This document is a book about computer security for administrators and users of computer networks. It contains an introduction to computer security and operating systems. Some key points covered include definitions of hackers and operating systems, a brief history of operating systems, and an overview of security aspects of operating systems such as external security, internal security, processor security, memory security and file security. The document provides guidance on securing operating systems.



![6(*85,'$'20387$,21$/
7$%/$'(217(1,'2
7DEODGH,OXVWUDFLRQHV
/LVWDGH7DEODV
$*5$'(,0,(1726
352/2*2
,1752'8,Ï1
'HILQLFLyQGH+DFNHU
)iEXODSDUD+DFNHUV
.SHUXFLW#5RM#
,1752'8,Ï1$/266,67(0$623(5$7,926
,QWURGXFFLyQ
RPSXWDGRURPSXWDGRUD2UGHQDGRU
RQFHSWR
2UJDQL]DFLyQ,QWHUQDGHORPSXWDGRU
%UHYH+LVWRULDGHORV6LVWHPDV2SHUDWLYRV
'HILQLFLyQ(VWUXFWXUD)XQFLRQHVGHORV6LVWHPDV2SHUDWLYRV
6HJXULGDGHQORV6LVWHPDV2SHUDWLYRV
6HJXULGDGH[WHUQD
6HJXULGDG,QWHUQD
6HJXULGDGGHOSURFHVDGRU
6HJXULGDGGHODPHPRULD
6HJXULGDGGHORV$UFKLYRV
8Q VLVWHPDRSHUDWLYRVHULR
6LVWHPD2SHUDWLYR81,;
$QWHFHGHQWHVKLVWyULFRV
*HQHUDOLGDGHV
DUDFWHUtVWLFDVGHO6LVWHPD2SHUDWLYR81,;
(OHQWRUQRGHXVXDULR81,;
)LORVRItDHOHPHQWDOGH81,;
RPDQGRV)XQGDPHQWDOHVGH81,;
$XGDHQ/tQHDGHORVVLVWHPDV81,;
0RYLPLHQWRSRUILFKHURVGLUHFWRULRV
'LUHFWRULRVGHOVLVWHPD
2WURVFRPDQGRVXVXDOHV
3URWHFFLyQGH$UFKLYRV
DPELRGHODVFDGHQDVGHSHUPLVR
$548,7(785$ '(5('(6
(VWUXFWXUDHQQLYHOHV
/260$1'$0,(1726'(/$5('
/RVPDQGDPLHQWRVGHOXVXDULRGHODUHG
/RVPDQGDPLHQWRVGHODGPLQLVWUDGRUGHODUHG
,1752'8,Ï1$/$5,372/2*Ë$
$1È/,6,65(0272'(/266,67(0$6
,QWURGXFFLyQ
/RFDOL]DFLyQ
6HUYLGRUGH1RPEUHV16](https://image.slidesharecdn.com/2001-05-15seguridadcomputacionalrev2-110626155412-phpapp02/85/Seguridad-Computacional-4-320.jpg)



![)LUHZDOOEDMROLQX[VRSRUWDGRHQXQVLVWHPD %HRZXOI
$SOLFDFLRQHV
'HVFULSFLyQ
-XVWLILFDFLyQ
DVRVLQWHUQDFLRQDOHV
/D8QLYHUVLGDGGHORV$QGHVSUHVHQWH
7HVWGHVHJXULGDGFRPSXWDFLRQDOSDUDXVXDULRVGHODUHG
,39
/DFDEHFHUDGHO,SY
DPSRVTXHFRQWLHQHODFDEHFHUDSULQFLSDOGHO,SY
RPSUREDFLyQHQWUHHO,SYHO,SY
,SY
(67$'Ë67,$6,17(51$,21$/(6
(576WDWLVWLFV
'HWHFWLYHVHQVHJXULGDGFRPSXWDFLRQDO
$XPHQWDQODVSpUGLGDVILQDQFLHUDV
$XWRSVLDLQIRUPiWLFD
8QiUHDHQH[SDQVLyQ
*/26$5,2
%,%/,2*5$)Ë$
7DEODGH,OXVWUDFLRQHV
,OXVWUDFLyQ2UJDQL]DFLyQLQWHUQDGHORPSXWDGRU
,OXVWUDFLyQ%UHYH+LVWRULDGH/RV6LVWHPDV2SHUDWLYRV
,OXVWUDFLyQ7DEODSDUDGHVHQFULSWDUSULPHUGtJLWRHQKH[DGHFLPDO
,OXVWUDFLyQ7DEODSDUDGHVHQFULSWDUVHJXQGRGtJLWRHQ+H[DGHFLPDO
,OXVWUDFLyQ0RGHORSDUDXVDU6073
,OXVWUDFLyQDEHFHUDGH,39
,OXVWUDFLyQDEHFHUD,39
/LVWDGH7DEODV
7DEOD(MHPSORGH1LYHOHVGHXQ62
7DEOD1LYHOHV26,GH,62
7DEOD7LSRVGH6XEUHGHVHQ73,3
7DEOD0HWDVGH,39
7DEOD(VSDFLRGHGLUHFFLRQHV,39
7DEOD7LSRVGHFDEHFHUDGHH[WHQVLyQ,39
8QLYHUVLGDGGHODXFD](https://image.slidesharecdn.com/2001-05-15seguridadcomputacionalrev2-110626155412-phpapp02/85/Seguridad-Computacional-8-320.jpg)







![HV RWUD HVWUDWHJLD XWLOL]DGD SRU ORV YiQGDORV LQIRUPiWLFRV FRQVLVWH HQ
FRQVHJXLUODVFODYHVGHORVXVXDULRVKDFLpQGRVHSDVDUSRUHODGPLQLVWUDGRUGHODUHGRXQ
VLPSOH RSHUDGRU GH VX SURYHHGRU GH VHUYLFLR D ,QWHUQHW SDUD REWHQHU DFFHVR DODV
FXHQWDVGHORVWDQWRVXVXDULRVLQFDXWRVTXHFDHQDQWHHVWDHVWUDWHJLD
x (O HVSLRQDMH LQGXVWULDO VH KD FRQYHUWLGR HQ RWUR IDFWRU TXH DWDxH D OD
SUREOHPiWLFD GH OD VHJXULGDG FRPSXWDFLRQDO ODV GLIHUHQWHV WpFQLFDV FRPR HQWUDU GH
PDQHUDLOHJDODXQVHUYLGRUGHO'R''HSDUWPHQWRI'HIHQVHIURP86$](https://image.slidesharecdn.com/2001-05-15seguridadcomputacionalrev2-110626155412-phpapp02/85/Seguridad-Computacional-16-320.jpg)

![6(*85,'$'20387$,21$/
x $SURYHFKDU OD GHILFLHQWH DGPLQLVWUDFLyQ GH XQD UHG HV RWUD IRUPD GH REWHQHU
DFFHVRDORVUHFXUVRVFRPSXWDFLRQDOHVGHXQDHPSUHVDSRUSDUWHGHORVLQWUXVRVQLQJ~Q
VLVWHPDRSHUDWLYRHVWDH[LPLGRGHIDOORVGHVHJXULGDGSRUORWDQWRORVDGPLQLVWUDGRUHV
GHEHQHVWDUDWHQWRVDQWHODVQRWLFLDVDFWXDOL]DGDVGHIDOORVGHVHJXULGDGHQ FDGDXQRGH
ORV SURJUDPDV TXH WLHQHQ HQ VXV VHUYLGRUHV SDUD LQVWDODU ODV DFWXDOL]DFLRQHV GH ORV
PLVPRV R HQ VX GHIHFWR ORV SDUFKHV TXH FRQWURODQ ORV IDOORV GH VHJXULGDG D HVRV
SURJUDPDV
x /RVYLUXV HQPXFKDVRFDVLRQHVDFRPSDxDQDSURJUDPDVYLVWRVRV~WLOHVSHUR
SRFR FRQILDEOHV HQ ,QWHUQHW ORV JXVDQRV VRQ XQD FODVH GH YLUXV TXH SDUD SRGHU
GLIXQGLUVH FRQ PDRUHIHFWLYLGDG VLQTXHORVXVXDULRVORQRWHQXWLOL]DQODVGLUHFFLRQHV
GHFRUUHRTXHVHHQFXHQWUDQHQHOHTXLSRDIHFWDGRSDUDHQYLDUVHDXWRPiWLFDPHQWH
x )DOORVGHVHJXULGDGHQSURJUDPDVVHVXPDQDODDYDODQFKDGHSUREOHPDVDWHQHU
HQ FXHQWD FXDQGR GHVHDPRV TXH QXHVWUD LQIRUPDFLyQ VHD OD PiV VHJXUD (Q DOJXQDV
RFDVLRQHVFXDQGRHOIDOORQRHVLQWHQFLRQDOVHOHVOODPDEXJ XDQGRHVLQWHQFLRQDOVH
OHVOODPDSXHUWDVWUDVHUDVRWURDQRVGHSHQGLHQGRGHOVHUYLFLRTXHSUHVWHGLFKRIDOOR
x /RVYiQGDORVLQIRUPiWLFRVVRQORVPiVSHOLJURVRVGLUHFWDPHQWHUHVSRQVDEOHV
TXH OD VHJXULGDG FRPSXWDFLRQDO VHD HO WHPD GH PDRU LPSRUWDQFLD HQ OD FRPXQLGDG
,QWHUQHWDHVWRVLQGLYLGXRVVHOHVGHEHWHQHUFRPSOHWDPHQWHFRQWURODGRVDOHMDGRVGH
FXDOTXLHU UHG $FWXDOPHQWH OD OHJLVODFLyQ HQ RORPELD D~Q VH HQFXHQWUD GHVLHUWD FRQ
UHVSHFWRDHVWHWLSRGHWHPDVVLQHPEDUJRHQHOiPELWRPXQGLDODVHKDQWRPDGRORV
FRUUHFWLYRV DGHFXDGRV VH VDQFLRQDQ GH IRUPD HMHPSODU D HVWH WLSR GH GHOLQFXHQWHV
FDVRV UHQRPEUDGRV FRPR HO GH .HYLQ 0LWQLFN -RKQ 'UDSHU ,DQ 0XUSK .HYLQ
3RXOVHQHQWUHRWURV PXHVWUDQDODFRPXQLGDGGH,QWHUQHWHQJHQHUDOTXHVLVHYLRODQODV
OHHVHVWDVVHHQFDUJDUDQGHHOORV
(O DXJH GH ,QWHUQHW HO DYDQFH HQ ODV WHOHFRPXQLFDFLRQHV HQ HO KDUGZDUH GH ORV
FRPSXWDGRUHV KDQ VLGR LPSRUWDQWHV HQ ORV ~OWLPRV DxRV DEULHQGR XQD JUDQ SXHUWD GH
FRPXQLFDFLyQTXHSHUPLWHDFXDOTXLHUXVXDULRUHDOL]DUWRGRWLSRGHWUDQVDFFLRQHVHQIRUPD
UHPRWDVLQGHVSOD]DUVHGHXQVLWLRDRWUR(VWRQRKDVLGRSRVLWLYRGHOWRGRGHELGRDTXH
HVWDJUDQSXHUWDGHFRPXQLFDFLyQKDTXHGDGRDELHUWDWDPELpQSDUDWRGRWLSRGHSHUVRQDMHV
HQFDUJDGRV GH EXVFDU IDOORV HQ ORV VLVWHPDV GH LQIRUPDFLyQ DSURYHFKiQGRVH GH HOORV
ORJUDQ DYHULJXDU GHVGH VXV GDWRV SHUVRQDOHV KDVWD ORV Q~PHURV GH ODV WDUMHWDV GH FUpGLWR
FXHQWDVEDQFDULDVWRGRWLSRGHLQIRUPDFLyQTXHOHVSXHGDFDXVDUDOJ~QWLSRGHEHQHILFLR
DGHPiV VH OOHYDQ WRGDV ODV FRQWUDVHxDV GHO XVXDULR VLQ REYLDPHQWH ROYLGDU GHMDU HQ HO
HTXLSRGHOLQFDXWRXQDSXHUWDWUDVHUDSRUPHGLRGHODFXDOHODWDFDQWHYDSRGHUHQWUDUWDQWDV
YHFHV TXLHUD HQ XQ IXWXUR 'HELGR D HVWR ODV QDFLRQHV GHO PXQGR KDQ FHQWUDGR VXV
HVIXHU]RV DO IRUWDOHFLPLHQWRGHODVHJXULGDGHQVXVUHGHVLQWHUQDVVLQHPEDUJRHVWRQRKD
VLGR VXILFLHQWH /D XQLYHUVLGDG GHO DXFD D WUDYpV GH VX SURJUDPD GH ,QJHQLHUtD GH
6LVWHPDVKDFUHDGRXQJUXSRGHLQYHVWLJDFLyQ*7,*UXSRGH7HFQRORJtDV,QWHUQHW](https://image.slidesharecdn.com/2001-05-15seguridadcomputacionalrev2-110626155412-phpapp02/85/Seguridad-Computacional-18-320.jpg)

