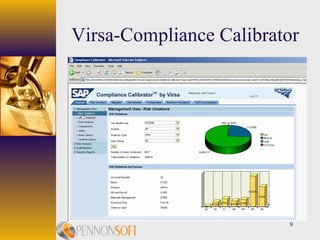
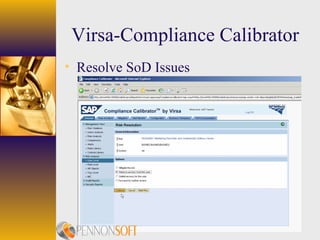
The document discusses using security compliance tools to detect and prevent security and controls violations in SAP systems. It outlines increased regulatory focus on security, risks like access control and segregation of duties issues, and how tools can help with real-time monitoring, resolving segregation of duties issues, and providing automated analysis and monitoring to assess authorization compliance. The benefits of these tools are that they can run with SAP, automate separation of duties analysis and monitoring of critical transactions, and provide quick assessments to business users, auditors, and security staff while avoiding manual analysis and false positives.