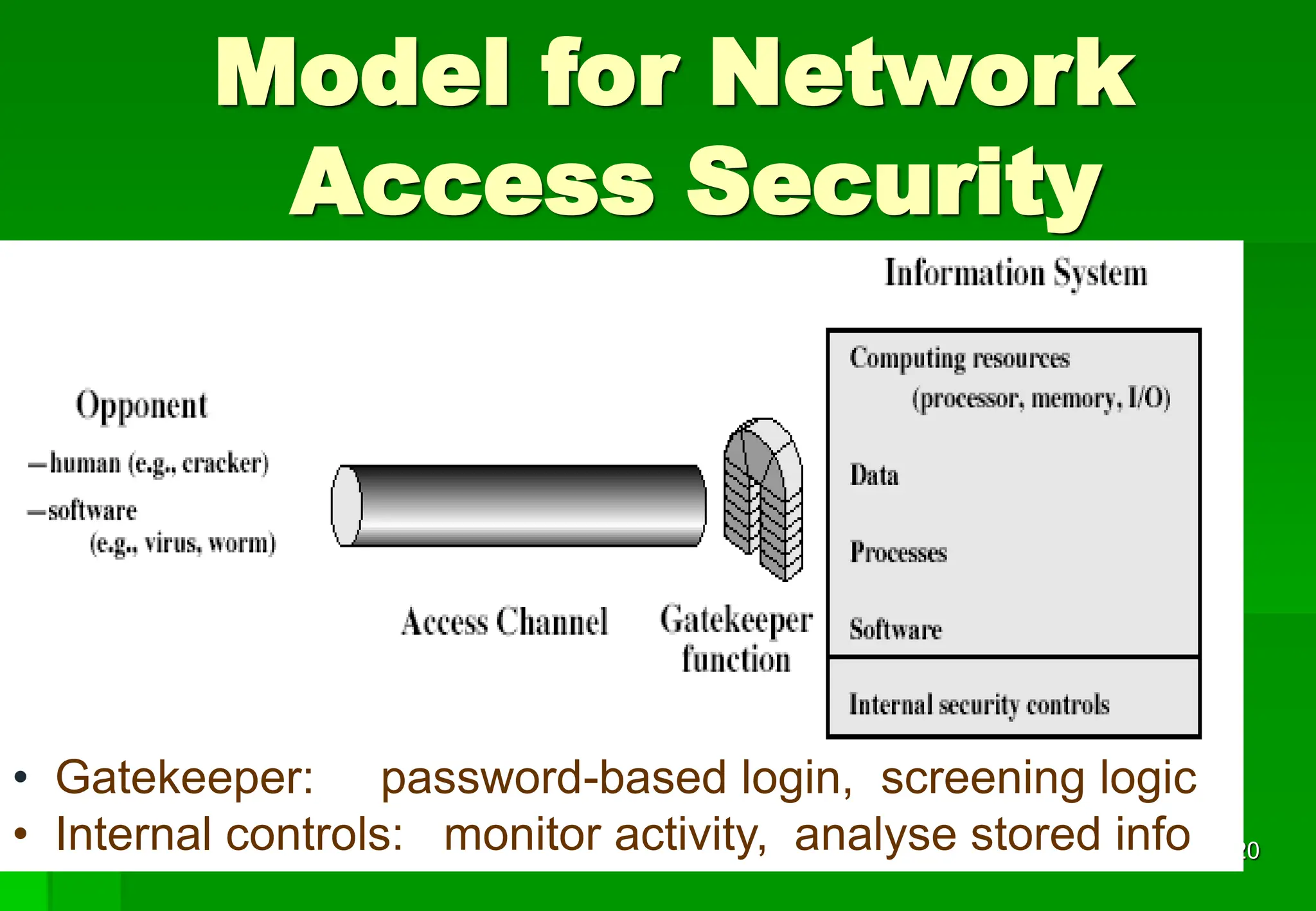
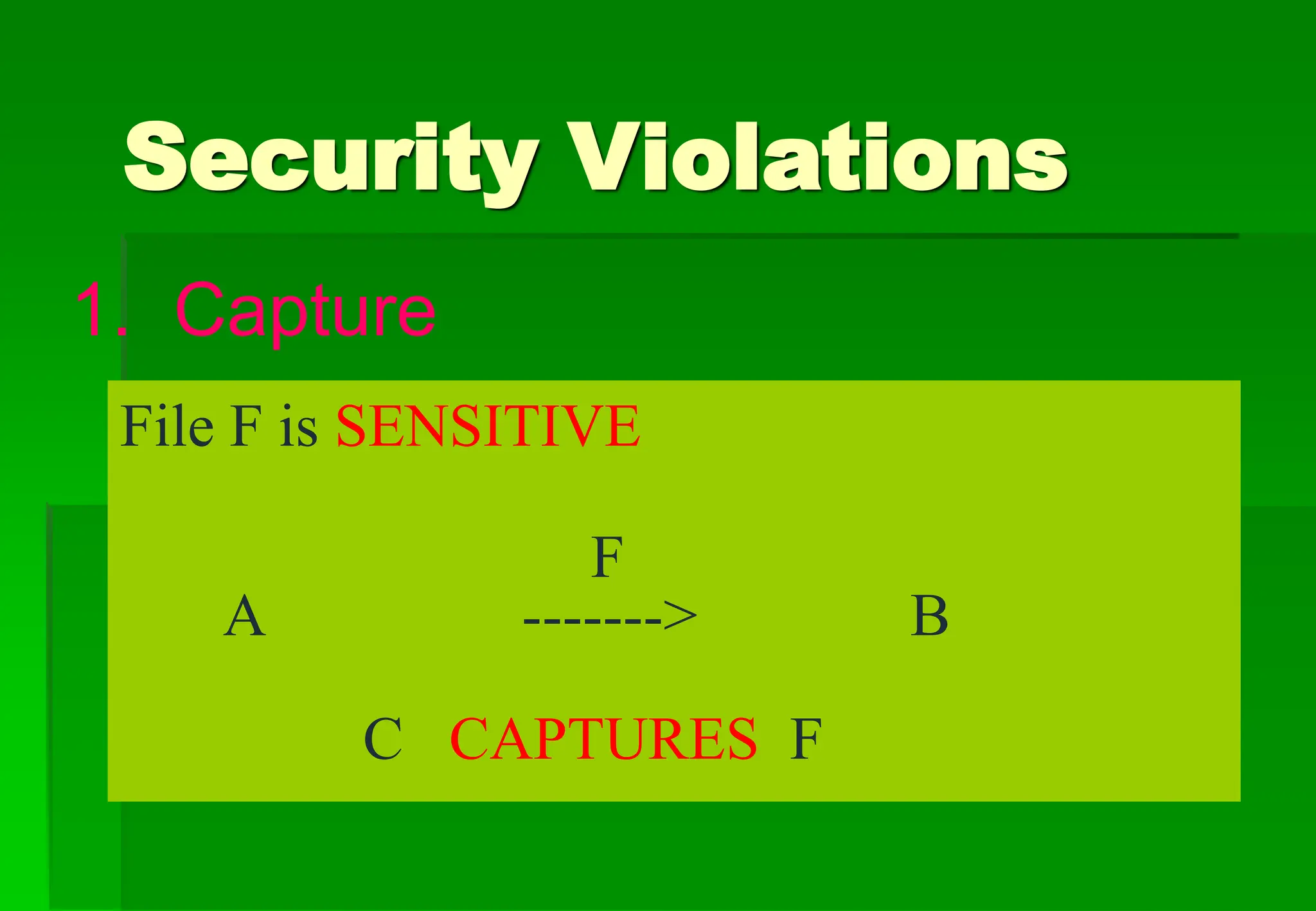
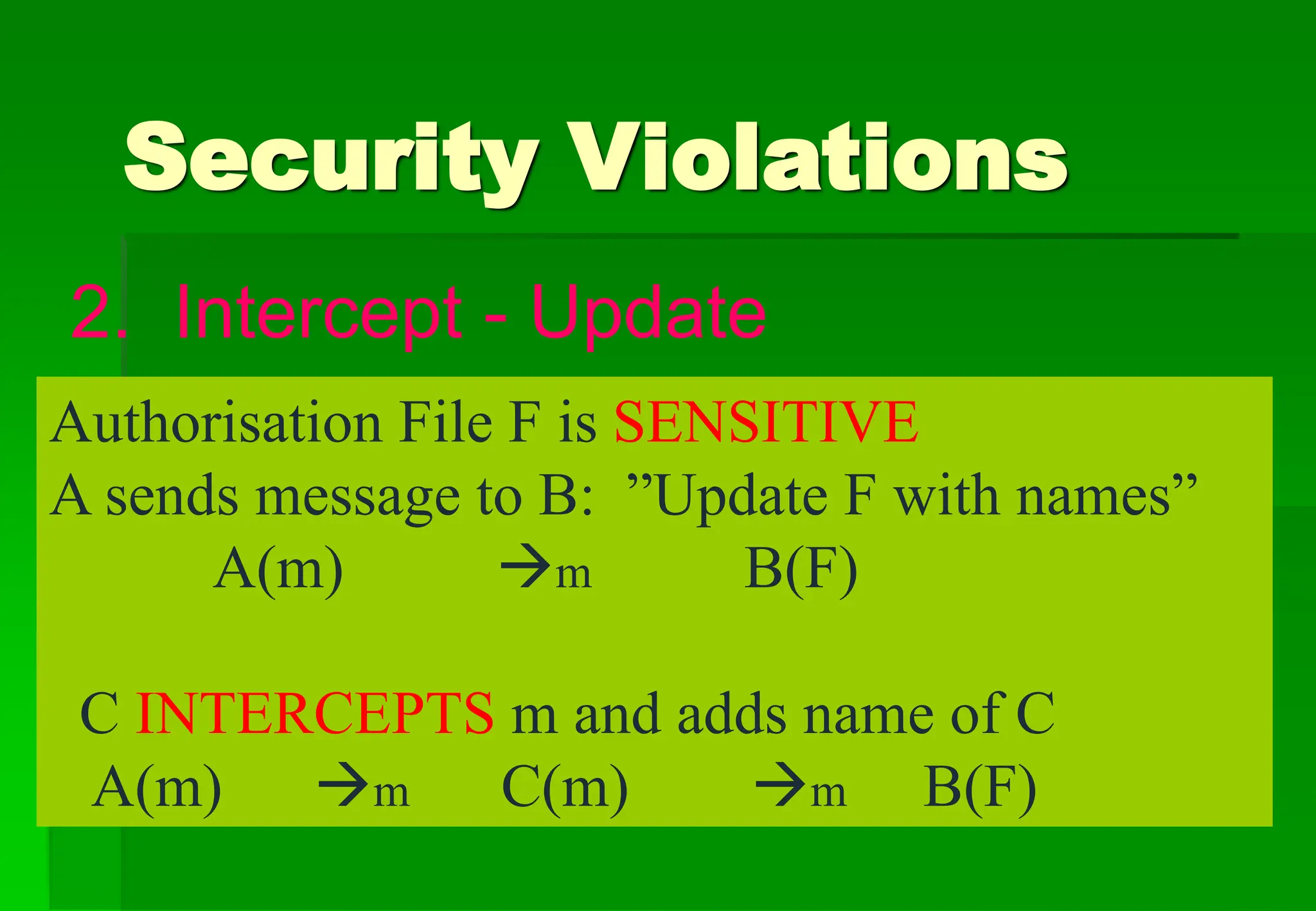
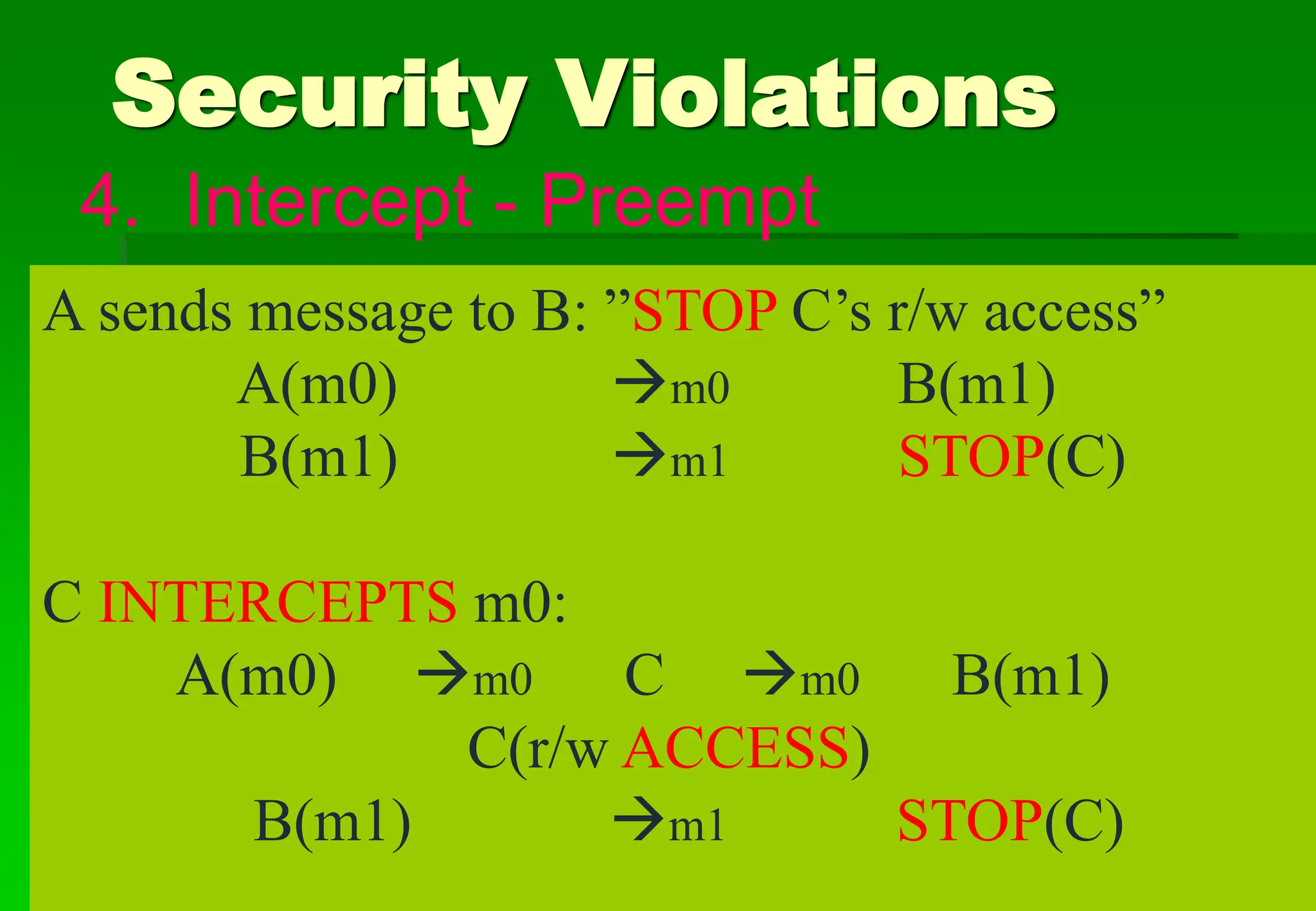
The document outlines security violations and