Security Threats in IT Infographic
•
0 likes•473 views
NTT's breadth and scope allowed it to analyse three billion IT Security attacks in 2013, the results was combined to produce the Global Threat Intelligence Report. This infographic is an extract from the Global Threat Intelligence Report.
Report
Share
Report
Share
Download to read offline
Recommended
The New Technology Elite March 2012

This document summarizes a presentation by Vinnie Mirchandani on the rise of the "technology elite." Mirchandani discusses 12 attributes that define the technology elite, including being elegant, exponential, efficient, mobile, maverick, malleable, physical, paranoid, pragmatic, speedy, social, and sustainable. He provides examples for each attribute, such as Virgin America demonstrating elegance and Google demonstrating sustainability through green energy initiatives. Overall, the presentation outlines the key characteristics of innovative technology leaders and companies that are shaping the industry.
iot-bringing-trust-to-iot[1]![iot-bringing-trust-to-iot[1]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![iot-bringing-trust-to-iot[1]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
The document discusses the potential of the Internet of Things (IoT) to generate $19 trillion in value over the next decade. However, it also notes that security concerns could hamper widespread adoption of IoT technologies if not addressed properly. The document advocates for a three-pronged approach to building trust in the IoT ecosystem through reliable connectivity, reliable security, and agile monetization solutions.
Homework gafam

The document discusses GAFAM, which refers to the largest technology companies: Google, Amazon, Facebook, Apple, and Microsoft. It notes their dominant market positions and massive market capitalizations. It also examines GAFAM's extensive financial control over the digital ecosystem through platforms and services. Finally, it looks at antitrust issues related to GAFAM's unmatched market dominance and growing power over the internet's architecture.
Top strategic predictions for 2016 and beyond

The document summarizes predictions from a Gartner report about emerging technologies between 2016 and 2021:
- Smart machines will take on more human tasks and the relationship between people and machines will transition from cooperative to codependent to competitive.
- Nearly half of all devices will have intelligence to request support by 2018.
- Robots and autonomous software will increasingly perform jobs like content creation, economic transactions, and workforce supervision.
- Security challenges will grow as digital capabilities expand into new systems like smart buildings, and customers will be responsible for most cloud security failures by 2021.
2019 Keynote at the Techno Security and Digital Forensics Conference - The Ve...

As the world embraces digital services and automation of critical systems, understanding risk, attributing actions, and deciphering attack methods will be crucial to the proliferation of connected technology. Trust is key, but transparency is greatly obscured. Forensics will grow to become the verification of truth and will play an ever-increasing role in understanding responsibility and controlling the dissemination of Fear, Uncertainty, and Doubt through actuarial data. Let’s explore the new areas, challenges, and opportunities for the bright future of digital forensics
Top 20 Machine to Machine (M2M) Companies 2018

For a report overview of this report please contact sara.peerun@visiongain.com
(+44 (0) 20 7336 6100) or refer to our website:
https://www.visiongain.com/Report/2156/Top-20-Machine-to-Machine-(M2M)-Companies-2018
The consumer in 2025 - Digital Futures 2025

•How consumers will – and won’t – change •What this will mean for the TMT value chain •Which businesses will thrive and why. Rob Gallagher, Director of Research - Media, Entertainment & Consumer, Ovum
Digital Marketing in Business

Digital Marketing has been a great "term" used globally, we interact with these terms regularly. Understand the need of Digital Marketing in your business area and boost your business
Recommended
The New Technology Elite March 2012

This document summarizes a presentation by Vinnie Mirchandani on the rise of the "technology elite." Mirchandani discusses 12 attributes that define the technology elite, including being elegant, exponential, efficient, mobile, maverick, malleable, physical, paranoid, pragmatic, speedy, social, and sustainable. He provides examples for each attribute, such as Virgin America demonstrating elegance and Google demonstrating sustainability through green energy initiatives. Overall, the presentation outlines the key characteristics of innovative technology leaders and companies that are shaping the industry.
iot-bringing-trust-to-iot[1]![iot-bringing-trust-to-iot[1]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![iot-bringing-trust-to-iot[1]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
The document discusses the potential of the Internet of Things (IoT) to generate $19 trillion in value over the next decade. However, it also notes that security concerns could hamper widespread adoption of IoT technologies if not addressed properly. The document advocates for a three-pronged approach to building trust in the IoT ecosystem through reliable connectivity, reliable security, and agile monetization solutions.
Homework gafam

The document discusses GAFAM, which refers to the largest technology companies: Google, Amazon, Facebook, Apple, and Microsoft. It notes their dominant market positions and massive market capitalizations. It also examines GAFAM's extensive financial control over the digital ecosystem through platforms and services. Finally, it looks at antitrust issues related to GAFAM's unmatched market dominance and growing power over the internet's architecture.
Top strategic predictions for 2016 and beyond

The document summarizes predictions from a Gartner report about emerging technologies between 2016 and 2021:
- Smart machines will take on more human tasks and the relationship between people and machines will transition from cooperative to codependent to competitive.
- Nearly half of all devices will have intelligence to request support by 2018.
- Robots and autonomous software will increasingly perform jobs like content creation, economic transactions, and workforce supervision.
- Security challenges will grow as digital capabilities expand into new systems like smart buildings, and customers will be responsible for most cloud security failures by 2021.
2019 Keynote at the Techno Security and Digital Forensics Conference - The Ve...

As the world embraces digital services and automation of critical systems, understanding risk, attributing actions, and deciphering attack methods will be crucial to the proliferation of connected technology. Trust is key, but transparency is greatly obscured. Forensics will grow to become the verification of truth and will play an ever-increasing role in understanding responsibility and controlling the dissemination of Fear, Uncertainty, and Doubt through actuarial data. Let’s explore the new areas, challenges, and opportunities for the bright future of digital forensics
Top 20 Machine to Machine (M2M) Companies 2018

For a report overview of this report please contact sara.peerun@visiongain.com
(+44 (0) 20 7336 6100) or refer to our website:
https://www.visiongain.com/Report/2156/Top-20-Machine-to-Machine-(M2M)-Companies-2018
The consumer in 2025 - Digital Futures 2025

•How consumers will – and won’t – change •What this will mean for the TMT value chain •Which businesses will thrive and why. Rob Gallagher, Director of Research - Media, Entertainment & Consumer, Ovum
Digital Marketing in Business

Digital Marketing has been a great "term" used globally, we interact with these terms regularly. Understand the need of Digital Marketing in your business area and boost your business
Meeting consumer needs, now and in the future - Digital Futures 2025

• Meeting the changing needs and expectations of consumers • How Sky has evolved to seize the opportunities the changing media landscape has created • What the future holds
Mai Fyfield, Chief Strategy Officer, Sky
Infographic on Smartphone Revolution

Infographic follows Andy Kirk's Three Principles of Good Visualization Design.
The infographic contains the information on both the negatives and positives of the smartphone boom in the USA.
8 graphs have been created in total,
1) Number of smartphone users in US – year wise
2) Evolution of smartphone – 1993 to 2012
3) Most preferred brand of smartphone
4) Number of internet users – State wise
5) Correlation plot between smartphone users and internet users in New Hampshire
6) Correlation plot between smartphone users, internet users and GDP of US – Year wise
7) Timeframe in which smartphones are being used – Before sleeping and after waking up
8) Smartphone which emits the highest radiation
Presentasi ltn nu

This document provides key digital statistics for Indonesia as of January 2018, including:
- Total population of 265.4 million with 56% living in urban areas
- 132.7 million internet users at a 50% penetration rate
- 130 million active social media users and 177.9 million unique mobile users at penetration rates of 49% and 67% respectively
- Common device usage among adults including 91% for mobile phones, 60% for smartphones, and 22% for laptop/desktop computers
- Average daily internet use of 8 hours and 51 minutes, social media use of 3 hours and 23 minutes, and TV viewing of 2 hours and 45 minutes
10 Top Newsworthy Tech Industry Headlines Of 2020 | Other Than COVID

TikTok was sold to an American company, flip phones had renewed interest and the EU wanted universal phone chargers, and Google partnered with AT&T on 5G networks. Twitter and SolarWinds suffered major hacks, Joe Biden became president-elect, and remote working grew significantly due to the pandemic while Nvidia's acquisition of ARM and IBM's split also made headlines in the tech industry in 2020 outside of COVID-19 news.
Sustainability, Best's Review, December 2018

Insurers must recognize the financial impact and benefit of investing in sustainable technology.
"Given the raison d'etre of the insurance industry is risk, despite sustainability's macro-economics being hard to qualify and quantify at a corporate business level, insurers need to take a more active role."
CES 2015 - Social Media Trends

Over CES 2015 from January 6-9th, there was a total of 735,437 social media posts, which was a 105% increase from the previous year. The most discussed topics were wearable technology, television, and gaming. The top brands mentioned were Mercedes-Benz, Dell, Asus, Lenovo, and Logitech. On Twitter, the most retweeted users were @Logitech, @CNET, @IntlCES, and @Intel. The most used hashtags were #CES2015, #CES, and #Android. The gender breakdown of social media discussions was 63% male and 37% female.
Telecom market growth awaits 5 g launch

