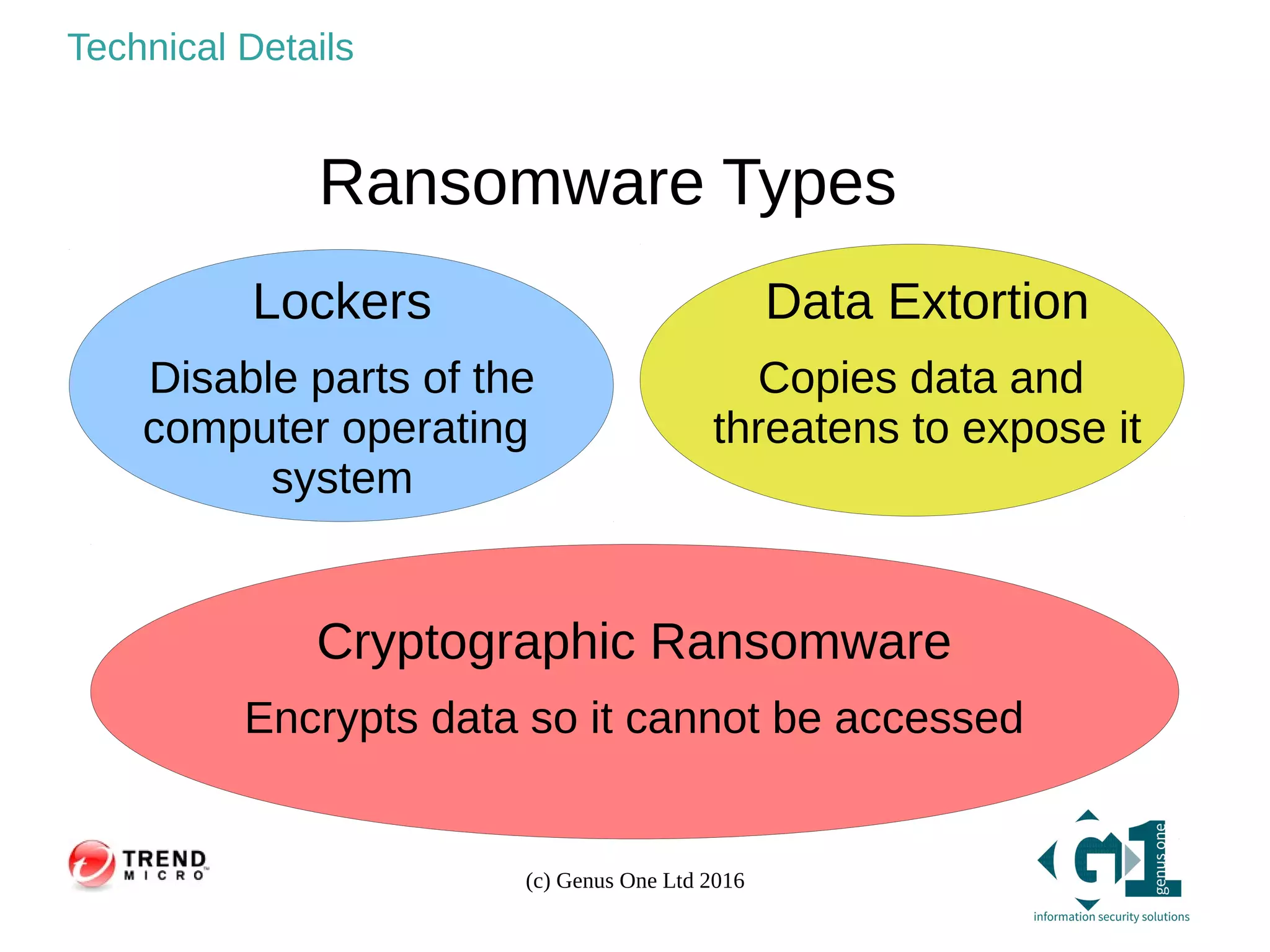
