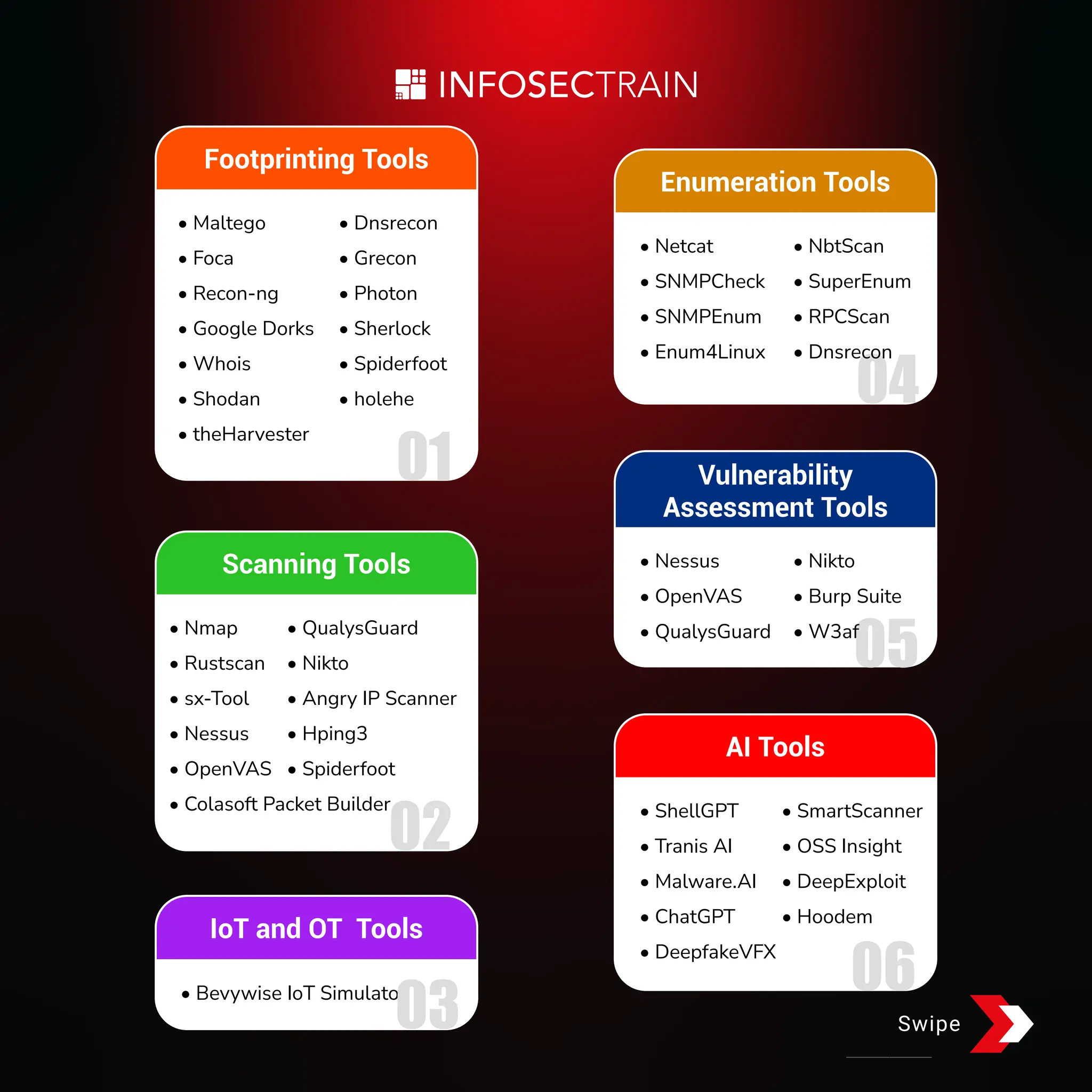
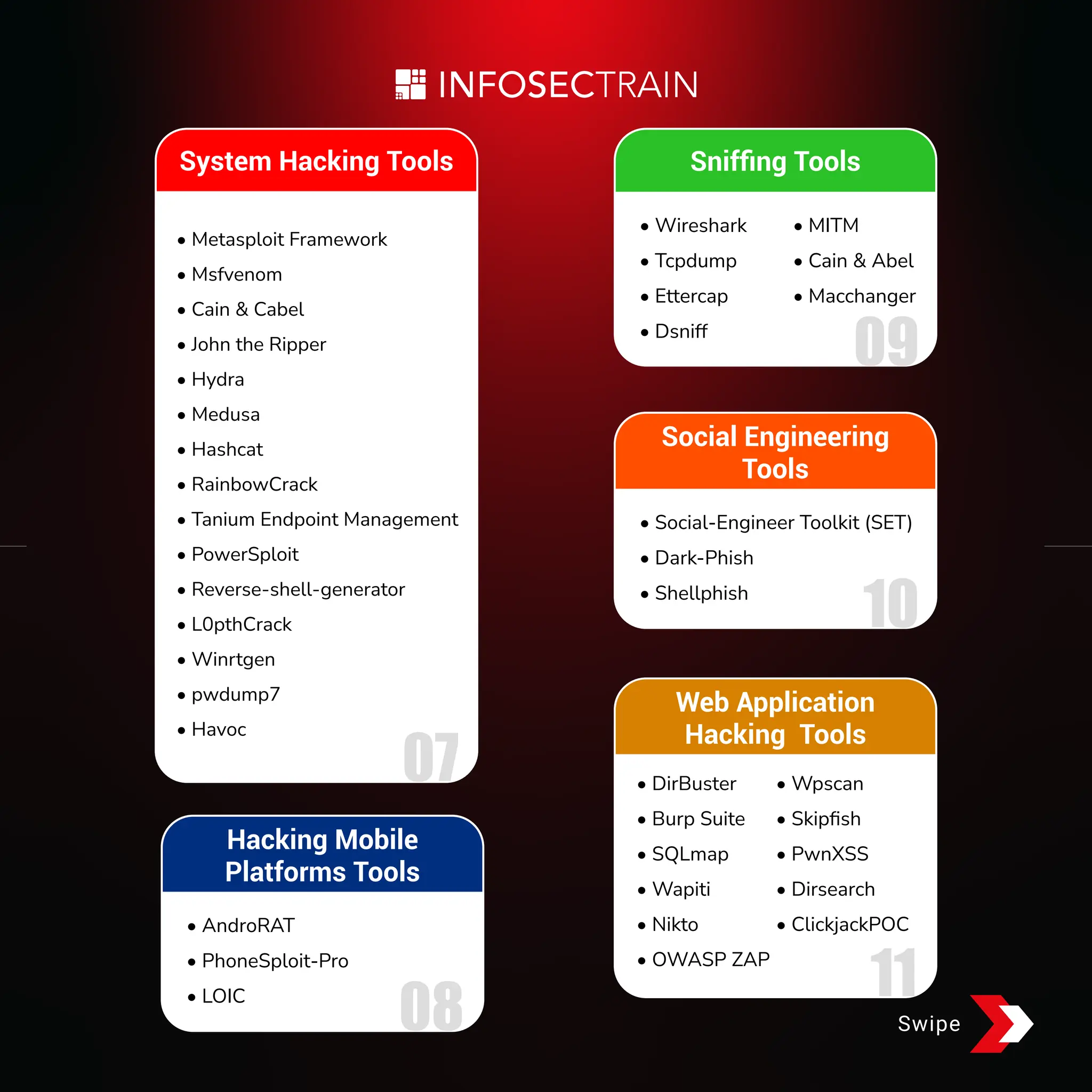
The document provides a comprehensive list of tools categorized by their use in vulnerability assessment, enumeration, IoT and OT, footprinting, AI, system hacking, sniffing, social engineering, web application hacking, mobile platform hacking, DoS, and more. Each category includes specific tools such as Nessus, Metasploit, and Wireshark, among others. Additionally, it promotes further learning through courses, workshops, and other resources.