5G is a crucial component of the global digitally connected ecosystem, currently. It is estimated that between 2019 and 2025, the number of 5G users will increase by roughly 1.2 Bn, globally. It will be interesting to see how the diverse factors come in to play for the massive launch of 5G technology. The new report on the on 5G technology entails insights into the market and puts forward a global viewpoint of 5G industry.
IQ Telecom - Spotlight On Mobile Trends

IQ Telecom shines a spotlight on some of the major current trends in the mobile industry.
Follow our SlideShare page for more trending news and slidedecks!
Information technology

Information technology (IT) is the use of computers to store, retrieve, transmit, and manipulate data,[1] or information, often in the context of a business or other enterprise.[2] IT is considered to be a subset of information and communications technology (ICT)
5G Infrastructure Investments

Federal infrastructure spending is expected to increase regardless of who wins the 2020 election, and 5G infrastructure will be a part of this. 5G networks will provide much faster data transfer speeds and connectivity between devices. The leading Western companies developing 5G technology are Ericsson, Nokia, and Qualcomm, which are seen as more trustworthy options than Chinese companies like Huawei. Investing in these three Western companies is recommended as a way to profit from the development of 5G infrastructure globally.
ADAB OF DIGITAL AWARENESS

This document discusses internet usage in Malaysia and cybersecurity issues. It provides statistics on internet users in Malaysia, the types of cybersecurity incidents reported, and the increasing number of incidents over time. It also outlines some of the main methods of sharing information online and risks of over-sharing personal information. The document encourages internet users to protect themselves by being discreet, skeptical, thoughtful, professional, and wary of what they share online.
CIS 2015 Security Without Borders: Taming the Cloud and Mobile Frontier - And...

This document introduces a new identity security system called Sierra Border Security V1.0. It discusses how the assumptions around internet and enterprise security have changed over time as the perimeter has expanded with new technologies. The key challenges mentioned are that identity is now too weak and disconnected to protect organizations at scale. The proposed new system aims to evolve authentication beyond single-factor to continuous multi-factor authentication using standards-based interactions. It will leverage big data and intelligence for dynamic access control and move to identity-based security definitions.
Applause case study 

Applause, a mobile app testing platform, received positive press coverage from over 30 publications for its product and growth. Many articles discussed Applause's new funding round, partnerships, and how its technology allows mobile apps to gather user feedback remotely. The wide range of publications, from tech outlets to finance journals, showed Applause's success in garnering interest across industries.
E-Commerce In India

This document discusses the digital revolution and its impact on various areas. It summarizes that the digital revolution refers to the transition from analog to digital technologies starting in the 1980s. It is ongoing and marks the beginning of the information era. While digital technologies are exponentially increasing productivity, they are also transforming employment and causing unemployment issues due to innovation. The document then provides statistics on India's growing e-commerce market size and the major product segments. It also defines virtual communities and discusses key aspects of the digital economy such as different industries, technologies, and its impact on business, government, and society.
Data Con LA 2018 Keynote - The secret to your big data success by Tim Eusterman

The document discusses how organizations can succeed with big data by integrating, automating, and orchestrating their digital business automation processes. It provides an example of how Malwarebytes leverages big data, artificial intelligence, and the cloud to protect millions of users by processing over 1.7 trillion data records per day to detect malware threats and remediate issues for their customers. The document advertises learning more at the BMC Software booth about their Control-M product and a chance to win a drone.
Digital Trend Study 2019 - "How to Survive in Digital 2019" - Teaser

This document provides a teaser and overview for a 2019 digital trend study titled "How to Survive in Digital 2019". It notes that over $1 trillion will be invested in 2019 across tech, startups, and giant companies' AI labs. This massive investment and speed of innovation will challenge companies. It previews five chapters covering topics like the impact of players like Softbank's $100 billion tech fund and the growth of apps like TikTok, as well as the expansion of Google Assistant and Chinese retailer JD.com into new markets. The study will provide 15 survival tips for navigating this changing digital landscape in 2019.
Presentación Alessander Firmino - eCommerce Day Bogotá 2015 

Diapositivas presentadas por Alessander Firmino, Managing Director Latam & Brasil Criteo, en el eCommerce Day Bogotá 2015 en la plenaria "TRENDS PITCH ECOMMERCE II – LO QUE VIENE EN ECOMMERCE CENTRADO EN RESULTADOS
Y CONVERSIÓN.".
Ready or Not: The Next Dialtone

These slides were created for Mr. Winston Damarillo's (Chairman of Amihan Global Strategies) talk at the Asian Carriers Conference in Cebu, Philippines, on Wednesday, September 13, 2017.
SEMPL 19: SNEHA NAGESH, Global Search Business Director, PHD Global Business UK

1) Stage I from 1950-1995 saw the introduction and spread of screens and the world wide web.
2) Stage II from 1990-2015 involved organizing information through search engines, browsers, and apps.
3) Stage III from 2010-2025 focuses on machine learning improving information extraction through virtual assistants and other technologies.
Innovation & Business Acquisitions of Smart Security

This document discusses trends in the home security market. It notes that while security systems may contribute to a decrease in break-ins, currently only 7.35% of American homes have a security system. It also states that the security industry will be worth $220 billion by 2015. The document outlines that traditional alarm systems rely on dispatch centers that rarely stop robberies, and are poorly designed and difficult to customize. Upcoming startups aim to provide more affordable and efficient alternatives to major security companies.
St Edmund's College prepares it's students for the future with NTT Communicat...

St Edmund's College prepares it's students for the future with NTT Communicat...NTT Communications ICT Solutions
To meet the demands of tomorrow’s information, St Edmunds needed to ensure its students would have reliable and fast access to technology for years to come. After a competitive tender for solutions and implementation partners St Edmund’s established a partnership with NTT Communications ICT Solutions (NTT ICT).Cooking on board a yacht

One of the benefits of a luxury yacht charter is the ability to cook your favorites on board, and dine whenever you want with some of the best views the world has to offer. There is nothing quite like sitting on deck at sunset tucking into a homemade feast with friends and loved ones. Cooking on board a yacht however can be quite a different experience, and takes a little more planning than your usual meal.
More Related Content
What's hot
Meeting consumer needs, now and in the future - Digital Futures 2025

• Meeting the changing needs and expectations of consumers • How Sky has evolved to seize the opportunities the changing media landscape has created • What the future holds
Mai Fyfield, Chief Strategy Officer, Sky
Infographic on Smartphone Revolution

Infographic follows Andy Kirk's Three Principles of Good Visualization Design.
The infographic contains the information on both the negatives and positives of the smartphone boom in the USA.
8 graphs have been created in total,
1) Number of smartphone users in US – year wise
2) Evolution of smartphone – 1993 to 2012
3) Most preferred brand of smartphone
4) Number of internet users – State wise
5) Correlation plot between smartphone users and internet users in New Hampshire
6) Correlation plot between smartphone users, internet users and GDP of US – Year wise
7) Timeframe in which smartphones are being used – Before sleeping and after waking up
8) Smartphone which emits the highest radiation
Presentasi ltn nu

This document provides key digital statistics for Indonesia as of January 2018, including:
- Total population of 265.4 million with 56% living in urban areas
- 132.7 million internet users at a 50% penetration rate
- 130 million active social media users and 177.9 million unique mobile users at penetration rates of 49% and 67% respectively
- Common device usage among adults including 91% for mobile phones, 60% for smartphones, and 22% for laptop/desktop computers
- Average daily internet use of 8 hours and 51 minutes, social media use of 3 hours and 23 minutes, and TV viewing of 2 hours and 45 minutes
10 Top Newsworthy Tech Industry Headlines Of 2020 | Other Than COVID

TikTok was sold to an American company, flip phones had renewed interest and the EU wanted universal phone chargers, and Google partnered with AT&T on 5G networks. Twitter and SolarWinds suffered major hacks, Joe Biden became president-elect, and remote working grew significantly due to the pandemic while Nvidia's acquisition of ARM and IBM's split also made headlines in the tech industry in 2020 outside of COVID-19 news.
Sustainability, Best's Review, December 2018

Insurers must recognize the financial impact and benefit of investing in sustainable technology.
"Given the raison d'etre of the insurance industry is risk, despite sustainability's macro-economics being hard to qualify and quantify at a corporate business level, insurers need to take a more active role."
CES 2015 - Social Media Trends

Over CES 2015 from January 6-9th, there was a total of 735,437 social media posts, which was a 105% increase from the previous year. The most discussed topics were wearable technology, television, and gaming. The top brands mentioned were Mercedes-Benz, Dell, Asus, Lenovo, and Logitech. On Twitter, the most retweeted users were @Logitech, @CNET, @IntlCES, and @Intel. The most used hashtags were #CES2015, #CES, and #Android. The gender breakdown of social media discussions was 63% male and 37% female.
Telecom market growth awaits 5 g launch