![6(*85,'$'20387$,21$/
'HILQLFLyQGH+DFNHU
(ODUFKLYRGHODMHUJDFRQWLHQHYDULDVGHILQLFLRQHVGHOWpUPLQR³KDFNHU´ODPDRUtDGH
ODV FXDOHV WLHQH TXH YHUFRQ OD DILFLyQ D OR WpFQLFR OD FDSDFLGDG GH GHOHLWDUVH FRQ OD
VROXFLyQ GH SUREOHPDV D VREUHSDVDUORV OtPLWHV 6L XVWHG TXLHUHVDEHUFRPR WUDEDMDQ
ORVKDFNHUVVLJDOHHQGRHVWHWH[WRVHGDUiFXHQWDTXHQRHVWDQIiFLO
([LVWHXQDFRPXQLGDGXQDFXOWXUDFRPSDUWLGDGHSURJUDPDGRUHVH[SHUWRVEUXMRVGH
UHGHV TXH FXD KLVWRULD VH SXHGH UDVWUHDU GpFDGDV DWUiV KDVWD ODV SULPHUDV
PLQLFRPSXWDGRUDV GH WLHPSR FRPSDUWLGR ORV SULPHURV H[SHULPHQWRV GH $53$QHW
/RV PLHPEURVGHHVWDFXOWXUDDFXxDURQHOWpUPLQR³KDFNHU´/RV KDFNHUVFRQVWUXHURQ
,QWHUQHW /RV KDFNHUV KLFLHURQ GHO VLVWHPD RSHUDWLYR 81,;OR TXH HV HQ OD DFWXDOLGDG
/RVKDFNHUVKDFHQDQGDU8VHQHW/RVKDFNHUVKDFHQTXHIXQFLRQHOD:::6LXVWHGHV
SDUWH GH HVWD FXOWXUD VL XVWHG KD FRQWULEXLGR D HOOD RWUD JHQWH OR OODPD KDFNHU
HQWRQFHVXVWHGHVXQKDFNHU
/D PHQWDOLGDG GH KDFNHUQRHVWiFRQILQDGDDHVWDFXOWXUDGHKDFNHUVHQVRIWZDUH+D
SHUVRQDVTXH DSOLFDQOD DFWLWXG GH KDFNHUD RWUDVFRVDVFRPRHOHFWUyQLFDRP~VLFDGH
KHFKRSXHGHXVWHGHQFRQWUDUODHQORVPiVDOWRVQLYHOHVGHFXDOTXLHUFLHQFLDRDUWH/RV
KDFNHUVHQVRIWZDUHUHFRQRFHQHVWRVHVStULWXVHPSDUHQWDGRVORVGHQRPLQDQ³KDFNHUV´
WDPELpQDOJXQRVVRVWLHQHQTXHODQDWXUDOH]D GHKDFNHUHVHQUHDOLGDGLQGHSHQGLHQWH
GHO PHGLR SDUWLFXODU HQ HO FXDO HO KDFNHU WUDEDMD (Q HO UHVWR GH HVWH GRFXPHQWR QRV
FRQFHQWUDUHPRV FRQ ODV KDELOLGDGHV DFWLWXGHV GH ORV KDFNHUV HQ VRIWZDUH HQ ODV
WUDGLFLRQHVGHODFXOWXUDFRPSDUWLGDTXHRULJLQyHOWpUPLQR³KDFNHU´
([LVWH RWUR JUXSR GH SHUVRQDV TXH D ORV JULWRV VH DXWR GHQRPLQDQ KDFNHUV SHUR QROR
VRQ eVWDV VRQ SHUVRQDV SULQFLSDOPHQWH YDURQHV DGROHVFHQWHV](https://image.slidesharecdn.com/2001-05-15seguridadcomputacionalrev2-110626155412-phpapp02/85/Seguridad-Computacional-20-320.jpg)
![TXH VH GLYLHUWHQ
LQJUHVDQGR LOHJDOPHQWH HQ FRPSXWDGRUDV HVWDIDQGR DO VLVWHPD GH WHOHIRQtD /RV
KDFNHUVGHYHUGDGWLHQHQXQQRPEUHSDUDHVDVSHUVRQDV³FUDFNHUV´QRTXLHUHQVDEHU
QDGD FRQ HOORV /RV KDFNHUV GH YHUGDG RSLQDQ TXH OD PDRUtD GH ORV FUDFNHUV VRQ
SHUH]RVRVLUUHVSRQVDEOHVQRPXEULOODQWHVIXQGDPHQWDQVXFUtWLFDHQTXHVHUFDSD]
GHURPSHUODVHJXULGDGQR ORKDFHDXQRXQKDFNHUGHODPLVPDPDQHUDTXHVHUFDSD]
GHHQFHQGHUXQDXWRFRQXQSXHQWHHQODOODYHQRORSXHGHWUDQVIRUPDUHQLQJHQLHURGH
DXWRPRWRUHV 'HVDIRUWXQDGDPHQWHPXFKRVSHULRGLVWDVHGLWRUHVXWLOL]DQHUUyQHDPHQWH
ODSDODEUD³KDFNHU´SDUDGHVFULELUDORVFUDFNHUV(VWRHVFDXVDGHHQRUPHLUULWDFLyQSDUD
ORVYHUGDGHURVKDFNHUV
/D GLIHUHQFLD EiVLFD HVWi HQ TXH ORV KDFNHUV FRQVWUXHQ FRVDV ORV FUDFNHUV ODV
GHVWUXHQ
6L XVWHG DXQ GHVHD FRQRFHU FyPR WUDEDMDQ ORV KDFNHUV FRQWLQ~H OHHQGR VH GDUi
FXHQWD TXH QR HV WDQ IiFLO 6L XVWHG TXLHUH VDEHU VREUH FUDFNHUV PHMRU PLUH HQ ORV
JUXSRVGHQRWLFLDVRQHZVHQDOWSUHSiUHVHSDUDVRSRUWDUODGXUDUHDOLGDGFXDQGR
GHVFXEUDTXHXVWHGQRHVWDQOLVWRFRPRFUHH
8QLYHUVLGDGGHODXFD](https://image.slidesharecdn.com/2001-05-15seguridadcomputacionalrev2-110626155412-phpapp02/85/Seguridad-Computacional-21-320.jpg)
![6(*85,'$'20387$,21$/
)iEXODSDUD+DFNHUV
.SHUXFLW#5RM#
+DEtDXQDYH]XQDXVXDULDGH,QWHUQHWOODPDGD.SHUXFLWDTXHHVWDEDFRQVXVDPLJRV
FKDWHDQGRHQHO,5FDQDOERVTXH'HSURQWROHOOHJyXQHPDLOGHVXPDPiTXHOH
GHFtD+LMDSRUDWWDFKPHQWWHPDQGRXQRVDUFKLYRVSDUDHOGRFXPHQWR+70/GHWX
DEXHOLWD 3RU IDYRU DFFHGH D VX FXHQWD VH ORV SDVDV SDUD TXH HOOD SXHGD PRQWDU VX
SDJLQD:::
DVt OD XVXDULD FXR ORJLQ QDPH HUD .SHUXFLWD VH GLVSXVR D DEULU XQD YHQWDQD
HQYLDUOHDVXDEXHOLWDORVDUFKLYRVTXHOHKDEtDQPDQGDGR
(VWDED KDFLHQGR XQ GRZQORDG GHO DWWDFKPHQW GHVGH VX FXHQWD ZHEPDLO FXDQGR GH
SURQWR OH OOHJR XQ PHQVDMH SRU ,4 GH XQ XVXDULR GH GLUHFFLyQ HO
ORER#KDFNHUERVTXHFRP PDLO WRHOORER#KDFNHUERVTXHFRP .SHUXFLWD OH FRQWHVWy
HOPHQVDMH,4(OREROD VDOXGyOHSUHJXQWyGRQGHLED
.SHUXFLWDOHFRQWHVWy
9RDODFXHQWDGHPLDEXHOLWDDHQYLDUOHXQVRIWZDUHSDUDTXHPRQWHVXSiJLQDZHE
DVt(ORERKL]RXQWHOQHWSRUXQDWDMROOHJyDODFXHQWDGHODDEXHOLWDSULPHUR
XDQGR OD FXHQWD GH OD DEXHOLWD OH SLGLy ORJLQ ,' LQJUHVR .SHUXFLWD FUDFNHy HO
SDVVZRUGHQWUy/DDEXHOLWDDOYHUTXHQRHUD.SHUXFLWDVLQRRWUDSHUVRQDWUDWyGH
KDFHUOHXQNLOODOSURFHVR
3HUR(ORERIXHPDVYHOR]OHKL]RXQ,03 IORRGDORVSXHUWRVTXHHOILUHZDOOGHOD
DEXHOLWDQRHVWDEDFRQWURODQGRFXDQGRFDyOHFDPELRHOSDVVZRUG
/XHJRVHWRPySULYLOHJLRVGH5227HQODPiTXLQDFDPELyHOVLVWHPDRSHUDWLYRSRU
XQRGLIHUHQWHTXHVHSDUHFtDHQWRGRKDVWDHQODLQWHUID]DOGHODDEXHOLWD
(QWRQFHVVHPHWLyDODFXHQWDGHODDEXHOLWDVHKL]RSDVDUSRUHOOD
$O UDWR OOHJR .SHUXFLWD FXDQGR HQWUy QRWy XQ SRFR FDPELDGD OD FXHQWD GH VX
DEXHOLWD/HKL]RXQWDONOHSUHJXQWR
$EXHOLWDSRUTXHWLHQHVHVDFXRWDHQGLVFRWDQJUDQGH
(VSDUDDOPDFHQDUPLVDUFKLYRVPHMRU
.SHUXFLWDSUHJXQWy
$EXHOLWDSRUTXHWLHQHVHVDLQWHUID]JUiILFDWDQQRYHGRVD
(VSDUDDGPLQLVWUDUPLVDUFKLYRVPHMRU
.SHUXFLWDVLQWLyTXHDOJRUDURVXFHGtDDKt
8QLYHUVLGDGGHODXFD](https://image.slidesharecdn.com/2001-05-15seguridadcomputacionalrev2-110626155412-phpapp02/85/Seguridad-Computacional-22-320.jpg)
![6(*85,'$'20387$,21$/
$EXHOLWDSRUTXHWLHQHVSULYLOHJLRVGH5227
3DUD5$.($57( 0(-25
.SHUXFLWD VH GLy FXHQWDTXHHVDQRHUDVXDEXHOLWDDOKDFHUOHXQZKRLVGHVFXEULy
TXHHVWDEDFRQHFWDGDGHVGHHORER#KDFNHUERVTXHFRP
,QPHGLDWDPHQWH PDQGy XQ HPDLO D VHFXULW#FEHUVSDFHFRSRUJ SDUD GHODWDU DO
LPSRVWRU(VWHWUDWyGHEORTXHDUVX323VHUYHUKDFLpQGROHXQRYHUORDGGHPHPRULD
SHUR.SHUXFLWDDKDEtDKHFKRFOLFNHQHOERWyQ6HQG
$O UDWR VH FRQHFWy D OD PiTXLQD XQR GH ORV LQYHVWLJDGRUHV GH FEHUVSDFHFRS TXH
UiSLGDPHQWH REWXYR OD GLUHFFLyQ ,3 GH (ORER OH KL]R XQ RYHUULGH D OD PiTXLQD VH
WRPy SULYLOHJLRV GH 5227 DQWHV GH TXH (ORER VH GLHUD FXHQWD OH KL]R XQ NLOO DO
SURFHVRFRORFyXQEDQDWRGRHOGRPLQLR
'HO7UDVKGHOVLVWHPDRSHUDWLYRGH(ORERVHSXGRUHFXSHUDUODWDEODGHSDUWLFLyQGHO
VLVWHPDGHODDEXHOLWDSRUORTXHVHSXGRUHFXSHUDUWRGDVXLQIRUPDFLyQ
/D DEXHOLWD SXGR UHFXSHUDU VX WUDEDMR VXELy VX SiJLQD ZHE D XQ SURPHGLR GH
.EVHJGH WUDQVIHUHQFLD (O VLWH IXH DGPLUDGR SRU WRGRVHQHOFLEHUHVSDFLRUHFLELHQGR
QXPHURVRVKLWVHQSRFRWLHPSR
),1
#QyQLPR
8QLYHUVLGDGGHODXFD](https://image.slidesharecdn.com/2001-05-15seguridadcomputacionalrev2-110626155412-phpapp02/85/Seguridad-Computacional-23-320.jpg)
![6(*85,'$'20387$,21$/
,1752'8,Ï1$/266,67(0$623(5$7,926
,QWURGXFFLyQ
/D GHILQLFLyQ PiV VHQFLOOD GH OR TXH HV XQ VLVWHPD RSHUDWLYR OD SRGHPRV HQXQFLDU HQ OD
VLJXLHQWH IUDVH ³8Q 6LVWHPD 2SHUDWLYR HV XQ VRIWZDUH TXH SRQH D GLVSRVLFLyQ GH ORV
XVXDULRVGHOFRPSXWDGRUORVUHFXUVRVKDUGZDUHSDUDVXXWLOL]DFLyQ´
/DKLVWRULDGHORVVLVWHPDVRSHUDWLYRVODSRGHPRVYHUHQGRVSDUWHVXQDpSRFDHQODFXDO
ORVRUGHQDGRUHVFDUHFtDQGHVLVWHPDRSHUDWLYRODRWUDHQODFXDOORVRUGHQDGRUHVDSRVHHQ
HOVLVWHPDRSHUDWLYR
/DFUHDFLyQGHOVLVWHPDRSHUDWLYRFRPRWDOVXUJHDSDUWLUGHODQHFHVLGDGGHPD[LPL]DUOD
HILFLHQFLD GH ORV UHFXUVRV KDUGZDUH GH ODV PiTXLQDV HV GHFLU FUHDU XQ VRIWZDUH FDSD]GH
XWLOL]DUGHPDQHUDHILFLHQWHWRGRVORVFRPSRQHQWHVKDUGZDUHGHORVSULPHURVFRPSXWDGRUHV
$QWHV GH SUHVHQWDU ODV IXQFLRQHV ODV FDUDFWHUtVWLFDV IXQGDPHQWDOHV GH ORV VLVWHPDV
RSHUDWLYRV YHUHPRV SULPHUR XQD EUHYH HYROXFLyQ KLVWyULFD GH WDO IRUPD TXH QRV SHUPLWD
HVWDEOHFHUODLPSRUWDQFLDGHORVVLVWHPDVRSHUDWLYRVHQORVFRPSXWDGRUHV
RPSXWDGRURPSXWDGRUD2UGHQDGRU
RQFHSWR
/DGHILQLFLyQHVODPLVPDSDUDFXDOTXLHUWLSRGHPiTXLQDODGHILQLFLyQJHQHUDODFHSWDGD
HVODVLJXLHQWHHVXQDPiTXLQDTXHOOHYDDFDERSURFHVDPLHQWRGHLQIRUPDFLyQGLJLWDO
,QIRUPDFLyQGLJLWDOHVDTXHOODTXHSXHGHH[SUHVDUVHSRUPHGLRGHQ~PHURVROHWUDV](https://image.slidesharecdn.com/2001-05-15seguridadcomputacionalrev2-110626155412-phpapp02/85/Seguridad-Computacional-24-320.jpg)

