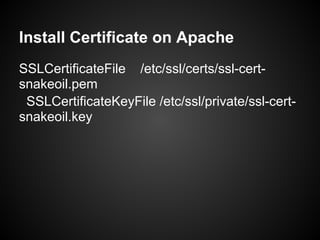
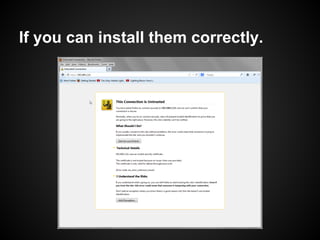
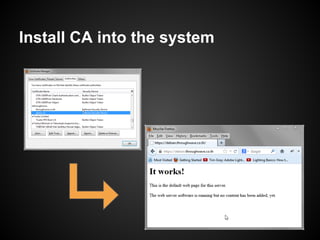
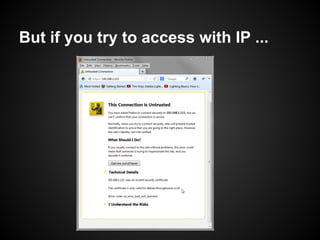
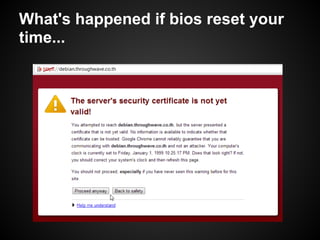
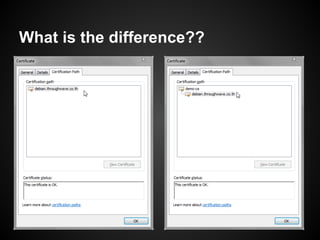
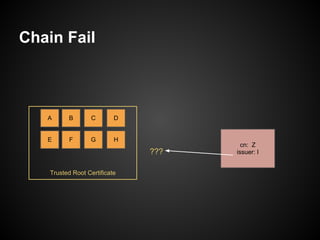
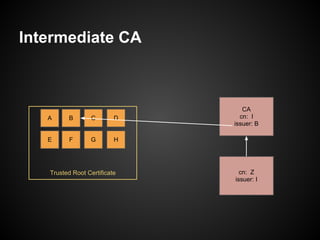
The document provides a detailed guide on SSL certificate management, including the use of OpenSSL for generating RSA key pairs, creating certificate requests, and installing certificates. It covers validation of certificates, connection to LDAPS, and troubleshooting common issues, alongside examples of commands and expected outputs. Key steps involve generating keys, creating self-signed certificates, and validating the certificate and key pairs.




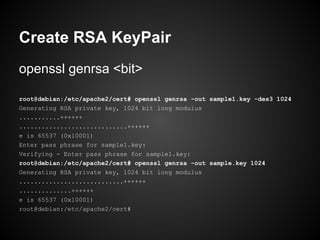
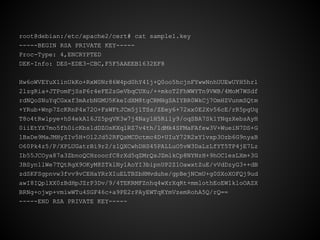
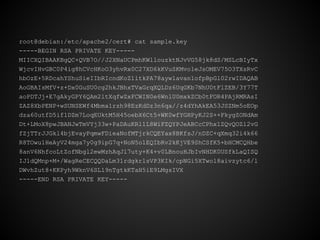
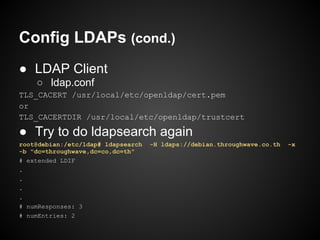
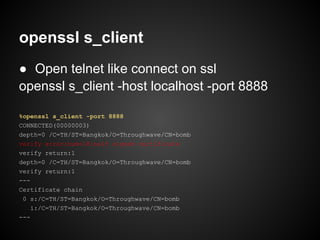
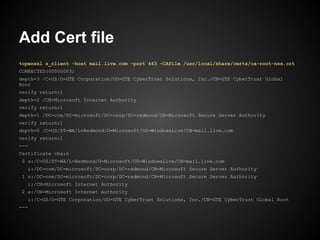
![Create Certificate Request
openssl req -key <privkey> -nodes -new
root@debian:/etc/apache2/cert# openssl req -key sample.key -nodes -new -out sample.csr
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:TH
State or Province Name (full name) [Some-State]:Bangkok
Locality Name (eg, city) []:
Organization Name (eg, company) [Internet Widgits Pty Ltd]:Throughwave
Organizational Unit Name (eg, section) []:
Common Name (eg, YOUR name) []:debian.throughwave.co.th
Email Address []:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
root@debian:/etc/apache2/cert#](https://image.slidesharecdn.com/certificate-130210111059-phpapp02/85/SSLCertificate101-10-320.jpg)
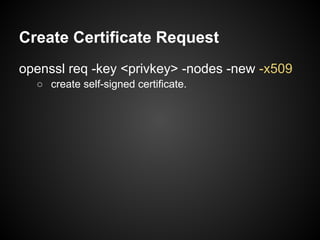







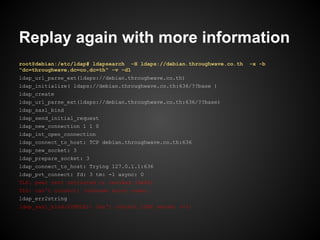
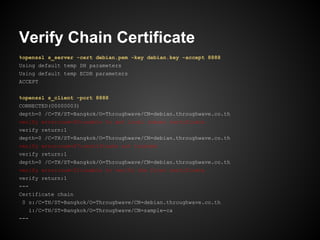
![%openssl req -key sample1.key -new -x509 -nodes -days 3650 -out sample1.cer
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:TH
State or Province Name (full name) [Some-State]:Bangkok
Locality Name (eg, city) []:
Organization Name (eg, company) [Internet Widgits Pty Ltd]:Throughwave
Organizational Unit Name (eg, section) []:
Common Name (eg, YOUR name) []:bomb
Email Address []:
%openssl x509 -in sample1.cer -text -noout](https://image.slidesharecdn.com/certificate-130210111059-phpapp02/85/SSLCertificate101-21-320.jpg)
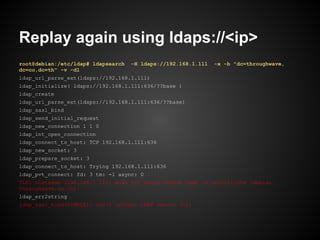
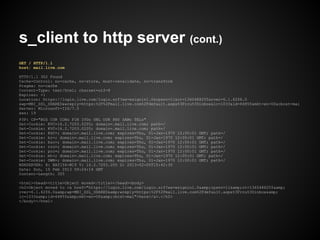
![Private Key vs Public Key
Private Key = [ modulus , private exponent]
Public Key = [ modulus, public exponent]
Valid Key Pair
Private Key.modulus = Public Key.modulus](https://image.slidesharecdn.com/certificate-130210111059-phpapp02/85/SSLCertificate101-23-320.jpg)