Embed presentation
Download to read offline
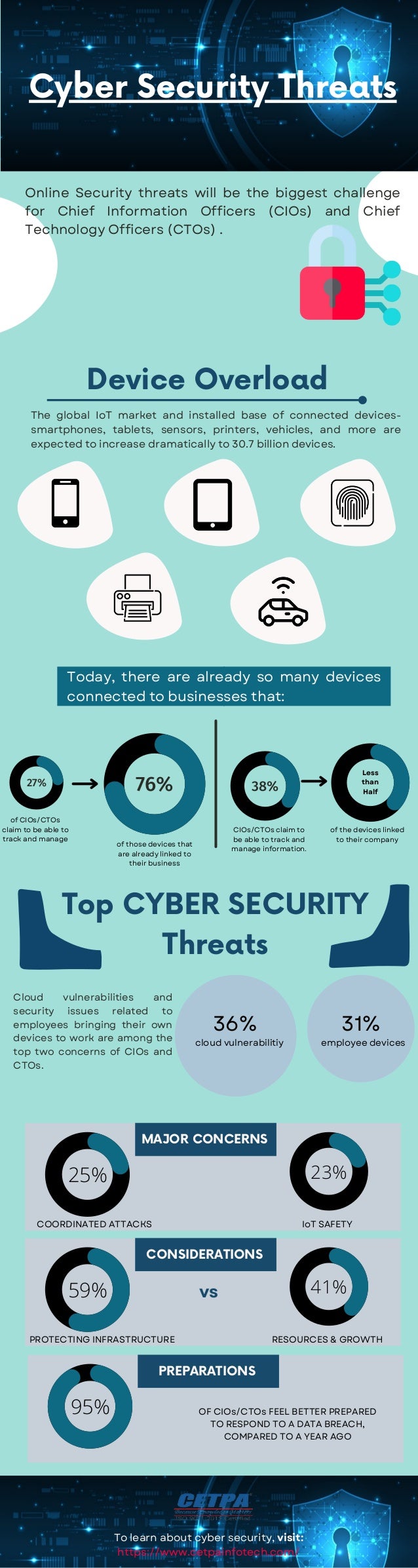
The global IoT market is projected to grow, reaching 30.7 billion connected devices, raising concerns about device overload and cyber security threats. Chief Information Officers (CIOs) and Chief Technology Officers (CTOs) identify online security threats as their greatest challenge, with specific concern over cloud vulnerabilities and employee devices. Many CIOs/CTOs feel better prepared to respond to data breaches compared to the previous year, although managing the proliferation of connected devices remains a significant challenge.