![QRHVILMRGHEHVHUGHILQLGRSRUHOXVXDULRGHODPiTXLQD6HGLFH
HQWRQFHVTXHHOXVXDULRSURJUDPDODFRPSXWDGRUD(OSURFHVDPLHQWRGHODLQIRUPDFLyQ
SURGXFH FRPR UHVXOWDGR PiV LQIRUPDFLyQ $ OD LQIRUPDFLyQ TXH YD VHU SURFHVDGD QRV
UHIHULUHPRVFRPRGDWRV GHHQWUDGDRHQWUDGDDOD LQIRUPDFLyQSURGXFLGD QRVUHIHULPRV
FRPRUHVXOWDGRVRVDOLGD
2UJDQL]DFLyQ,QWHUQDGHORPSXWDGRU
8QD FRPSXWDGRUD HVWD FRQIRUPDGD SRU ORV VXEVLVWHPDV 3URFHVDGRU 0HPRULD
'LVSRVLWLYRVGH(QWUDGD6DOLGD
3RSXODUPHQWH VH OH GHQRPLQD SURFHVDGRU D OD FDMD TXH FRQWLHQHQ WRGRV ORV GLVSRVLWLYRV
LQWHUQRV GHO FRPSXWDGRU UHDOPHQWH HVWH HOHPHQWR HV XQR GH ORV GLVSRVLWLYRV GHO
FRPSXWDGRU HV HO TXH SHUPLWH HMHFXWDU OD OyJLFD GH ORV SURJUDPDV LQFOXHQGR OD GHO
VLVWHPDRSHUDWLYR
8QLYHUVLGDGGHODXFD](https://image.slidesharecdn.com/2001-05-15seguridadcomputacionalrev2-110626155412-phpapp02/85/Seguridad-Computacional-26-320.jpg)
![6(*85,'$'20387$,21$/
,OXVWUDFLyQ2UJDQL]DFLyQLQWHUQDGHORPSXWDGRU
(O PHMRU WpUPLQR SDUD HVWR HV 38 8QLGDG HQWUDO GH 3URFHVDPLHQWR](https://image.slidesharecdn.com/2001-05-15seguridadcomputacionalrev2-110626155412-phpapp02/85/Seguridad-Computacional-27-320.jpg)
![OD FXDO HVWD
UHSUHVHQWDGD HQ OD ,OXVWUDFLyQ HQ HO UHFXDGUR L]TXLHUGR HVWH D VX YH] VH SXHGH GLYLGLU HQ
XQLGDG DULWPpWLFR OyJLFD XQLGDG GH FRQWURO ORV UHJLVWURV HVWRV HOHPHQWRV SHUPLWHQ
HMHFXWDU FDGD XQD GH ODV LQVWUXFFLRQHV GH ORV SURJUDPDV HQ FRQMXQWR FRQ ODPHPRULD GHO
FRPSXWDGRU D OD FXDO FRP~QPHQWH VH OH GHQRPLQD PHPRULD 5$0 5DQGRP $FFHVV
0HPRU](https://image.slidesharecdn.com/2001-05-15seguridadcomputacionalrev2-110626155412-phpapp02/85/Seguridad-Computacional-28-320.jpg)




![x ,QVWUXFFLRQHVPDQXDOHV
x 3pUGLGDGH7LHPSRHQFDPELRVGHWDUHDV
x $JLOL]DUHOSDVRGHXQWUDEDMRDRWUR
*HQHUDFLyQ x ³3URFHVDPLHQWRSRUORWHV´](https://image.slidesharecdn.com/2001-05-15seguridadcomputacionalrev2-110626155412-phpapp02/85/Seguridad-Computacional-33-320.jpg)


![HMHFXFLyQGHORVSURJUDPDV
x $SUHQGL]DMHHQJRUURVRGHOVLVWHPD
x (PSOHRGH5HGHVGHRUGHQDGRUHV
*HQHUDFLyQ x 3URFHVDPLHQWRHQOtQHD](https://image.slidesharecdn.com/2001-05-15seguridadcomputacionalrev2-110626155412-phpapp02/85/Seguridad-Computacional-36-320.jpg)