5G is a crucial component of the global digitally connected ecosystem, currently. It is estimated that between 2019 and 2025, the number of 5G users will increase by roughly 1.2 Bn, globally. It will be interesting to see how the diverse factors come in to play for the massive launch of 5G technology. The new report on the on 5G technology entails insights into the market and puts forward a global viewpoint of 5G industry.
IQ Telecom - Spotlight On Mobile Trends

IQ Telecom shines a spotlight on some of the major current trends in the mobile industry.
Follow our SlideShare page for more trending news and slidedecks!
Information technology

Information technology (IT) is the use of computers to store, retrieve, transmit, and manipulate data,[1] or information, often in the context of a business or other enterprise.[2] IT is considered to be a subset of information and communications technology (ICT)
5G Infrastructure Investments

Federal infrastructure spending is expected to increase regardless of who wins the 2020 election, and 5G infrastructure will be a part of this. 5G networks will provide much faster data transfer speeds and connectivity between devices. The leading Western companies developing 5G technology are Ericsson, Nokia, and Qualcomm, which are seen as more trustworthy options than Chinese companies like Huawei. Investing in these three Western companies is recommended as a way to profit from the development of 5G infrastructure globally.
ADAB OF DIGITAL AWARENESS

This document discusses internet usage in Malaysia and cybersecurity issues. It provides statistics on internet users in Malaysia, the types of cybersecurity incidents reported, and the increasing number of incidents over time. It also outlines some of the main methods of sharing information online and risks of over-sharing personal information. The document encourages internet users to protect themselves by being discreet, skeptical, thoughtful, professional, and wary of what they share online.
CIS 2015 Security Without Borders: Taming the Cloud and Mobile Frontier - And...

This document introduces a new identity security system called Sierra Border Security V1.0. It discusses how the assumptions around internet and enterprise security have changed over time as the perimeter has expanded with new technologies. The key challenges mentioned are that identity is now too weak and disconnected to protect organizations at scale. The proposed new system aims to evolve authentication beyond single-factor to continuous multi-factor authentication using standards-based interactions. It will leverage big data and intelligence for dynamic access control and move to identity-based security definitions.
Applause case study 

Applause, a mobile app testing platform, received positive press coverage from over 30 publications for its product and growth. Many articles discussed Applause's new funding round, partnerships, and how its technology allows mobile apps to gather user feedback remotely. The wide range of publications, from tech outlets to finance journals, showed Applause's success in garnering interest across industries.
E-Commerce In India

This document discusses the digital revolution and its impact on various areas. It summarizes that the digital revolution refers to the transition from analog to digital technologies starting in the 1980s. It is ongoing and marks the beginning of the information era. While digital technologies are exponentially increasing productivity, they are also transforming employment and causing unemployment issues due to innovation. The document then provides statistics on India's growing e-commerce market size and the major product segments. It also defines virtual communities and discusses key aspects of the digital economy such as different industries, technologies, and its impact on business, government, and society.
Data Con LA 2018 Keynote - The secret to your big data success by Tim Eusterman

The document discusses how organizations can succeed with big data by integrating, automating, and orchestrating their digital business automation processes. It provides an example of how Malwarebytes leverages big data, artificial intelligence, and the cloud to protect millions of users by processing over 1.7 trillion data records per day to detect malware threats and remediate issues for their customers. The document advertises learning more at the BMC Software booth about their Control-M product and a chance to win a drone.
Digital Trend Study 2019 - "How to Survive in Digital 2019" - Teaser

This document provides a teaser and overview for a 2019 digital trend study titled "How to Survive in Digital 2019". It notes that over $1 trillion will be invested in 2019 across tech, startups, and giant companies' AI labs. This massive investment and speed of innovation will challenge companies. It previews five chapters covering topics like the impact of players like Softbank's $100 billion tech fund and the growth of apps like TikTok, as well as the expansion of Google Assistant and Chinese retailer JD.com into new markets. The study will provide 15 survival tips for navigating this changing digital landscape in 2019.
Presentación Alessander Firmino - eCommerce Day Bogotá 2015 

Diapositivas presentadas por Alessander Firmino, Managing Director Latam & Brasil Criteo, en el eCommerce Day Bogotá 2015 en la plenaria "TRENDS PITCH ECOMMERCE II – LO QUE VIENE EN ECOMMERCE CENTRADO EN RESULTADOS
Y CONVERSIÓN.".
Ready or Not: The Next Dialtone

These slides were created for Mr. Winston Damarillo's (Chairman of Amihan Global Strategies) talk at the Asian Carriers Conference in Cebu, Philippines, on Wednesday, September 13, 2017.
SEMPL 19: SNEHA NAGESH, Global Search Business Director, PHD Global Business UK

1) Stage I from 1950-1995 saw the introduction and spread of screens and the world wide web.
2) Stage II from 1990-2015 involved organizing information through search engines, browsers, and apps.
3) Stage III from 2010-2025 focuses on machine learning improving information extraction through virtual assistants and other technologies.
Innovation & Business Acquisitions of Smart Security

This document discusses trends in the home security market. It notes that while security systems may contribute to a decrease in break-ins, currently only 7.35% of American homes have a security system. It also states that the security industry will be worth $220 billion by 2015. The document outlines that traditional alarm systems rely on dispatch centers that rarely stop robberies, and are poorly designed and difficult to customize. Upcoming startups aim to provide more affordable and efficient alternatives to major security companies.
What's hot (20)
Meeting consumer needs, now and in the future - Digital Futures 2025

Meeting consumer needs, now and in the future - Digital Futures 2025
10 Top Newsworthy Tech Industry Headlines Of 2020 | Other Than COVID

10 Top Newsworthy Tech Industry Headlines Of 2020 | Other Than COVID
CIS 2015 Security Without Borders: Taming the Cloud and Mobile Frontier - And...

CIS 2015 Security Without Borders: Taming the Cloud and Mobile Frontier - And...
Data Con LA 2018 Keynote - The secret to your big data success by Tim Eusterman

Data Con LA 2018 Keynote - The secret to your big data success by Tim Eusterman
Digital Trend Study 2019 - "How to Survive in Digital 2019" - Teaser

Digital Trend Study 2019 - "How to Survive in Digital 2019" - Teaser
Presentación Alessander Firmino - eCommerce Day Bogotá 2015 

Presentación Alessander Firmino - eCommerce Day Bogotá 2015
SEMPL 19: SNEHA NAGESH, Global Search Business Director, PHD Global Business UK

SEMPL 19: SNEHA NAGESH, Global Search Business Director, PHD Global Business UK
Innovation & Business Acquisitions of Smart Security

Innovation & Business Acquisitions of Smart Security
Viewers also liked
St Edmund's College prepares it's students for the future with NTT Communicat...

St Edmund's College prepares it's students for the future with NTT Communicat...NTT Communications ICT Solutions
To meet the demands of tomorrow’s information, St Edmunds needed to ensure its students would have reliable and fast access to technology for years to come. After a competitive tender for solutions and implementation partners St Edmund’s established a partnership with NTT Communications ICT Solutions (NTT ICT).Cooking on board a yacht

One of the benefits of a luxury yacht charter is the ability to cook your favorites on board, and dine whenever you want with some of the best views the world has to offer. There is nothing quite like sitting on deck at sunset tucking into a homemade feast with friends and loved ones. Cooking on board a yacht however can be quite a different experience, and takes a little more planning than your usual meal.
Retro Responsive: From Fixed-Width to Flexible in 55 Minutes

Would you like to make your website work on a variety of screens, from tiny mobile devices to enormous desktops? In this session, we'll demonstrate how to retrofit a fixed-width site with basic responsive design features. You'll learn about tools and techniques for previewing your responsive site, find out how to create scalable images, discover ways to plan flexible and consistent web typography, and see the latest design approaches for responsive menu systems. Some experience with HTML and CSS will help you get the most out of this session.
Omanvaa mobile app

The OMANVAA app allows users to select herbs to display information about, provides web access for further research, and offers the option to create an account for efficient service delivery or continue anonymously.
InnoYouth kursus om innovation i AT (Almen Studieforberedelse) på Maribo Gymn...

