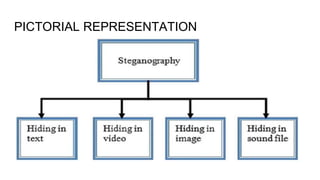
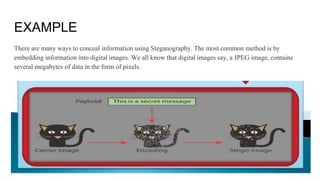
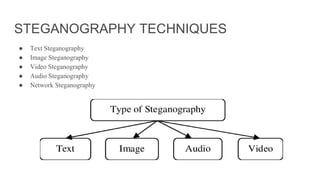
This document discusses Steganography Project. Steganography is the technique of hiding secret data within ordinary files like images or messages to avoid detection. The document outlines the introduction, examples, advantages, and disadvantages of steganography. It also discusses techniques like image steganography and the proposed model for the project. The goal is to develop a software that can hide messages in images with less data reduction and detection during transmission.