![6(*85,'$'20387$,21$/
yPRVHSUHVHQWDHQODILJXUDVHDSUHFLDTXHHQHVWDpSRFDQRH[LVWtDHOVLVWHPDRSHUDWLYR
FRPRWDOSRUFRQVLJXLHQWHVHHVSHFLDOL]DURQORVWUDEDMRVSDUDSRGHUXVDUHVWDVPiTXLQDVVH
XWLOL]DEDHODFFHVRSRURSHUDGRUHOFXDOHUDXQXVXDULRHVSHFLDOL]DGRTXHWHQLDODPLVLyQGH
PDQLSXODUODPiTXLQDFDUJDUSURJUDPDVREWHQHUUHVXOWDGRVHWF/RVSURJUDPDGRUHVHUDQ
XVXDULRV TXH IRUPDWHDEDQ ORV WUDEDMRV XVDQGR FyGLJR PiTXLQD ORV SDVDEDQ D ORV
RSHUDGRUHVSDUDTXHHOORVORVHMHFXWDUDQHQODPiTXLQD
(Q FDGD FDPELR GH WDUHD HO RSHUDGRU GHEtD UHLQLFLDU WRGD OD PiTXLQD FRQ HO SURJUDPD
FRUUHFWRSDUDHMHFXWDUORVSURJUDPDVGHSHQGLHQGRGHVXVQHFHVLGDGHVHVWRFRQOOHYDEDDXQD
JUDQSpUGLGDGHWLHPSRHQHOSDVRGHXQWUDEDMRDORWUR8QDPHMRUDVHUHDOL]yDODJUXSDU
ORV WUDEDMRV GHO PLVPR WLSR HMHFXWDUOR HQ XQ VROR ORWH D HVWR VH OH FRQRFLy FRPR
SURFHVDPLHQWR SRU JUXSRV (IHFWLYDPHQWH HVWR SHUPLWLy GLVPLQXLU HO WLHPSR TXH
GHPRUDEDQ ORV WUDEDMRV HQ VHU HMHFXWDGRV 3RVWHULRUPHQWH VH GHWHFWR TXH HO WUDEDMR
UHDOL]DGR SRU HO RSHUDGRU FRQVLVWtD HQ XQD VHULH GH SDVRV ILMRV VLVWHPiWLFRV DVt VH GLR
RULJHQDODHODERUDFLyQGHXQSURJUDPDUHVLGHQWHHQODPHPRULDGHORVFRPSXWDGRUHVTXH
SHUPLWtDFODVLILFDUHOWUDEDMRHMHFXWDUORSRUORWHVFRPXQHV$HVWHSURJUDPDVHOHOODPR
PRQLWRU UHVLGHQWH DFWXDOPHQWH HV FRQVLGHUDGR FRPR HO SULPHU VLVWHPD RSHUDWLYR HQ ODV
PiTXLQDV
/RV VLJXLHQWHV DYDQFHV HQ ORV VLVWHPDVRSHUDWLYRV VH FDUDFWHUL]DURQ SRU OD E~VTXHGD GH OD
PHMRUD GHO UHQGLPLHQWR DVt VH LPSOHPHQWR HO PDQHMRRII ± OLQH DO DSDUHFHU ODV FLQWDV
PDJQpWLFDVTXHVRQPiVUiSLGDVTXHODVOHFWRUDVGHWDUMHWDVVHSRGtDDOPDFHQDUORVWUDEDMRV
HQ HVWDV FLQWDV IXHUD GH OtQHD PLHQWUDV VH HMHFXWDQ XQDV WDUHDV D DOPDFHQDGDV HQ OD
PiTXLQD /R PLVPR SDUD OD VDOLGD GH ORV GDWRV 2WUR HOHPHQWR TXH DXGy HQ HO
UHQGLPLHQWR IXH HO EXIIHULQJ OD FXDO FRQVLVWH HQ DOPDFHQDPLHQWRV LQWHUPHGLRV HQWUH OD
PiTXLQDPLHQWUDVHOSURFHVDGRUHMHFXWDRWUDVWDUHDVSRVWHULRUPHQWHSXHGHDWHQGHUHOEXIIHU
GH LQIRUPDFLyQ (OVSRROLQJ SHUPLWLy DSURYHFKDV OHFWXUDV HVFULWXUDV VLPXOWDQHDV D ORV
PRGHUQRVGLVFRVGXURVTXHSHUPLWLHURQHVWDVFDUDFWHUtVWLFDV
$ SDUWLU GH OD JHQHUDFLyQ VH HPSH]DURQ D LPSOHPHQWDU FDUDFWHUtVWLFDV DGLFLRQDOHV D ORV
VLVWHPDV RSHUDWLYRV TXH OH GLHURQ HILFLHQFLD HILFDFLD D OD HODERUDFLyQ GH WUDEDMRV GH
GLIHUHQWHVtQGROHVFRQXVXDULRVRWUDEDMRVVLPXOWiQHRV/DPXOWLSURJUDPDFLyQ SHUPLWLy
HMHFXWDUYDULRVSURJUDPDVVLPXOWiQHDPHQWHHQXQDPiTXLQDLQGHSHQGLHQWHGHOQ~PHURGH
SURFHVDGRUHV TXH SRVHD HVWD FXDQGR PDQHMDPRV YDULRV SURFHVDGRUHV VH HVWDEOHFLHURQ ORV
VLVWHPDV GH PXOWLSURFHVDPLHQWR $Vt SRFR D SRFR VH IXHURQ HQFRQWUDQGR PHMRUHV
WHFQRORJtDV GH PD[LPL]DFLyQ GH ORV UHFXUVRV GH ODV FRPSXWDGRUDV FRQ OD SRVWHULRU
DSDULFLyQGHRWURVSUREOHPDVLQKHUHQWHVDHVWDVQXHYDVWHFQRORJtDV
)LQDOPHQWH HQ ODV ~OWLPDV JHQHUDFLRQHV VH SXHGH DSUHFLDU TXH ORV VLVWHPDV RSHUDWLYRV VH
HVSHFLDOL]DQGHDFXHUGRDODVQHFHVLGDGHVGHXVXDULRHQODVDSOLFDFLRQHVHVSHFtILFDVFRPR
HOPDQHMRGHEDVHVGHGDWRVVLVWHPDVGHLQIRUPDFLyQJHRJUiILFD(VWRHVGHELGRDTXHHO
KDUGZDUH KD OOHJDGR D JUDQGHV YHORFLGDGHV GH SURFHVDPLHQWR PDQLSXODFLyQ GH GDWRV OR
FXDO SHUPLWH D ODV DSOLFDFLRQHV GHVSUHRFXSDUVH SRU HO UHQGLPLHQWR HQIRFDUVH HQ OD
FRQVWUXFFLyQ DGHFXDGD GH VLVWHPDV TXH UHVSRQGDQ DO PDQHMR GHO FRQRFLPLHQWR QR GH
VLPSOHVGDWRV
8QLYHUVLGDGGHODXFD](https://image.slidesharecdn.com/2001-05-15seguridadcomputacionalrev2-110626155412-phpapp02/85/Seguridad-Computacional-40-320.jpg)
![6(*85,'$'20387$,21$/
'HILQLFLyQ(VWUXFWXUD)XQFLRQHVGHORV6LVWHPDV2SHUDWLYRV
(Q ORV VHVHQWDV XQ 62 VH GHILQH FRPR
(O VRIWZDUH TXH FRQWUROD DO KDUGZDUH
$FWXDOPHQWH XQ 62 VH GHILQH FRPR /RV SURJUDPDV LPSOHPHQWDGRV HQ 6RIWZDUH R
)LUPZDUHTXHKDFHQSRVLEOHTXHVHXVHHO+DUGZDUH
/DWHQGHQFLDDFWXDOHVKDFHU62PiVVLPSOHVRULHQWDGRVDODVQHFHVLGDGHVGHOXVXDULR
)XQFLRQHVJHQHUDOHVGHXQ62
UHDODLPDJHQTXHHOXVXDULRFRQRFHGHHOHQRWUDVSDODEUDVHO62GLVSRQHDOXVXDULRXQD
LQWHUID]TXHOHSHUPLWDFRPXQLFDUVHFRQODPiTXLQD
XPSOH OD )XQFLyQ GH 6LVWHPD OyJLFR VREUH HO VLVWHPD ItVLFR GH OD PiTXLQD SHUPLWLHQGR
FRPSDUWLUKDUGZDUHVRIWZDUHFRQRWURVXVXDULRV
3ODQLILFD ORV UHFXUVRV FUtWLFRV GHO VLVWHPD HQWUH ORV XVXDULRV SURFHVDGRU PHPRULD
GLVSRVLWLYRVGHHQWUDGDVDOLGDGHLQIRUPDFLyQ(6](https://image.slidesharecdn.com/2001-05-15seguridadcomputacionalrev2-110626155412-phpapp02/85/Seguridad-Computacional-41-320.jpg)


![6(*85,'$'20387$,21$/
1LYHO± +DUGZDUH
7DEOD(MHPSORGH1LYHOHVGHXQ62
0iTXLQD 9LUWXDO 3UHVHQWDQ XQD ,QWHUIDFH D FDGD SURFHVR SUHVHQWDQGR XQD PiTXLQD TXH
SDUHFHLGpQWLFDDODPiTXLQDUHDOVXEDFHQWH
x 0DQHMRGH0XOWLSURJUDPDFLyQ
x 0iTXLQDH[WHQGLGD
x ,QWHJUDFLyQGHGLVWLQWRV62
x (OQ~FOHRHVXQPRQLWRUYLUWXDO
OLHQWH 6HUYLGRU 6LVWHPD RSHUDWLYR GH SURSyVLWR JHQHUDO DGPLQLVWUD ORV SURFHVRV OD
PHPRULDODFRPXQLFDFLyQHQWUHSURFHVRV
3UHVWDFLRQHVGHXQ6LVWHPD2SHUDWLYR
/DV SUHVWDFLRQHVGHORVVLVWHPDVRSHUDWLYRVODVSRGHPRVFODVLILFDUVHJ~QHOXVXDULRGHODV
PLVPDV
3URJUDPDGRU(OSURJUDPDGRUQHFHVLWDHMHFXWDUORVSURJUDPDVUHDOL]DURSHUDFLRQHVGH(6
JHVWLRQDUDUFKLYRV
6LVWHPD(OVLVWHPDPDQLSXODORVUHFXUVRVGHODPiTXLQDOOHYDXQDVHVWDGtVWLFDVGHOXVRGH
ORVPLVPRVPDQWLHQHXQDVSURWHFFLRQHVDIDOORVSURFHVDGRU(6GHPHPRULD](https://image.slidesharecdn.com/2001-05-15seguridadcomputacionalrev2-110626155412-phpapp02/85/Seguridad-Computacional-44-320.jpg)
![/RVSURFHVRVODPHPRULDOD(6
8QD GH ODV SULQFLSDOHV IXQFLRQHV GH ORV VLVWHPDV RSHUDWLYRV UDGLFD HQ OD JHVWLyQ
DGPLQLVWUDFLyQGHORVSURFHVRVODPHPRULDOD(6([LVWHQFDStWXORVHQWHURVHQOLEURVGH
VLVWHPDV RSHUDWLYRV SDUD ORV PHFDQLVPRV PpWRGRV XWLOL]DGRV SRU ORV 62 SDUD OD
DGPLQLVWUDFLyQGHHVWRVGLVSRVLWLYRV1RHVHOILQGHHVWHWH[WRSUHVHQWDUHVWDLQIRUPDFLyQ
SRUTXH VH H[WLHQGH PiV KDOOD GH ORV ORV OtPLWHV GH OD WHPiWLFD WUDWDGD 6H SURFHGHUi D
SUHVHQWDU FRQFHSWRV IXQGDPHQWDOHV TXH SHUPLWHQ UHODFLRQDUVH FRQ OD VHJXULGDG
FRPSXWDFLRQDOGLUHFWDPHQWH
/RVSURFHVRV
8Q SURFHVR HV XQ SURJUDPD HQ HMHFXFLyQ MXQWR FRQ XQ HQWRUQR DVRFLDGR UHJLVWURV
YDULDEOHV HWF](https://image.slidesharecdn.com/2001-05-15seguridadcomputacionalrev2-110626155412-phpapp02/85/Seguridad-Computacional-45-320.jpg)
![$FWXDOPHQWH H[LVWHQ VLVWHPDV RSHUDWLYRV TXH SHUPLWHQ D ORV XVXDULRV
LQLFLDUGLYHUVRVSURFHVRVDVXYH]HVWRVSURFHVRVSXHGHQJHQHUDUPiVSURFHVRVKLMRVWRGR
HVWR VH UHDOL]D HQ VLVWHPDV GH P~OWLSOHV XVXDULRV PXOWLSURJUDPDFLyQ](https://image.slidesharecdn.com/2001-05-15seguridadcomputacionalrev2-110626155412-phpapp02/85/Seguridad-Computacional-46-320.jpg)




