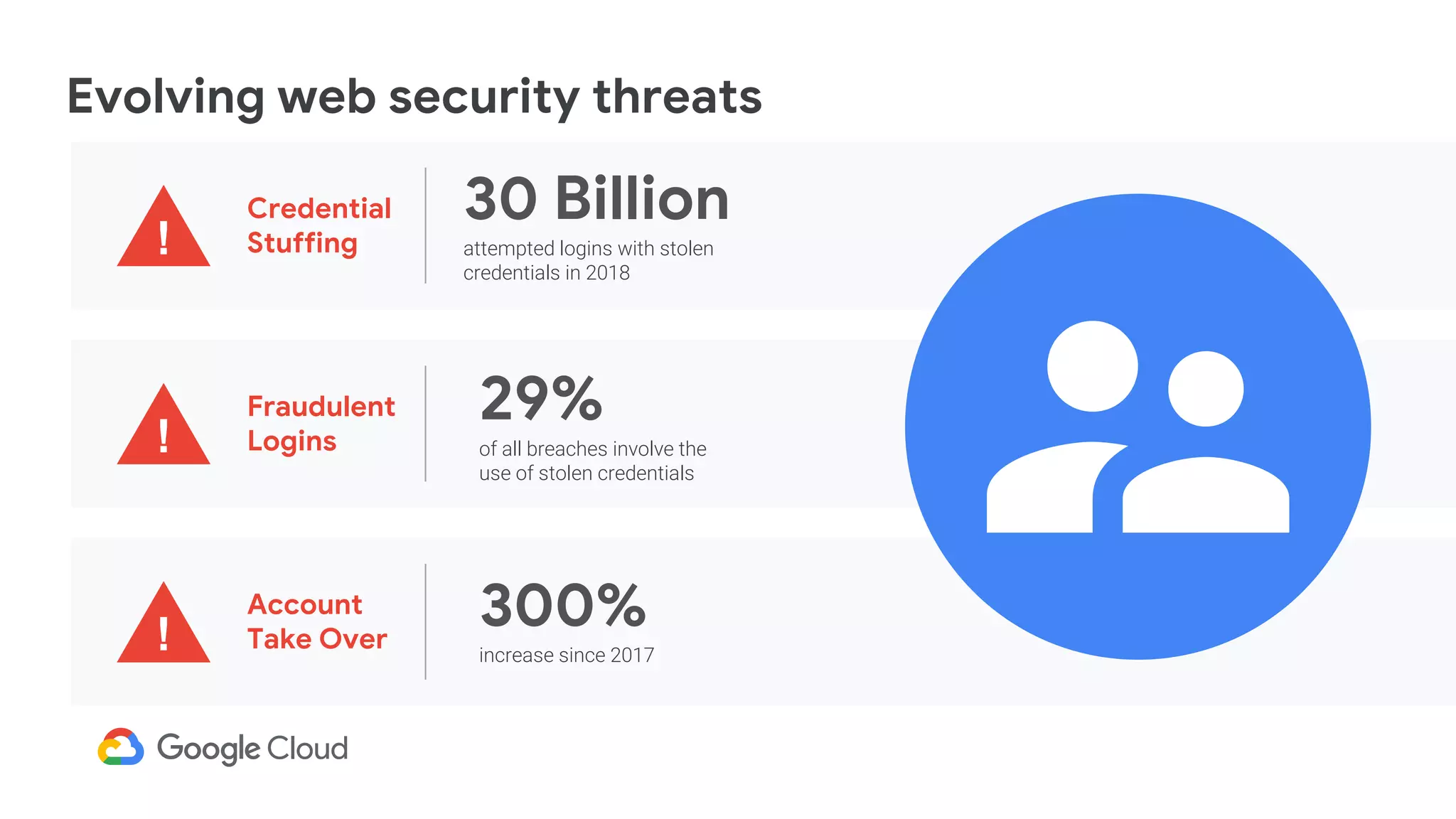
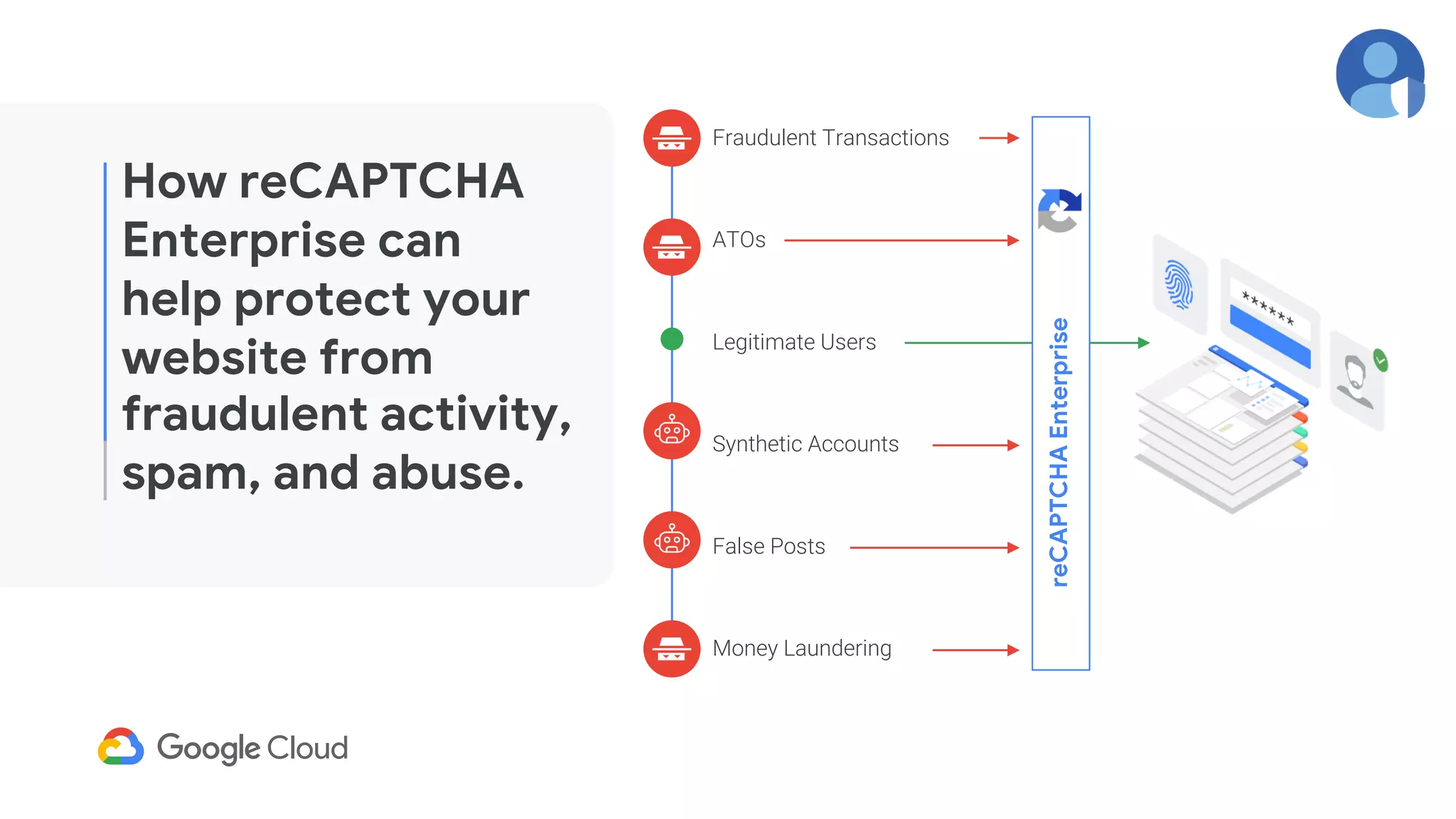
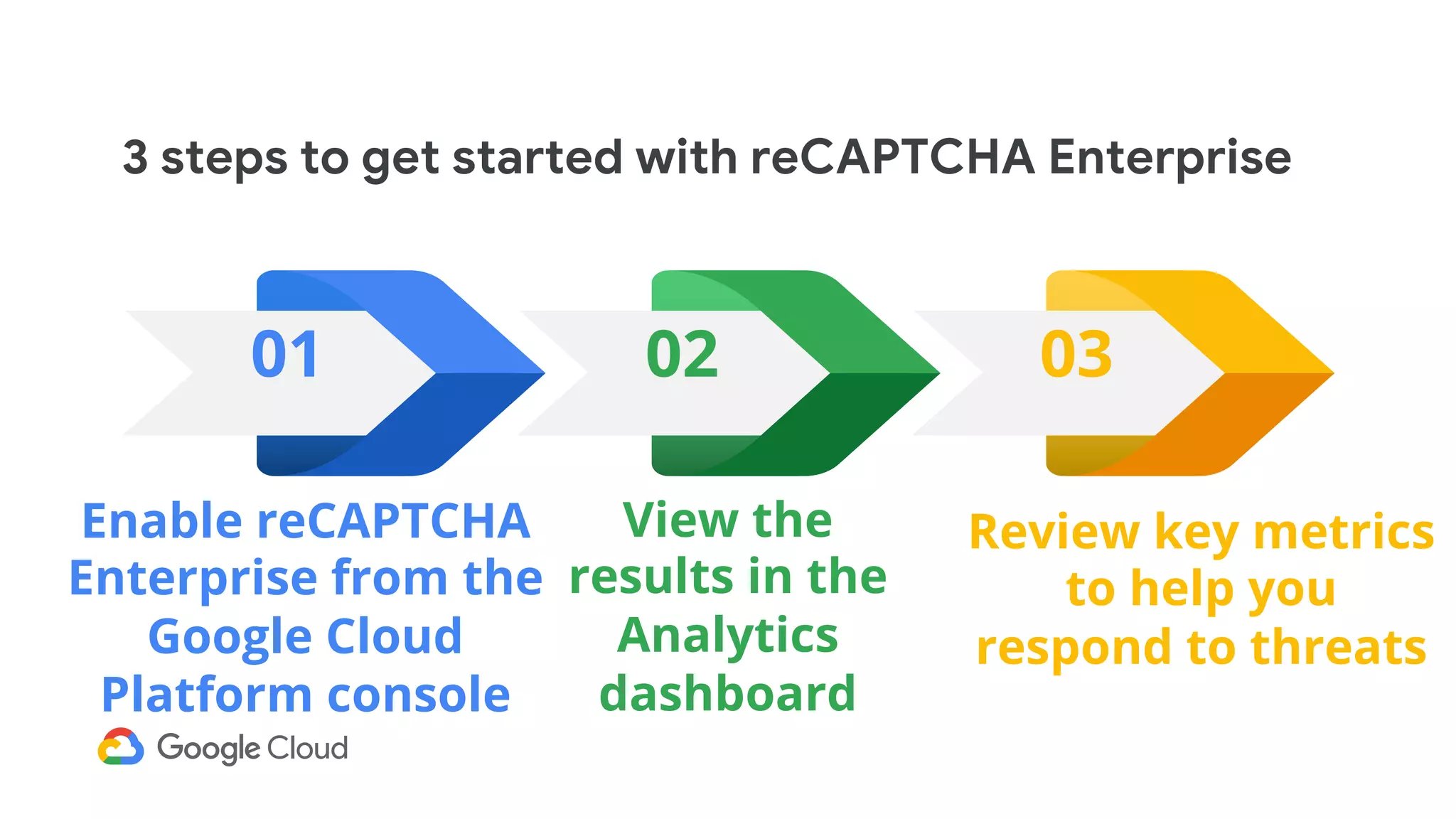
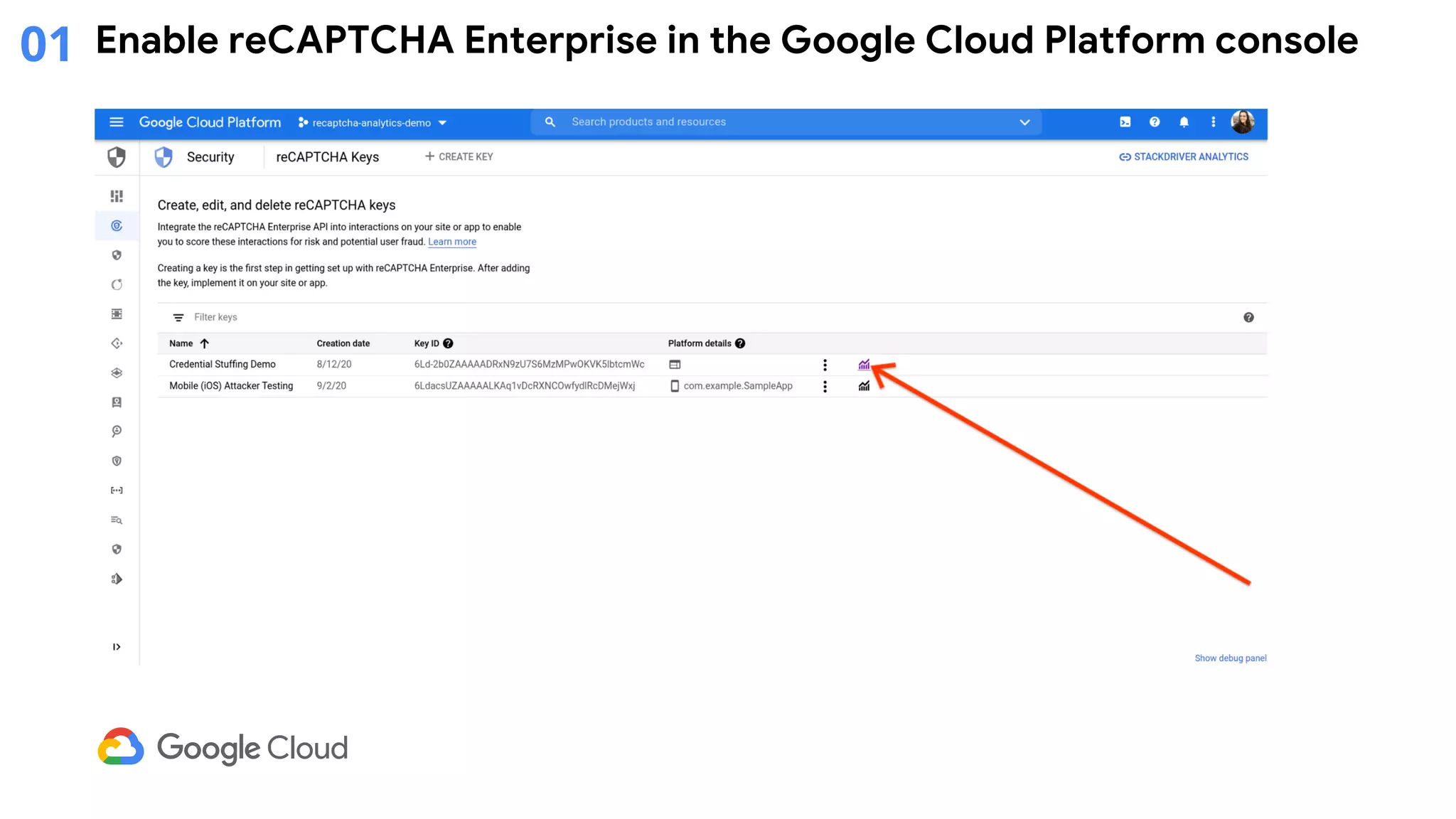
