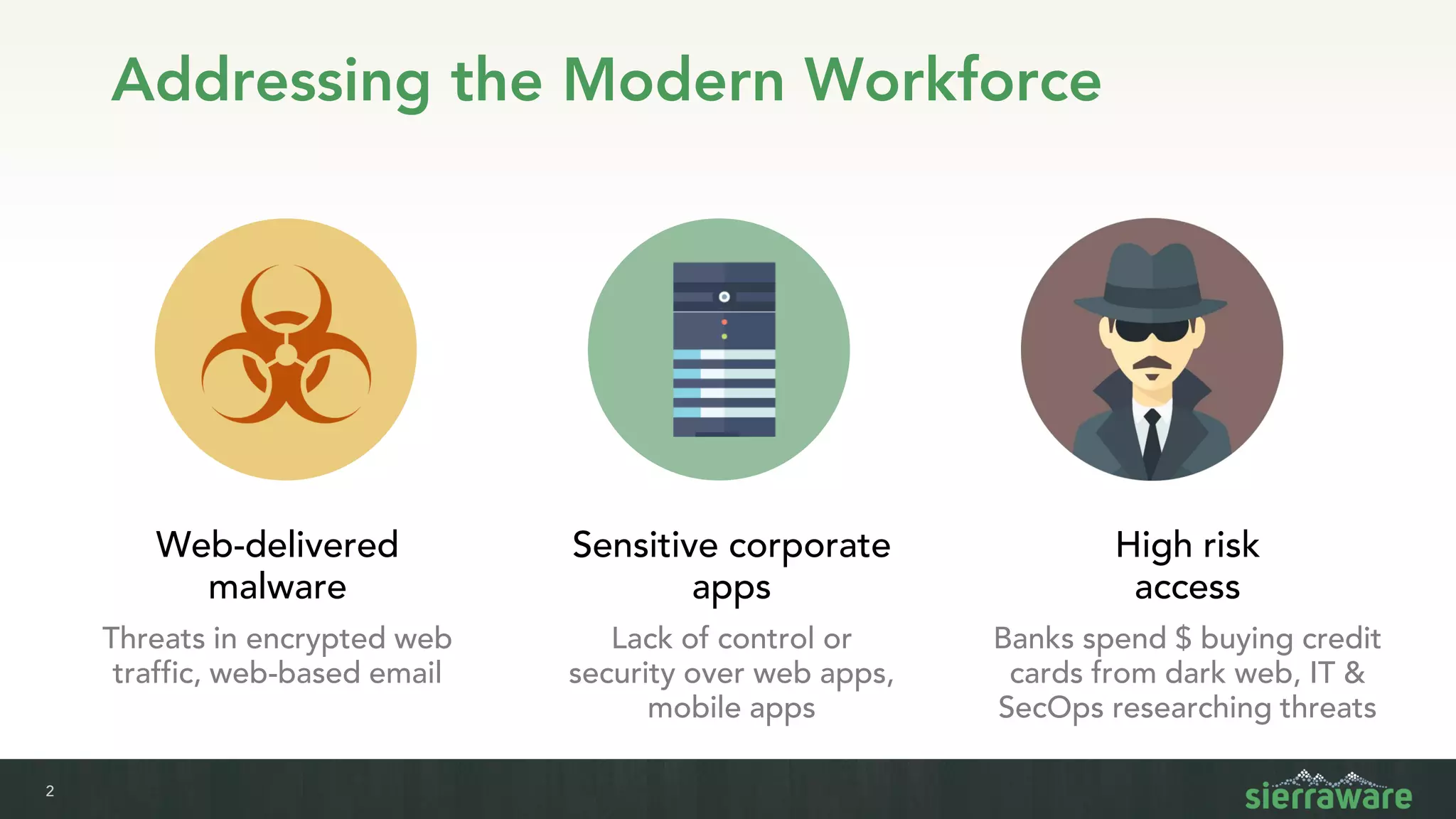
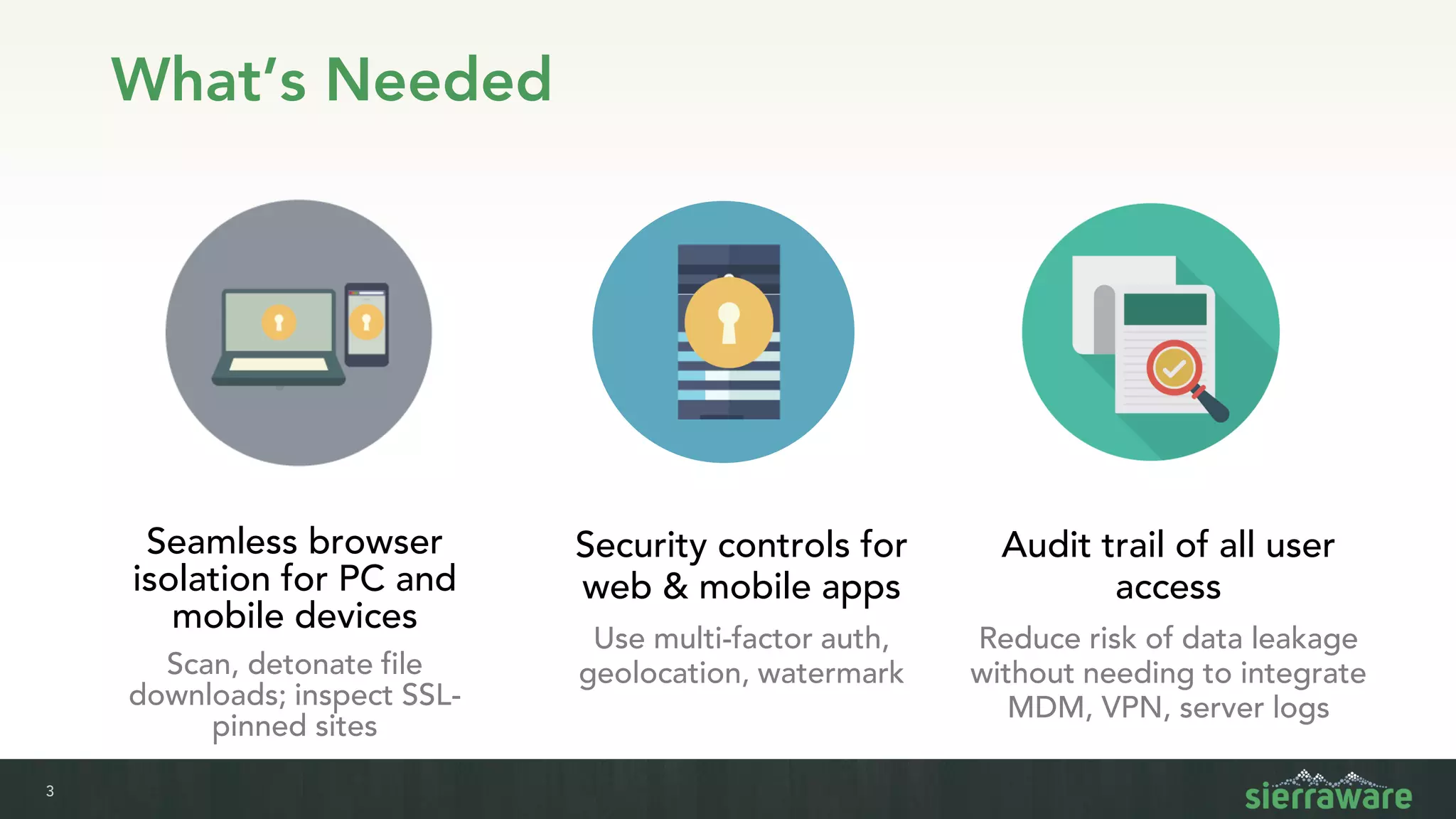
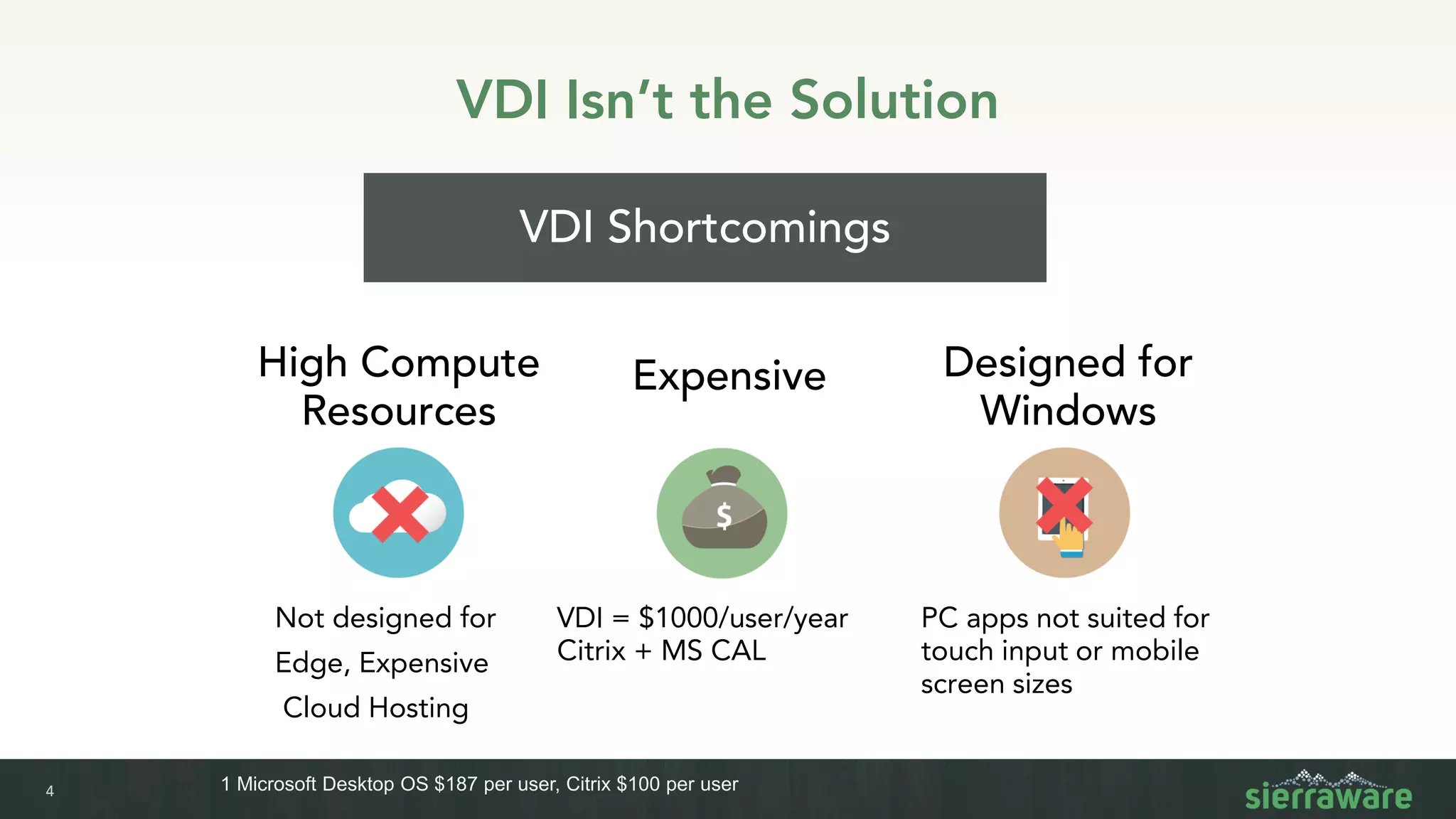
