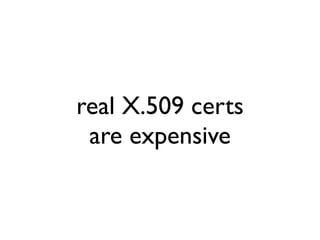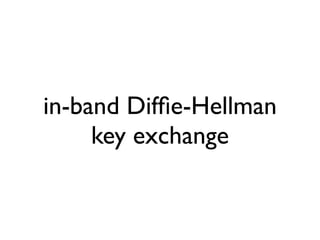Embed presentation
Downloaded 128 times









































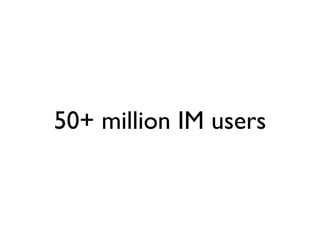






























































































































































































































Jabber is an open-source messaging protocol that was created in 1998. It uses XML over TCP connections and has a client-server architecture. While originally not designed with high security in mind, efforts have been made to enhance Jabber's security, including implementing TLS for encrypted connections, SASL for authentication, and working to enable end-to-end encryption. However, security challenges still remain and further improvements are needed areas like spam prevention and protecting against man-in-the-middle attacks.