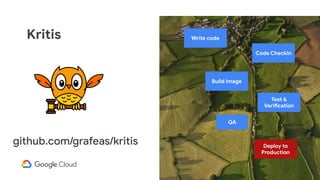
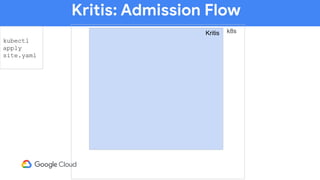
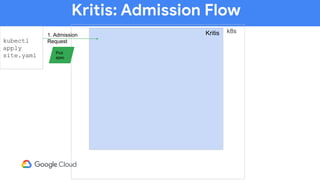
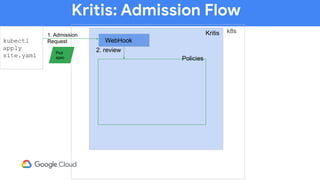
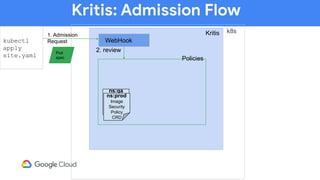
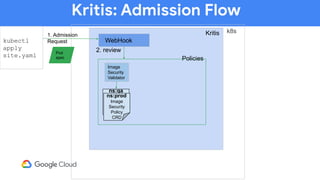
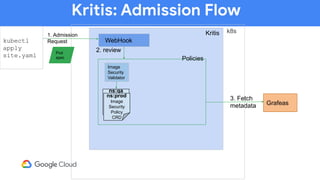
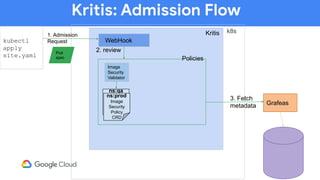
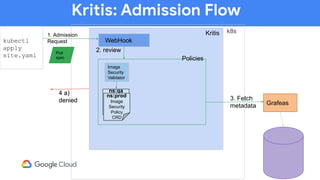
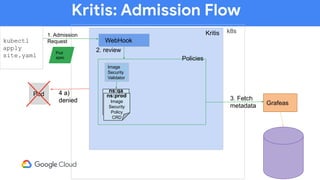
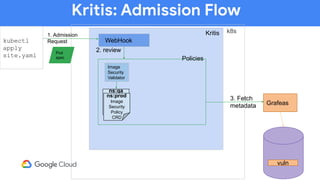
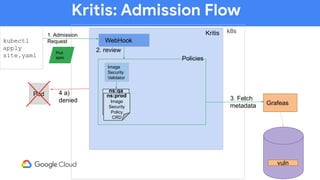
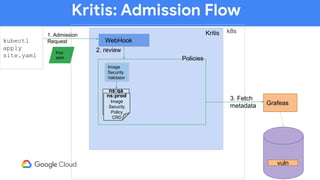
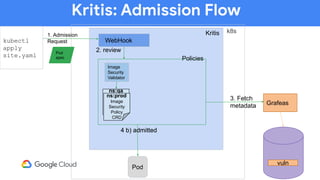
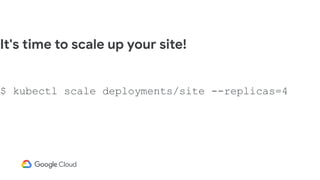
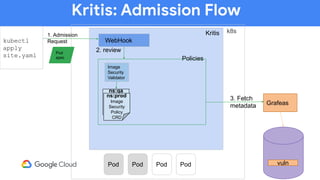
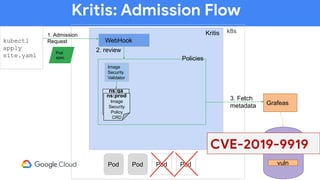
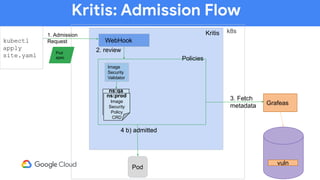
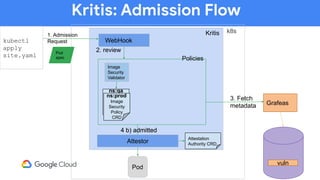
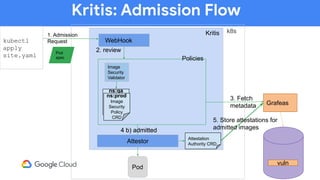
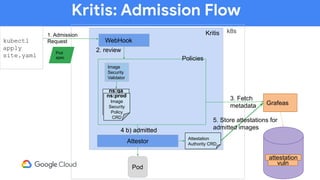
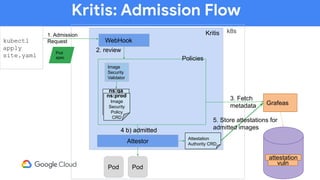
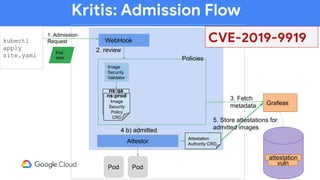
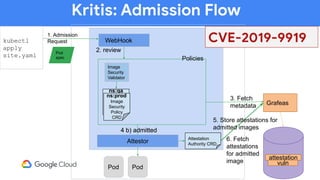
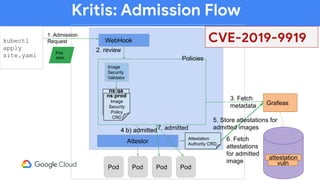
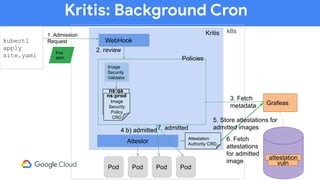
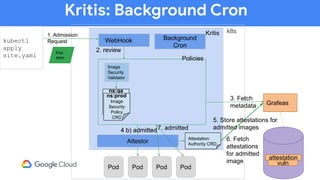
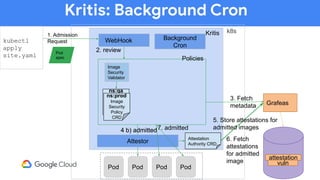
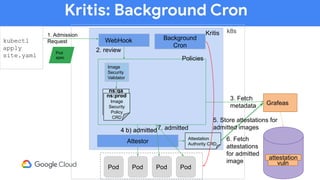
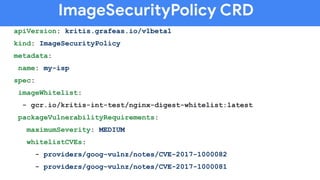
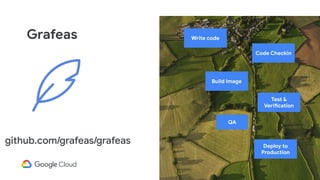
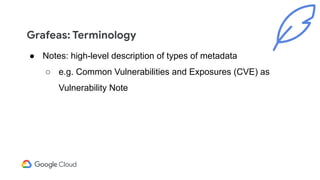