Slideshow fra InnoYouth kursus om innovation i AT (Almen Studieforberedelse) på Maribo Gymnasium d. 25 marts 2014
الأمة والحاكم

الى طلبة العلم وأعلام الدعوة والصمود...
الى من يتصدون للباطل بلسانهم وبيانهم للحق ليجلو الغشاوة عن العيون ليعروا الباطل كي يحشد له الحق جنده..
الى من نلمح فيهم الإخلاص والغيرة على هذا الدين وهذه الأمة الكريمة..
نقدم لكم هذا الجهد العلمي الدافع في اتجاه بيان الحق وضبط العلاقة بين الحاكم والأمة وتجلية حقيقة أوضاع التغلب من حيث الحديث والأدلة الشرعية مع النظر الى أثر قبولها بإطلاق على مدار التاريخ..
نقدم لكم هذا الجهد راجين من ربنا تعالى قبوله من صاحبه ـ رحمه الله ـ وراجين من الله تعالى أن يحسن أثره في قلوبكم وفي واقعنا الأليم.. منتظرين من ربنا تعالى فرجا قريبا وفتحا عاجلا..
http://ahlusunnah.org/node/298829
http://ahlusunnah.org/sites/default/files/books/nation_and_ruling.pdf
Content as strategy: creating value throughout the consumer’s journey

Content is King and a King is a strategist! Digital Content is strategy because it creates customer value that leads to engagement, loyalty and differentiation. How can a publisher identify, create and manage the pieces of content that will build the strategic customer value puzzle? Understanding the consumer’s journey – the steps and means used through the buying process is the right tool to do so.
10 reasons to do a Langkawi yacht charter

Here are 10 reasons why you should do a Langkawi yacht charter and explore this magical place for yourself; see more at: http://www.simpsonyachtcharter.com/5-reasons-to-do-a-langkawi-yacht-charter-part-1/
LSN Lead System Network Presentation 100% Commisions

Join us here: http://leadsystemnetwork.com/smartmarket
Welcome to your last stop to all of your marketing tools all in one package! LSN is perfect for any marketer who wants to leverage the internet, as well as mobile technology, to support them in selling any program or product!
Tags:
Live Chat,
Social media inviters,
Webinar Platform,
Google Hangouts,
Viral Blogging Platform,
LSN,
LSN results,
LSN truth,
LSN report,
LSN launch,
LSN success,
LSN update,
LSN cash,
LSN compensation plan,
LSN review,
LSN scam,
Lead System Network,
Lead System Network truth,
Lead System Network report,
Lead System Network launch,
Lead System Network success,
Lead System Network update,
Lead System Network cash,
Lead System Network compensation plan,
Lead System Network review,
Lead System Network scam,
Outline of maiden speech

Danielle Palmer outlines her maiden speech in parliament which will discuss same-sex marriage, the whale watching industry in Hervey Bay and threats from Japanese whaling, the treatment of asylum seekers, and infrastructure needs in Hervey Bay. She will acknowledge the traditional owners of the land, thank her constituents, and provide background on herself and Hervey Bay before discussing each of the five topics in her speech using facts and rhetoric to support her positions.
Content in customer's journey

Το περιεχόμενο ως προστιθέμενη αξία για τον αγοραστή, σε όλη τη διάρκεια του κύκλου απόφασης, αγοράς, χρήσης.
Create new kinds of multiuser experiences using hydna and Unity

Hydna is a hosted backend into which you can send data and have it instantly appear on other devices.
Viewers also liked (15)
St Edmund's College prepares it's students for the future with NTT Communicat...

St Edmund's College prepares it's students for the future with NTT Communicat...
Retro Responsive: From Fixed-Width to Flexible in 55 Minutes

Retro Responsive: From Fixed-Width to Flexible in 55 Minutes
InnoYouth kursus om innovation i AT (Almen Studieforberedelse) på Maribo Gymn...

InnoYouth kursus om innovation i AT (Almen Studieforberedelse) på Maribo Gymn...
Content as strategy: creating value throughout the consumer’s journey

Content as strategy: creating value throughout the consumer’s journey
LSN Lead System Network Presentation 100% Commisions

LSN Lead System Network Presentation 100% Commisions
Create new kinds of multiuser experiences using hydna and Unity

Create new kinds of multiuser experiences using hydna and Unity
Similar to Security Threats in IT Infographic
Deception Technology Market – Overview of advancements in innovation 2025

Computing systems and servers are largely affected by numerous security issues such as viruses, malware, cyber-attacks, worm infections, trojan attacks, and others.
Cyberattacks on the Rise Infographic

For more information, visit http://sparkcognition.com
Cybersecurity is the number one priority for both industry and government sectors. In fact, $90 trillion could be lost by 2030 due to cyberattacks if cybersecurity fails to accelerate. What are we doing now and what’s the future?
Global Cyber Security Overview | TechSci Research 

Simple Cyber Security Overview that provide you a simple way to understand the cyber security and their benefits. https://www.techsciresearch.com/
Digital Transformation & Cloud Profitability

A quick view about Digital Transformation and what's happening with Industries across the globe.
A guidance to IT Channel to accelerate Cloud Profitability with valuable resources for download.
The 10 Fastest Growing Cyber Security Companies of 2017

The 10 Fastest Growing Cyber Security Companies of 2017Insights success media and technology pvt ltd
- Cybersecurity spending has grown significantly over the past decade, from $3.5 billion in 2004 to an estimated $120 billion in 2017, driven largely by increasing cybercrime.
- Many large companies have significantly increased their cybersecurity budgets in response, including Bank of America which has an unlimited budget for cybersecurity, JPMorgan Chase which doubled its budget to $500 million, and Microsoft which invests over $1 billion annually.
- However, small and medium businesses are particularly vulnerable as they bear 72% of cyber attacks but often lack the resources of larger companies to implement robust cybersecurity programs. Highground Cyber aims to help small and mid-market CEOs protect their companies through comprehensive cybersecurity solutions.Cost of Cybercrime Study in Financial Services: 2019 Report

Now in its 9th year, this new Accenture presentation explores the impact associated with cybercrime, quantifying the cost of cyberattacks and analyzing trends in malicious activities in the financial services industry. And this year for the first time, we look to the future so that financial services organizations can better target their funds and resources and open up new revenue opportunities to unlock economic value.
Pat Pather- Cyber Security Unchartered: Vigilance, Innovation and Adaptability

Pat Pather, Chief Executive Officer at Forensic Sciences Institute, delivered a presentation on Cyber Security Unchartered: Vigilance, Innovation and Adaptability- Exploring the Depths of Cybersecurity, at Public Sector Cybersecurity Summit 2023 on the 3rd of October 2023. #PublicSec2023 #Conference #Cybersecurity #PublicSector
Security transformation: Helping you manage digital risk

Una brecha es algo que es imposible de evitar con absoluta certeza, pero la capacidad de las empresas para reaccionar y responder a una situación como esta, es lo que permite que pueda minimizar los impactos y mantenerse resiliente frente a una situación adversa. Es por esto que cada vez se hace más importante contar con soluciones que permitan realizar la gestión del riesgo de manera integrada y con un mayor nivel de madurez, que brinden la posibilidad de tener una visión completa de lo que está afectando la seguridad de la empresa y responder de manera efectiva y alineada con lo que realmente necesita el negocio
Digital Resilience flipbook

The document discusses the need for organizations to build a "Digital Fortress" to protect against increasing cyber threats. Recent cyber attacks on large companies showed that cyber security needs to be a top priority. The author proposes a model called DRONE (Digital Resilience Operational Network Ecosystem) to help organizations establish real-time risk management, identity access management, and governance to improve their digital resilience through early threat recognition and response. Adopting the DRONE model can help organizations leverage security best practices and government initiatives to strengthen their cyber defenses.
Digital Resilience flipbook

The document discusses the need for organizations to build a "Digital Fortress" to protect against increasing cyber threats. Recent cyber attacks on large companies showed that even major banks are vulnerable. The risks are exacerbated by new technologies and changing business models. To establish effective digital resilience, the document proposes a model called DRONE (Digital Resilience Operational Network Ecosystem) that includes real-time risk management, identity access management, and a security excellence center to provide insight into cyber risks. The model also emphasizes governance, employee awareness, and frequent testing to manage threats both within and outside an organization.
Foro Empresarial Perú 2017 - Tendencias impactando Ciudades & Negocios

The document discusses several unstoppable trends affecting cities and businesses, including digital transformation, disruptive technologies, and megatrends. Key points include: (1) Digital transformation is driving the 4th industrial revolution through technologies like artificial intelligence, blockchain, and 5G. (2) Emerging technologies like augmented reality, autonomous robots, 3D printing, and artificial intelligence will enable digital transformation. (3) Automation is rising with the autonomous vehicle market projected to reach $60 billion by 2030. (4) Megatrends include urbanization, smart infrastructure, health and wellness, future mobility, and the cognitive era. Spending on safe city solutions and surveillance is increasing globally to address security challenges from threats like cyber
Cyber security investments 2021

We found that while cyber security was named as the topmost future tech adoption for organizations in 2019, cyber security is now the second tech priority for 2021 but with a higher budget than previously allocated. We also discovered that cloud security currently holds more importance with CISOs, CTOs and CIOs than data security and privacy.
Volume2 chapter1 security

Preparing today for tomorrow’s threats.
When companies hear the word “security,” what concepts come to mind
— safety, protection or perhaps comfort? To the average IT administrator,
security conjures up images of locked-down networks and virus-free devices.
An attacker, state-sponsored agent or hactivist, meanwhile, may view security
as a way to demonstrate expertise by infiltrating and bringing down corporate
or government networks for profit, military goals, political gain — or even fun.
We live in a world in which cybercrime is on the rise. A quick scan of the
timeline of major incidents (See Figure 1, Page 9) shows the increasing
frequency and severity of security breaches — a pattern that is likely
to continue for years to come. Few if any organizations are safe from
cybercriminals, to say nothing of national security. In fact, experts even
exposed authentication and encryption vulnerabilities in the U.S. Federal
Aviation Administration’s new state-of-the-art multibillion-dollar air
traffic control system
What Are Cyber Attacks All About? | Cyberroot Risk Advisory