![QRUPDOPHQWH
VH FODVLILFDQ ORV SURFHVRV FRPR OLPLWDGRV SRU (6 OLPLWDGRV SRU SURFHVDGRU HVWR HV
FXDQGR ORV SURFHVRV VH FDUDFWHUL]DQ SRU KDFHU PXFKDV SHWLFLRQHV DO 62 GHO XVR GH ORV
GLVSRVLWLYRVGHHQWUDGDVDOLGDGHOSURFHVDGRUUHVSHFWLYDPHQWH
/D0HPRULD
/D PHPRULDGHOFRPSXWDGRUHVXQRGHORVGLVSRVLWLYRVPiVLPSRUWDQWHVSDUDODHMHFXFLyQ
GHODVDSOLFDFLRQHV7RGRSURFHVRWLHQHXQHVSDFLRHQODPHPRULDKDVWDHOPLVPRVLVWHPD
RSHUDWLYR GHEH H[LVWLU HQ OD PHPRULD GHO FRPSXWDGRU (O 62 HV HO HQFDUJDGR GH
DGPLQLVWUDU HVWH UHFXUVR GH DVLJQDU HVSDFLRV SDUD SURFHVRV HQWUDQWHV GH DGPLQLVWUDUOR
HQWUH HOORV XDQGR VH HMHFXWD XQ SURFHVR GDxLQR (M 9LUXV](https://image.slidesharecdn.com/2001-05-15seguridadcomputacionalrev2-110626155412-phpapp02/85/Seguridad-Computacional-51-320.jpg)
![HVWH QRUPDOPHQWH KDFH XQD
SHWLFLyQ GH PHPRULD VH LQVWDOD HQ DOJ~Q ULQFyQ GH HOOD /D PHPRULD HV XQR GH ORV
UHFXUVRV TXH XWLOL]DQ PiV HVWRV SURJUDPDV GDxLQRV SDUD DOPDFHQDUVH HMHFXWDUVH HV PiV
SDUDSUHYDOHFHUD~QFXDQGRVHKDOODERUUDGRHOSURJUDPDItVLFDPHQWHGHORVGLVFRVGXURV
'LVSRVLWLYRVGH(6
/RV GLVSRVLWLYRV GH HQWUDGD VDOLGD VRQ WRGRV ORV HOHPHQWRV KDUGZDUH TXH SHUPLWHQ DO
FRPSXWDGRUUHFLELUHQYLDULQIRUPDFLyQIXHUDGHOVLVWHPD(QWUHHOORVSRGHPRVHQFRQWUDU
ODV WDUMHWDV GH UHG ODV WDUMHWDV GH 02'(0 DOJR PX LPSRUWDQWH ORVSXHUWRV ORV FXDOHV
VRQ ODV SXHUWDV GH HQWUDGD VDOLGD GH LQIRUPDFLyQ GHO FRPSXWDGRU VRQ ODV YtDV SRU ODV
FXDOHVORVLQWUXVRVDFFHGHQDpOQRUPDOPHQWHORVSXHUWRVVHQXPHUDQFRQGtJLWRVHQWHURV
SRVHHQ XQD GLUHFFLyQ HQ OD PHPRULD GHO FRPSXWDGRU HQ OD FXDO FRORFDQ UHFLEHQ OD
LQIRUPDFLyQ 7RGDV ODV PiTXLQDV VX UHVSHFWLYR 62 HVWDEOHFHQ XQ FRQMXQWR DPSOLR GH
SXHUWRVSDUDFRPXQLFDFLRQHVFRQILJXUDFLyQGHVHUYLFLRVWHOQHWLQWHUQHWWUDQVIHUHQFLDGH
DUFKLYRVHWF](https://image.slidesharecdn.com/2001-05-15seguridadcomputacionalrev2-110626155412-phpapp02/85/Seguridad-Computacional-52-320.jpg)

![6(*85,'$'20387$,21$/
(Q HVWH DSDUWDGR VH SUHWHQGH DQDOL]DU ORV DVSHFWRV TXH LQWHUYLHQHQ HQ OD VHJXULGDG GH ORV
VLVWHPDVLQIRUPiWLFRVHQJHQHUDOHQORVVLVWHPDVRSHUDWLYRVHQSDUWLFXODU
3ULPHURVHKDFHXQEDODQFHUHTXHULPLHQWRVPHFDQLVPRVQHFHVDULRVSDUDSRVHHUXQDEXHQD
VHJXULGDGLQIRUPiWLFDWDQWRGHORVHTXLSRVFRPRGHORVSURJUDPDVGDWRV
/D VHJXULGDG VHSXHGH DQDOL]DU GHVGH GRV HQIRTXHVOD VHJXULGDG H[WHUQD OD VHJXULGDG
LQWHUQD
6H GHEHQ HVWDEOHFHU GLUHFWULFHV PHFDQLVPRV GH VHJXULGDG TXH SHUPLWDQ HVWDEOHFHU XQ
VLVWHPD VHJXUR 8QD GH HOODV VRQ ODV UHVWULFFLRQHV D ORV DFFHVRV GH ODV SHUVRQDV QR
DXWRUL]DGDV DO OXJDU GRQGH HVWiQ ORV HTXLSRV PDQWHQHU HQ EXHQ HVWDGR ORV PDWHULDOHV
SUHYHQLUULHVJRVFDWDVWUyILFRVFRPRLQXQGDFLRQHVLQFHQGLRVHWF0XFKRVGHORVFDVRVGH
YLRODFLyQGHGDWRVVHFDXVDQSRUHODFFHVRGHSHUVRQDOQRDXWRUL]DGDVDORVHTXLSRV ([LVWH
RWUDFXVDGHHVWRVDFFHVRVHVODPLFURLQIRUPiWLFD HOVRIWZDUHPDOLQWHQFLRQDGRHVGHFLU
SHTXHxRVSURJUDPDVTXHWLHQHQODIDFLOLGDGGHUHSURGXFLUVHHMHFXWDUVHFXRVHIHFWRVVRQ
GHVWUXFWLYRVHQODPDRUtDGHORVFDVRVHOGDxRHVLUUHYHUVLEOH YLUXVLQIRUPiWLFRV](https://image.slidesharecdn.com/2001-05-15seguridadcomputacionalrev2-110626155412-phpapp02/85/Seguridad-Computacional-54-320.jpg)
![3RUHVWRORVJRELHUQRVGHORVGLVWLQWRVSDtVHVKDQGLFWDGROHHVQRUPDVSDUDDVHJXUDUXQD
UDFLRQDOVHJXULGDGHQORVVLVWHPDVGHLQIRUPDFLyQSURWHJHUHOGHUHFKRDODLQWLPLGDGGHOD
LQIRUPDFLyQGHODVSHUVRQDV
6HJXULGDGH[WHUQD
8Q FRUUHFWR VLVWHPD GH VHJXULGDGHVHOTXHDUWLFXODWRGRVORVVXEVLVWHPDVGHSURWHFFLRQHV
HQWUH VL GH WDO IRUPD TXH SDUD TXH XQ LQWUXVR SXHGD YLRODUOD VH HQFXHQWUH FRQ YDULRV
REVWiFXORVDODYH]7RGRVORVPHFDQLVPRVGLULJLGRVDDVHJXUDUHOVLVWHPDLQIRUPiWLFRVLQ
TXHHOSURSLRVLVWHPDLQWHUYHQJDHVORTXHVHGHQRPLQDVHJXULGDGH[WHUQD
3RGHPRVYHUODVHJXULGDGH[WHUQDGHGRVIRUPDV
6HJXULGDG )tVLFD (QJORED ORV PHFDQLVPRV TXH LPSLGHQ D ORV DJHQWHV ItVLFR HQWUDU DO
VLVWHPD LQIRUPiWLFR (M )XHJR KXPR LQXQGDFLRQHV GHVFDUJDV HOpFWULFDV FDPSRV
PDJQpWLFRV DFFHVR ItVLFR GH SHUVRQDV GH PDOD LQWHQFLyQ](https://image.slidesharecdn.com/2001-05-15seguridadcomputacionalrev2-110626155412-phpapp02/85/Seguridad-Computacional-55-320.jpg)
![$Vt SRGHPRV HVWDEOHFHU GRV
IRUPDV
x 3URWHFFLyQFRQWUDGHVDVWUHV(OHPHQWRVGHSUHYHQFLyQGHWHFFLyQHOLPLQDFLyQGH
ORVDJHQWHVPHQFLRQDGRVDQWHULRUPHQWH
x 3URWHFFLyQ FRQWUD LQWUXVRV (OHPHQWRV TXH QR SHUPLWDQ HO DFFHVR ItVLFR GH ODV
SHUVRQDVQRDXWRUL]DGDV(M3XHUWDVGHVHJXULGDGKXHOODVFyGLJRVHWF
6HJXULGDG GH $GPLQLVWUDFLyQ (QJORED ORV PHFDQLVPRV PiV XVXDOHV SDUD LPSHGLU HO
DFFHVROyJLFRGHSHUVRQDVItVLFDVDOVLVWHPD3RGHPRVGLYLGLUHVWRFRPR
8QLYHUVLGDGGHODXFD](https://image.slidesharecdn.com/2001-05-15seguridadcomputacionalrev2-110626155412-phpapp02/85/Seguridad-Computacional-56-320.jpg)
![6(*85,'$'20387$,21$/
3URWHFFLyQGHDFFHVR(VHOPHFDQLVPRTXHSHUPLWHFRQHFWDUDORVXVXDULRVDXWRUL]DGRV
QRSHUPLWLUODHQWUDGDDORVLQWUXVRV/DVPRGDOLGDGHVVRQ
3DODEUDV GH DFFHVR SDVVZRUG](https://image.slidesharecdn.com/2001-05-15seguridadcomputacionalrev2-110626155412-phpapp02/85/Seguridad-Computacional-57-320.jpg)



![6HJXULGDG )XQFLRQDO (QJORED DVSHFWRV UHODWLYRV DO IXQFLRQDPLHQWR GHO VLVWHPD D OD
VHJXULGDGGHODVLQVWDODFLRQHVVHSUHWHQGHWHQHU
6HJXULGDGHQODWUDQVPLVLyQGHGDWRV/DV OtQHDVGHWUDQVPLVLyQVRQIiFLOPHQWHYLRODEOHV
SRUHVWRVHXWLOL]DQODVVLJXLHQWHVWpFQLFDV
RPSDFWDFLyQ GH ORV GDWRV 6H FRPSULPHQ ORV GDWRV SDUD TXH RFXSHQ HO PHQRU HVSDFLR
SRVLEOHDVtFRQVHJXLUHQSULQFLSLRTXHODGXUDFLyQGHODWUDQVPLVLyQVHDPHQRUTXHSDUD
HQWHQGHUOD KDOOD TXH GHVFRPSDFWDUOD (QWUH ORV PpWRGRV GH FRPSDFWDFLyQ H[LVWHQ OD
UHGXFFLyQ GH HVSDFLRV HQ EODQFR FRGLILFDFLyQ SRU GLIHUHQFLD ULSWRJUDItD D
H[SOLFDGD
)LDELOLGDG $GHPiV GH ODV PHGLGDV DQWHULRUHV VH VXHOHQ WRPDU RWUDV SDUD DVHJXUDU HO
FRUUHFWR HVWDGR GH OD LQIRUPDFLyQ DO OOHJDU D VX GHVWLQR 6H SXHGHQ SUHVHQWDU SUREOHPDV
GHELGRV D FDXVDV DFFLGHQWDOHV FRPR OD LQIOXHQFLD GH IXHUWHV FDPSRV PDJQpWLFRV
SHUWXUEDFLRQHVHOpFWULFDVHWFDVtFRPRSRUPRWLYRVGHLQWUXVLyQGHLQIRUPDFLyQFRQHOILQ
GHPRGLILFDUODRGHVWUXLUOD3DUDHVWRVHOHDxDGHXQDLQIRUPDFLyQDGLFLRQDODODVFDEHFHUDV
GH ORV GDWRV HQYLDGRV FRQ HO ILQ GH DVHJXUDU TXH OD LQIRUPDFLyQ OOHJy FRUUHFWDPHQWH
1RUPDOPHQWHVHXVDQORVVLJXLHQWHVPpWRGRV
x %LWGHSDULGDG
x yGLJRVGH+DPPLQJ
x yGLJRGHUHGXQGDQFLDFtFOLFD
6LVWHPDV WROHUDQWHV D ORV IDOORV 6H XWLOL]DQ HQ VLVWHPDV GRQGH VH SXHGD SHUGHU
LQIRUPDFLyQ GHELGR D XQ PDO IXQFLRQDPLHQWR GH ORV PLVPRV (V LPSRUWDQWH SDUD ORV
8QLYHUVLGDGGHODXFD](https://image.slidesharecdn.com/2001-05-15seguridadcomputacionalrev2-110626155412-phpapp02/85/Seguridad-Computacional-61-320.jpg)


