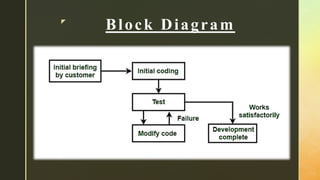
The document discusses the exploratory program development style, which is an informal approach allowing programmers to rely on intuition rather than systematic methodologies. This style, primarily used for small programs and by students, faces limitations including increased development time and costs, unmaintainable code, and challenges in team environments. The document highlights that this approach is mostly outdated and not favored in professional settings.