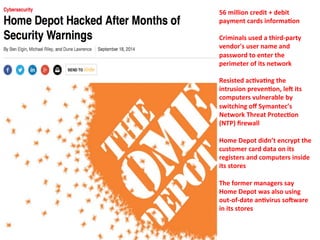
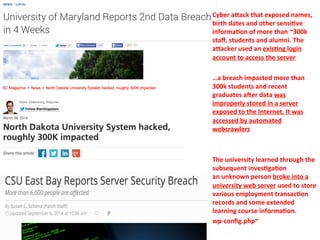
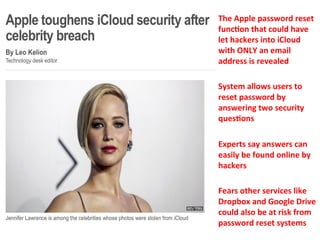
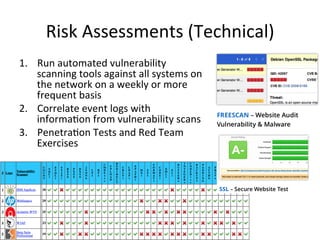
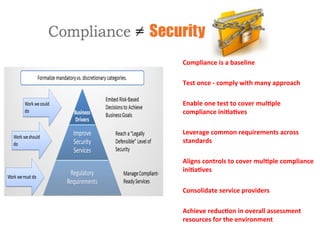
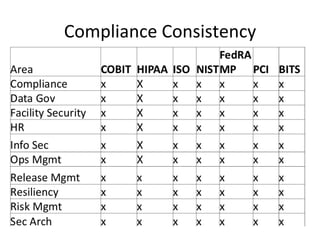
The document discusses security and compliance considerations for startups based on lessons from recent data breaches. It covers common threat vectors in past breaches like failing to activate intrusion prevention systems, storing credit card data without encryption, and insecure password management. It then provides recommendations in areas like data protection, firewalls, encryption, secure configurations, application security, risk assessments, backups, employee training, and vendor security. The presentation aims to help startups protect themselves against threats while meeting compliance needs.