![x 5HORMKDUGZDUHSDUDHYLWDUHOEORTXHRGHOSURFHVDGRU
6HJXULGDGGHODPHPRULD
6H WUDWD GH PHFDQLVPRV SDUD HYLWDU TXH XQ XVXDULR DFFHGD OD LQIRUPDFLyQ GH RWUR VLQ
DXWRUL]DFLyQ(QWUHHOORVFLWDUHPRVGRV
x 5HJLVWUROtPLWHVIURQWHUD
x (VWDGRSURWHJLGRQRSURWHJLGRGHOSURFHVDGRU
x $GHPiVVHXWLOL]DQSDUDODPHPRULDPpWRGRVFRPRHOGHXWLOL]DUXQELWGHSDULGDGRHO
GHFKHTXHRGHVXPD
6HJXULGDGGHORV$UFKLYRV
/D ILQDOLGDG SULQFLSDO GH ODV FRPSXWDGRUDV HV HO WUDWDPLHQWR GH OD LQIRUPDFLyQ TXH VH
DOPDFHQD SHUPDQHQWHPHQWH HQ ORV DUFKLYRV /D SpUGLGD R DOWHUDFLyQ QR GHVHDGD GHGLFKD
LQIRUPDFLyQ FDXVDUtD WUDVWRUQRV TXH SRGUtDQ VHU LUUHSDUDEOHV HQ DOJXQRV FDVRV 3DUD XQ
FRUUHFWRPDQHMRGHODLQIRUPDFLyQVHGHEHHQIRFDUGHVGHGRVDVSHFWRVODGLVSRQLELOLGDG
ODSULYDFLGDG GHORVDUFKLYRV
'LVSRQLELOLGDG GH ORV DUFKLYRV 8Q DUFKLYR GHEH WHQHU OD LQIRUPDFLyQ SUHYLVWD HVWDU
GLVSRQLEOHHQHOPRPHQWRTXHXQXVXDULRODQHFHVLWH+DTXHWHQHUSUHVHQWHODQHFHVLGDG
GHDVHJXUDUWDOFLUFXQVWDQFLDSDUDHOORVHSXHGHQUHDOL]DUODVVLJXLHQWHVDFFLRQHV
8QLYHUVLGDGGHODXFD](https://image.slidesharecdn.com/2001-05-15seguridadcomputacionalrev2-110626155412-phpapp02/85/Seguridad-Computacional-64-320.jpg)


![VH UHDOLFH XQD FRSLD GHO FRQWHQLGR GH ORV DUFKLYRV GH IRUPD TXH VL VH GHVWUXHQpVWRV HV
SRVLEOHODUHFXSHUDFLyQGHORVGDWRVDSDUWLUGHOD~OWLPDGHODVFRSLDV(VWRVHVXHOHKDFHU
FRQSURJUDPDVGHXWLOLGDGGHORVVLVWHPDVRSHUDWLYRV
$UFKLYR/2*(QVLVWHPDVGHWLHPSRFRPSDUWLGRGyQGHWUDEDMDQVLPXOWiQHDPHQWHPXFKRV
XVXDULRV TXH HQWUH RWUDV RSHUDFLRQHV OOHYDQ DFDER QXPHURVDV DFWXDOL]DFLRQHV
PRGLILFDFLRQHV GH DUFKLYRV QR VRQ VXILFLHQWHV ODV SHULyGLFDV FRSLDV GH VHJXULGDG SDUD
DIURQWDU OD SpUGLGD GH LQIRUPDFLyQ 6L IDOOD OD FRPSXWDGRUD VH SXHGH UHFXSHUDU R
UHFRQVWUXLUODLQIRUPDFLyQDSDUWLUGHORVDUFKLYRV/2*ORVFXDOHVOOHYDQODLQIRUPDFLyQGH
WRGDVODVPRGLILFDFLRQHVKHFKDVDORVDUFKLYRVGHO XVXDULR
3ULYDFLGDGGHORVDUFKLYRV(OFRQWHQLGRGHORVDUFKLYRVVHGHEHSURWHJHUGHORVDFFHVRV
QR GHVHDGRV (QWUH HO SHOLJUR GH SHUPLWLU D WRGRV ORV XVXDULRV ORV DFFHVRV D FXDOTXLHU
DUFKLYR OD ULJLGH] GH FDGD XVXDULR VyOR SXHGD DFFHGHU D ORV VXRV HO VLVWHPD GH
SURWHFFLyQGHEHSHUPLWLUDFFHVRVGHIRUPDFRQWURODGDVHJ~QODVUHJODVSUHGHILQLGDVFRQ
ODVFRQVLJXLHQWHVDXWRUL]DFLRQHVDGDXVXDULRDOFRPHQ]DUODVHVLyQHQXQVLVWHPDWUDVVX
LGHQWLILFDFLyQ WLHQH DVLJQDGR SRU HO VLVWHPD GH SURWHFFLyQ XQ GRPLQLR FRPSXHVWR GH XQD
VHULHGHUHFXUVRVGHRSHUDFLRQHVSHUPLWLGDVSRUHMHPSORXQDVHULHGHDUFKLYRVDORVTXH
SXHGH DFFHGHU QR WHQLHQGR SHUPLVR SDUD HO UHVWR GH ORV DUFKLYRV 1RUPDOPHQWH HVWR VH
PDQHMDFRQORTXHVHFRQRFHFRPRPDWUL]GHGRPLQLRVHQODFXDOODVILODVVRQORVGRPLQLRV
ODVFROXPQDVVRQWRGRVORVUHFXUVRVGHOVLVWHPDORVGRPLQLRVUHFXUVRVUHODFLRQDGRVHQ
WLSR GH SHUPLVR VREUH HVWRV GHWHUPLQDUDQ HO JUDGR GH SURWHFFLyQ D FDGD XVXDULR 6L OD
PDWUL] HV GH SRFRV GDWRV VH XWLOL]D HO PpWRGR GH DVLJQDU XQD OLVWD GH GRPLQLRV D FDGD
UHFXUVRHVWRVHFRQRFHFRPROLVWDGHDFFHVR
8QVLVWHPDRSHUDWLYRVHULR
([LVWHQ GLIHUHQWHV WLSRV GH VLVWHPDV RSHUDWLYRV FRQ GLIHUHQWHV DUTXLWHFWXUDV FRPR VH YLR
DQWHULRUPHQWH /RV VLVWHPDV RSHUDWLYRV PRGHUQRV FXPSOHQ FRQ ODV IXQFLRQHV
SUHVWDFLRQHV EiVLFDV SHUR KD TXH UHFRQRFHU TXH FDGD VLVWHPD WLHQH VXV SURSLDV
SDUWLFXODULGDGHV DVt FRPR GLIHUHQFLDVHQ UREXVWH] SRWHQFLD HVWDELOLGDG (Q OD JDPD GH
HVWRV VLVWHPDV RSHUDWLYRV HQFRQWUDPRV ORV VLVWHPDV 8QL[ ORV FXDOHV VRQ DFHSWDGRV HQ HO
PXQGRFRPRORVVLVWHPDVRSHUDWLYRVPiVHILFDFHVHILFLHQWHVTXHVXVKRPyORJRV
/D UD]yQ GH WRPDU HO VLVWHPD RSHUDWLYR 8QL[ R /LQX[ SDUD HO PDQHMR GH OD VHJXULGDG
FRPSXWDFLRQDOUDGLFDSUHFLVDPHQWHHQODUREXVWH]HILFDFLDXWLOLGDGHVSDUDHOPDQHMRGHOD
VHJXULGDGHQORVFRPSXWDGRUHVHQODVUHGHVGHFRPSXWDGRUDV$GHPiVSRUORVLJXLHQWH
(OREMHWLYRGHXQ6LVWHPD2SHUDWLYRVHULRHVHOGHFUHDUXQDPiTXLQDYLUWXDOSDUDODTXHVHD
VHQFLOOR WUDEDMDU (V GHFLU RFXOWDU HO KDUGZDUH +:](https://image.slidesharecdn.com/2001-05-15seguridadcomputacionalrev2-110626155412-phpapp02/85/Seguridad-Computacional-67-320.jpg)





