Secure wireless modem
•Download as PPT, PDF•
0 likes•179 views
Report
Share
Report
Share
Recommended
More Related Content
What's hot
What's hot (7)
How to upgrade tp link adsl modem router (trend chip solution)

How to upgrade tp link adsl modem router (trend chip solution)
Viewers also liked
Viewers also liked (8)
Similar to Secure wireless modem
Similar to Secure wireless modem (20)
write a Review about Wired Network Security -Network Security Hardware.docx

write a Review about Wired Network Security -Network Security Hardware.docx
Webinar NETGEAR - Nuovi AP Professionali Prosafe WAC720 e WAC730

Webinar NETGEAR - Nuovi AP Professionali Prosafe WAC720 e WAC730
Commissioning, Managing & Troubleshooting Industrial Networks

Commissioning, Managing & Troubleshooting Industrial Networks
More from creativelakshu
More from creativelakshu (6)
Recently uploaded
Recently uploaded (20)
Kotlin Multiplatform & Compose Multiplatform - Starter kit for pragmatics

Kotlin Multiplatform & Compose Multiplatform - Starter kit for pragmatics
Vulnerability_Management_GRC_by Sohang Sengupta.pptx

Vulnerability_Management_GRC_by Sohang Sengupta.pptx
Presentation on how to chat with PDF using ChatGPT code interpreter

Presentation on how to chat with PDF using ChatGPT code interpreter
"Federated learning: out of reach no matter how close",Oleksandr Lapshyn

"Federated learning: out of reach no matter how close",Oleksandr Lapshyn
The Codex of Business Writing Software for Real-World Solutions 2.pptx

The Codex of Business Writing Software for Real-World Solutions 2.pptx
Unblocking The Main Thread Solving ANRs and Frozen Frames

Unblocking The Main Thread Solving ANRs and Frozen Frames
Automating Business Process via MuleSoft Composer | Bangalore MuleSoft Meetup...

Automating Business Process via MuleSoft Composer | Bangalore MuleSoft Meetup...
Unleash Your Potential - Namagunga Girls Coding Club

Unleash Your Potential - Namagunga Girls Coding Club
Artificial intelligence in the post-deep learning era

Artificial intelligence in the post-deep learning era
08448380779 Call Girls In Diplomatic Enclave Women Seeking Men

08448380779 Call Girls In Diplomatic Enclave Women Seeking Men
#StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024

#StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024
Secure wireless modem
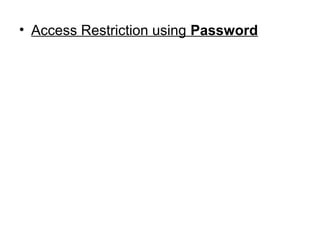
- 1. • Access Restriction using Password
- 2. Login to the ADSL Router on http://192.168.1.1 The username and password by default are ‘admin’ and ‘admin’. Click on ‘advanced’
- 3. Click on ‘wireless security’
- 4. Select the WEP security. Enable WEP security. Key in the desired security password. Click on Apply.
- 5. • Access List (MAC based)
- 6. • To add the clients to the access list, find out the MAC id of the clients (wireless interface card) where the connectivity is required, using the command ipconfig –all. • To find out the MAC id from already active clients, follow the following method.
- 7. •Click on ‘lan clients’ under the ‘advanced’ menu
- 8. Copy the MAC ids for the clients whom access has to be permitted.
- 9. • To add the clients to the access list find the following method.
- 10. •Click on ‘wireless management’ under ‘advanced’ menu.
- 11. Select the check box ‘enable access list’ Select ‘allow’ Enter the MAC id in the space provided. Click on add.
- 12. Click on ‘apply’
- 13. • Save the entire configuration by following the method given below.
Editor's Notes
- Proceed to Wireless Security