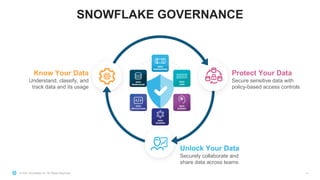
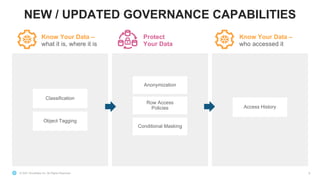
This document discusses Snowflake's data governance capabilities including challenges around data silos, complexity of data management, and balancing security and governance with data utilization. It provides an overview of Snowflake's platform for ingesting and sharing data across various sources and consumers. Key governance capabilities in Snowflake like object tagging, classification, anonymization, access history and row/column level policies are described. The document also previews upcoming conditional masking policies and provides examples of implementing object tagging and access policies in Snowflake.



![© 2021 Snowflake Inc. All Rights Reserved
PROTECT YOUR DATA
Anonymization
7
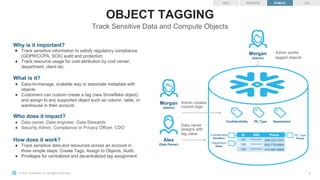
Data Owner creates
anonymized view
Alex
(Data Owner)
Customer Table
name gender age zip_code phone
John Smith male 39 79007 123-555-1234
Jane Doe female 50 77001 333-555-1236
Mary Taylor female 46 77020 222-333-1111
Michael Gaines male 37 79003 666-666-1357
Taylor
(Data Analyst)
name gender age zip_code phone
**** male [36-40] 790** ***-***-****
**** female [46-50] 770** ***-***-****
**** female [46-50] 770** ***-***-****
**** male [36-40] 790** ***-***-****
Anonymized View
Data Analyst queries
anonymized view
Admin defines
policies
Morgan
(Admin)
PUBLIC GA
PRIVATE
DEV
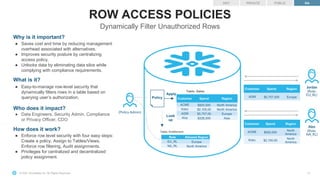
Why is it important?
● Risk management and compliance
● Retains analytical value
● Unique vs competitors (native anonymity)
What is it?
● An irreversible process of de-identifying data according to k-
Anonymity (industry standard)
Who does it impact?
● Data Owner, Data Engineer
● Security Admin, Compliance or Privacy Officer, CDO
● Data Analyst, Data Scientist
How does it work?
● Create an anonymized view that has the k-Anonymity
property
● Remove directly identifying information
● Generalize or suppress indirectly or quasi identifying
information into groups of at least size k](https://image.slidesharecdn.com/snowflakedatagovernancedeepdive81821-220819034138-8fc35d93/85/Snowflake-Data-Governance-7-320.jpg)


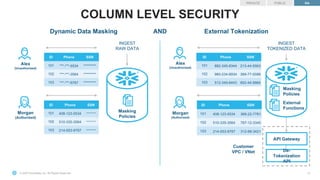

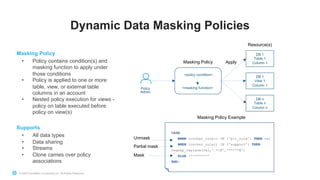

![© 2021 Snowflake Inc. All Rights Reserved
ALTER {TABLE | VIEW} <name> MODIFY COLUMN <col_name> [UN]SET MASKING
POLICY <name>;
Example:
ALTER TABLE customer MODIFY COLUMN email SET MASKING POLICY
email_mask;
ALTER VIEW customer_v MODIFY COLUMN email SET MASKING POLICY
email_mask;
Note: policies can also be applied to external tables.
Apply Masking Policy To Column(s)](https://image.slidesharecdn.com/snowflakedatagovernancedeepdive81821-220819034138-8fc35d93/85/Snowflake-Data-Governance-16-320.jpg)