![(VWD RFXOWDFLyQ GH KDUGZDUH GHEH UHDOL]DUVH GH XQ PRGR FyPRGR VHJXUR 'HEH VHU
FyPRGRSDUDSRGHUXWLOL]DUORVVHUYLFLRVGHOPLVPRVLQSUREOHPDVDXQTXHQRGLUHFWDPHQWH
VLQR D WUDYpV GHO 62 HQ HVWH FDVR HO 81,; GHEH VHU VHJXUR SDUD OLEHUDU DO
SURJUDPDGRUGHODSUHRFXSDFLyQGHHYLWDUFDWiVWURIHVIXQFLyQGHODTXHVHGHEHHQFDUJDUHO
SURSLR VLVWHPD $ ORV SURJUDPDGRUHVGH '26 HVWR GH OD RFXOWDFLyQ SXHGH SDUHFHUOHVXQD
GHVYHQWDMDVLQHPEDUJRHVWRHVSRUTXHHO'26QRUHDOL]DHVWDIXQFLyQDOPHQRVGHIRUPD
FyPRGDVHJXUD
'HVGHXQDYLVLyQDPSOLDHO62GHEHVXSRQHU
x 8QHQWRUQRGHPDQWHQLPLHQWRFUHDFLyQGHSURJUDPDV
x 8Q LQWHUID] VRILVWLFDGR GH RSHUDFLRQHV SDUD HO SURJUDPDGRU XQ LQWpUSUHWH GH
FRPDQGRV
x /DFRUUHFWDJHVWLyQGHUHFXUVRVGHOVLVWHPD
'HVGHXQDYLVLyQPiVUHVWULQJLGDVHFRQVLGHUDHO62FRPRHOQ~FOHRRNHUQHOGHOVLVWHPD
FRQODVIXQFLRQHVHVWUXFWXUDVGHGDWRVQHFHVDULDVSDUD*(67,21$5UHFXUVRV$VtSXHV
HO62GHEH
x (MHFXWDUSURJUDPDV
x $VLJQDUUHFXUVRV38](https://image.slidesharecdn.com/2001-05-15seguridadcomputacionalrev2-110626155412-phpapp02/85/Seguridad-Computacional-73-320.jpg)
![x (QFDUJDUVHGHODSURWHFFLyQGHOVLVWHPD
x /DVRSHUDFLRQHVGHHQWUDGDVDOLGD
x /DJHVWLyQGHXVXDULRVSURFHVRV
x /DGHWHFFLyQGHHUURUHV
x /DPDQLSXODFLyQGHOVLVWHPDGHILFKHURV
/OHJDGRV D HVWH SXQWR ORV SURJUDPDGRUHV FRQ H[SHULHQFLD HQ '26 DGYHUWLUiQ TXH HQ OD
PDRUtD GHORVFDVRVVRQHOORVORVTXHVHHQFDUJDQGHHVWDVIXQFLRQHVHQOXJDUGHOSURSLR
VLVWHPD
81,;FRPRODPDRUtDGHORV62DFWXDOHVHVXQVLVWHPDPXOWLXVXDULRPXOWLWDUHD(VWR
LQIOXHHQODJHVWLyQGHODSURWHFFLyQGHOVLVWHPD TXHVROXFLRQDGHODVLJXLHQWHIRUPD
7RGDV ODV RSHUDFLRQHV GH ( 6 VRQ UHDOL]DGDV SRU 81,;HQ HO OODPDGR PRGR VXSHUYLVRU
PRGR GH HMHFXFLyQ HQ HO TXH HO 62 WRPD FRQWURO WRWDO GHO RUGHQDGRU DUUHEDWiQGRVHOR DO
SURJUDPDGHXVXDULR(OXVXDULRVLQHPEDUJRWLHQHODLPSUHVLyQGHVHUpOTXLHQUHDOL]DOD
RSHUDFLyQ LQYRFDQGR XQD VVWHP FDOO R OODPDGD DO VLVWHPD GHVGH SURJUDPD /D IRUPD GH
XQD VVWHP FDOO HV OD GH XQD IXQFLyQ FXDOTXLHUD HV OD IRUPD TXH WLHQH HO XVXDULR GH
LQWHUDFWXDUFRQHOVLVWHPD
8QLYHUVLGDGGHODXFD](https://image.slidesharecdn.com/2001-05-15seguridadcomputacionalrev2-110626155412-phpapp02/85/Seguridad-Computacional-74-320.jpg)
![6(*85,'$'20387$,21$/
81,;WLHQHXQDEVROXWRFRQWUROGHODPHPRULDJHVWLRQDQGROtPLWHVGH]RQDSDUDXVXDULRV
SDUD Vt PLVPR SURSRUFLRQDQGR OODPDGDV SDUD SHWLFLyQ OLEHUDFLyQ 3RGUtD FRPSDUDUVH
FRQHOPRGRSURWHJLGRGHXQH[WHQGHUGH'26
$OVHUXQ62PXOWLXVXDULRPXOWLWDUHDSHURPRQRSURFHVDGRUGHEHUHDOL]DUODJHVWLyQGH
OD 38 DVLJQiQGRVHOD R DUUHEDWiQGRVHOD D ORV SURJUDPDV GH XVXDULR VLVWHPD GH WLHPSR
FRPSDUWLGR](https://image.slidesharecdn.com/2001-05-15seguridadcomputacionalrev2-110626155412-phpapp02/85/Seguridad-Computacional-75-320.jpg)

![x 8QWUDSRLQWHUUXSFLyQHVSHFLDOKDUGZDUHTXHJHQHUDOPHQWHDQLTXLODHOSURFHVRTXH
ODSURYRFy
6LVWHPD2SHUDWLYR81,;
$QWHFHGHQWHVKLVWyULFRV
(O 62 8QL[ IXH FUHDGR D ILQDOHV GH OD GpFDGD GH ORV VREUHOD EDVH GH YDULRV WUDEDMRV
UHDOL]DGRV FRQMXQWDPHQWH SRU HO 0,7 /DERUDWRULRV %(// 'LFKRV WUDEDMRV SURHFWR
08/7,6](https://image.slidesharecdn.com/2001-05-15seguridadcomputacionalrev2-110626155412-phpapp02/85/Seguridad-Computacional-77-320.jpg)

![GHVDUUROOy SRU VX FXHQWD XQ
VLVWHPD RSHUDWLYR PRQRXVXDULR FRQ OD FDUDFWHUtVWLFD SULQFLSDO GH XQ VLVWHPD GH DUFKLYRV
MHUiUTXLFR
(O VLVWHPDHQFRQWUyPXFKRVHQWXVLDVWDVVHKL]RSRUWDEOHDOUHVFULELUVHFDVLtQWHJUDPHQWH
HQOHQJXDMHVHVXPLQLVWUyHQFyGLJRIXHQWHDODVXQLYHUVLGDGHVFRQILQHVDFDGpPLFRV
$Vt OD XQLYHUVLGDG GH DOLIRUQLD HQ %HUNHOH VH DSURSLR PRGLILFR GLFKR VLVWHPD
IXQGDPHQWDOPHQWHFRPXQLFDFLRQHVGLYHUVDVXWLOLGDGHVFRPRHOHGLWRUYL](https://image.slidesharecdn.com/2001-05-15seguridadcomputacionalrev2-110626155412-phpapp02/85/Seguridad-Computacional-79-320.jpg)

![6(*85,'$'20387$,21$/
$FWXDOPHQWHH[LVWHQGRVFRUULHQWHVODVFXDOHVFDGDYH]SRVHHQPiVHOHPHQWRVFRPXQHVOD
%6'OD6VWHP95
*HQHUDOLGDGHV
(O62 8QL[VHHQFDUJDGHFRQWURODUDVLJQDUORVUHFXUVRVItVLFRVGHORUGHQDGRUKDUGZDUH](https://image.slidesharecdn.com/2001-05-15seguridadcomputacionalrev2-110626155412-phpapp02/85/Seguridad-Computacional-81-320.jpg)

![HOHVFDOyQPiVEDMRTXHUHDOL]DWDUHDVWDOHVFRPR
HODFFHVRDORVGLVSRVLWLYRVWHUPLQDOHVGLVFRVFLQWDV](https://image.slidesharecdn.com/2001-05-15seguridadcomputacionalrev2-110626155412-phpapp02/85/Seguridad-Computacional-83-320.jpg)






![DUDFWHUtVWLFDVGHO6LVWHPD2SHUDWLYR81,;
/DVSULQFLSDOHVVRQ
8QVLVWHPDGHILFKHURVMHUiUTXLFRHQHOTXHWRGRVHHQFXHQWUDDQFODGRHQODUDt]URRW](https://image.slidesharecdn.com/2001-05-15seguridadcomputacionalrev2-110626155412-phpapp02/85/Seguridad-Computacional-90-320.jpg)
![/D
PDRUtD GH OD OLWHUDWXUD VREUH HO WHPD GLFH TXH HO VLVWHPD GH ILFKHURV 81,; HV XQ JUDIR
DFtFOLFRVLQHPEDUJRODUHDOLGDGHVTXHVHWUDWDGHXQJUDIRFtFOLFR(O'26SRUHMHPSOR
HVXQiUEROFRQXQGLUHFWRULRUDt]GHODTXHFXHOJDQVXEGLUHFWRULRVTXHDVXYH]VRQUDtFHV
GHRWURVVXEiUEROHV8QJUDIRFtFOLFRHVFRPRXQiUEROHQHOTXHVHSXHGHQHQOD]DUQRGRV
GHQLYHOHVLQIHULRUHVFRQXQQLYHOVXSHULRU(VGHFLUVHSXHGHHQWUDUHQXQVXEGLUHFWRULR
DSDUHFHUPiVFHUFDGHODUDt]GHORTXHVHHVWDED
(O VLVWHPD GH ILFKHURV HVWi EDVDGR HQ OD LGHD GH YRO~PHQHV TXH VH SXHGHQ PRQWDU
GHVPRQWDUSDUDORTXHVHOHVDVLJQDXQQRGRGHOiUEROFRPRSXQWRGHDQFODMH8QVLVWHPD
ItVLFRSXHGHGLYLGLUVHHQXQRRPiVYRO~PHQHV
81,;UHDOL]DXQULJXURVRFRQWUROGHDFFHVRDILFKHURVDGDXQRVHHQFXHQWUDSURWHJLGRSRU
XQDVHFXHQFLDGHELWV6yORVHSHUPLWHHODFFHVRJOREDODOURRWRVXSHUXVXDULR3RUWDQWRHO
XQLYHUVRGHXVXDULRVGH81,;VHHQFXHQWUDGLYLGLGRHQGRVJUXSRVSULQFLSDOHVQRVyORSDUD
8QLYHUVLGDGGHODXFD](https://image.slidesharecdn.com/2001-05-15seguridadcomputacionalrev2-110626155412-phpapp02/85/Seguridad-Computacional-91-320.jpg)

