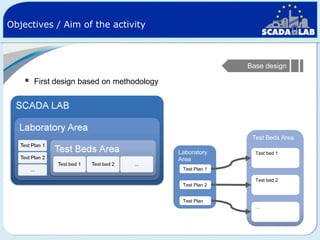
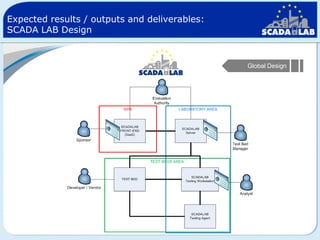
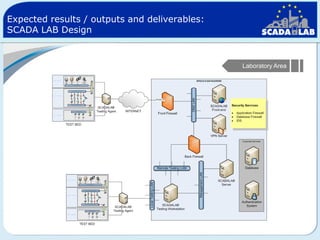
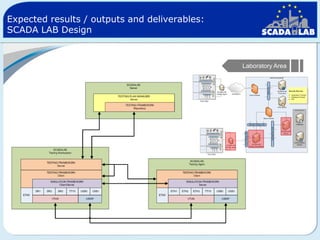
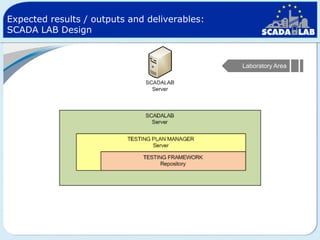
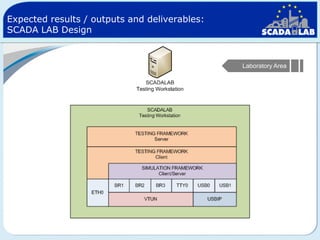
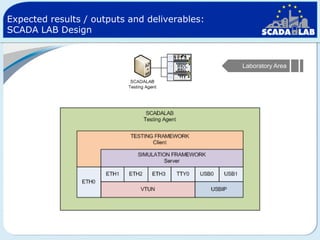
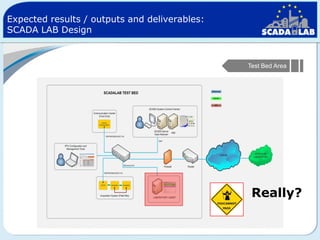
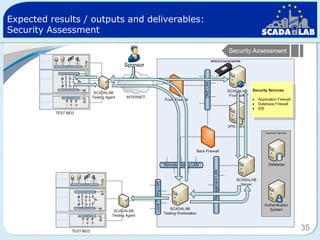
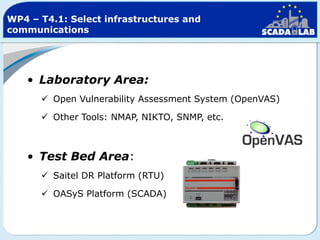
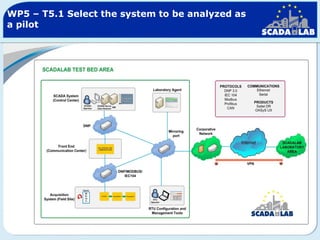
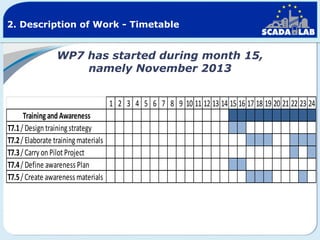
The document outlines work packages 4 and 5 of the SCADALab project. Work package 4 involves implementing the SCADA laboratory designed in work package 3, including setting up the laboratory area and connecting it to various test beds. Work package 5 focuses on pilot testing and experimentation using the new SCADA laboratory to conduct security assessments and tests on the connected infrastructure test beds. The work will validate the SCADA laboratory design and help refine it for future use in assessing the security of critical infrastructure systems.









![WP2 – T2.2: Develop Testing Methodology
• At a preliminary stage, 11 existing testing
methodologies (CPNI, US-CERT, ANSI/ISA,
INL [2], DOE, NIST, LEET, CERT-CC, ISECOM,
CCRA) were thoroughly analysed and rated
based on their suitability for the SCADALAB
project
• Later on, the information gathered through
the above task has been used as a basis to
develop an entirely new testing methodology
specific for the SCADALAB environment](https://image.slidesharecdn.com/scadalabproject-131203120436-phpapp01/85/First-SCADA-LAB-International-Workshop-11-320.jpg)