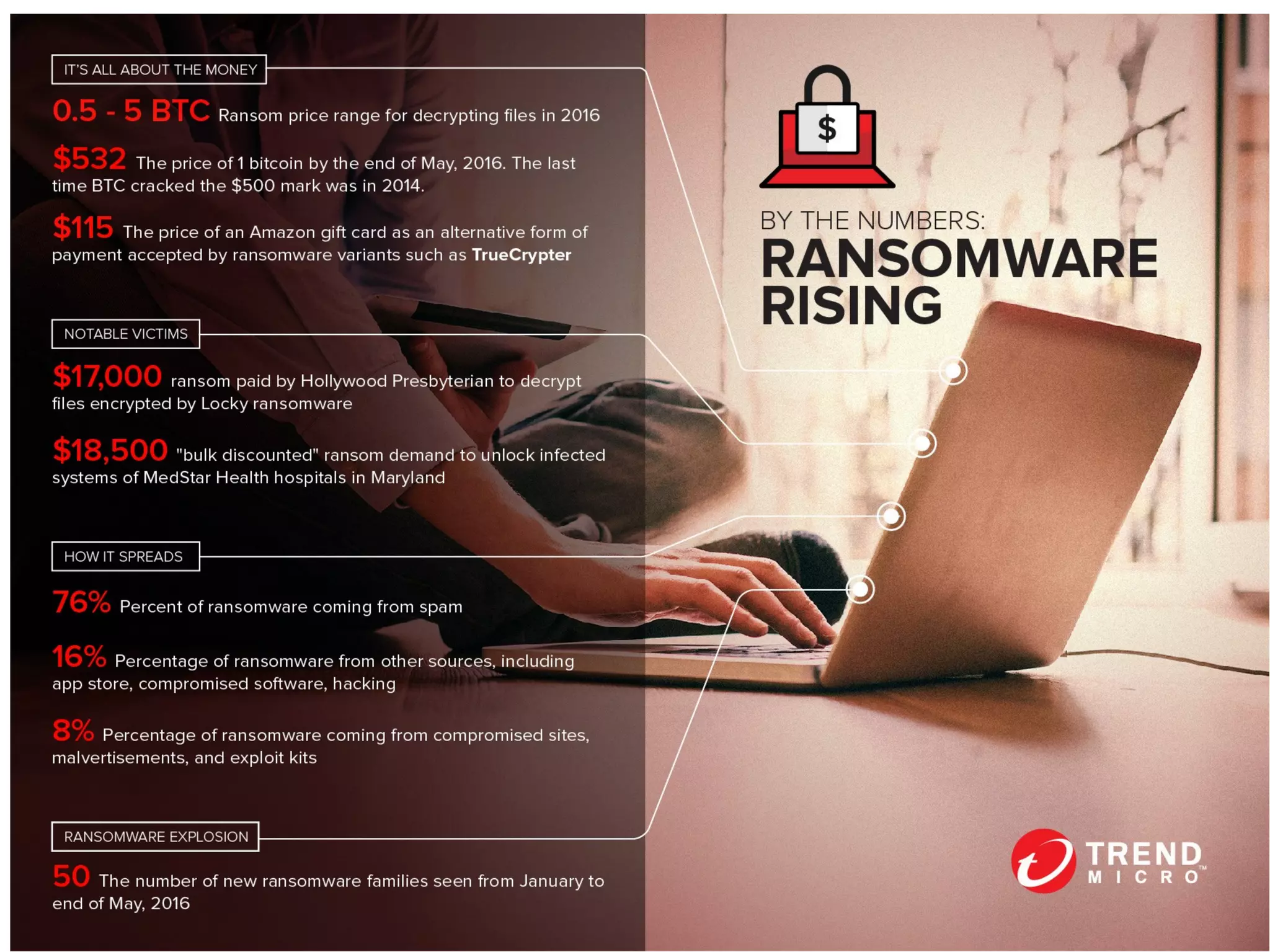