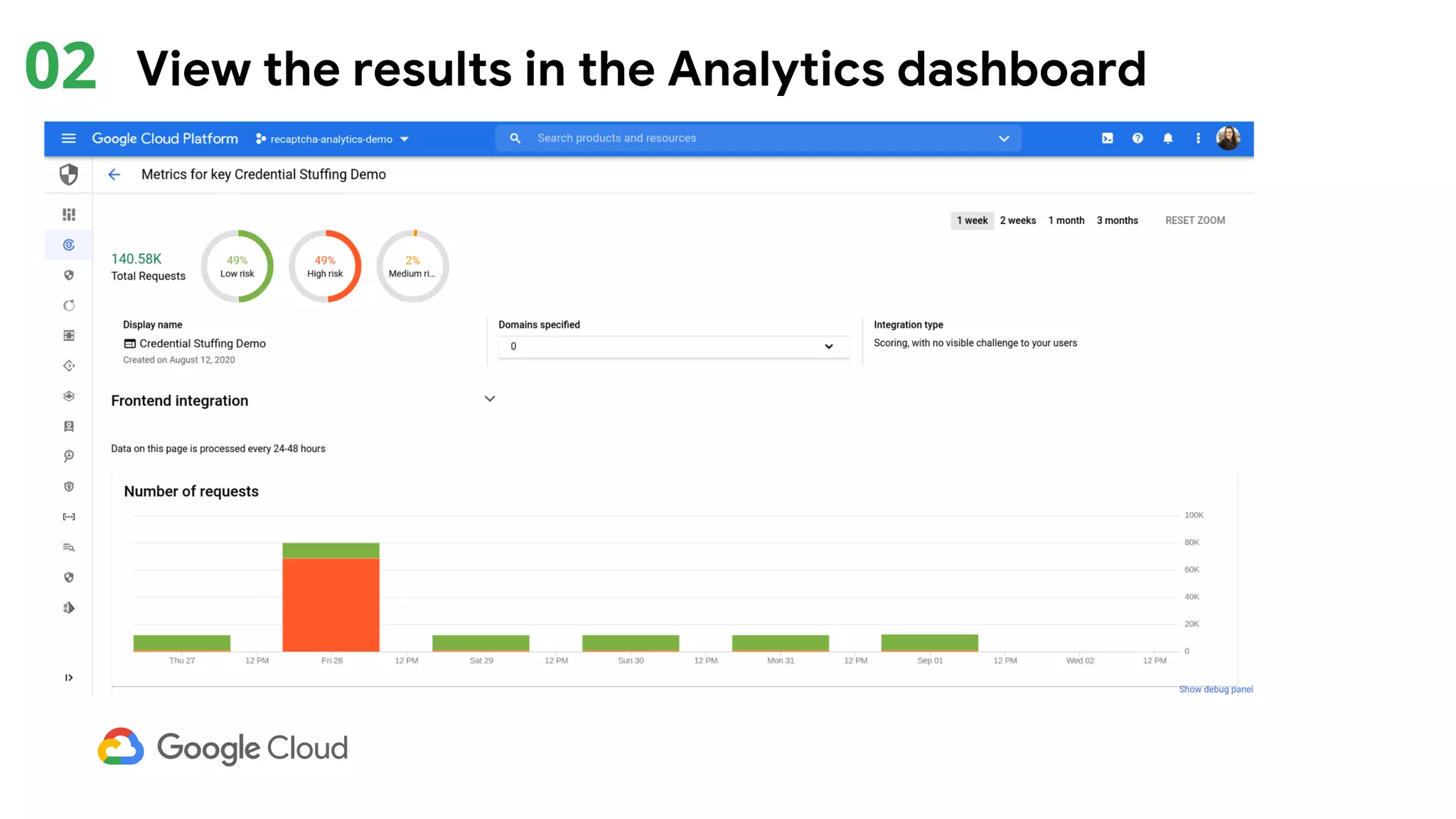
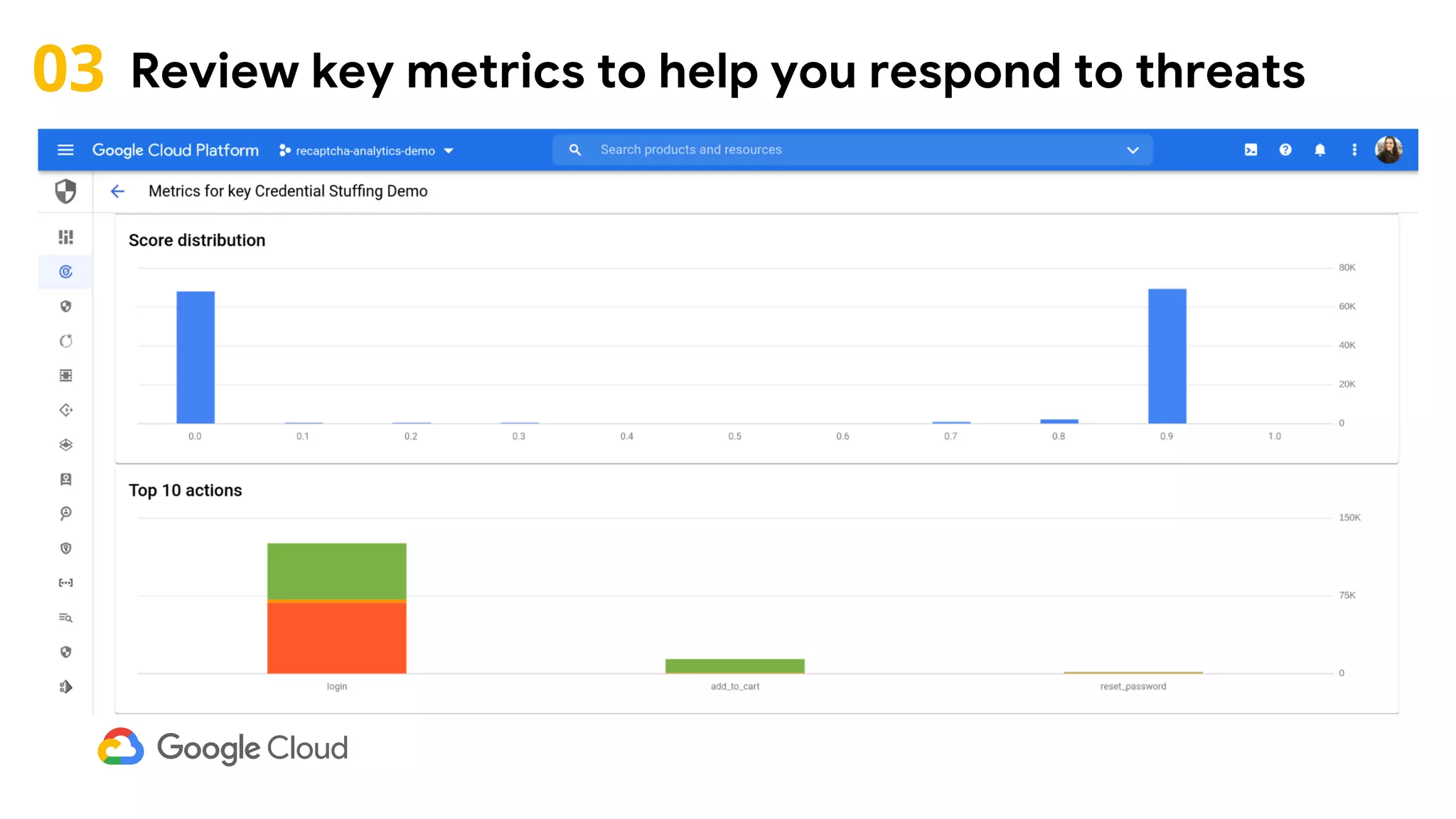
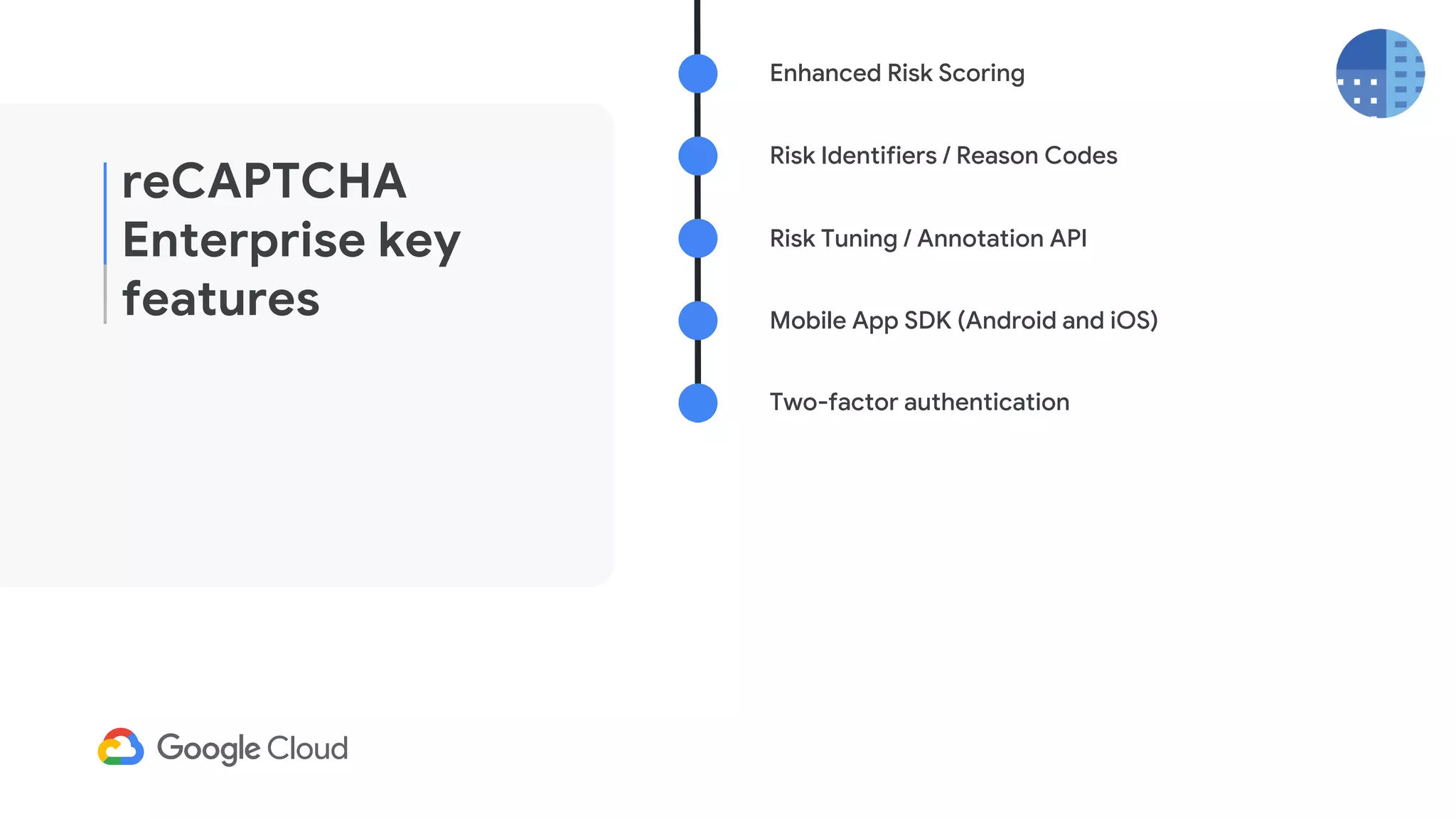
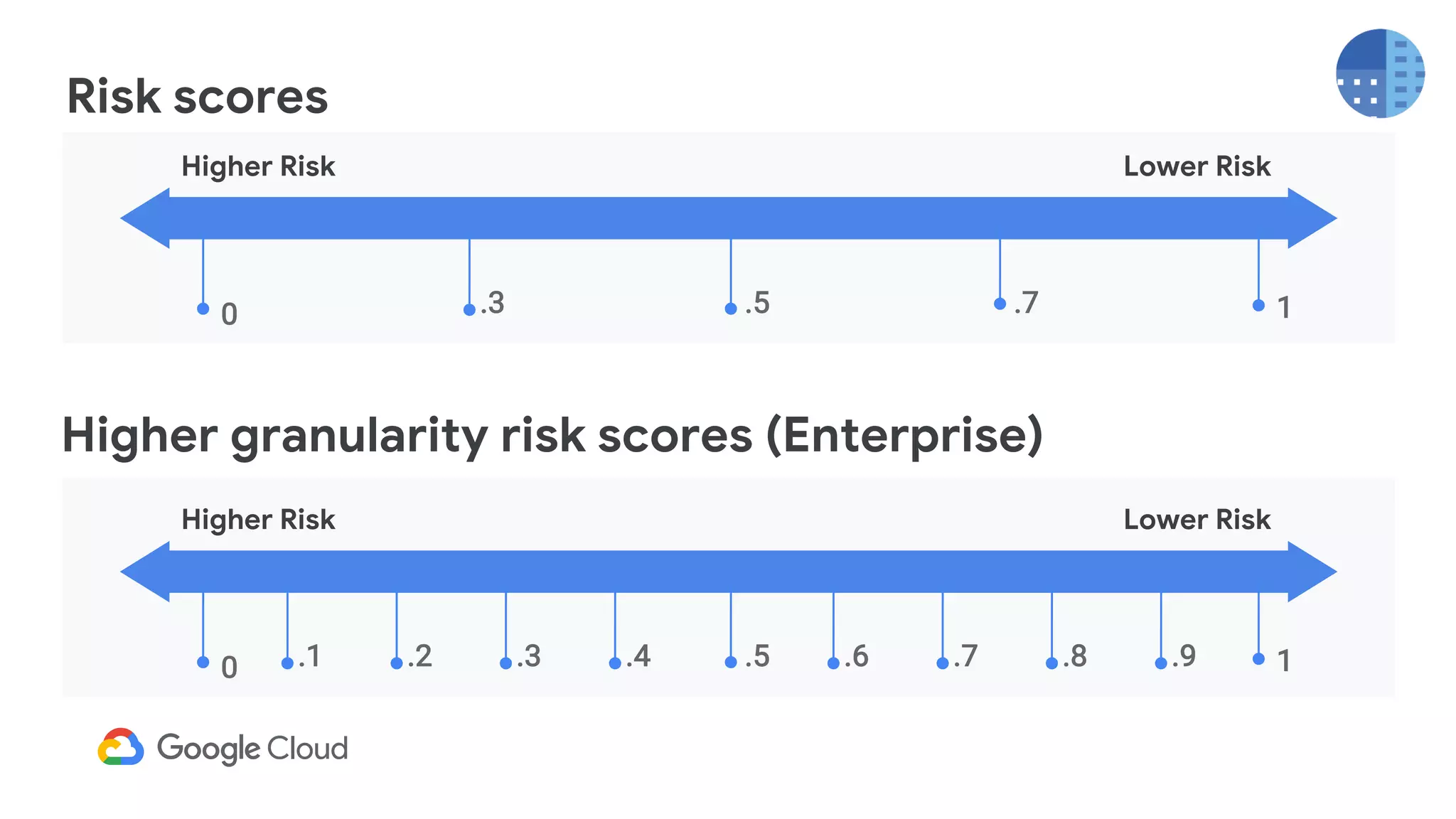
The document provides an overview of Google reCAPTCHA Enterprise, which helps protect websites from fraudulent activity, spam, and abuse. It discusses evolving web security threats like credential stuffing and account takeover that have increased in recent years. The document then summarizes reCAPTCHA Enterprise's features for detecting and preventing these threats, including risk scoring, reason codes, mobile app SDKs, and two-factor authentication. It provides steps to get started and a demo of how reCAPTCHA Enterprise analyzes interactions and takes action based on risk scores.


![reCAPTCHA
Enterprise risk
score
{
'tokenProperties': {
'valid': True,
'hostname': 'www.google.com',
'action': 'homepage',
'createTime': u'2019-03-28T12:24:17.894Z'
},
'confidence': 0.1,
'reasons': ['AUTOMATION'],
'event': {
'token': 'RESPONSE_TOKEN',
'siteKey': 'SITE_KEY'
},
'name':
u'projects/[PROJECT_ID]/assessments/b6ac310000000000'
}
01
02
03
04
05
06
07
08
09
10](https://image.slidesharecdn.com/securityboulevardwebinardeck-200929202019/75/Step-by-Step-Guide-to-Protecting-Web-Apps-with-Google-reCAPTCHA-15-2048.jpg)