Embed presentation
Download to read offline

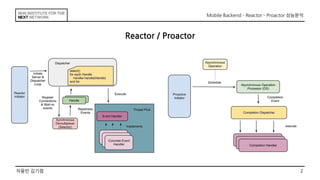

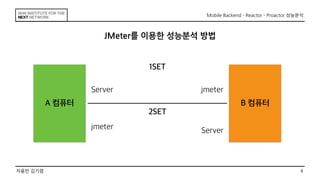
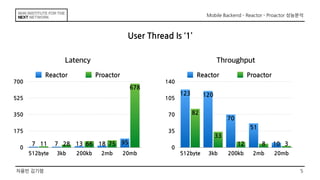
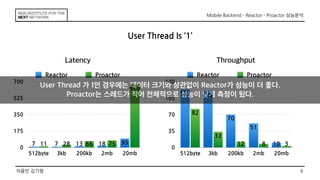
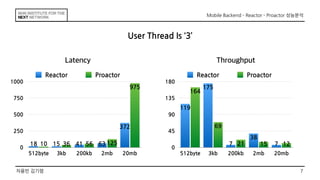
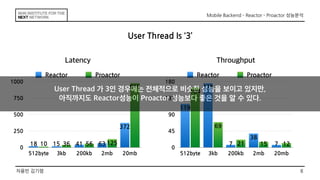
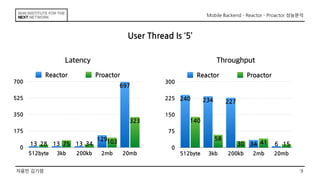

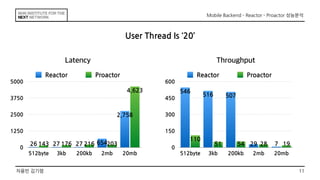
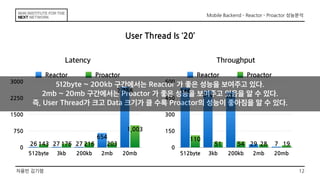
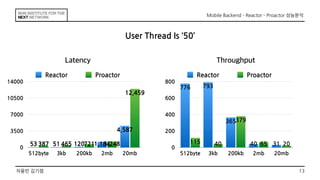




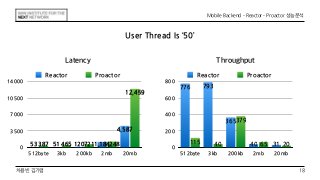
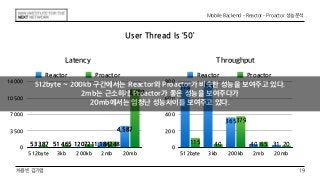



This document discusses the implementation of Reactor and Proactor patterns for a mobile backend server. It describes code for handling connections and dispatching events using the Reactor pattern with thread-per-connection and thread pool approaches. It also describes an implementation of the Proactor pattern that uses non-blocking I/O with asynchronous socket channels and completion handlers. Code examples and class diagrams are provided to illustrate how events are handled asynchronously without blocking server threads.





















