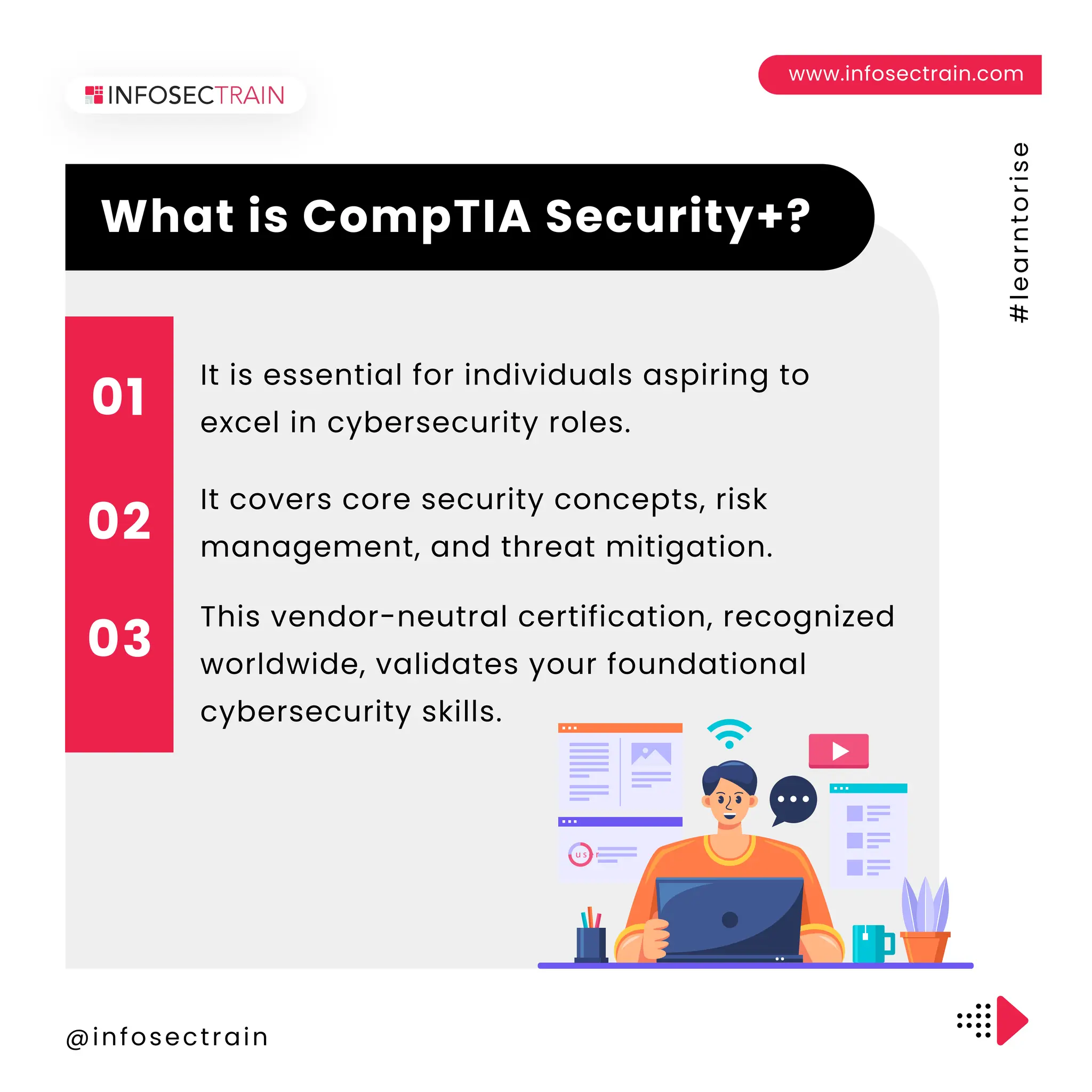
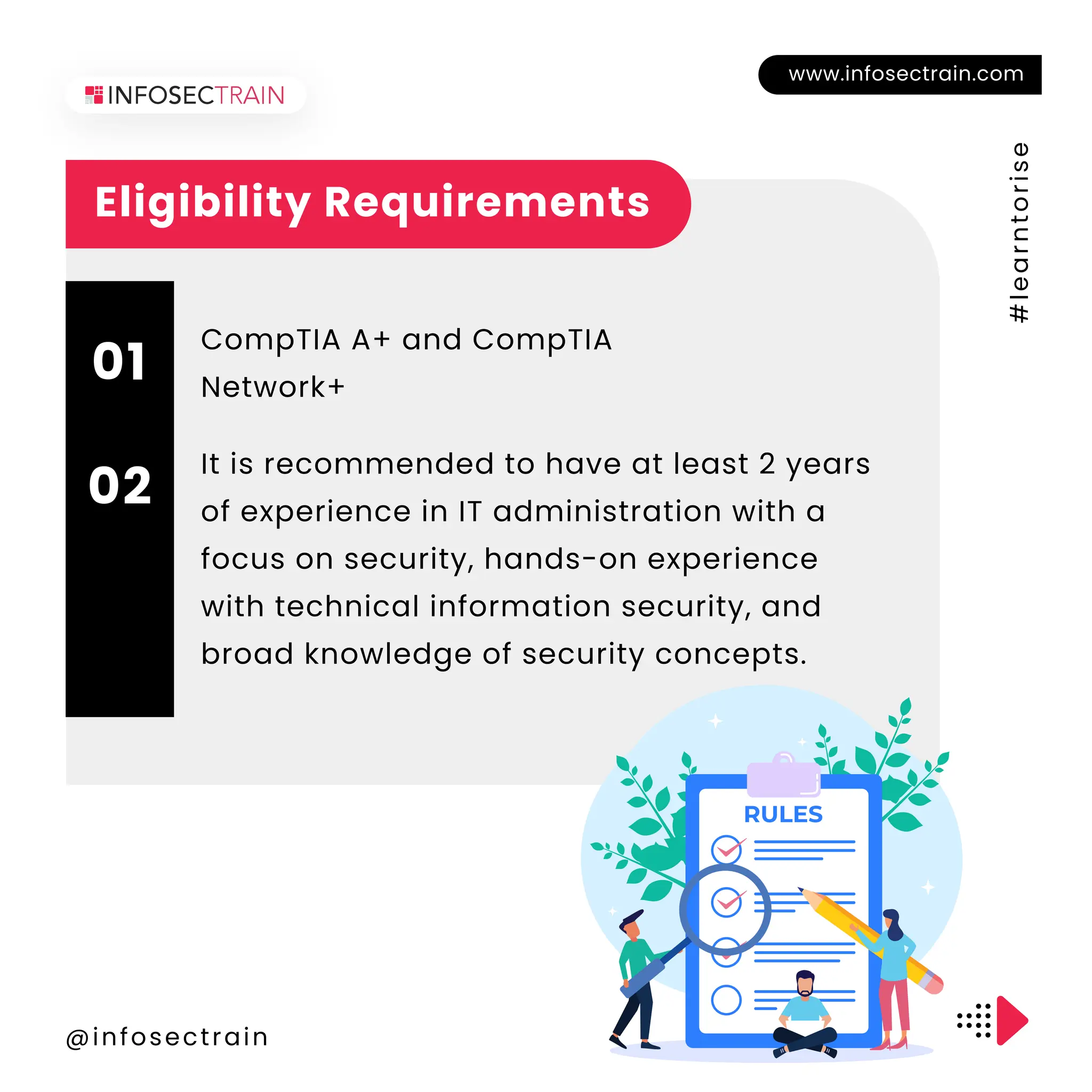
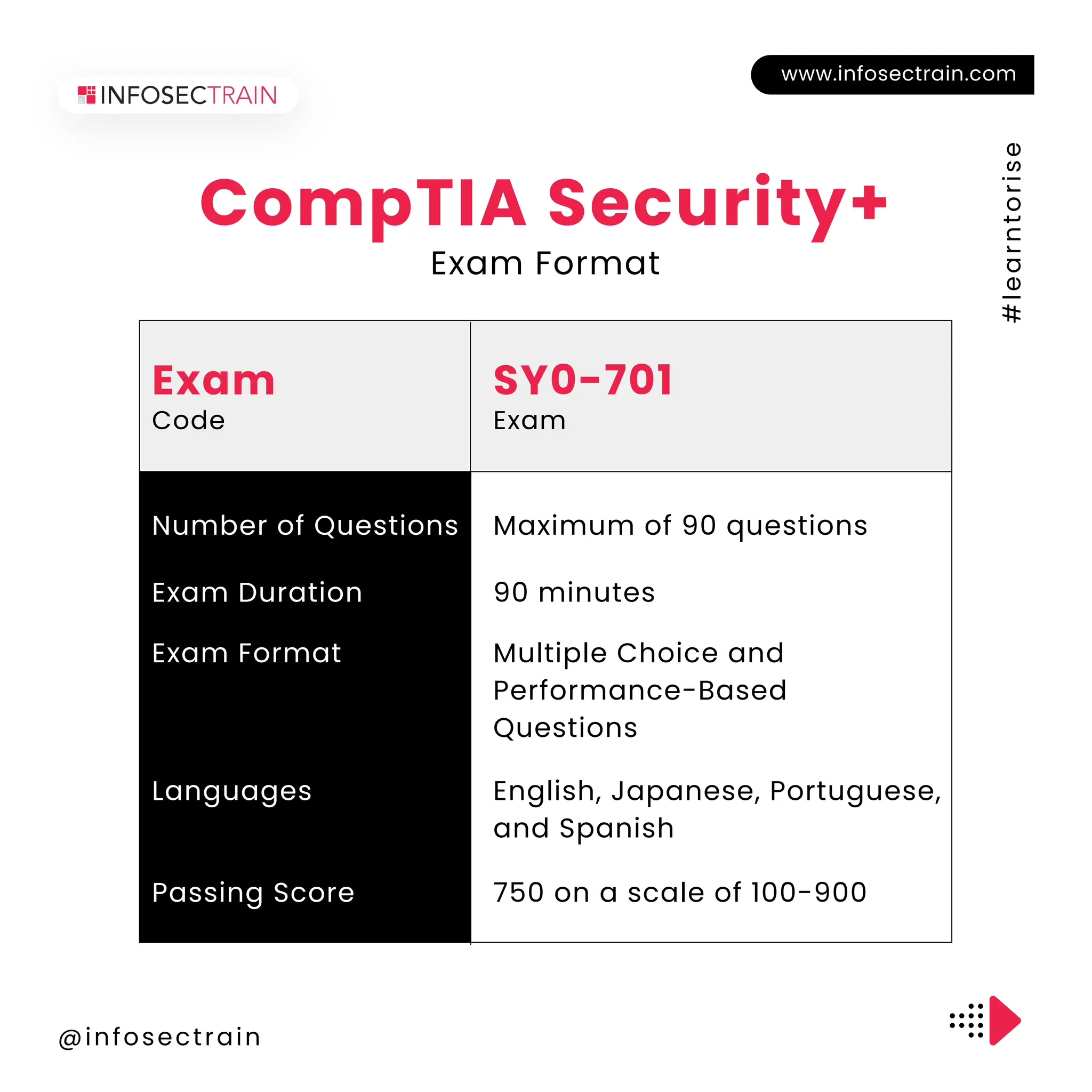