Cyber attacks involve compromising computer systems and networks to cause harm. The rise in cyber attacks has been driven by more people working remotely during the pandemic using unsecured networks, making systems easier to hack. Research shows that businesses are becoming more aware of cyber risks and are purchasing more cyber insurance as a result. Statistics show that cybercrime costs over $1 trillion globally each year and the average cost of a data breach for a business is over $3 million. Certain industries like healthcare, energy, and finance are particularly at risk of costly cyber attacks.
Cyber Security Threats 

Cyber Security threats will be the biggest challenges for chief information officers and chief technology officers. In this document, you'll see the cyber security threats.
Cyber Security small

RSA provides cybersecurity solutions such as threat detection, identity and access management, and fraud prevention to nearly half of global Fortune 500 companies. The document discusses the growing need for cybersecurity and skills in the UK, highlighting challenges like phishing attacks, ransomware, and the importance of continuous training and updated systems. It provides tips from security experts on how companies can better protect themselves and tackle the shortage of cybersecurity skills.
As telcos go digital, cybersecurity risks intensify by pwc

globalaviationairospace.com
Cyber security for telecommunications companies
The rewards and risks of the cloud, devices, and data
The fastest growing sources of security incidents, increase over 2013
Security strategies for evolving technologies
Strategic initiatives to improve cybersecurity
Coronavirus Impact Assessment And Mitigation Strategies In ICT Industry Compl...

Risk Mitigation Strategy ICT Industry The PowerPoint template is useful tool in presenting coronavirus impact assessment and mitigation strategies associated to ICT industry. It covers details regarding the ICT sector overview with market drivers and major areas of sector and how ICT sector has been affected during COVID 19 pandemic, how ICT sector is performing during COVID 19 impact of coronavirus outbreak on Global and Chinas ICT market growth, impact on telecom sector. It provides details about how COVID 19 has modified forecasted assumption associated to ICT sector. Various enterprise risks are identified such as disruption due to social distancing, plummeting employee productivity, stressed supply chain, recession in ICT sector, unemployment and investment pullback risk, and economic instability and civil unrest due to pandemic. It also covers details about how these risks can be mitigated through business impact analysis, risk readiness assessment, risk management plan, business continuity plan and how risk of fake news spreading can be controlled, policy management, incident management in terms how technology plays vital role in avoiding various incidents during pandemic, risk response plan for firms associated to ICT sector during COVID 19 outbreak. It contains information regarding the role of government assistance in reviving ICT sector. It also covers risk maturity survey questionnaire to ensure the maturity level of enterprises in handling risks. https://bit.ly/3v37vtj
Ninth Annual Cost of Cybercrime Study in Financial Services – 2019 Report

This new Accenture Security document reports on how the cost of cybercrime continues to increase for financial services companies and explores how enhanced cybersecurity can unlock substantial new financial value for their organizations
Future Watch: Cybersecurity market in South Africa 

The document discusses cybersecurity trends in South Africa. Some key points:
1. South Africa has a growing cybersecurity market due to increasing digital transformation and cyber attacks targeting sectors like financial services and healthcare.
2. The cybersecurity market in South Africa is expected to grow from $667 million in 2017 to over $1 billion by 2022, as enterprises allocate more of their IT budgets to security.
3. Common causes of data breaches in South Africa include malicious attacks and human errors, with the financial cost estimated to be around $200 million per year.
Similar to Security Threats in IT Infographic (20)
Deception Technology Market – Overview of advancements in innovation 2025

Deception Technology Market – Overview of advancements in innovation 2025
The 10 Fastest Growing Cyber Security Companies of 2017

The 10 Fastest Growing Cyber Security Companies of 2017
Cost of Cybercrime Study in Financial Services: 2019 Report

Cost of Cybercrime Study in Financial Services: 2019 Report
Pat Pather- Cyber Security Unchartered: Vigilance, Innovation and Adaptability

Pat Pather- Cyber Security Unchartered: Vigilance, Innovation and Adaptability
Security transformation: Helping you manage digital risk

Security transformation: Helping you manage digital risk
Foro Empresarial Perú 2017 - Tendencias impactando Ciudades & Negocios

Foro Empresarial Perú 2017 - Tendencias impactando Ciudades & Negocios
What Are Cyber Attacks All About? | Cyberroot Risk Advisory

What Are Cyber Attacks All About? | Cyberroot Risk Advisory
As telcos go digital, cybersecurity risks intensify by pwc

As telcos go digital, cybersecurity risks intensify by pwc
Coronavirus Impact Assessment And Mitigation Strategies In ICT Industry Compl...

Coronavirus Impact Assessment And Mitigation Strategies In ICT Industry Compl...
Ninth Annual Cost of Cybercrime Study in Financial Services – 2019 Report

Ninth Annual Cost of Cybercrime Study in Financial Services – 2019 Report
Future Watch: Cybersecurity market in South Africa 

Future Watch: Cybersecurity market in South Africa
Recently uploaded
留学学历(UoA毕业证)奥克兰大学毕业证成绩单官方原版办理

制做办理奥克兰大学学历证书<176555708微信>【毕业证明信-推荐信做学费单>【微信176555708】【制作UoA毕业证文凭认证奥克兰大学毕业证成绩单购买】【UoA毕业证书】{奥克兰大学文凭购买}】成绩单,录取通知书,Offer,在读证明,雅思托福成绩单,真实大使馆教育部认证,回国人员证明,>【制作UoA毕业证文凭认证奥克兰大学毕业证成绩单购买】【UoA毕业证书】{奥克兰大学文凭购买}留信网认证。
奥克兰大学学历证书<微信176555708(一对一服务包括毕业院长签字,专业课程,学位类型,专业或教育领域,以及毕业日期.不要忽视这些细节.这两份文件同样重要!毕业证成绩单文凭留信网学历认证!)[留学文凭学历认证(留信认证使馆认证)奥克兰大学毕业证成绩单毕业证证书大学Offer请假条成绩单语言证书国际回国人员证明高仿教育部认证申请学校等一切高仿或者真实可查认证服务。
多年留学服务公司,拥有海外样板无数能完美1:1还原海外各国大学degreeDiplomaTranscripts等毕业材料。海外大学毕业材料都有哪些工艺呢?工艺难度主要由:烫金.钢印.底纹.水印.防伪光标.热敏防伪等等组成。而且我们每天都在更新海外文凭的样板以求所有同学都能享受到完美的品质服务。
国外毕业证学位证成绩单办理方法:
1客户提供办理奥克兰大学奥克兰大学硕士毕业证成绩单信息:姓名生日专业学位毕业时间等(如信息不确定可以咨询顾问:我们有专业老师帮你查询);
2开始安排制作毕业证成绩单电子图;
3毕业证成绩单电子版做好以后发送给您确认;
4毕业证成绩单电子版您确认信息无误之后安排制作成品;
5成品做好拍照或者视频给您确认;
6快递给客户(国内顺丰国外DHLUPS等快读邮寄)
— — — — 我们是挂科和未毕业同学们的福音我们是实体公司精益求精的工艺! — — — -
一真实留信认证的作用(私企外企荣誉的见证):
1:该专业认证可证明留学生真实留学身份同时对留学生所学专业等级给予评定。
2:国家专业人才认证中心颁发入库证书这个入网证书并且可以归档到地方。
3:凡是获得留信网入网的信息将会逐步更新到个人身份内将在公安部网内查询个人身份证信息后同步读取人才网入库信息。
4:个人职称评审加20分个人信誉贷款加10分。
5:在国家人才网主办的全国网络招聘大会中纳入资料供国家500强等高端企业选择人才。
Ready to Unlock the Power of Blockchain!

Imagine a world where data flows freely, yet remains secure. A world where trust is built into the fabric of every transaction. This is the promise of blockchain, a revolutionary technology poised to reshape our digital landscape.
Toptal Tech is at the forefront of this innovation, connecting you with the brightest minds in blockchain development. Together, we can unlock the potential of this transformative technology, building a future of transparency, security, and endless possibilities.
APNIC Foundation, presented by Ellisha Heppner at the PNG DNS Forum 2024

Ellisha Heppner, Grant Management Lead, presented an update on APNIC Foundation to the PNG DNS Forum held from 6 to 10 May, 2024 in Port Moresby, Papua New Guinea.
Should Repositories Participate in the Fediverse?

