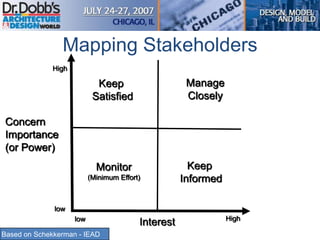
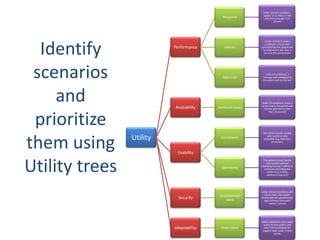
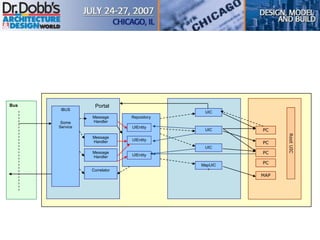
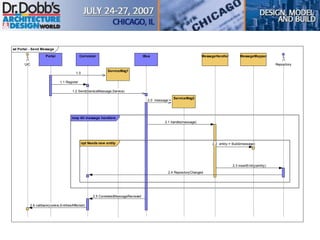
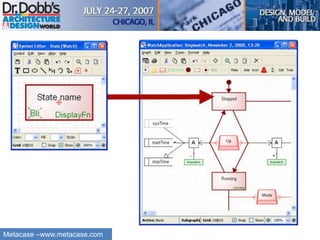
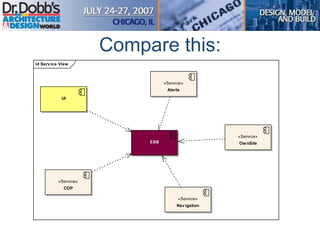
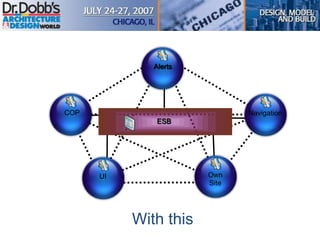
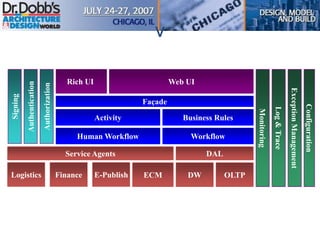
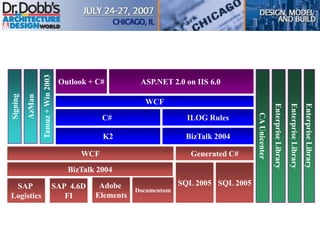
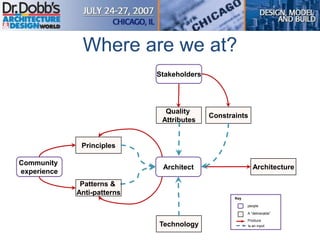
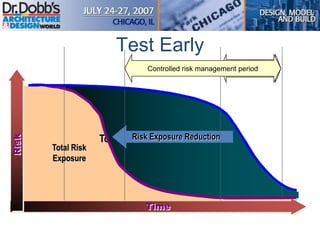
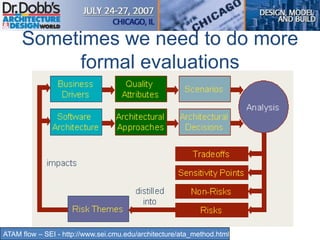
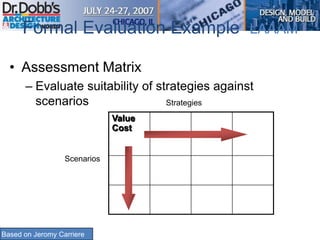
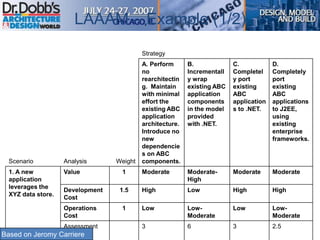
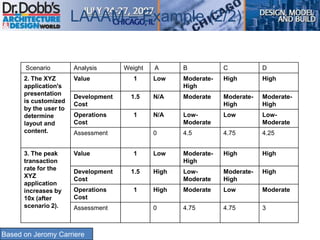
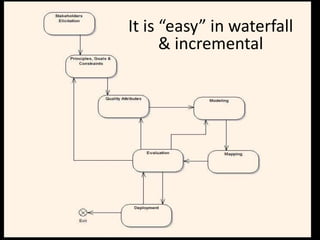
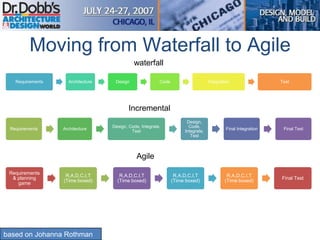
The document provides an overview of software architecture. It discusses key aspects of architecture including stakeholders, quality attributes, modeling, mapping to technologies, evaluation, and deployment. Stakeholders and quality attributes are important to consider early on. Various modeling techniques can be used to design the architecture. Formal evaluation methods help ensure the architecture meets quality goals. Both incremental and agile approaches can be taken to deploy the architecture in iterations. The architect plays an important role in all phases from initial design to deployment.