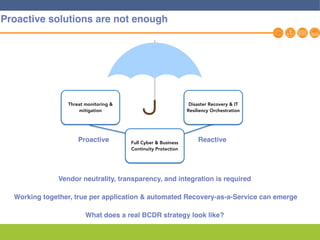
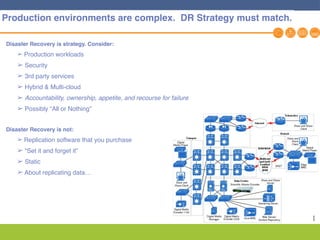
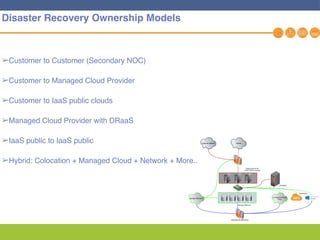
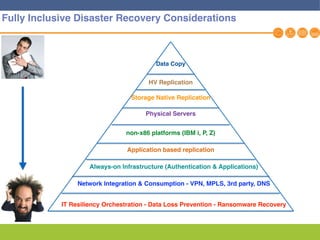
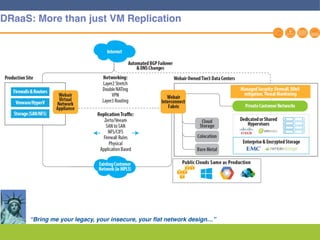
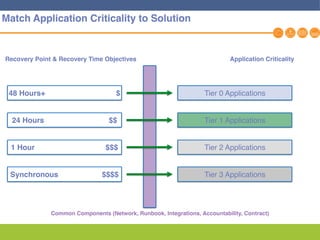
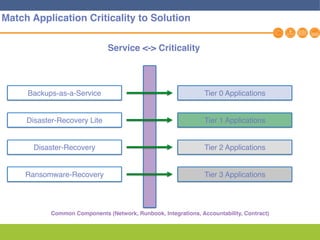
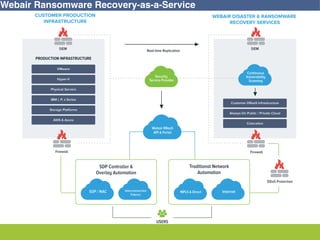
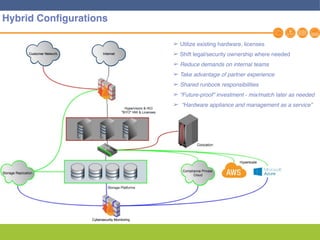
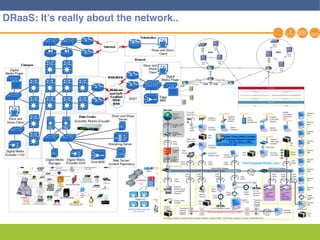
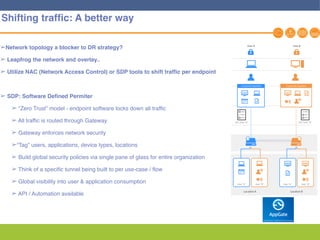
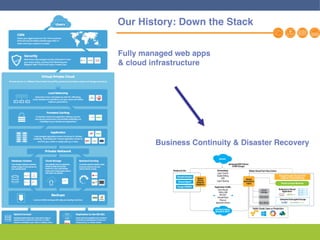
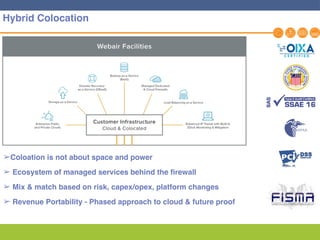
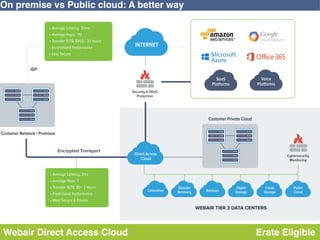
This document discusses disaster recovery strategies and solutions. It notes that production environments are complex and a DR strategy must match this complexity. It considers factors like production workloads, security, third party services, hybrid/multi-cloud environments, testing, and accountability. The document also discusses various DR ownership models including customer-managed, DRaaS, and hybrid options. It emphasizes the importance of network integration and outlines considerations for security, testing, and matching application criticality to the appropriate DR solution.