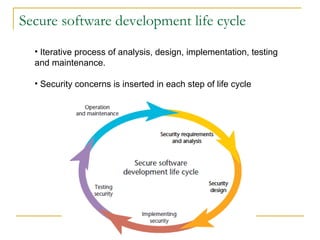
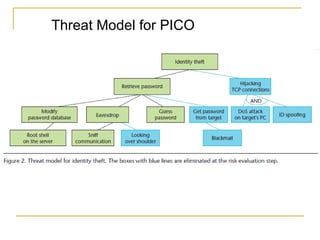
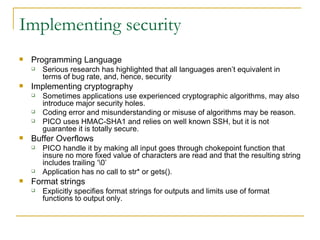
The document discusses secure software development methodology and provides an example of its application to the development of a messaging application called PICO. The methodology involves performing security analysis, design, and testing at each stage of the software development life cycle. For PICO, security threats are modeled and addressed through techniques like user authentication, encryption of messages, and preventing vulnerabilities like buffer overflows. Testing is an important but difficult part of the process, focusing on both expected and unexpected system behaviors.