Presentation for OR2024 making the case that repositories could play a part in the "fediverse" of distributed social applications
Understanding User Behavior with Google Analytics.pdf

Unlocking the full potential of Google Analytics is crucial for understanding and optimizing your website’s performance. This guide dives deep into the essential aspects of Google Analytics, from analyzing traffic sources to understanding user demographics and tracking user engagement.
Traffic Sources Analysis:
Discover where your website traffic originates. By examining the Acquisition section, you can identify whether visitors come from organic search, paid campaigns, direct visits, social media, or referral links. This knowledge helps in refining marketing strategies and optimizing resource allocation.
User Demographics Insights:
Gain a comprehensive view of your audience by exploring demographic data in the Audience section. Understand age, gender, and interests to tailor your marketing strategies effectively. Leverage this information to create personalized content and improve user engagement and conversion rates.
Tracking User Engagement:
Learn how to measure user interaction with your site through key metrics like bounce rate, average session duration, and pages per session. Enhance user experience by analyzing engagement metrics and implementing strategies to keep visitors engaged.
Conversion Rate Optimization:
Understand the importance of conversion rates and how to track them using Google Analytics. Set up Goals, analyze conversion funnels, segment your audience, and employ A/B testing to optimize your website for higher conversions. Utilize ecommerce tracking and multi-channel funnels for a detailed view of your sales performance and marketing channel contributions.
Custom Reports and Dashboards:
Create custom reports and dashboards to visualize and interpret data relevant to your business goals. Use advanced filters, segments, and visualization options to gain deeper insights. Incorporate custom dimensions and metrics for tailored data analysis. Integrate external data sources to enrich your analytics and make well-informed decisions.
This guide is designed to help you harness the power of Google Analytics for making data-driven decisions that enhance website performance and achieve your digital marketing objectives. Whether you are looking to improve SEO, refine your social media strategy, or boost conversion rates, understanding and utilizing Google Analytics is essential for your success.
Search Result Showing My Post is Now Buried

Search results burying my post that used to rank before Google's March 2024 algorithm update.
Gen Z and the marketplaces - let's translate their needs

The product workshop focused on exploring the requirements of Generation Z in relation to marketplace dynamics. We delved into their specific needs, examined the specifics in their shopping preferences, and analyzed their preferred methods for accessing information and making purchases within a marketplace. Through the study of real-life cases , we tried to gain valuable insights into enhancing the marketplace experience for Generation Z.
The workshop was held on the DMA Conference in Vienna June 2024.
留学挂科(UofM毕业证)明尼苏达大学毕业证成绩单复刻办理

精仿办理明尼苏达大学学历证书<176555708微信>【毕业证明信-推荐信做学费单>【微信176555708】【制作UofM毕业证文凭认证明尼苏达大学毕业证成绩单购买】【UofM毕业证书】{明尼苏达大学文凭购买}】成绩单,录取通知书,Offer,在读证明,雅思托福成绩单,真实大使馆教育部认证,回国人员证明,>【制作UofM毕业证文凭认证明尼苏达大学毕业证成绩单购买】【UofM毕业证书】{明尼苏达大学文凭购买}留信网认证。
明尼苏达大学学历证书<微信176555708(一对一服务包括毕业院长签字,专业课程,学位类型,专业或教育领域,以及毕业日期.不要忽视这些细节.这两份文件同样重要!毕业证成绩单文凭留信网学历认证!)(留信学历认证永久存档查询)采用学校原版纸张、特殊工艺完全按照原版一比一制作(包括:隐形水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠,文字图案浮雕,激光镭射,紫外荧光,温感,复印防伪)行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备,十五年致力于帮助留学生解决难题,业务范围有加拿大、英国、澳洲、韩国、美国、新加坡,新西兰等学历材料,包您满意。
◆◆◆◆◆ — — — — — — — — 【留学教育】留学归国服务中心 — — — — — -◆◆◆◆◆
【主营项目】
一.毕业证【微信:176555708】成绩单、使馆认证、教育部认证、雅思托福成绩单、学生卡等!
二.真实使馆公证(即留学回国人员证明,不成功不收费)
三.真实教育部学历学位认证(教育部存档!教育部留服网站永久可查)
四.办理各国各大学文凭(一对一专业服务,可全程监控跟踪进度)
如果您处于以下几种情况:
◇在校期间,因各种原因未能顺利毕业……拿不到官方毕业证【微信:176555708】
◇面对父母的压力,希望尽快拿到;
◇不清楚认证流程以及材料该如何准备;
◇回国时间很长,忘记办理;
◇回国马上就要找工作,办给用人单位看;
◇企事业单位必须要求办理的
◇需要报考公务员、购买免税车、落转户口
◇申请留学生创业基金
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分→ 【关于价格问题(保证一手价格)
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
选择实体注册公司办理,更放心,更安全!我们的承诺:可来公司面谈,可签订合同,会陪同客户一起到教育部认证窗口递交认证材料,客户在教育部官方认证查询网站查询到认证通过结果后付款,不成功不收费!
我们所定的价格是非常合理的,而且我们现在做得单子大多数都是代理和回头客户介绍的所以一般现在有新的单子 我给客户的都是第一手的代理价格,因为我想坦诚对待大家 不想跟大家在价格方面浪费时间
对于老客户或者被老客户介绍过来的朋友,我们都会适当给一些优惠。
学历顾问:微信:176555708
制作原版1:1(Monash毕业证)莫纳什大学毕业证成绩单办理假

退学买莫纳什大学毕业证>【微信176555708】办理莫纳什大学毕业证成绩单【微信176555708】Monash毕业证成绩单Monash学历证书Monash文凭【Monash毕业套号文凭网认证莫纳什大学毕业证成绩单】【哪里买莫纳什大学毕业证文凭Monash成绩学校快递邮寄信封】【开版莫纳什大学文凭】Monash留信认证本科硕士学历认证1:1完美还原海外各大学毕业材料上的工艺:水印阴影底纹钢印LOGO烫金烫银LOGO烫金烫银复合重叠。文字图案浮雕激光镭射紫外荧光温感复印防伪。
可办理以下真实莫纳什大学存档留学生信息存档认证:
1莫纳什大学真实留信网认证(网上可查永久存档无风险百分百成功入库);
2真实教育部认证(留服)等一切高仿或者真实可查认证服务(暂时不可办理);
3购买英美真实学籍(不用正常就读直接出学历);
4英美一年硕士保毕业证项目(保录取学校挂名不用正常就读保毕业)
留学本科/硕士毕业证书成绩单制作流程:
1客户提供办理信息:姓名生日专业学位毕业时间等(如信息不确定可以咨询顾问:我们有专业老师帮你查询莫纳什大学莫纳什大学毕业证offer);
2开始安排制作莫纳什大学毕业证成绩单电子图;
3莫纳什大学毕业证成绩单电子版做好以后发送给您确认;
4莫纳什大学毕业证成绩单电子版您确认信息无误之后安排制作成品;
5莫纳什大学成品做好拍照或者视频给您确认;
6快递给客户(国内顺丰国外DHLUPS等快读邮寄)
— — — — — — — — — — — 《文凭顾问微信:176555708》
办理新西兰奥克兰大学毕业证学位证书范本原版一模一样

原版一模一样【微信:741003700 】【新西兰奥克兰大学毕业证学位证书】【微信:741003700 】学位证,留信认证(真实可查,永久存档)offer、雅思、外壳等材料/诚信可靠,可直接看成品样本,帮您解决无法毕业带来的各种难题!外壳,原版制作,诚信可靠,可直接看成品样本。行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备。十五年致力于帮助留学生解决难题,包您满意。
本公司拥有海外各大学样板无数,能完美还原海外各大学 Bachelor Diploma degree, Master Degree Diploma
1:1完美还原海外各大学毕业材料上的工艺:水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠。文字图案浮雕、激光镭射、紫外荧光、温感、复印防伪等防伪工艺。材料咨询办理、认证咨询办理请加学历顾问Q/微741003700
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
一比一原版(LBS毕业证)伦敦商学院毕业证成绩单专业办理

LBS毕业证原版定制【微信:176555708】【伦敦商学院毕业证成绩单-学位证】【微信:176555708】(留信学历认证永久存档查询)采用学校原版纸张、特殊工艺完全按照原版一比一制作(包括:隐形水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠,文字图案浮雕,激光镭射,紫外荧光,温感,复印防伪)行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备,十五年致力于帮助留学生解决难题,业务范围有加拿大、英国、澳洲、韩国、美国、新加坡,新西兰等学历材料,包您满意。
◆◆◆◆◆ — — — — — — — — 【留学教育】留学归国服务中心 — — — — — -◆◆◆◆◆
【主营项目】
一.毕业证【微信:176555708】成绩单、使馆认证、教育部认证、雅思托福成绩单、学生卡等!
二.真实使馆公证(即留学回国人员证明,不成功不收费)
三.真实教育部学历学位认证(教育部存档!教育部留服网站永久可查)
四.办理各国各大学文凭(一对一专业服务,可全程监控跟踪进度)
如果您处于以下几种情况:
◇在校期间,因各种原因未能顺利毕业……拿不到官方毕业证【微信:176555708】
◇面对父母的压力,希望尽快拿到;
◇不清楚认证流程以及材料该如何准备;
◇回国时间很长,忘记办理;
◇回国马上就要找工作,办给用人单位看;
◇企事业单位必须要求办理的
◇需要报考公务员、购买免税车、落转户口
◇申请留学生创业基金
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分→ 【关于价格问题(保证一手价格)
我们所定的价格是非常合理的,而且我们现在做得单子大多数都是代理和回头客户介绍的所以一般现在有新的单子 我给客户的都是第一手的代理价格,因为我想坦诚对待大家 不想跟大家在价格方面浪费时间
对于老客户或者被老客户介绍过来的朋友,我们都会适当给一些优惠。
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
选择实体注册公司办理,更放心,更安全!我们的承诺:可来公司面谈,可签订合同,会陪同客户一起到教育部认证窗口递交认证材料,客户在教育部官方认证查询网站查询到认证通过结果后付款,不成功不收费!
学历顾问:微信:176555708
一比一原版(SLU毕业证)圣路易斯大学毕业证成绩单专业办理