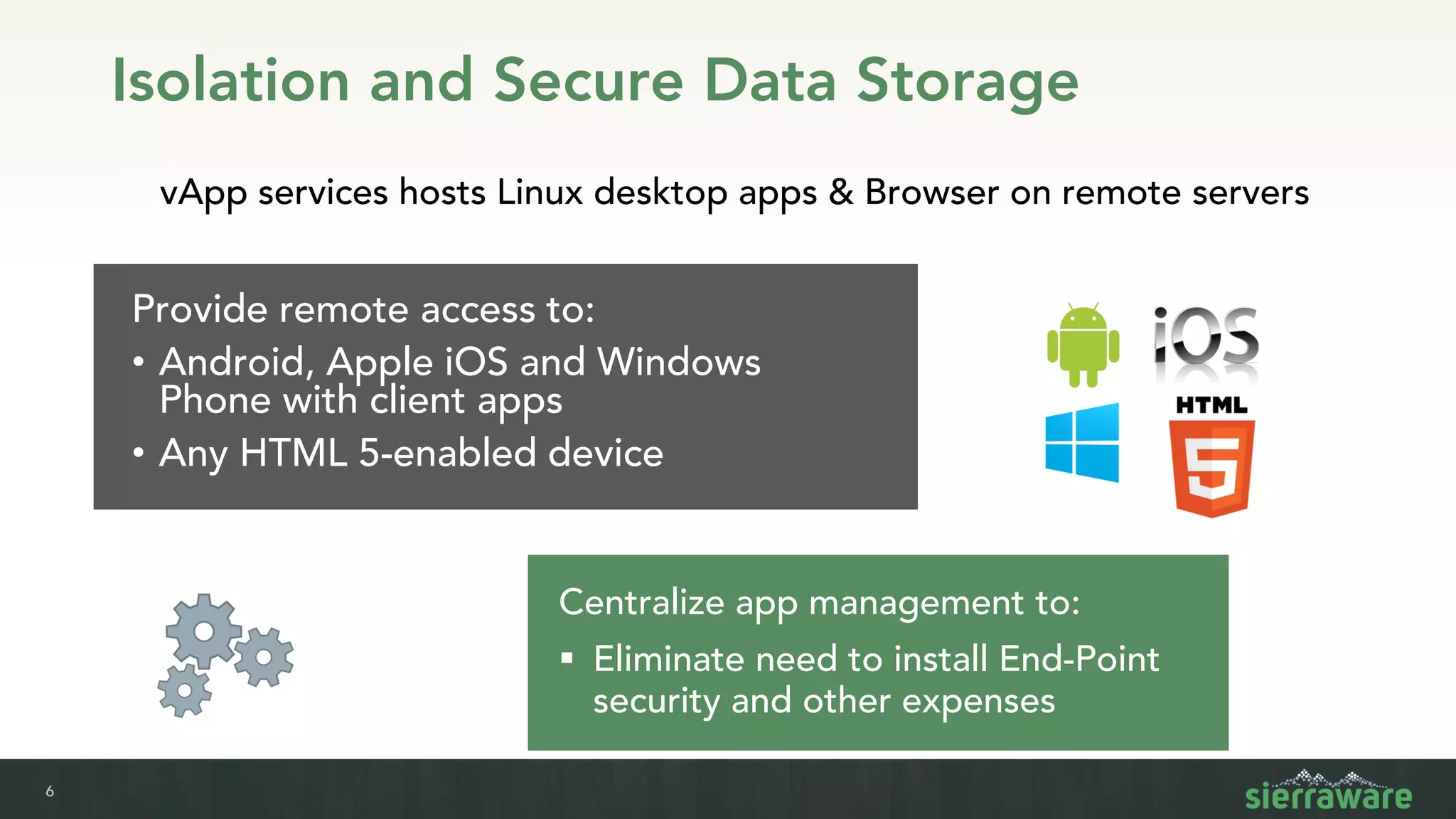
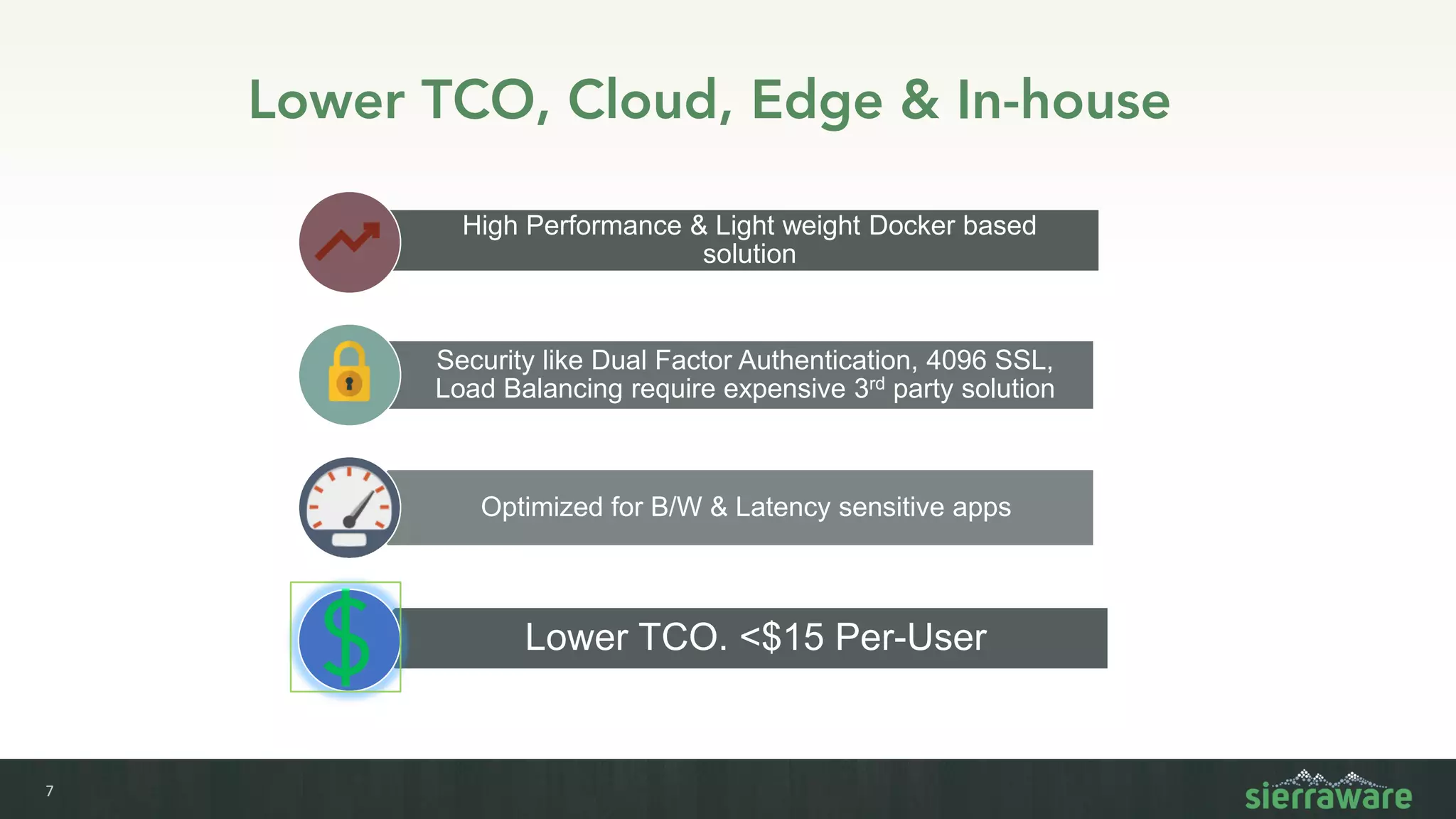
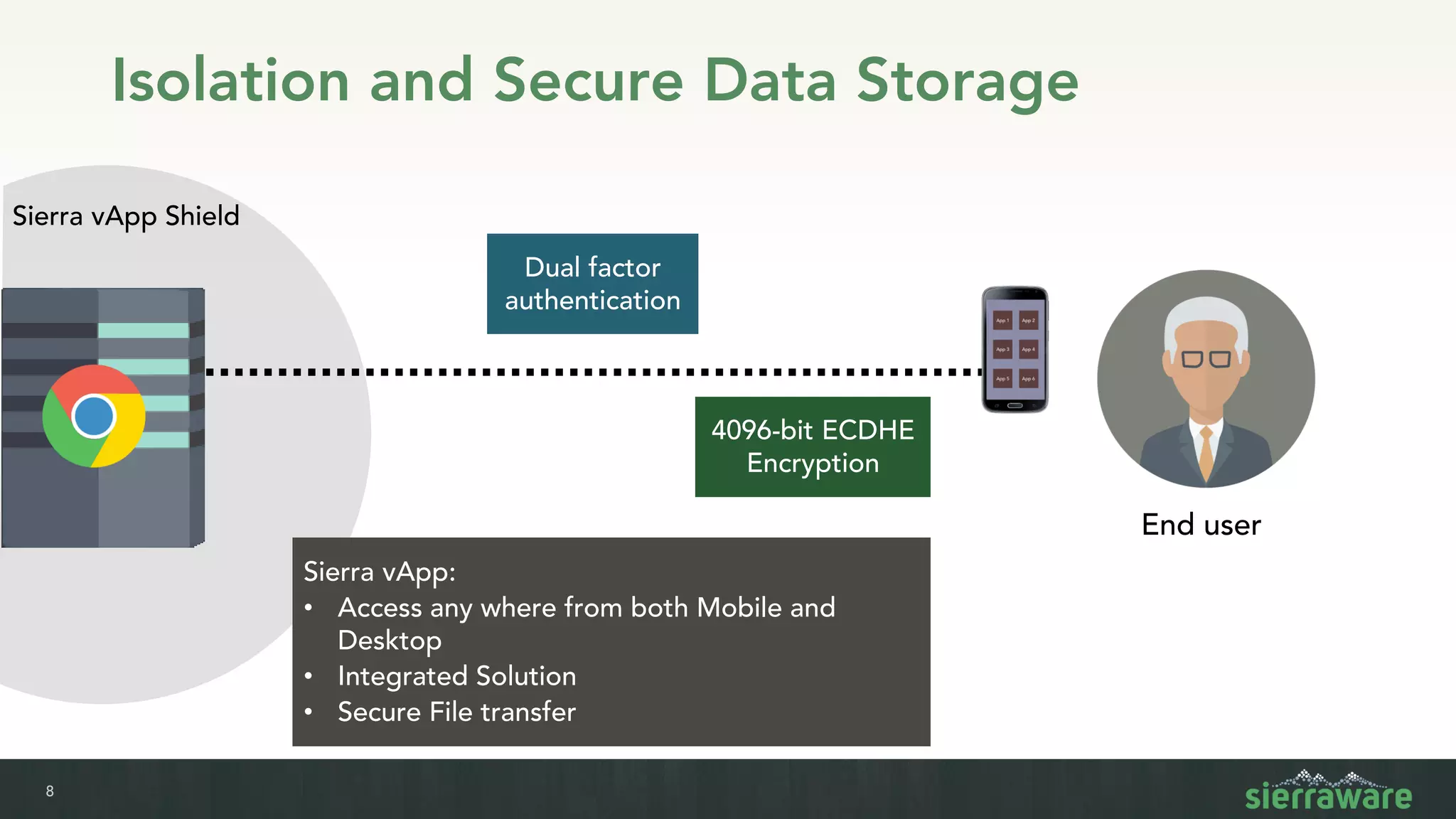
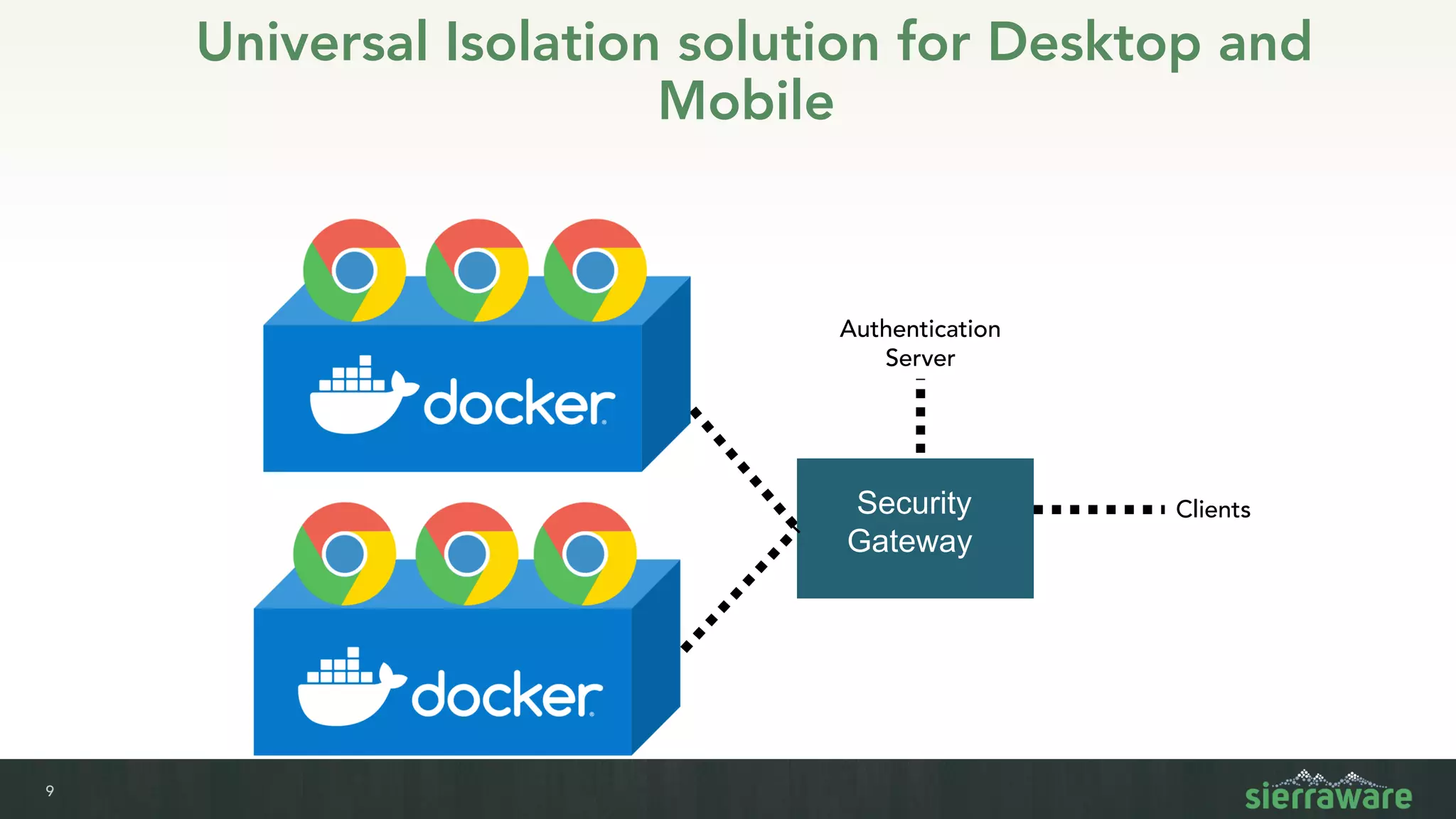