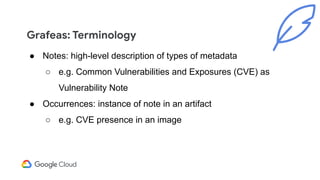
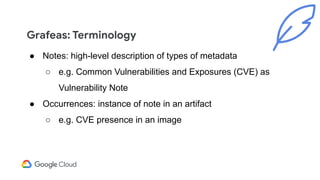
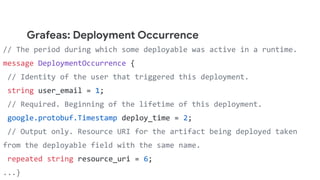
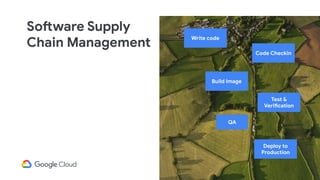
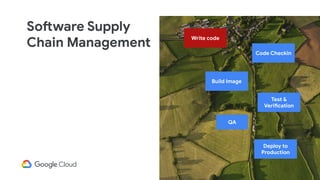
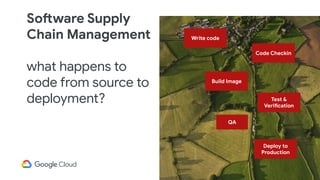
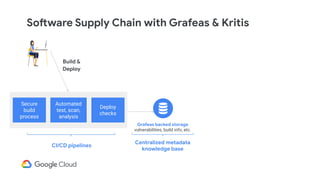
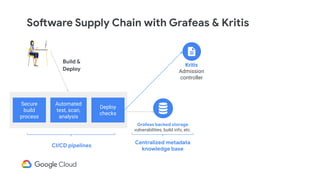
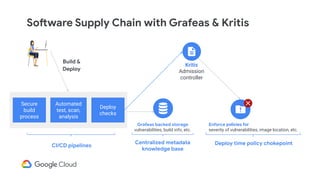
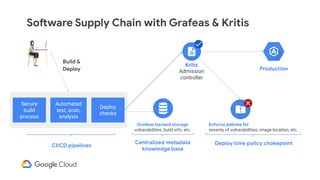
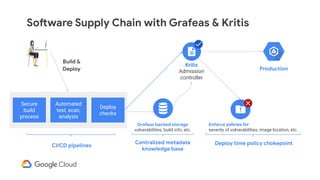
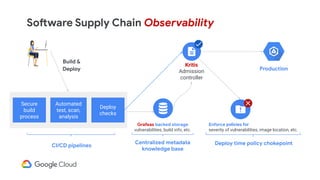
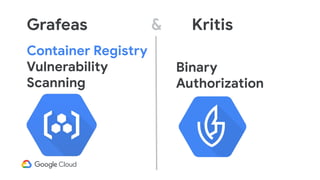
The document discusses software supply chain observability using Grafeas and Kritis, highlighting their roles in managing code from check-in to deployment through CI/CD pipelines. It details how Kritis enforces deployment policies related to security vulnerabilities and how Grafeas serves as a centralized metadata knowledge base for build information and vulnerabilities. The presentation emphasizes the importance of policy enforcement and vulnerability scanning in the secured deployment of software applications.









![Είναι όλα ελληνικά για μένα
[It's all Greek to me]](https://image.slidesharecdn.com/monitoramasoftwaresupplychainobservabilitywithgrafeasandkritis-190605182357/85/Software-Supply-Chain-Observability-with-Grafeas-and-Kritis-26-320.jpg)