SLU毕业证原版定制【微信:176555708】【圣路易斯大学毕业证成绩单-学位证】【微信:176555708】(留信学历认证永久存档查询)采用学校原版纸张、特殊工艺完全按照原版一比一制作(包括:隐形水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠,文字图案浮雕,激光镭射,紫外荧光,温感,复印防伪)行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备,十五年致力于帮助留学生解决难题,业务范围有加拿大、英国、澳洲、韩国、美国、新加坡,新西兰等学历材料,包您满意。
◆◆◆◆◆ — — — — — — — — 【留学教育】留学归国服务中心 — — — — — -◆◆◆◆◆
【主营项目】
一.毕业证【微信:176555708】成绩单、使馆认证、教育部认证、雅思托福成绩单、学生卡等!
二.真实使馆公证(即留学回国人员证明,不成功不收费)
三.真实教育部学历学位认证(教育部存档!教育部留服网站永久可查)
四.办理各国各大学文凭(一对一专业服务,可全程监控跟踪进度)
如果您处于以下几种情况:
◇在校期间,因各种原因未能顺利毕业……拿不到官方毕业证【微信:176555708】
◇面对父母的压力,希望尽快拿到;
◇不清楚认证流程以及材料该如何准备;
◇回国时间很长,忘记办理;
◇回国马上就要找工作,办给用人单位看;
◇企事业单位必须要求办理的
◇需要报考公务员、购买免税车、落转户口
◇申请留学生创业基金
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分→ 【关于价格问题(保证一手价格)
我们所定的价格是非常合理的,而且我们现在做得单子大多数都是代理和回头客户介绍的所以一般现在有新的单子 我给客户的都是第一手的代理价格,因为我想坦诚对待大家 不想跟大家在价格方面浪费时间
对于老客户或者被老客户介绍过来的朋友,我们都会适当给一些优惠。
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
选择实体注册公司办理,更放心,更安全!我们的承诺:可来公司面谈,可签订合同,会陪同客户一起到教育部认证窗口递交认证材料,客户在教育部官方认证查询网站查询到认证通过结果后付款,不成功不收费!
学历顾问:微信:176555708
可查真实(Monash毕业证)西澳大学毕业证成绩单退学买

办理假西澳大学毕业证【微信176555708】购买,办理Monash成绩单,Monash毕业证制作【微信176555708】【西澳大学毕业证】,Monash毕业证购买,Monash学位证,西澳大学学位证【Monash成绩单制作】【Monash毕业证文凭 Monash本科 澳洲学历认证原版制作【diploma certificate degree transcript 】【留信网认证,本科,硕士,海归,博士,排名,成绩单】代办国外(海外)澳洲、韩国、加拿大、新西兰等各大学毕业证。 ?我们对海外大学及学院的毕业证成绩单所使用的材料,尺寸大小,防伪结构(包括:水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠。 文字图案浮雕,激光镭射,紫外荧光,温感,复印防伪)都有原版本文凭对照。#一整套西澳大学文凭证件办理#—包含西澳大学西澳大学毕业证成绩单学历认证|使馆认证|归国人员证明|教育部认证|留信网认证永远存档教育部学历学位认证查询办理国外文凭国外学历学位认证#我们提供全套办理服务。
一整套留学文凭证件服务:
一:西澳大学西澳大学毕业证成绩单毕业证 #成绩单等全套材料从防伪到印刷水印底纹到钢印烫金
二:真实使馆认证(留学人员回国证明)使馆存档
三:真实教育部认证教育部存档教育部留服网站永久可查
四:留信认证留学生信息网站永久可查
国外毕业证学位证成绩单办理方法:
1客户提供办理西澳大学西澳大学毕业证成绩单信息:姓名生日专业学位毕业时间等(如信息不确定可以咨询顾问:我们有专业老师帮你查询);
2开始安排制作毕业证成绩单电子图;
3毕业证成绩单电子版做好以后发送给您确认;
4毕业证成绩单电子版您确认信息无误之后安排制作成品;
5成品做好拍照或者视频给您确认;
6快递给客户(国内顺丰国外DHLUPS等快读邮寄)。
教育部文凭学历认证认证的用途:
如果您计划在国内发展那么办理国内教育部认证是必不可少的。事业性用人单位如银行国企公务员在您应聘时都会需要您提供这个认证。其他私营 #外企企业无需提供!办理教育部认证所需资料众多且烦琐所有材料您都必须提供原件我们凭借丰富的经验帮您快速整合材料让您少走弯路。
实体公司专业为您服务如有需要请联系我: 微信176555708
Meet up Milano 14 _ Axpo Italia_ Migration from Mule3 (On-prem) to.pdf

Quattordicesimo Meetup di Milano, tenutosi a Milano il 23 Maggio 2024 dalle ore 17:00 alle ore 18:30 in presenza e da remoto.
Abbiamo parlato di come Axpo Italia S.p.A. ha ridotto il technical debt migrando le proprie APIs da Mule 3.9 a Mule 4.4 passando anche da on-premises a CloudHub 1.0.
Internet of Things in Manufacturing: Revolutionizing Efficiency & Quality | C...

This article delves into how the Internet of Things in manufacturing is reshaping the industry, its benefits, challenges, and future prospects.
国外证书(Lincoln毕业证)新西兰林肯大学毕业证成绩单不能毕业办理

退学办理新西兰林肯大学毕业证【微信176555708】学历认证怎么做:原版仿制新西兰林肯大学电子版成绩单毕业证认证【新西兰林肯大学毕业证成绩单】、新西兰林肯大学文凭证书成绩单复刻offer录取通知书、购买Lincoln圣力嘉学院本科毕业证、【新西兰林肯大学毕业证办理Lincoln毕业证书哪里买】、新西兰林肯大学 Offer在线办理Lincoln Offer新西兰林肯大学Bachloer Degree。1客户提供办理信息:姓名生日专业学位毕业时间等(如信息不确定可以咨询顾问:微信176555708我们有专业老师帮你查询);
2开始安排制作毕业证成绩单电子图;
3毕业证成绩单电子版做好以后发送给您确认;
4毕业证成绩单电子版您确认信息无误之后安排制作成品;
5成品做好拍照或者视频给您确认;
6快递给客户(国内顺丰国外DHLUPS等快读邮寄)。
7完成交易删除客户资料
高精端提供以下服务:
一:新西兰林肯大学新西兰林肯大学毕业证文凭证书全套材料从防伪到印刷水印底纹到钢印烫金
二:真实使馆认证(留学人员回国证明)使馆存档
三:真实教育部认证教育部存档教育部留服网站可查
四:留信认证留学生信息网站可查
五:与学校颁发的相关证件1:1纸质尺寸制定(定期向各大院校毕业生购买最新版本毕,业证成绩单保证您拿到的是鲁昂大学内部最新版本毕业证成绩单微信176555708)
A.为什么留学生需要操作留信认证?
留信认证全称全国留学生信息服务网认证,隶属于北京中科院。①留信认证门槛条件更低,费用更美丽,并且包过,完单周期短,效率高②留信认证虽然不能去国企,但是一般的公司都没有问题,因为国内很多公司连基本的留学生学历认证都不了解。这对于留学生来说,这就比自己光拿一个证书更有说服力,因为留学学历可以在留信网站上进行查询!
B.为什么我们提供的毕业证成绩单具有使用价值?
查询留服认证是国内鉴别留学生海外学历的唯一途径但认证只是个体行为不是所有留学生都操作所以没有办理认证的留学生的学历在国内也是查询不到的他们也仅仅只有一张文凭。所以这时候我们提供的和学校颁发的一模一样的毕业证成绩单就有了使用价值。
Bridging the Digital Gap Brad Spiegel Macon, GA Initiative.pptx

Brad Spiegel Macon GA’s journey exemplifies the profound impact that one individual can have on their community. Through his unwavering dedication to digital inclusion, he’s not only bridging the gap in Macon but also setting an example for others to follow.
重新申请毕业证书(RMIT毕业证)皇家墨尔本理工大学毕业证成绩单精仿办理