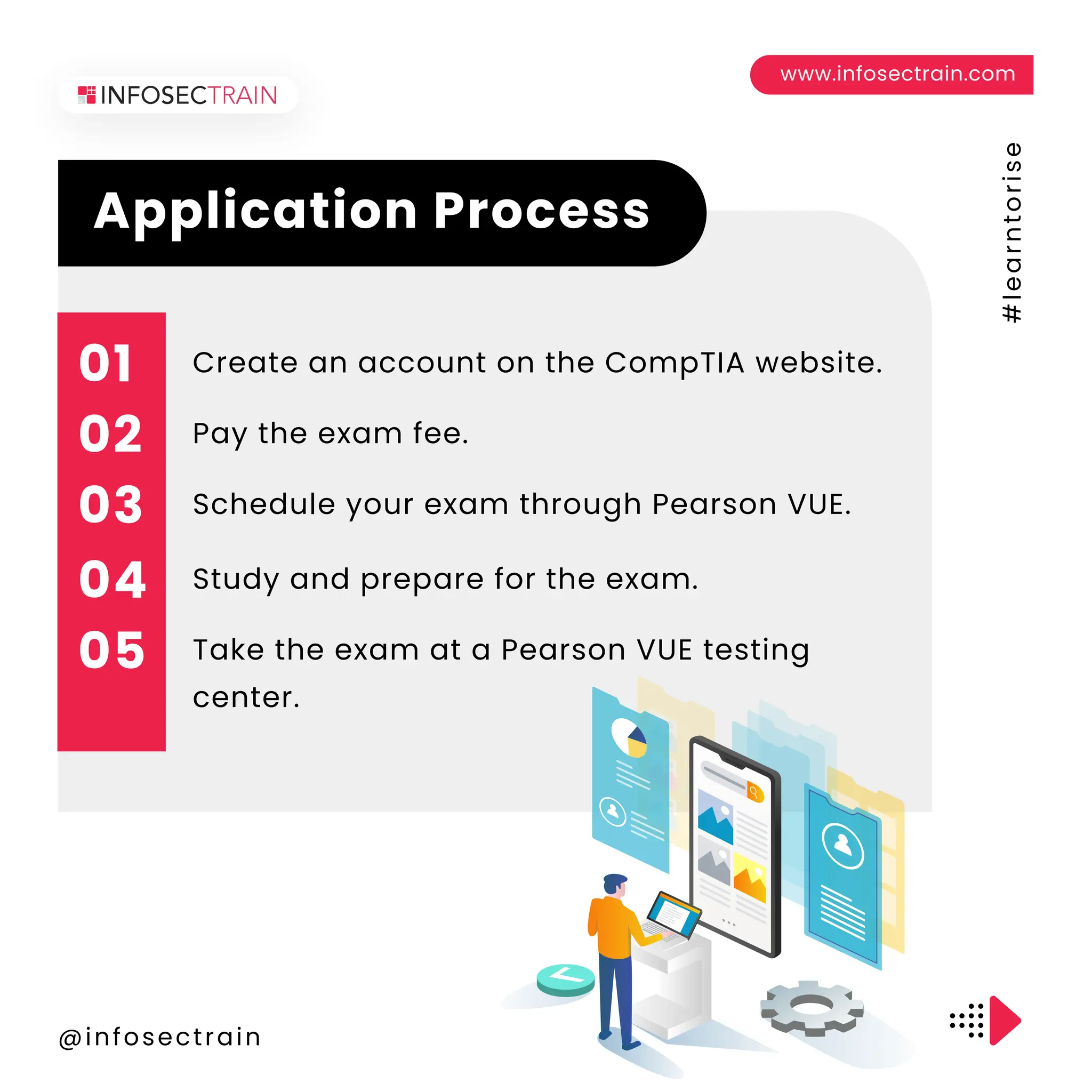
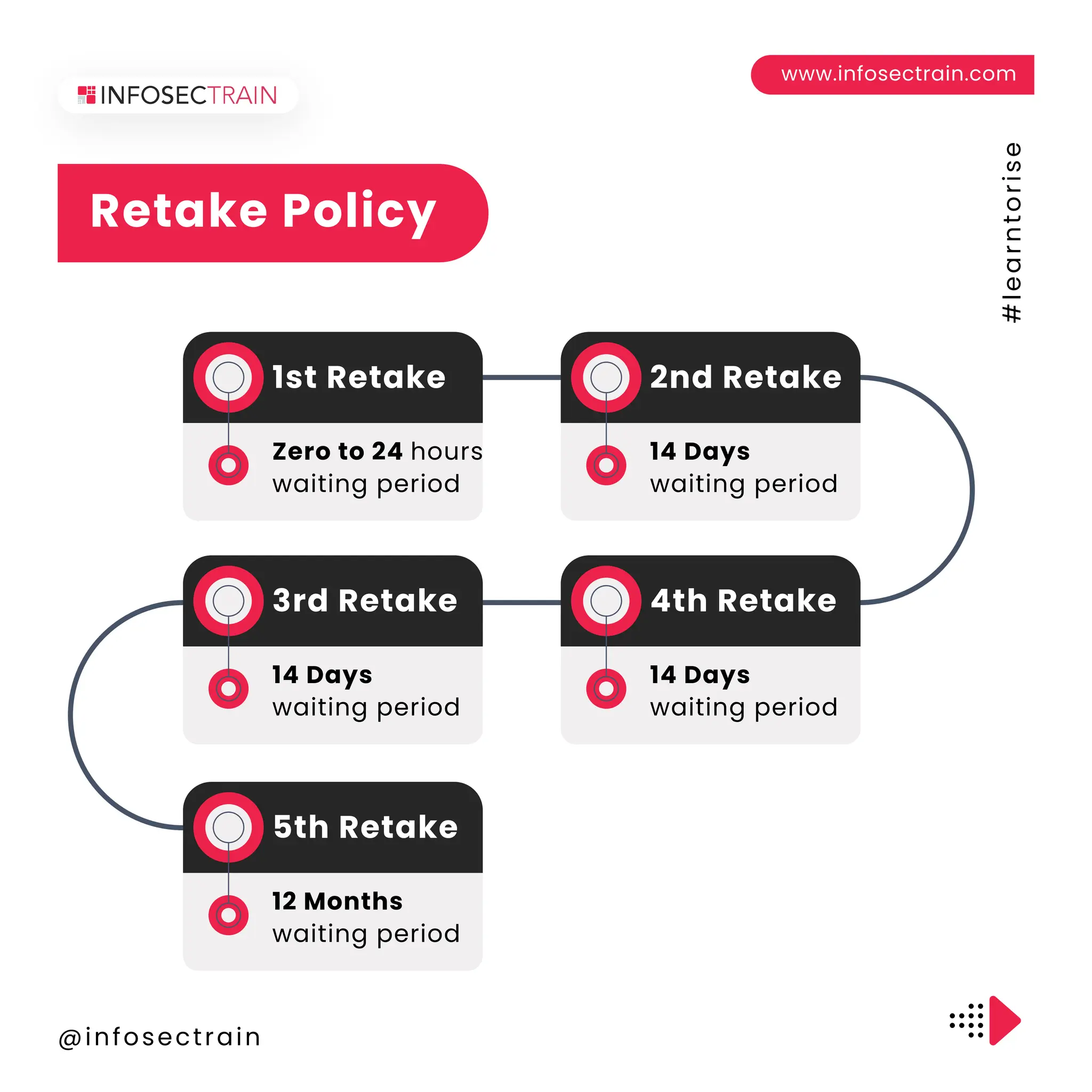
