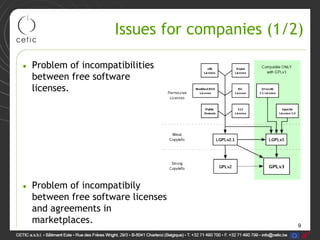
The document discusses legal issues related to analyzing source code for intellectual property violations. It summarizes tools like Ohcount that can detect licensing information in source code and find files related to attributions, patents, or brands. The presentation provides examples of using these tools to analyze simple libraries and free software suites to identify potential license violations or missing attribution files. Limitations include inability to analyze architecture or recognize all license types.
![[ RMLL 2013, Bruxelles – Thursday 11th
July 2013 ]
Legal analysis of source code
Presenter : Dr Ir Robert Viseur](https://image.slidesharecdn.com/rmll2013-rv-slides-licenses-130722162518-phpapp02/75/Legal-analysis-of-source-code-1-2048.jpg)