The document discusses several aspects of cyber security and cyber warfare:
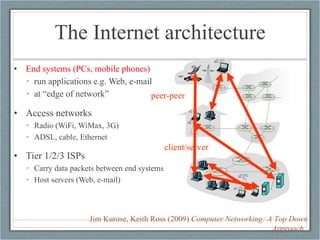
1) It describes the basic architecture of the internet and how data is transmitted between end systems and servers.
2) It discusses different types of cyber attacks like denial of service attacks and botnets, and whether these rise to the level of acts of war.
3) Experts argue that cyber operations can only temporarily confuse military systems and are best used as a support function for other types of warfare.
4) The challenges of attribution, response, and deterrence in cyber space are discussed, as is the importance of cyber defense over cyber offense.


![What is “cyberwar”? “ The ‘Korean’ cyber incidents of early July did not rise to the level of an act of war. They were annoying and for some agencies, embarrassing, but there was no violence or destruction... Cybercrime does not rise to the level of an act of war, even when there is state complicity, nor does espionage – [which] are the activities that currently dominate cyber conflict... Estonia and Georgia … came under limited cyber attack as part of larger conflicts with Russia, but in neither case were there casualties, loss of territory, destruction, or serious disruption of critical services. The ‘denial of service’ attacks used against these countries sought to create political pressure and coerce the target governments, but how to respond to such coercion remains an open question, particularly in light of the uncertain attribution and deniability” (Lewis, 2009: 2—3). “ At best, these operations can confuse and frustrate operators of military systems, and then only temporarily. Thus, cyberwar can only be a support function for other elements of warfare” (Libicki, 2009: xiv—xv)](https://image.slidesharecdn.com/cyber-terrain-100420111059-phpapp01/85/The-cyber-terrain-4-320.jpg)
![Deterrence and preemption “ [W]e need to reengineer the Internet [for] attribution, geolocation, intelligence analysis and impact assessment” –Mike McConnell, 28/2/10 “ [C]aution is necessary when contemplating cyberdeterrence. Attribution, predictable response, the ability to continue attack, and the lack of a counterforce option are all significant barriers… cyberdefense remains the Air Force’s most important activity within cyberspace.” (Libicki, 2009: xix-xx)](https://image.slidesharecdn.com/cyber-terrain-100420111059-phpapp01/85/The-cyber-terrain-5-320.jpg)

