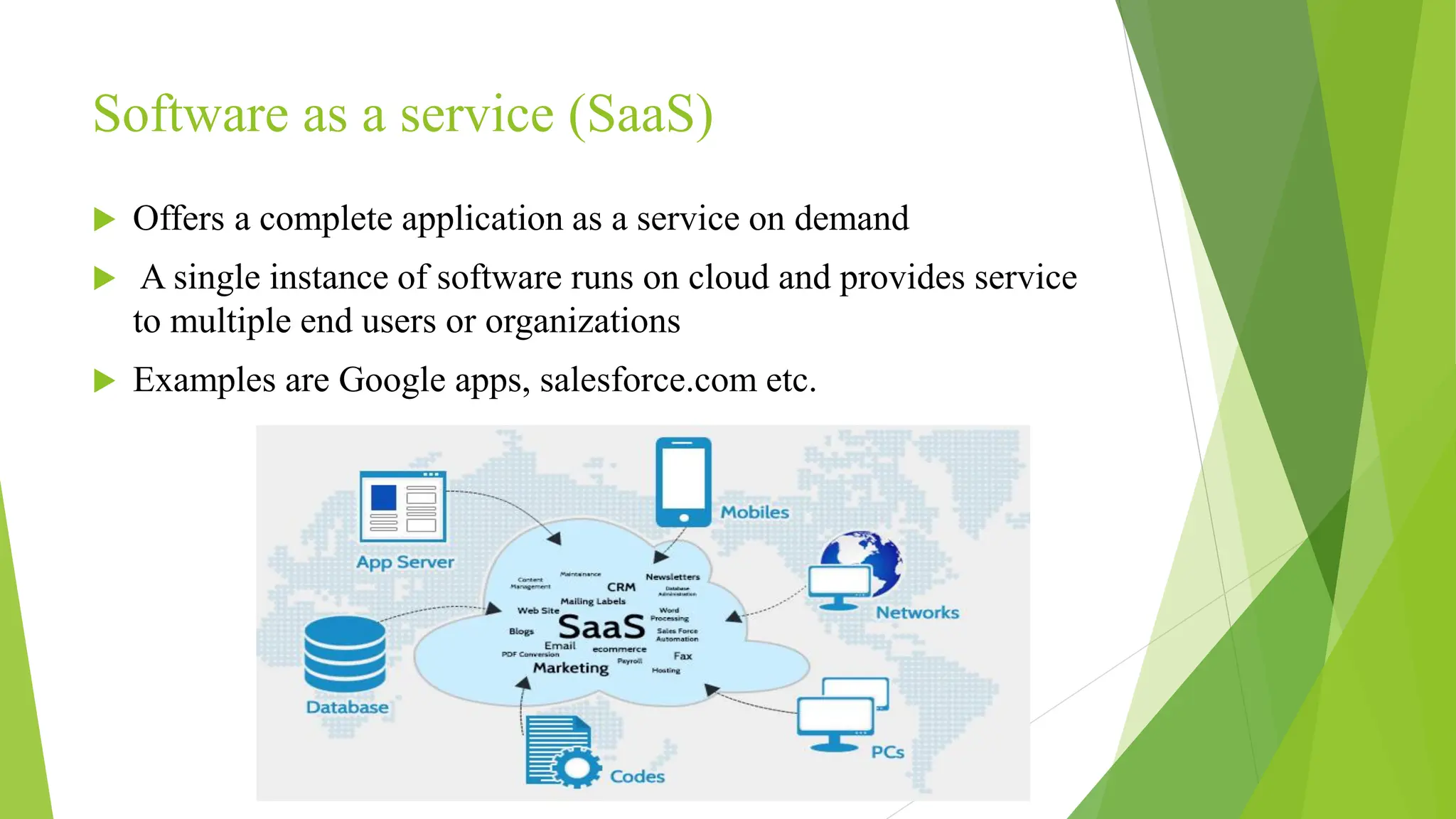
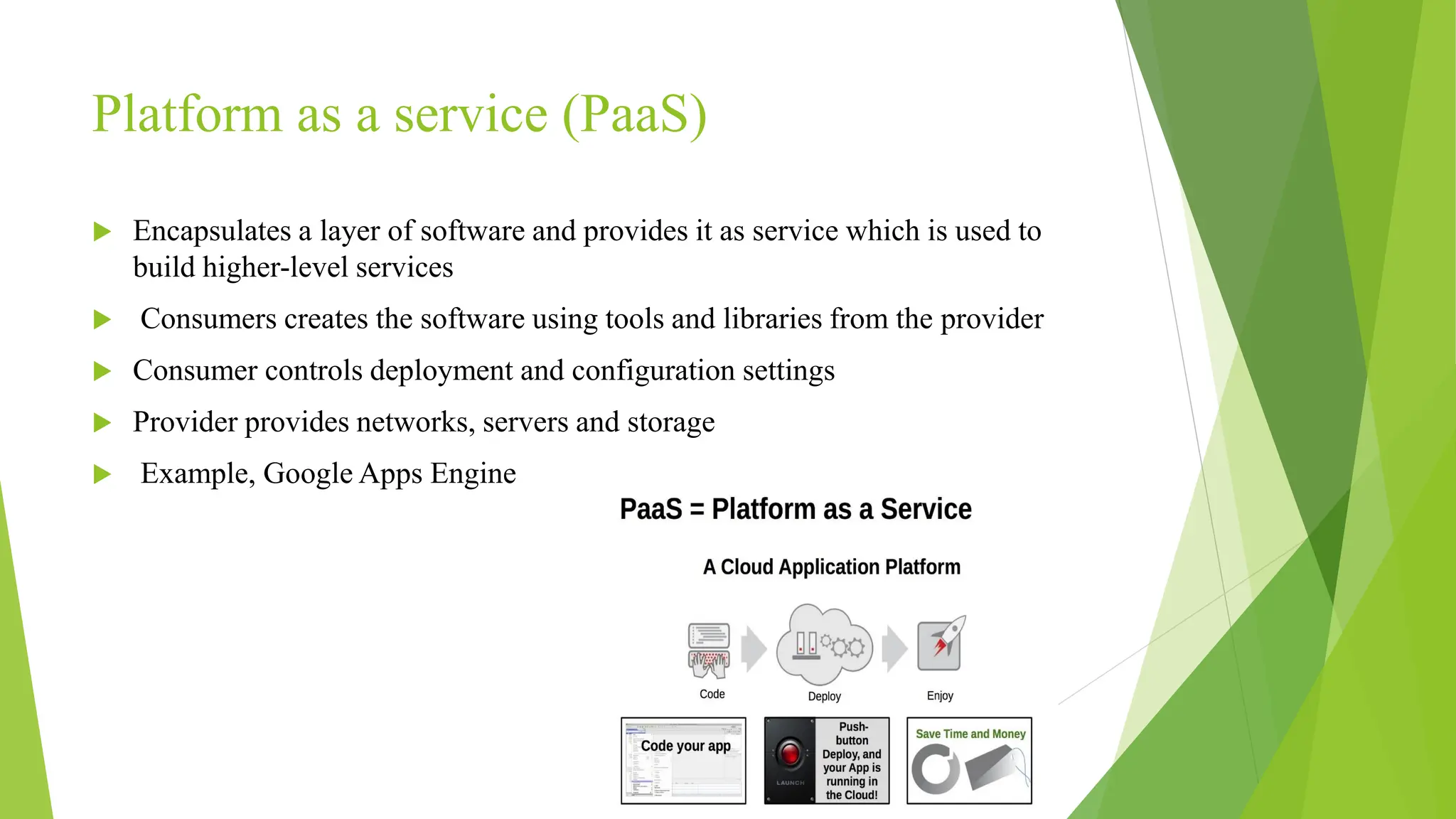
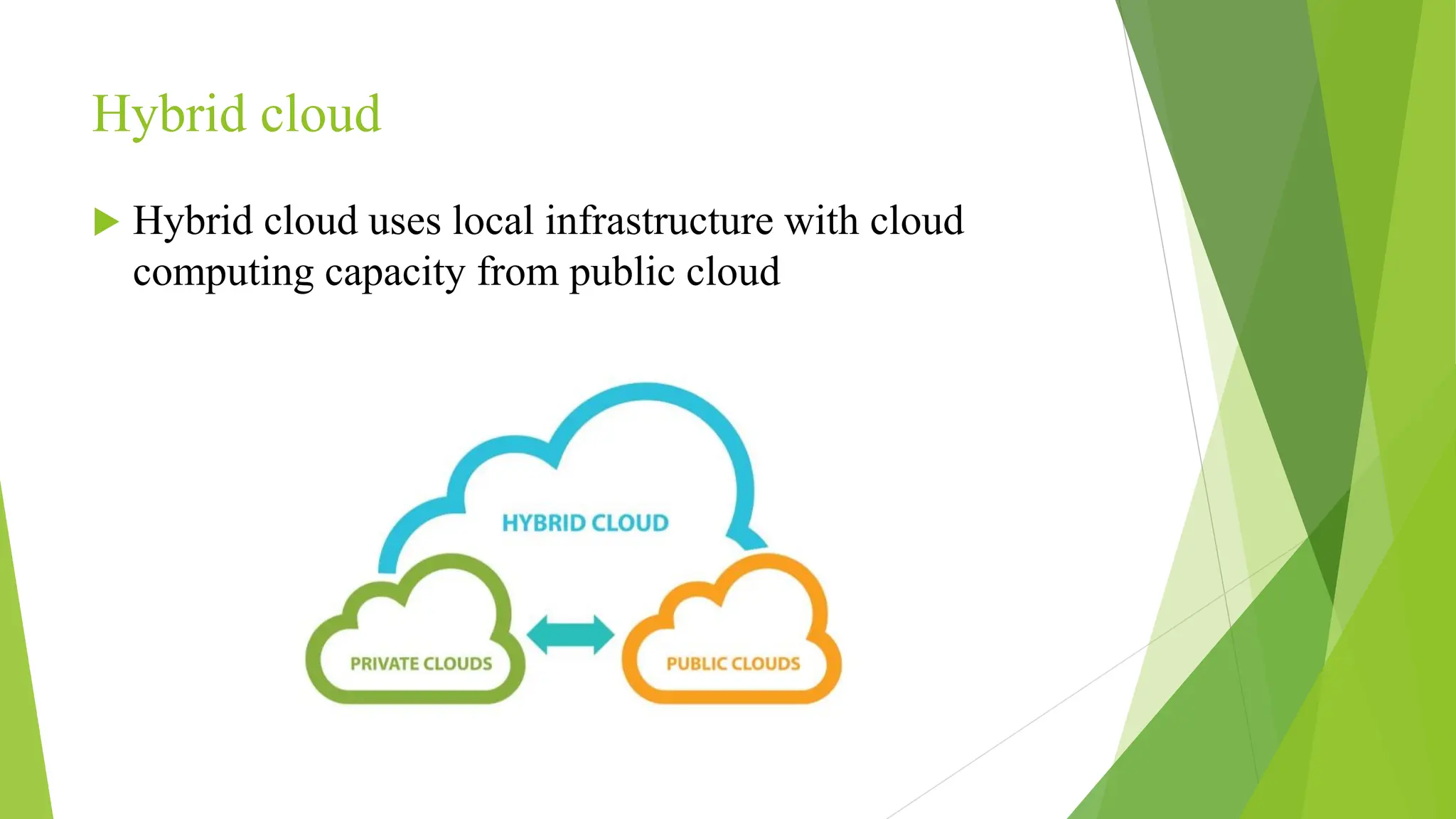
The document provides an overview of cloud computing, including its definition, history, architectural layers (IaaS, PaaS, SaaS), and infrastructure models (public, private, hybrid). It also discusses the Certified Ethical Hacker (CEH) certification and various types of security vulnerabilities and hackers. Key advantages of cloud computing include cost savings, speed, reliability, and enhanced collaboration.