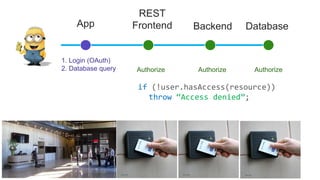
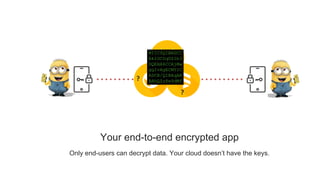
The document discusses end-to-end encryption for apps and databases. It describes generating encryption keys for users, encrypting data in the app using those keys so that only intended users can decrypt it, and storing the encrypted data in a database. The document also mentions generating backup keys from a username and password to prevent key loss.






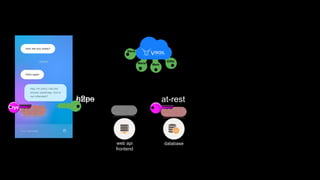




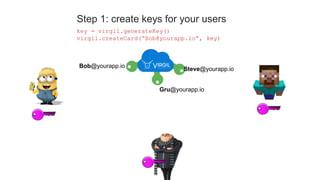
![Step 2: encrypt stuff in the app. Store encrypted data in your db.
encrSelfie = virgil.encrypt(selfie, [“Bob@yourapp.io”, me])
db.collection(“photos”).doc(“Selfie17”).set({encrSelfie})
Bob@yourapp.io
Gru@yourapp.io
Steve@yourapp.io](https://image.slidesharecdn.com/mobilemondayslides-181011042528/85/Secure-your-app-user-data-with-end-to-end-encryption-17-320.jpg)