the OSI security architecture framework, detailing various attack types and prevention mechanisms. It categorizes services such as authentication, access control, confidentiality, integrity, and non-repudiation, along with specific security mechanisms. Additionally, it addresses both passive and active attacks, emphasizing the importance of system integrity and availability in network security.




![OSI Security Architecture
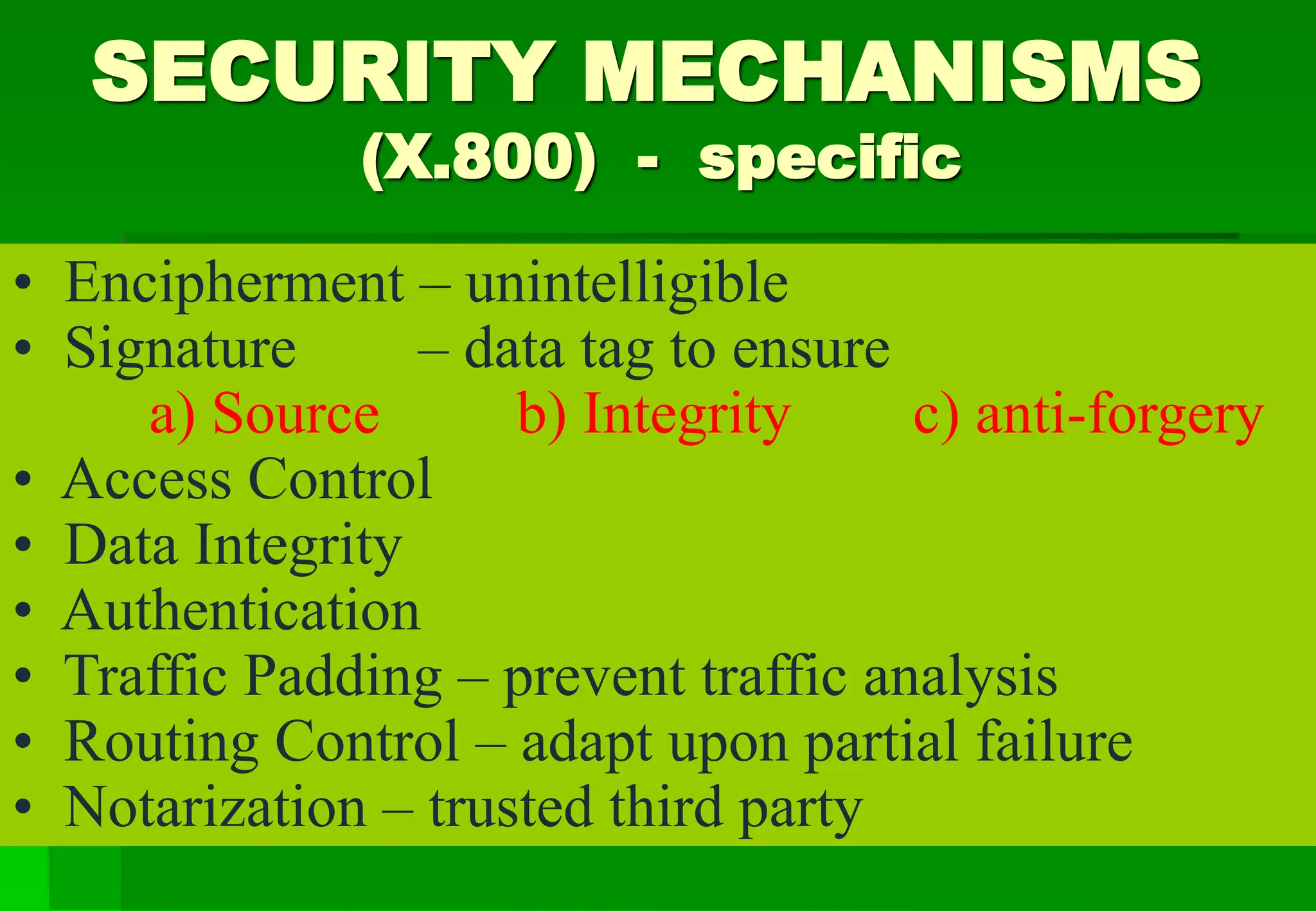
Categories(services)
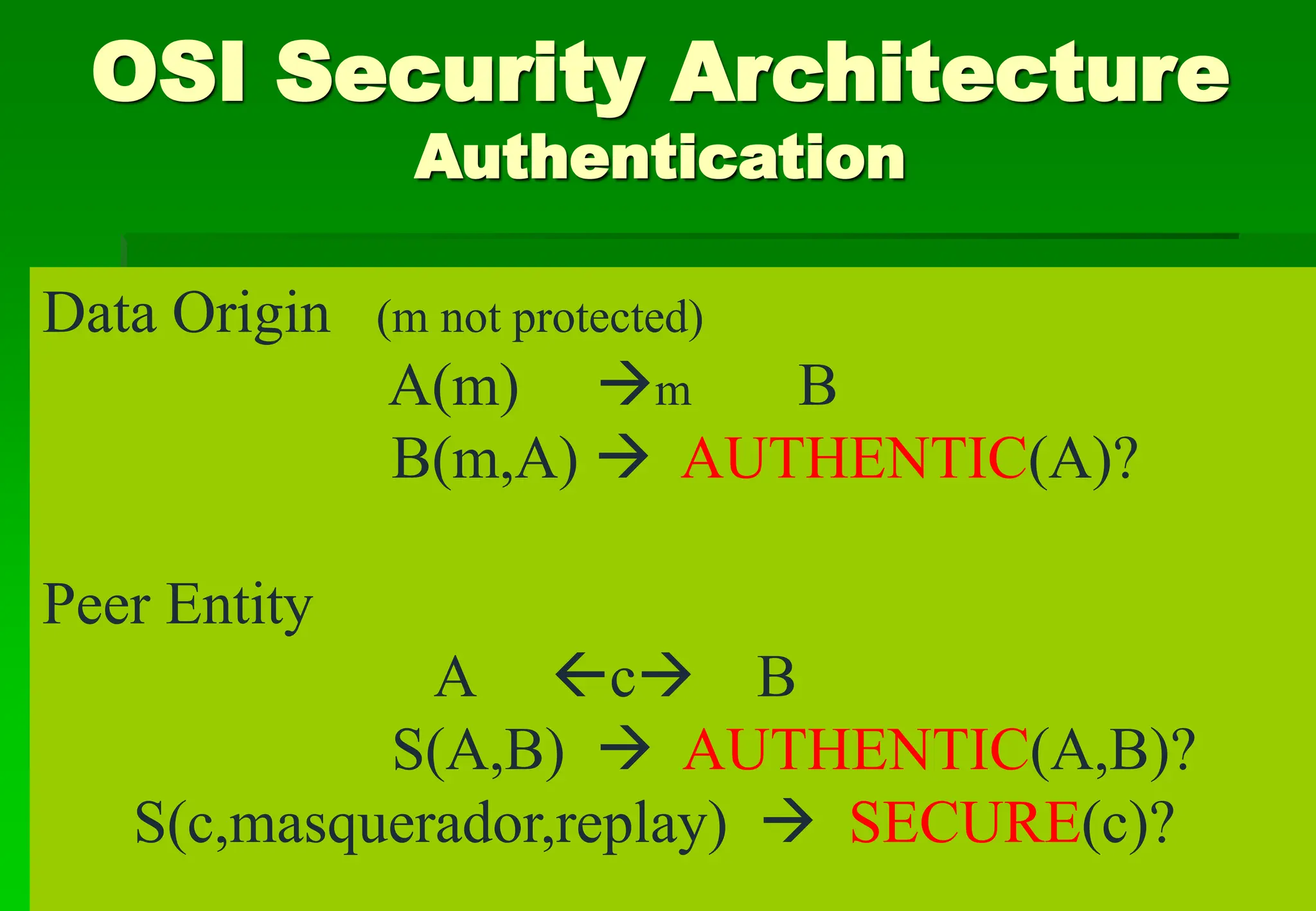
• Authentication (peer-entity, data-origin)
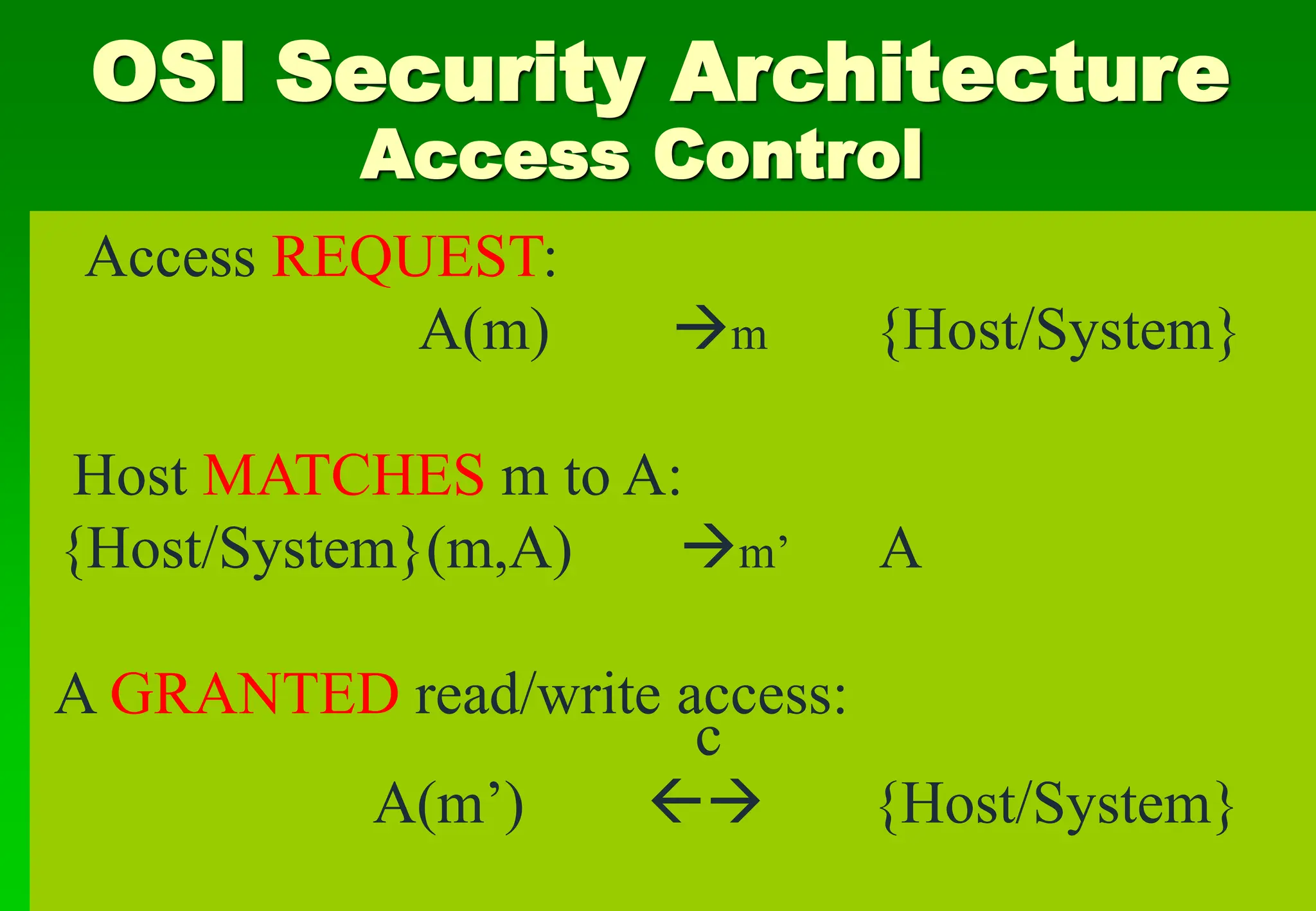