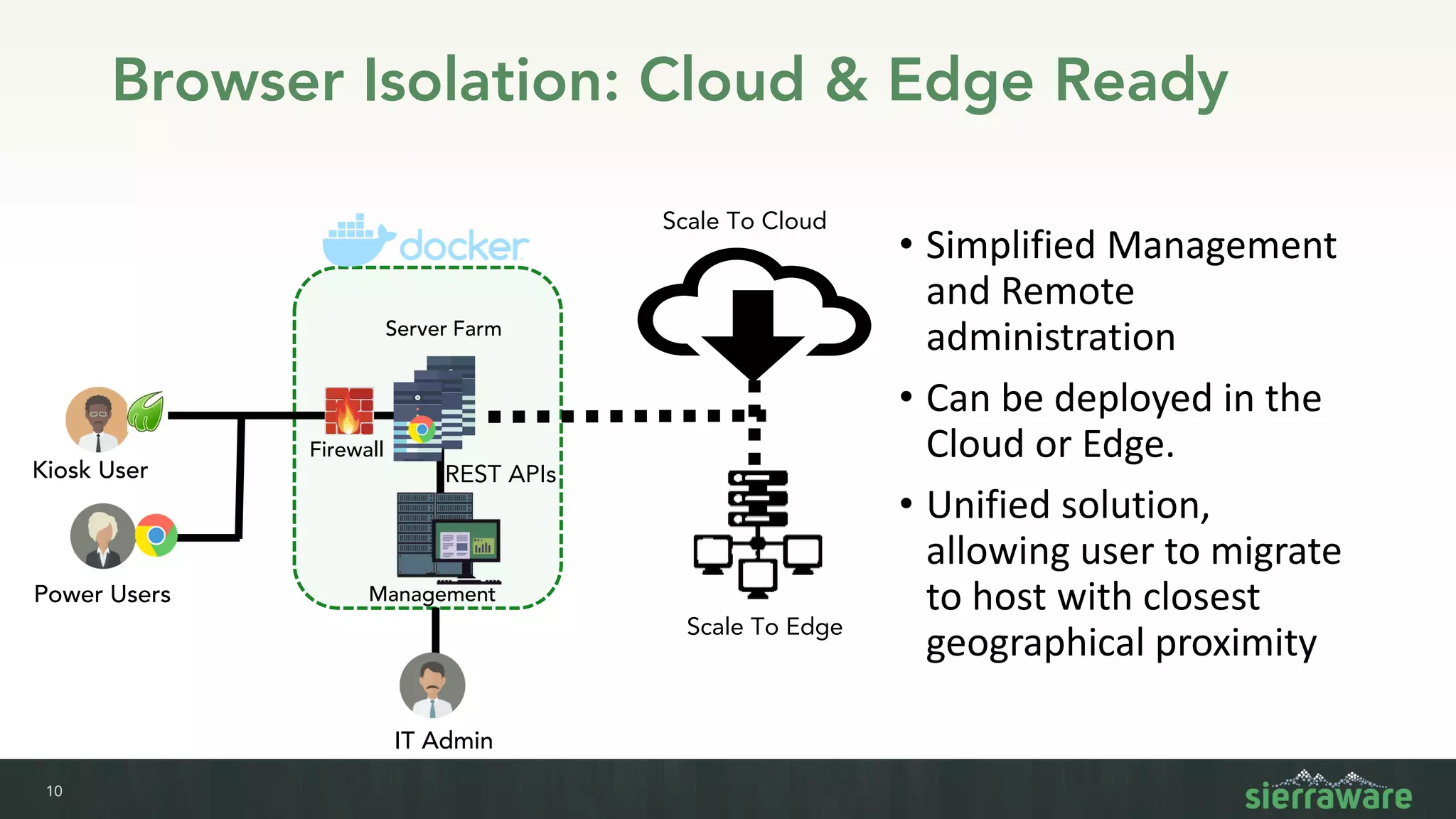
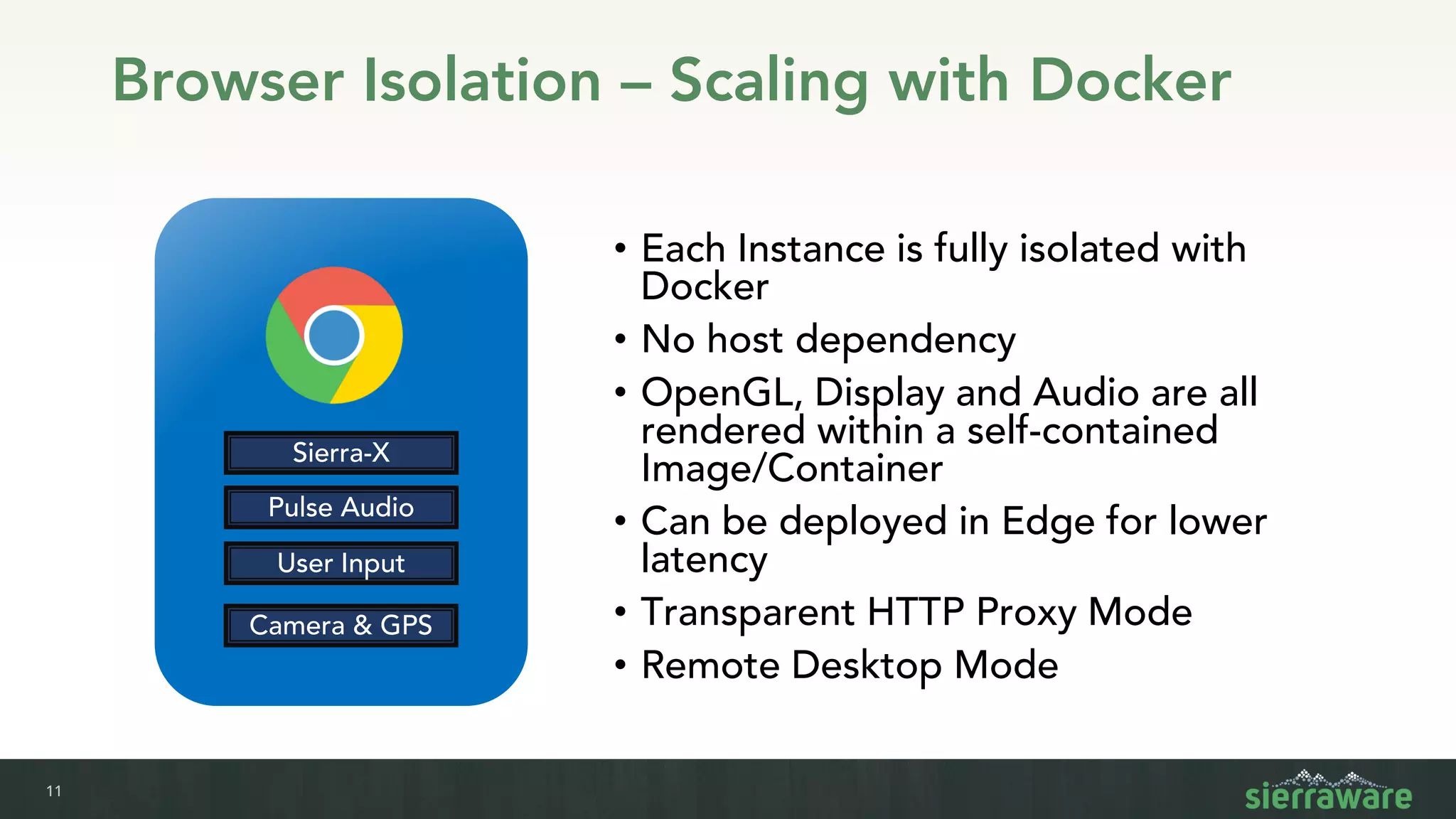
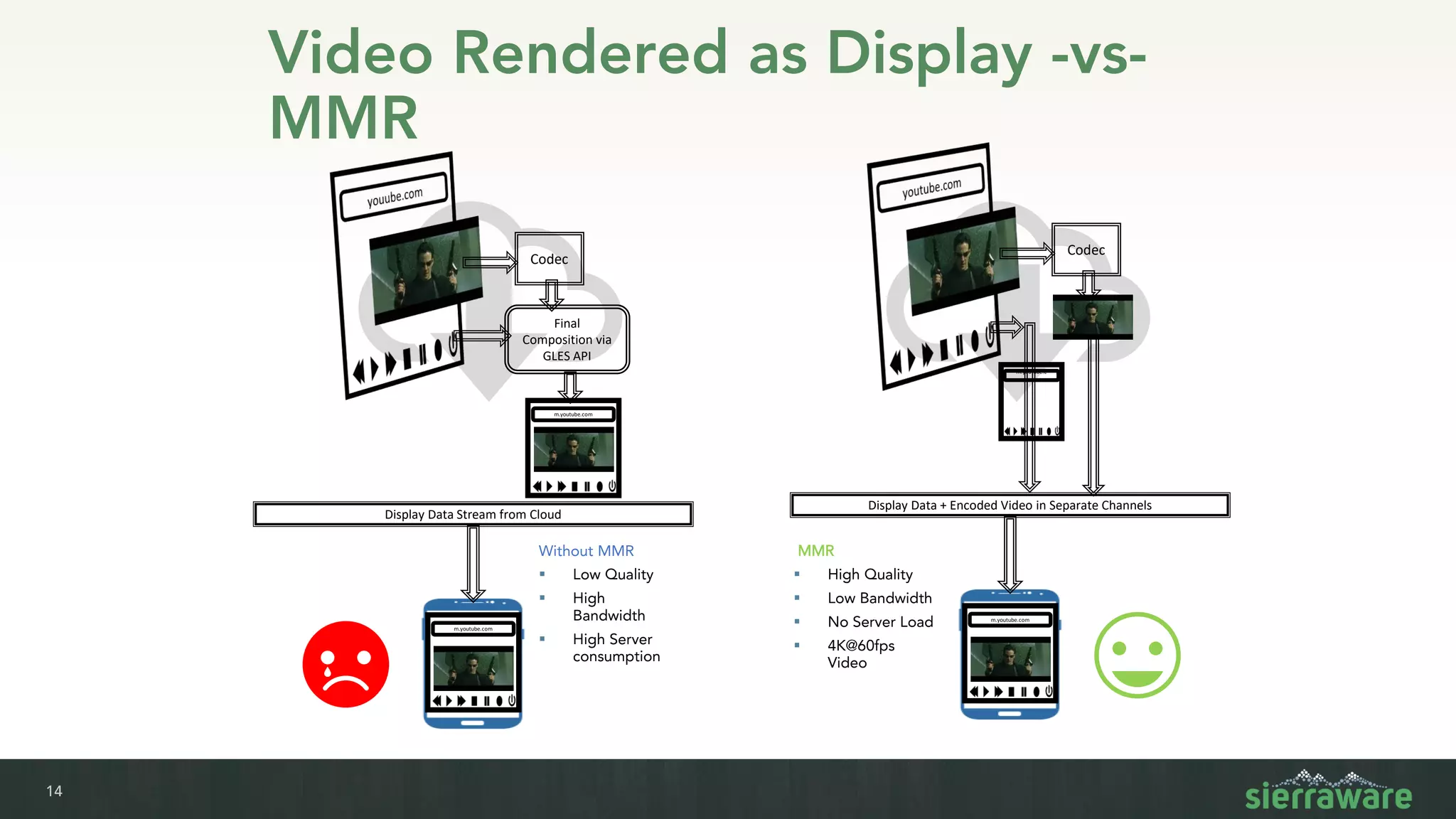
