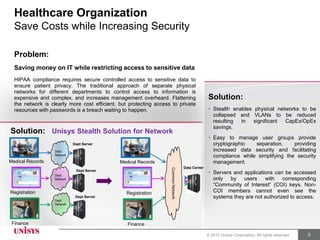
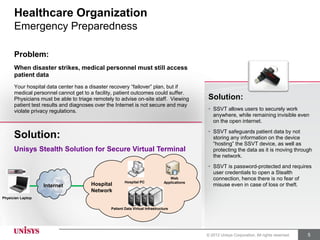
The document describes how the Unisys Stealth Solution can help healthcare organizations securely share private health information, save costs by simplifying networks while increasing security, solve the leading cause of HIPAA data breaches by preventing theft of laptops containing private data, and allow medical personnel to access patient data during emergencies even when away from secure facilities. The Stealth Solution uses strong encryption, message shredding, and controlled access through user credentials to protect data in motion across networks and remote access.