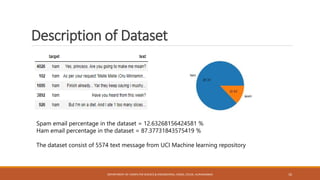
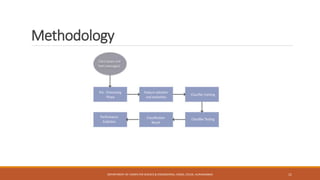
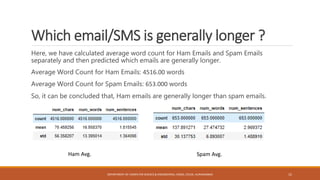
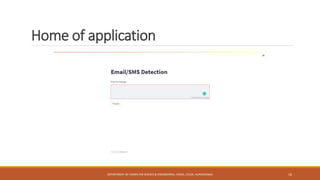
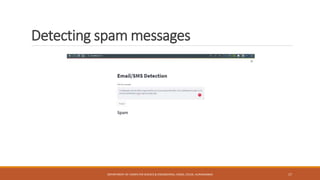
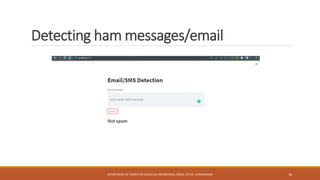
The seminar at CSMSS Chh. Shahu College of Engineering focused on email and SMS spam detection using machine learning techniques. It detailed the methodologies, algorithms, and technologies employed, including libraries such as NumPy and pandas, and highlighted the prevalence of spam in communication systems. The conclusion emphasizes the significant issue of spam, which poses security threats and impacts communication efficiency.