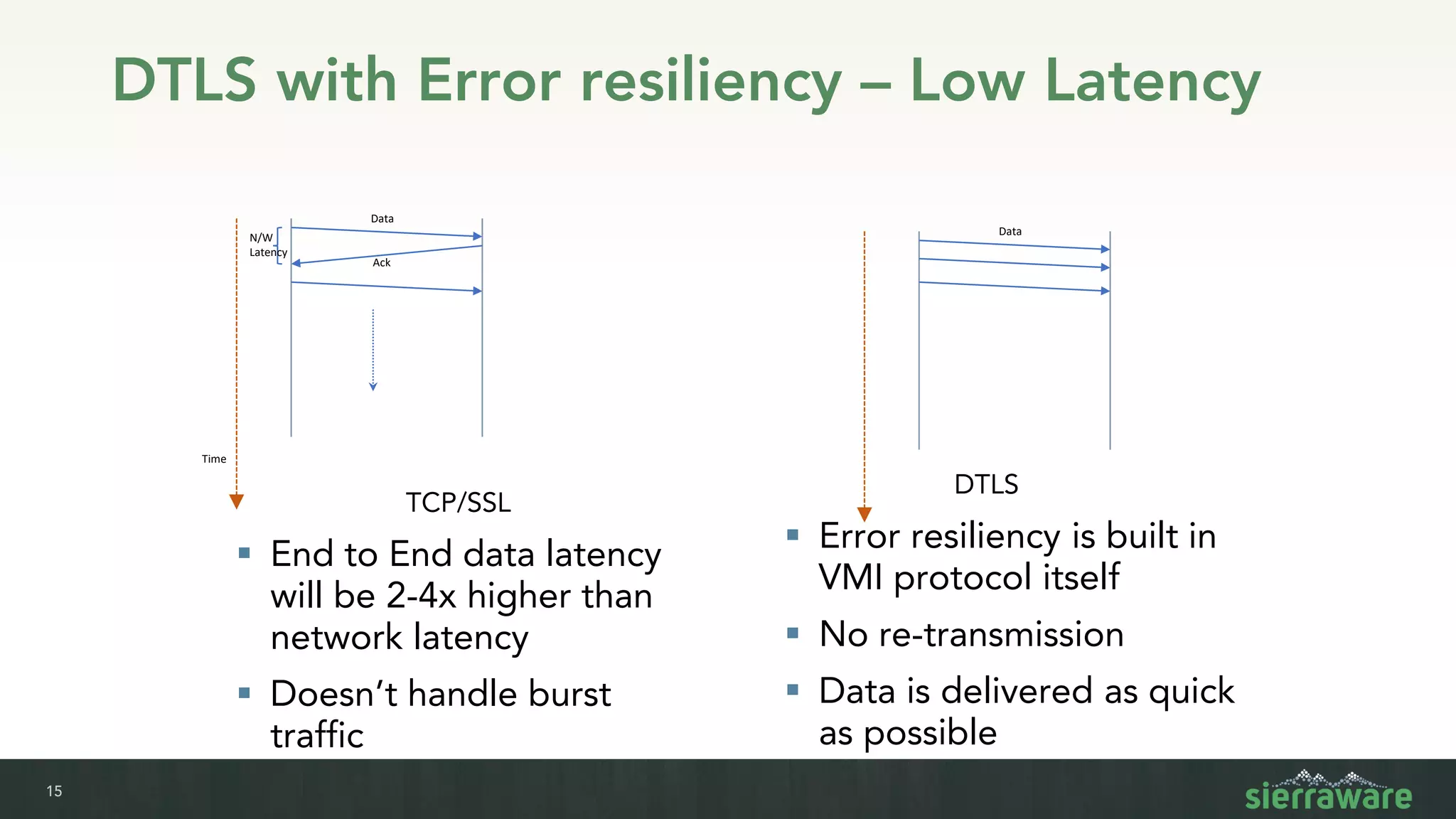
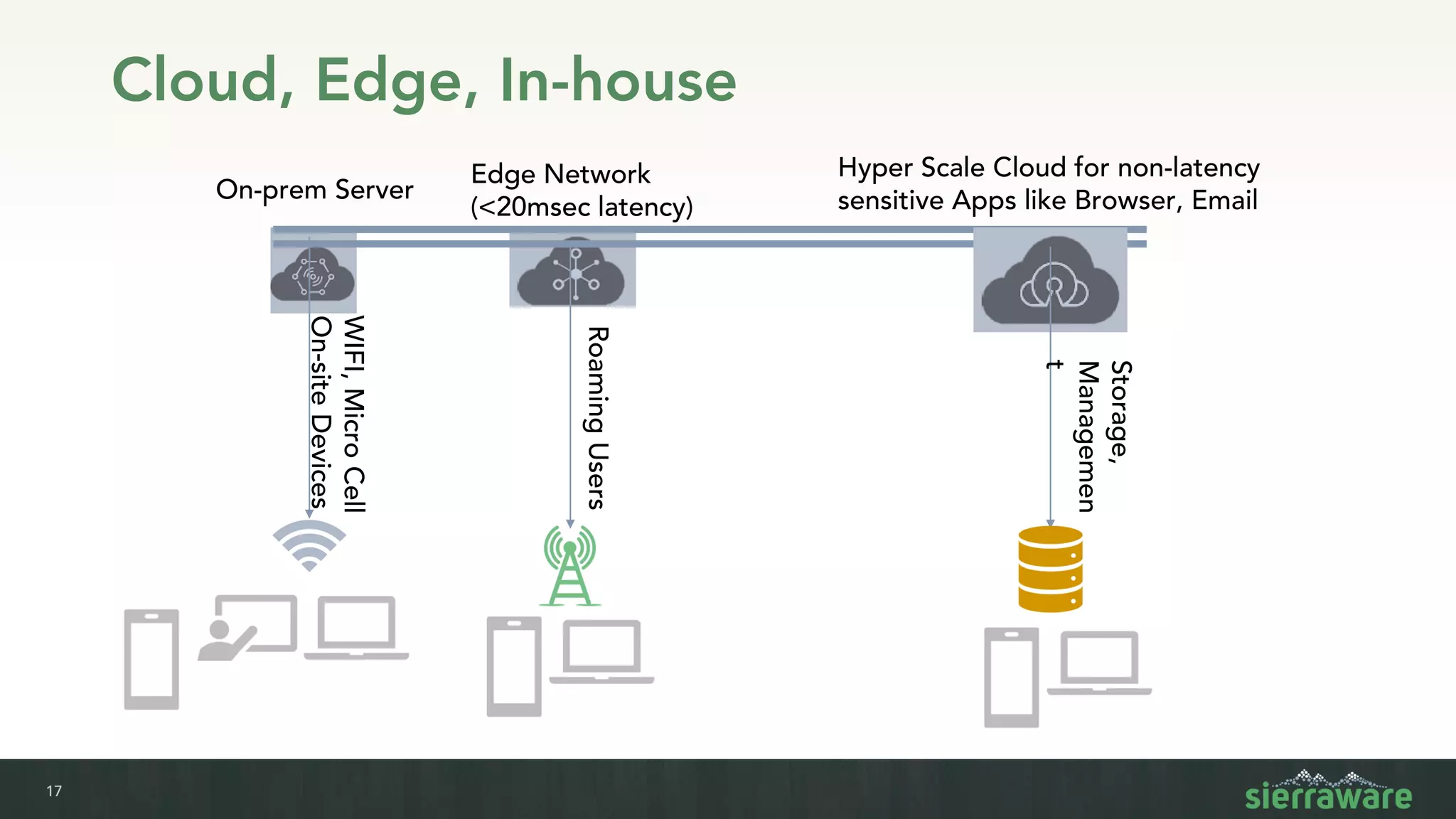
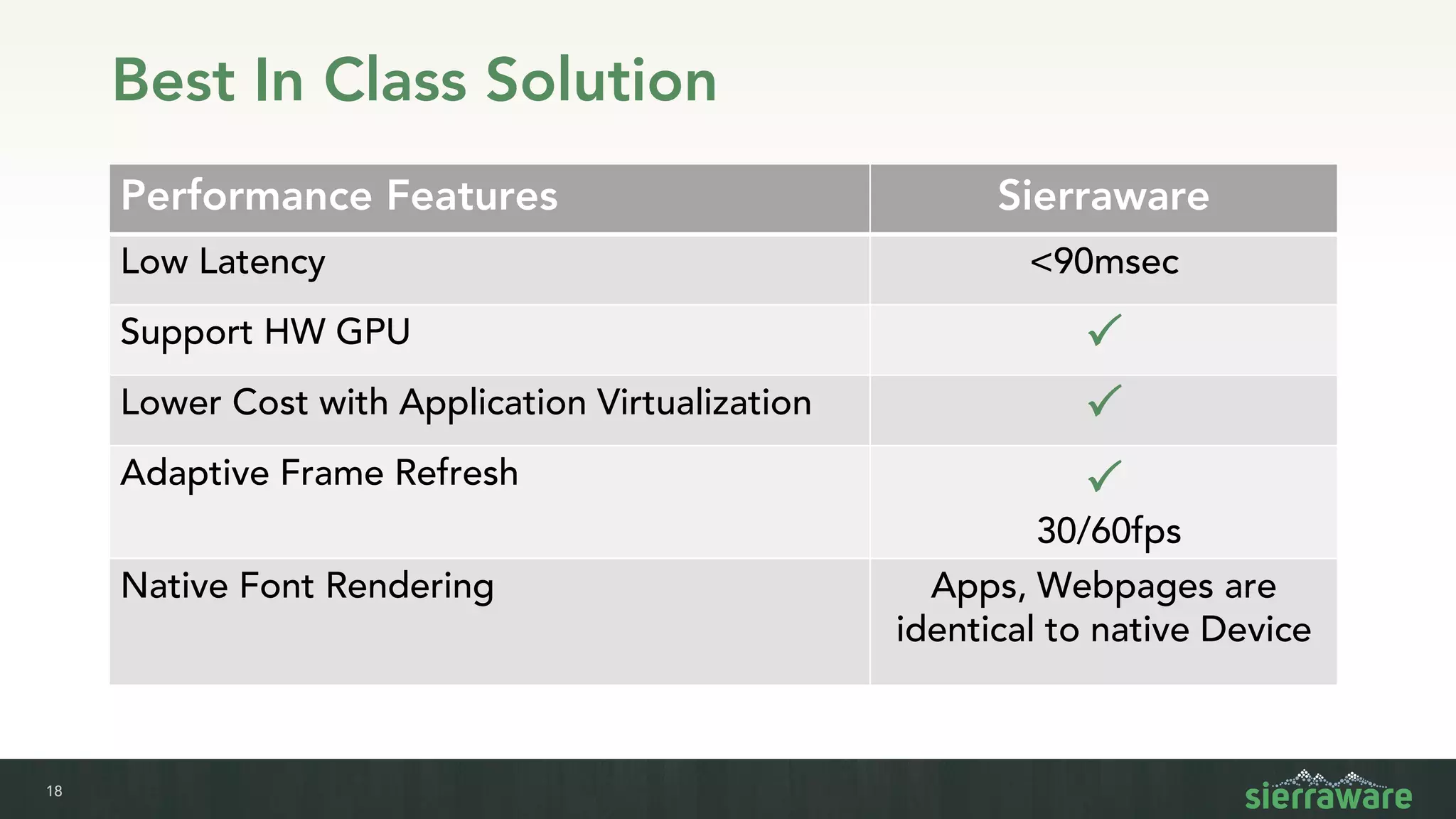
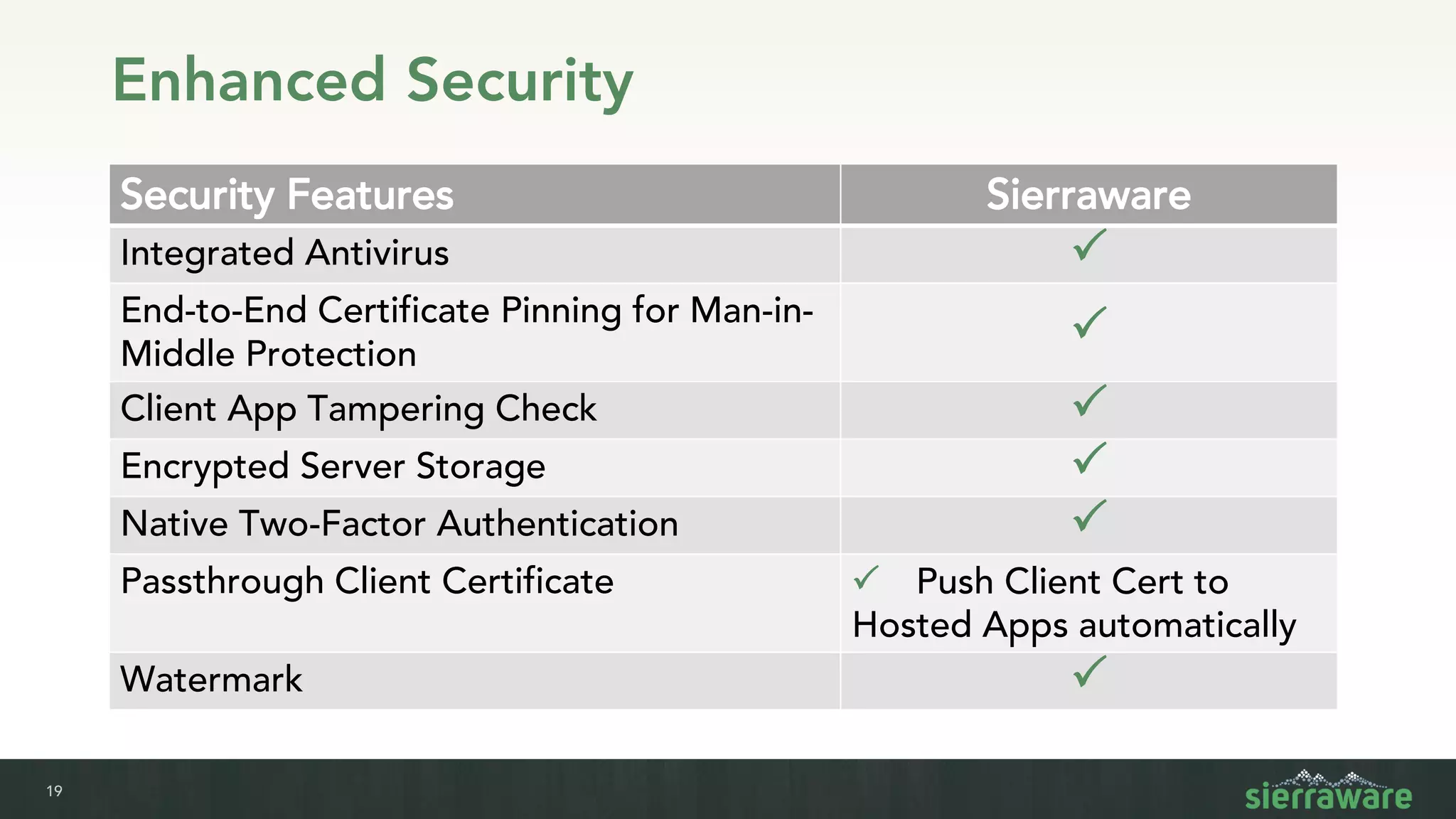