不能毕业办理【RMIT毕业证【微信176555708】皇家墨尔本理工大学文凭学历】【微信176555708】【皇家墨尔本理工大学文凭学历证书】【皇家墨尔本理工大学毕业证书与成绩单样本图片】毕业证书补办 Fake Degree做学费单【毕业证明信-推荐信】成绩单,录取通知书,Offer,在读证明,雅思托福成绩单,真实大使馆教育部认证,回国人员证明,留信网认证。网上存档永久可查!全套服务:皇家墨尔本理工大学皇家墨尔本理工大学本科学位证成绩单真实回国人员证明 #真实教育部认证。让您回国发展信心十足#铸就十年品质!信誉!实体公司!可以视频看办公环境样板如需办理真实可查可以先到公司面谈勿轻信小中介黑作坊!
可以提供皇家墨尔本理工大学钢印 #水印 #烫金 #激光防伪 #凹凸版 #最新版的毕业证 #百分之百让您绝对满意
印刷DHL快递毕业证 #成绩单7个工作日真实大使馆教育部认证1个月。为了达到高水准高效率
请您先以qq或微信的方式对我们的服务进行了解后如果有皇家墨尔本理工大学皇家墨尔本理工大学本科学位证成绩单帮助再进行电话咨询。
国外毕业证学位证成绩单如何办理:
1客户提供办理信息:姓名生日专业学位毕业时间等(如信息不确定可以咨询顾问:我们有专业老师帮你查询);
2开始安排制作皇家墨尔本理工大学毕业证成绩单电子图;
3毕业证成绩单电子版做好以后发送给您确认;
4毕业证成绩单电子版您确认信息无误之后安排制作成品;
5成品做好拍照或者视频给您确认;
6快递给客户(国内顺丰国外DHLUPS等快读邮寄)。
不能毕业如何获得(USYD毕业证)悉尼大学毕业证成绩单一比一原版制作

挂科购买☀【悉尼大学毕业证购买】【微信176555708】【USYD毕业证模板办理】加拿大文凭、本科、硕士、研究生学历都可以做,二、业务范围:
★、全套服务:毕业证、成绩单、化学专业毕业证书伪造【悉尼大学大学毕业证】微信176555708【USYD学位证书购买】◆◆◆◆◆ — — — 归国服务中心 — — -◆◆◆◆◆
【主营项目】
一.毕业证、成绩单、使馆认证、教育部认证、雅思托福成绩单、学生卡等!
二.真实使馆公证(即留学回国人员证明,不成功不收费)
三.真实教育部学历学位认证(教育部存档!教育部留服网站永久可查)
四.办理各国各大学文凭(一对一专业服务,可全程监控跟踪进度)
国外毕业证、学位证、成绩单办理流程:
1、客户提供办理信息:姓名、生日、专业、学位、毕业时间等(如信息不确定可以咨询顾问:【微信176555708】我们有专业老师帮你查询);
2、开始安排制作毕业证、成绩单电子图;
3、毕业证、成绩单电子版做好以后发送给您确认;
4、毕业证、成绩单电子版您确认信息无误之后安排制作成品;
5、成品做好拍照或者视频给您确认;
6、快递给客户(国内顺丰,国外DHL、UPS等快读邮寄)。
专业服务,请勿犹豫联系我!本公司是留学创业和海归创业者们的桥梁。一次办理,终生受用,一步到位,高效服务。详情请在线咨询办理,欢迎有诚意办理的客户咨询!洽谈。
◆招聘代理:本公司诚聘英国、加拿大、澳洲、新西兰、加拿大、法国、德国、新加坡各地代理人员,如果你有业余时间,有兴趣就请联系我们咨询【微信176555708】
没文凭怎么找工作。让您回国发展信心十足!
★、真实教育部学历学位认证;(一对一专业服务,可全程监控跟踪进度)
★、真实使馆认证,可以通过大使馆查询确认;(即教育部留服认证,不成功不收费)
★、毕业证、成绩单等材料,从防伪到印刷、水印到钢印烫金,高精仿度都是跟学校原版100%相同的;(敬请放心使用)
★、可以提供钢印、水印、烫金、激光防伪、凹凸版、最新版的毕业证、百分之百让您绝对满意、
★、印刷,DHL快递毕业证、成绩单7个工作日,真实大使馆教育部认证1个月。为了达到高水准高效率。
Recently uploaded (20)
APNIC Foundation, presented by Ellisha Heppner at the PNG DNS Forum 2024

APNIC Foundation, presented by Ellisha Heppner at the PNG DNS Forum 2024
Understanding User Behavior with Google Analytics.pdf

Understanding User Behavior with Google Analytics.pdf
Gen Z and the marketplaces - let's translate their needs

Gen Z and the marketplaces - let's translate their needs
Meet up Milano 14 _ Axpo Italia_ Migration from Mule3 (On-prem) to.pdf

Meet up Milano 14 _ Axpo Italia_ Migration from Mule3 (On-prem) to.pdf
Internet of Things in Manufacturing: Revolutionizing Efficiency & Quality | C...

Internet of Things in Manufacturing: Revolutionizing Efficiency & Quality | C...
Bridging the Digital Gap Brad Spiegel Macon, GA Initiative.pptx

Bridging the Digital Gap Brad Spiegel Macon, GA Initiative.pptx
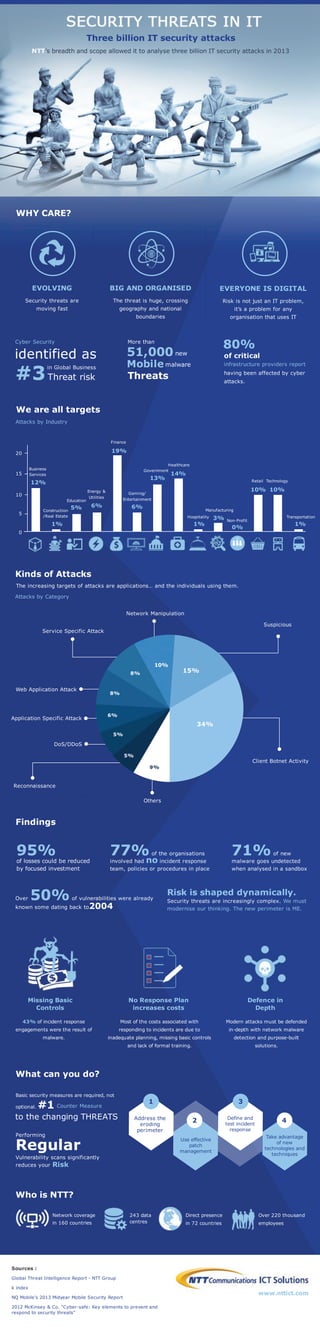
Security Threats in IT Infographic
- 1. ThreebillionITsecurityattacks WHYCARE? EVOLVING Securitythreatsare movingfast BIG AND ORGANISED Thethreatishuge,crossing geographyandnational boundaries EVERYONEISDIGITAL RiskisnotjustanITproblem, it’saproblem forany organisationthatusesIT NTT’sbreadthandscopeallowedittoanalysethreebillionITsecurityattacksin2013 CyberSecurity inGlobalBusiness Threatrisk identifiedas #3 Morethan Threats new malware 51,000 Mobile ofcritical havingbeenaffectedbycyber attacks. infrastructureprovidersreport 80% 95% oflossescouldbereduced byfocusedinvestment Wearealltargets AttacksbyIndustry 20 15 10 5 0 Education Energy& Utilities Finance Gaming/ Entertainment Government Healthcare Hospitality Manufacturing Non-Profit RetailTechnology Transportation Business Services Construction /RealEstate 12% 1% 1% 1% 0% 5% 6% 19% 6% 13% 14% 3% 10% 10% KindsofAttacks Theincreasingtargetsofattacksareapplications… andtheindividualsusingthem. AttacksbyCategory 34% 15% 10% 8% 8% 6% 5% 5% 9% ClientBotnetActivity Suspicious NetworkManipulation ServiceSpecificAttack WebApplicationAttack ApplicationSpecificAttack DoS/DDoS Reconnaissance Others Findings Basicsecuritymeasuresarerequired,not optional.#1CounterMeasure tothechangingTHREATS 77% oftheorganisations involvedhadnoincidentresponse team,policiesorproceduresinplace 71% ofnew malwaregoesundetected whenanalysedinasandbox Performing Regular Vulnerabilityscanssignificantly reducesyourRisk Over50% ofvulnerabilitieswerealready knownsomedatingbackto2004 Riskisshapeddynamically. Securitythreatsareincreasinglycomplex.Wemust moderniseourthinking.Thenew perimeterisME. MissingBasic Controls 43% ofincidentresponse engagementsweretheresultof malware. NoResponsePlan increasescosts Mostofthecostsassociatedwith respondingtoincidentsaredueto inadequateplanning,missingbasiccontrols andlackofformaltraining. x x x x x x x x Modernattacksmustbedefended in-depthwithnetworkmalware detectionandpurpose-built solutions. Defencein Depth Whatcanyoudo? Addressthe eroding perimeter Useeffective patch management 1 3 2 4Defineand testincident response Takeadvantage ofnew technologiesand techniques WhoisNTT? Networkcoverage in160countries Directpresence in72countries 243data centres Over220thousand employees Sources: GlobalThreatIntelligenceReport-NTTGroup kindex NQ Mobile’s2013MidyearMobileSecurityReport 2012McKinsey&Co.“Cyber-safe:Keyelementstopreventand respondtosecuritythreats” www.nttict.com
