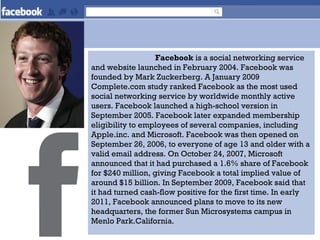
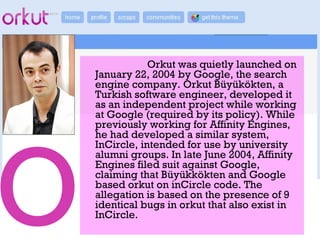
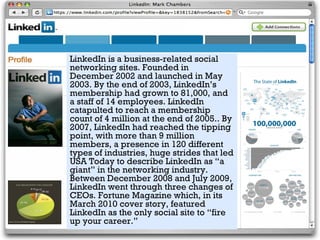
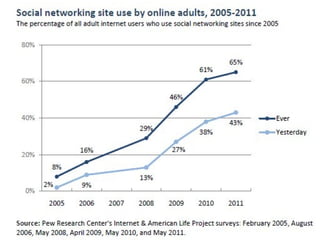
The document outlines the evolution and impact of various social networking sites, including Facebook, Twitter, and LinkedIn, detailing their founding, growth, and features. It highlights the rise in popularity of these platforms, their commercial use for advertising, and the risks involved, such as phishing, cyberstalking, and identity theft. It also offers precautions for users to safeguard their information while engaging on these sites.