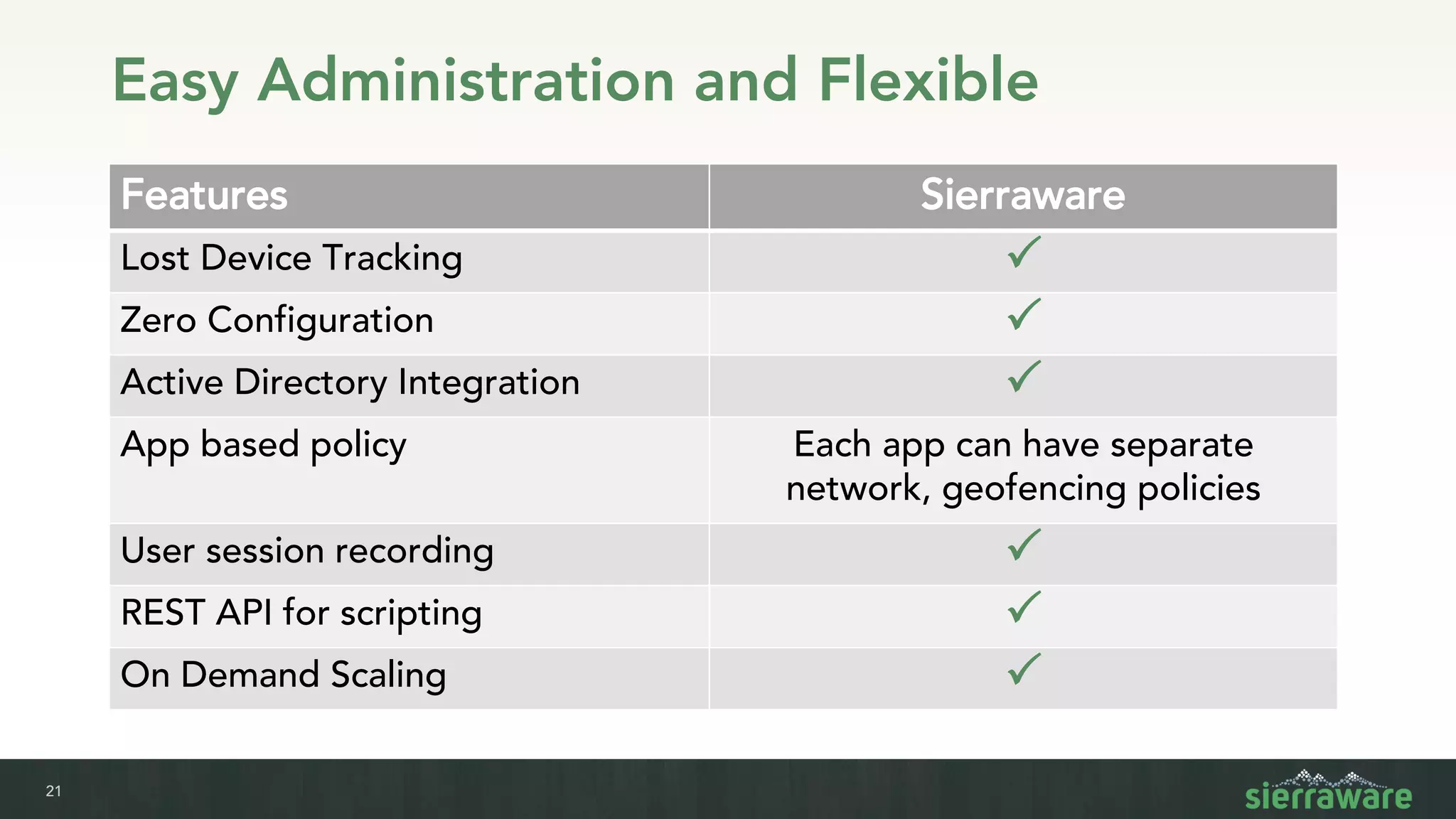
Sierra vApp provides browser isolation and secure remote access to desktop and mobile apps from any device. It addresses security issues with web-delivered threats and lack of control over web and mobile apps. Compared to VDI solutions, Sierra vApp has lower costs at under $15 per user, supports both mobile and desktop, and can be deployed on-premises or in the cloud/edge. It provides a seamless, secure experience across all devices with features like strong authentication, encryption, and isolation of sensitive data.