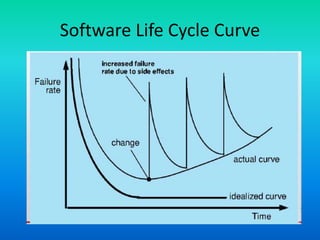
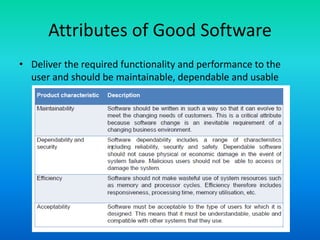
This document defines software and discusses key concepts in software engineering. It states that software includes computer programs, data structures, and documentation. Software products can be generic, sold to any customer, or customized to meet a specific customer's needs. The specification for generic products is owned by the developer, while customized product specifications are owned by the customer. Software engineering aims to develop software cost-effectively using appropriate theories, methods and tools across the entire software development life cycle.