• Access Control
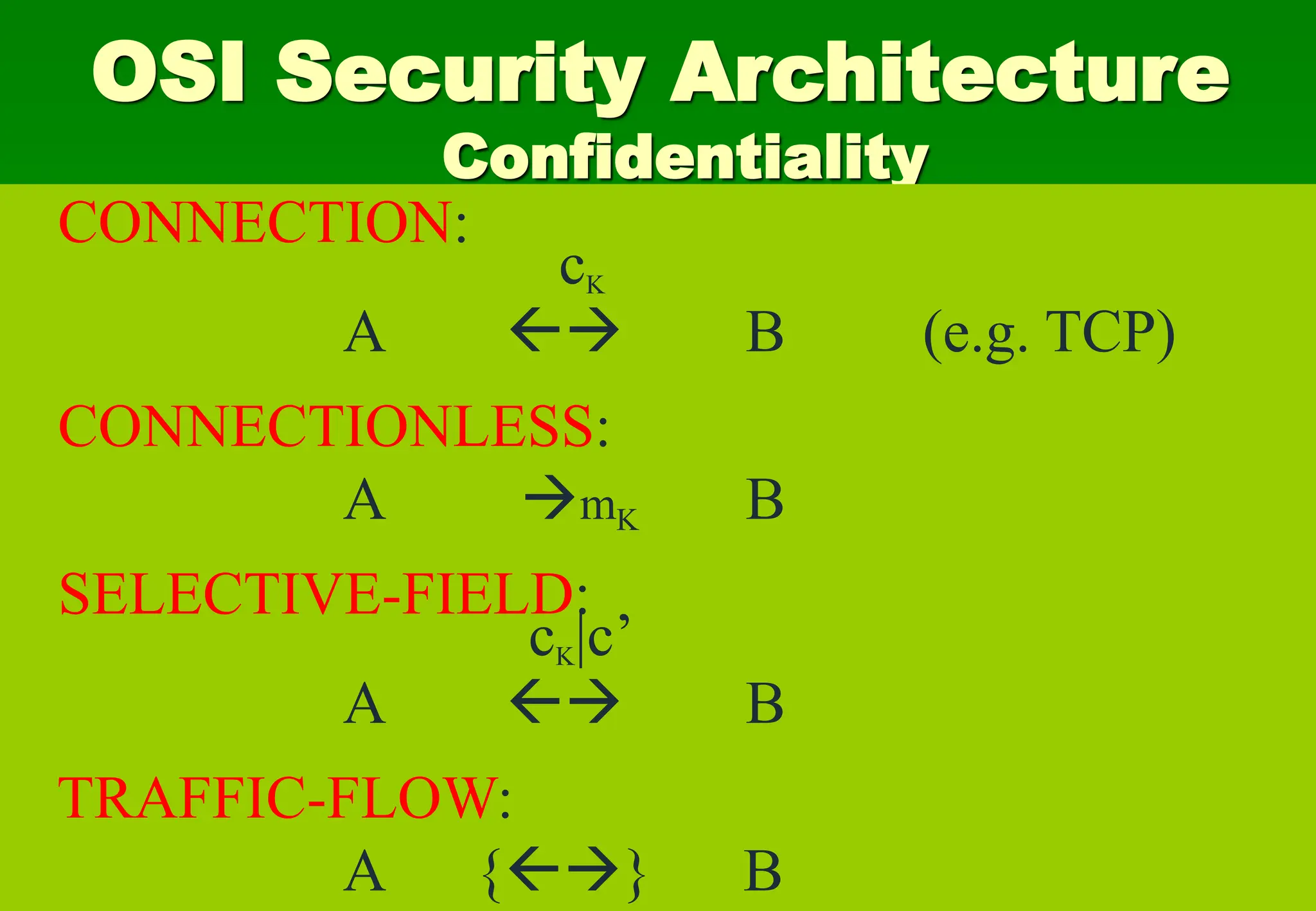
• Data Confidentiality (connection,
connectionless, selective-field, traffic-flow)
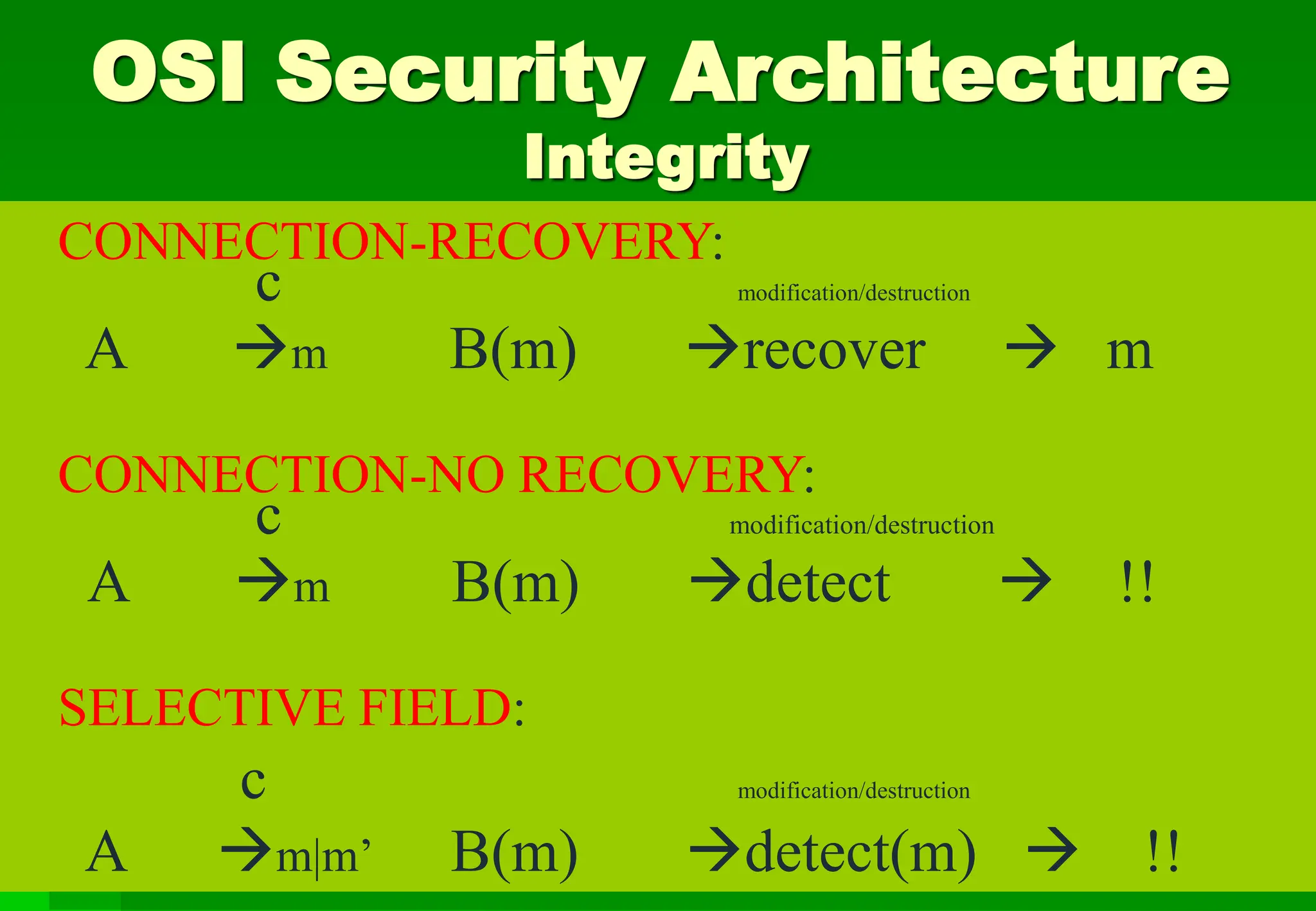
• Data Integrity (connection[recovery,
no-recovery, selective-field],
connectionless[no-recovery,selective-field])
• NonRepudiation (origin, destination)](https://image.slidesharecdn.com/chp1-240625143935-b96237bd/75/SA-Access-Control-Security-Violations-OSI-Security-Architecture-Network-Security-Model-Security-Violations-8-2048.jpg)
![OSI Security Architecture
Non-Repudiation
SENDER VERIFICATION:
A m,[A] B(m,[A]) mA
RECEIVER VERIFICATION:
A m B
B [m],[B] A([m],[B]) mB](https://image.slidesharecdn.com/chp1-240625143935-b96237bd/75/SA-Access-Control-Security-Violations-OSI-Security-Architecture-Network-Security-Model-Security-Violations-13-2048.jpg)