Embed presentation
Downloaded 13 times







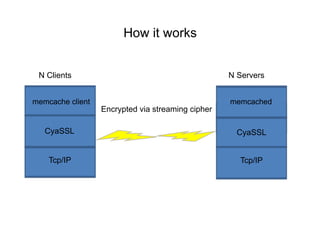

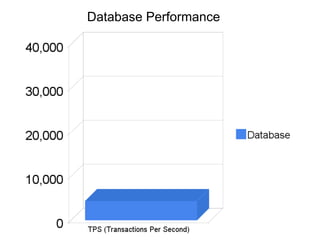
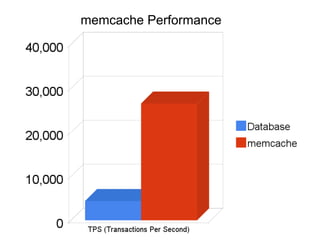
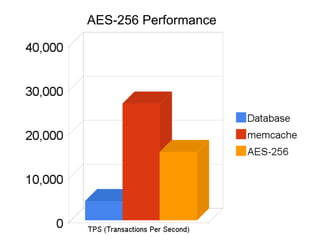
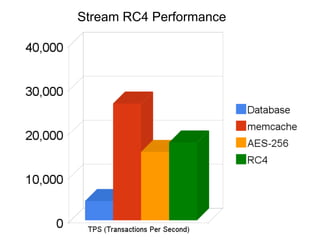
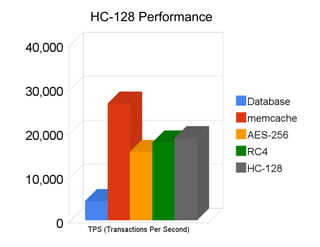
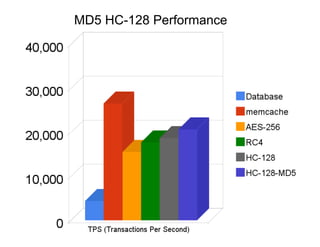





The document discusses securing Memcache through encryption and authentication methods like SASL and YaSSL. It highlights the importance of protecting sensitive data and outlines practical usage, availability, and performance considerations. The content also touches on future performance directions and includes contact information for the author.



