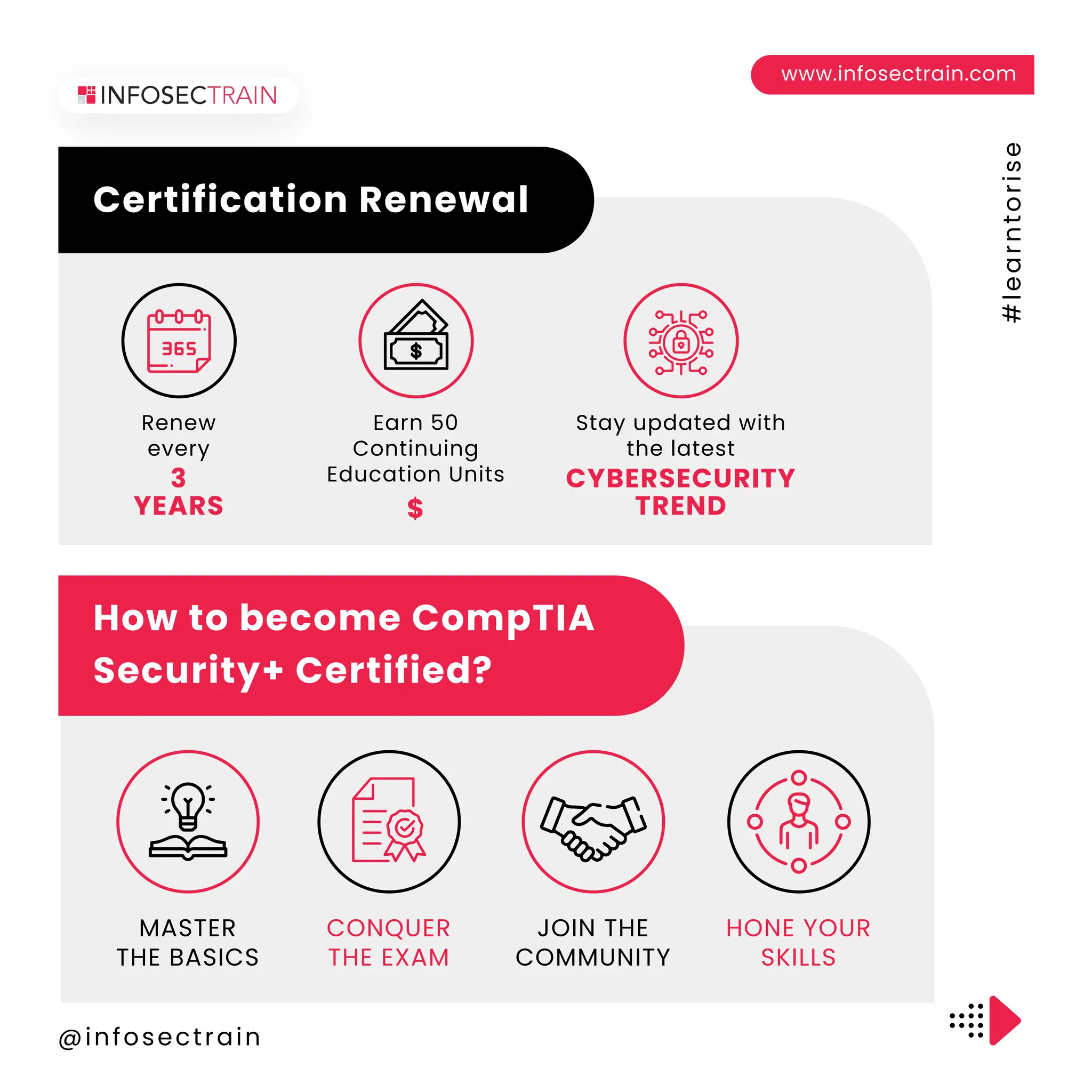
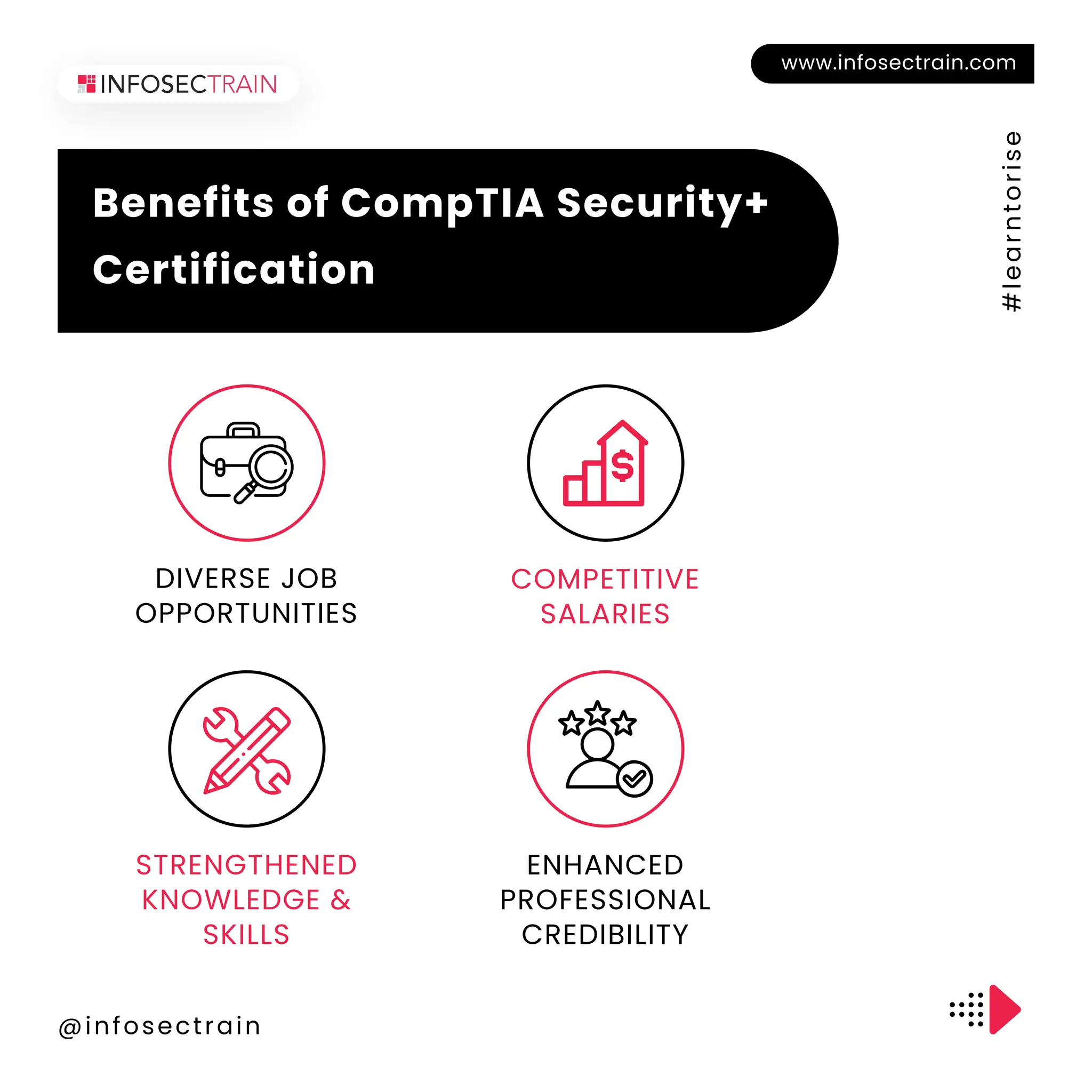
The document outlines the CompTIA Security+ certification, which covers core security concepts and is aimed at individuals pursuing careers in cybersecurity. It includes eligibility requirements, exam details, the application process, retake policies, and benefits of certification, such as job opportunities and enhanced credibility. Additionally, it highlights the importance of continuous education and skill development in the field.