![SDUDLQLFLDUPDQLSXODU
SURFHVRV FRQFXUUHQWHV DVtQFURQRV 8Q XVXDULR SXHGH HMHFXWDU YDULRV SURFHVRV
LQWHUFDPELDUORVHLQWHUFRQHFWDUORVDWUDYpVGHSLSHVRWXEHUtDVVLPEROL]DGRVSRUHOFDUiFWHUæ
$6,,](https://image.slidesharecdn.com/2001-05-15seguridadcomputacionalrev2-110626155412-phpapp02/85/Seguridad-Computacional-93-320.jpg)
![(Q '26 WDPELpQ H[LVWH OD LGHD GHO SLSH VLQ HPEDUJR DO QR H[LVWLU
FRQFXUUHQFLD GH SURFHVRV QR VH WUDWD GH XQD FRPXQLFDFLyQ HQ WLHPSR UHDO VLQR GH XQ
SDVRGHLQIRUPDFLyQDWUDYpVGHILFKHURVWHPSRUDOHV
81,;HVXQ62GHUHGDOJRTXHPXFKRVFRQIXQGHQFRQXQ62GLVWULEXLGR3RUHOORVH
KDLQFOXLGRHQVXQ~FOHRODDUTXLWHFWXUDGHSURWRFRORVGHLQWHUQHW73,3
(OHQWRUQRGHXVXDULR81,;
6LQWHWL]DQGRORH[SXHVWRGHILQLUHPRVD81,;FRPRXQVLVWHPDPXOWLXVXDULRGHWLHPSR
FRPSDUWLGR(OXVXDULRLQWURGXFHFRPDQGRVUHFLEHUHVXOWDGRVHQXQWHUPLQDO
7RGR XVXDULR GLVSRQH GH XQ GLUHFWRULR SULYDGR OODPDGR KRPH GLUHFWRU VREUH HO TXH
H[FHSWXDQGRDOURRWVyORpOWLHQHFRQWURO
/DVHJXULGDGHQ81,;QRHVXQDGLUHFWLYDSULQFLSDOGHELGRDVXRULJHQSURSyVLWRLQLFLDO
SRUORTXHVHSXHGHUHFRUUHUWRGRHOiUEROGHILFKHURVHVGHFLUHOJUDIR](https://image.slidesharecdn.com/2001-05-15seguridadcomputacionalrev2-110626155412-phpapp02/85/Seguridad-Computacional-94-320.jpg)
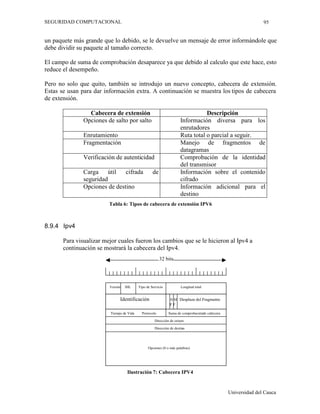
![6(*85,'$'20387$,21$/
)LORVRItDHOHPHQWDOGH81,;
3DUD81,;HOXQLYHUVRHVXQVLVWHPDGHILFKHURV1RH[LVWHQSHULIpULFRVVyORILFKHURV'H
HVWHPRGRVHXQLILFDQWRGRVORVSURFHVRV(6/RV GLUHFWRULRVVRQILFKHURVTXHFRQWLHQHQ
HQODFHV FRQ RWURV ILFKHURV 7HUPLQDOHV GLVFRV FRPSDFWRV H LPSUHVRUDV VRQ ILFKHURV HQ
WHRUtD VH SXHGH HVFULELU OHHU GH WRGRV HOORV 3DUD HQFRQWUDU ORV ILFKHURV HQ HO GLVFR HO
VLVWHPDXWLOL]DSXQWHURVOODPDGRVLQRGRV$OERUUDUXQILFKHURVLPSOHPHQWHVHERUUDVXL
QRGR SHUR DO FRQWUDULR TXH HQ '26 XQD YH] VH KD ERUUDGR DOJR HQ 81,; HV
,55(83(5$%/( D TXH QR KD IRUPD GH HQFRQWUDU GH QXHYR HO FDPLQR D OD
LQIRUPDFLyQHQGLVFR
DGDSURFHVRRSURJUDPDHQPHPRULDWLHQHXQRZQHU RSURSLHWDULRTXHHVHOVXMHWRTXHOR
KD ODQ]DGR 'HVGH VX QDFLPLHQWR DGTXLHUH ORV SHUPLVRV GHO RZQHU XDQGR XQ SURFHVR
TXHGDKXpUIDQRVHOHGHQRPLQDGHPRQLRRGDHPRQ YHUHPRVRWUDVGRVDFHSFLRQHVSDUDHVWH
WpUPLQRpVWDHVODPHQRVXVDGDSUHFLVD](https://image.slidesharecdn.com/2001-05-15seguridadcomputacionalrev2-110626155412-phpapp02/85/Seguridad-Computacional-96-320.jpg)
![(OVLVWHPDQRHV62GHWLHPSRUHDO£8,'$'2$/'(621(7$5816,67(0$
81,;3RGUtDQSHUGHUVHGDWRVTXHILJXUDQ FRPRDUFKLYDGRV(O62HMHFXWDODVyUGHQHV
FXDQGRTXLHUHDXQTXHGpSRUUHFLELGDXQDRUGHQGHHVFULWXUDHQGLVFRSXHGHHVWDUGDQGR
SULRULGDGDRWURSURJUDPDUHDOPHQWHUHDOL]DXQDODERUGHFDFKpLQWHUQD](https://image.slidesharecdn.com/2001-05-15seguridadcomputacionalrev2-110626155412-phpapp02/85/Seguridad-Computacional-97-320.jpg)
![3DUDDVHJXUDUVHGH
TXHWRGRVHUHIOHMDHQODPHPRULDGHPDVDHVGHFLUGHTXHVHKDHVFULWRGHYHUGDGORTXHVH
WHQtD TXH HVFULELU H[LVWH OD RUGHQ VQF 6L VH GHVHD DSDJDU XQ RUGHQDGRU EDMR 81,; VH
GHEHU HQWUDU DO VLVWHPD FRPR URRW R VXSHUXVXDULR HMHFXWDU OD RUGHQ KDOW 8QD YH] HO
VLVWHPD KDD UHDOL]DGR ODV RSHUDFLRQHV RSRUWXQDV OR QRWLILFDUi VH SRGUi DSDJDU OD
PiTXLQDVLQSHOLJUR
81,;GLIHUHQFLDODVPD~VFXODVGHODVPLQ~VFXODVFDVHVHQVLWLYH](https://image.slidesharecdn.com/2001-05-15seguridadcomputacionalrev2-110626155412-phpapp02/85/Seguridad-Computacional-98-320.jpg)


![6(*85,'$'20387$,21$/
3DVVZG
(VSHUDQGR XQ SDVVZRUG R SDODEUD FODYH DVRFLDGRV DO ORJLQ VL WRGR YD ELHQ D VH HVWi
GHQWUR0LHQWUDVVHWHFOHDODSDODEUDFODYHQRDSDUHFHHFRHQSDQWDOODSDUDTXHQDGLHHQORV
DOUHGHGRUHVSXHGDOHHUOD3RUHOORVLVHSURGXFHXQHUURUDOWHFOHDUKDEUiRWUDRSRUWXQLGDG
(QFDVRGHTXHQRKDDGHILQLGDQLQJXQDSDODEUDGHSDVRREYLDPHQWHQRVHSUHJXQWDUiSRU
HOOD(VWRVXHOHRFXUULUFRQHOXVXDULRURRWFXDQGR81,;HVWiUHFLpQLQVWDODGR6LXQDYH]
GHQWUR VH GHVHD VDOLU EDVWDU WHFOHDU H[LW ORJRXW R VLPSOHPHQWH 21752/' VHJ~Q HO
VLVWHPDHQTXHXQRVHHQFXHQWUH
1DGDPiVWHUPLQDUHOSURFHVRGHORJLQXQDVKHOODUUDQFDDXWRPiWLFDPHQWHDGYLHUWHGHVX
GLVSRVLFLyQ D UHFLELU FRPDQGRV PRVWUDQGR XQ SURPSW TXH SRU GHIHFWR VHUi XQR GH ORV
VtPERORV ! y HQ IXQFLyQ GH TXH VKHOO VH XVH GH VL XQR HV HO URRW R QR (VWH
SURPSWHTXLYDOHDOIDPRVR!GHO'26FRPRHVWH~OWLPRHVUHGHILQLEOH
DGHVGHGHQWURVHSXHGHHPSH]DUDMXJDUFRQDOJXQRVFRPDQGRV
(FKR
6XILQDOLGDGHVPRVWUDUPHQVDMHVHVGHFLUSUHVHQWDXQHFRGHVXVDUJXPHQWRVHQSDQWDOOD
GHPRGRLGpQWLFRDFRPRIXQFLRQDHOHFKRGHO'26/DGLIHUHQFLDHVWULEDHQTXHDOLJXDO
TXH OD PDRUtD GH ORV FRPDQGRV 81,; GLVSRQH GH XQ JUDQ Q~PHUR GH RSFLRQHV 'H
PRPHQWR VyOR VH PHQFLRQDUi OD RSFLyQ HFKRQ TXH HYLWD HO UHWRUQR GH FDUUR H LQLFLR GH
OtQHDHFKRWDPELpQVLUYHSDUDPRVWUDUYDORUHVGHYDULDEOHV3RUHMHPSOR
HFKR7(50
0RVWUDUiHOYDORUGHODYDULDEOHWHUPTXHHVXQDYDULDEOHGHODVKHOOTXHLQGLFDHOWLSRGH
WHUPLQDO RQ HVWR VH DGHODQWD OD LGHDGH TXH H[LVWHQ YDULDEOHVGHHQWRUQRDOLJXDOTXHHQ
'26GHOPLVPRPRGRSXHGHQH[DPLQDUVHPHGLDQWHODLQVWUXFFLyQVHW
KRVWQDPH
,QGLFDHOQRPEUHGHODPiTXLQDTXHDORMDHOVLVWHPD1RVHWUDWDGHOQRPEUHGHOKDUGZDUH
VLQRGHXQQRPEUHFRQTXHVHEDXWL]DDWRGRVORVVLVWHPDV81,;(VWRVHGHEHDTXH81,;
HVXQVLVWHPDHQUHGSRUWDQWRKDTXHWHQHUELHQLGHQWLILFDGDVDODVPiTXLQDV
ZKR
0XHVWUD XQD OLVWD GH ORV XVXDULRV TXH VH HQFXHQWUDQ FRQHFWDGRV HQ HVH PRPHQWR HQ HO
VLVWHPD
ZKRDPL
$XQTXHSXHGHLQGXFLUDODVRQULVDVXIXQFLyQHVLQIRUPDUOHDXQRGHTXLpQHV1RVHWUDWD
GH UHVROYHUSUREOHPDVGH SHUVRQDOLGDG HQFXDQWRXQRVHPXHYHXQSRFRSRUHOVLVWHPD
8QLYHUVLGDGGHODXFD](https://image.slidesharecdn.com/2001-05-15seguridadcomputacionalrev2-110626155412-phpapp02/85/Seguridad-Computacional-101-320.jpg)
![6(*85,'$'20387$,21$/
VLHPSUH TXH GLVSRQJD GH PiV GH XQD FXHQWD GHVFXEULUi TXH HV XQ FRPDQGR UHDOPHQWH
QHFHVDULR
OV
8QD YH] HO XVXDULR VH KD VLWXDGR VDEH GyQGH HVWi TXLpQ HV FRQYLHQH DEULU ORV RMRV
PLUDU DOUHGHGRU OV DEUHYLDWXUD GH /LVW PXHVWUD HO FRQWHQLGR GH XQ GLUHFWRULR 6X
IXQFLRQDPLHQWRVLQWD[LVHQDQiORJRDOGLUGHO'26$VtSXHVODVLQWD[LVHV
OVRSFLRQHV@SDWK@PiVFDUDGHILFKHURV@
(QWUHODVRSFLRQHVODVPiVXVDGDVVRQ
OTXHLQGLFDSHUPLVRVIHFKDSURSLHWDULR
DOLVWDWDPELpQORVILFKHURV
(Q81,;ORVQRPEUHVGHILFKHURQRVHYHQVXMHWRVDODVUHJODVGH'26TXHORVOLPLWDD
FDUDFWHUHV XQD H[WHQVLyQ GH FDUDFWHUHV VHSDUDGRV SRU XQ SXQWR VLQR TXH SXHGHQWHQHU
XQDORQJLWXGHQWUHFDUDFWHUHVHQIXQFLyQGHODYHUVLyQ3RURWUDSDUWHH[LVWHQORV
PLVPRV ZLOFDUGV GHO '26
DXQTXH VX XVR GLILHUH OLJHUDPHQWH D TXH SHUPLWH
H[SUHVLRQHV GHO WLSR
FDGHQD@
3DUD 81,; XQ ILFKHUR FXR QRPEUH FRPLHQ]D SRU HO
FDUiFWHUSXQWR](https://image.slidesharecdn.com/2001-05-15seguridadcomputacionalrev2-110626155412-phpapp02/85/Seguridad-Computacional-102-320.jpg)
![FRPRSURILOHHVXQILFKHURRFXOWR~QLFDPHQWHVHUiOLVWDGRVLVHXWLOL]D
ODRSFLyQD
FDW
0XHVWUDHOFRQWHQLGRGHXQILFKHURGHOPLVPRPRGRTXHHOWSHGHO'26(TXLYDOHWHFOHDU
FDWORJLQHQ81,;TXHWSHORJLQHQ'26 DXQTXHORJLQQRHVQRPEUHYiOLGRHQ'26](https://image.slidesharecdn.com/2001-05-15seguridadcomputacionalrev2-110626155412-phpapp02/85/Seguridad-Computacional-103-320.jpg)