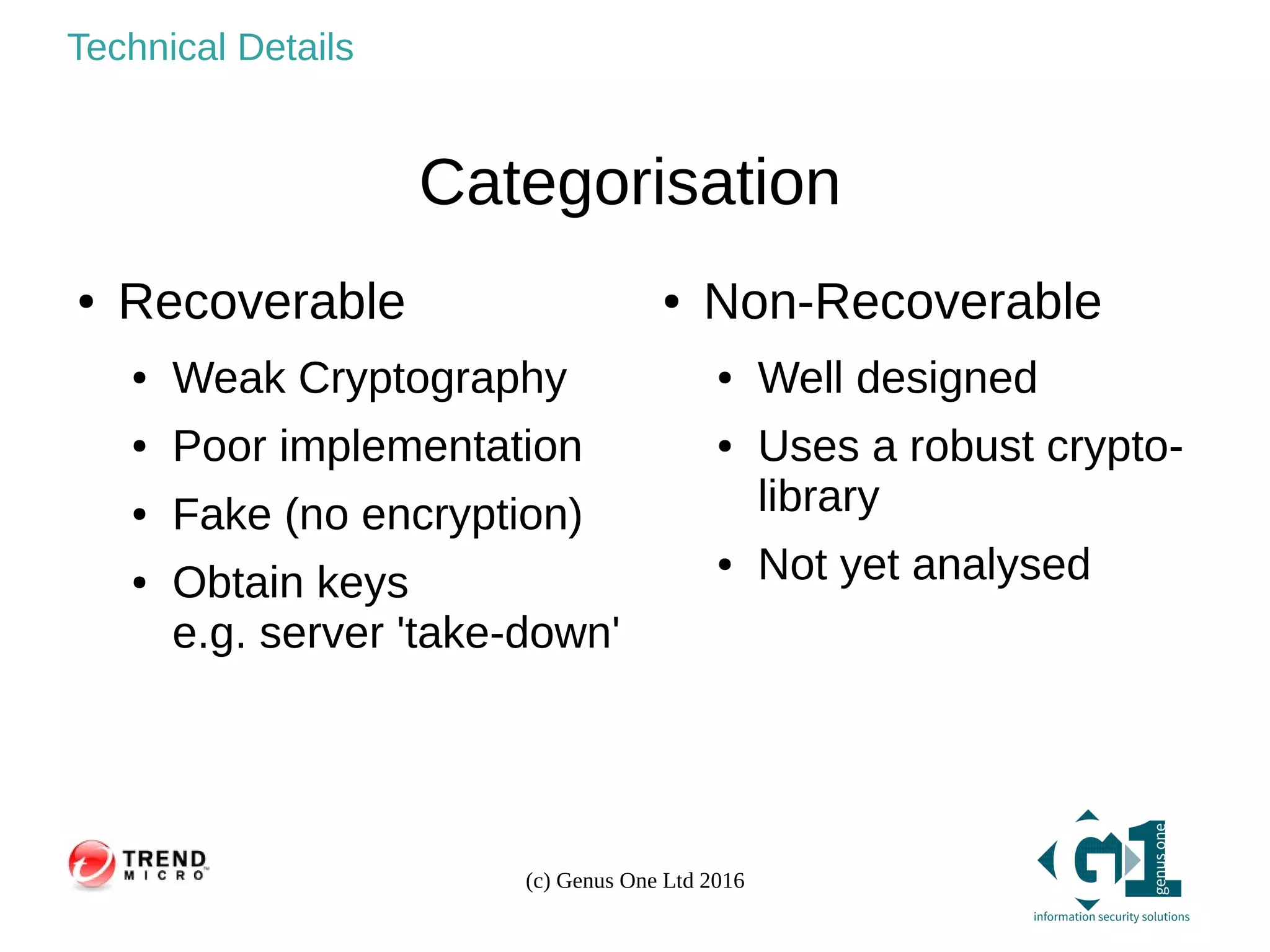
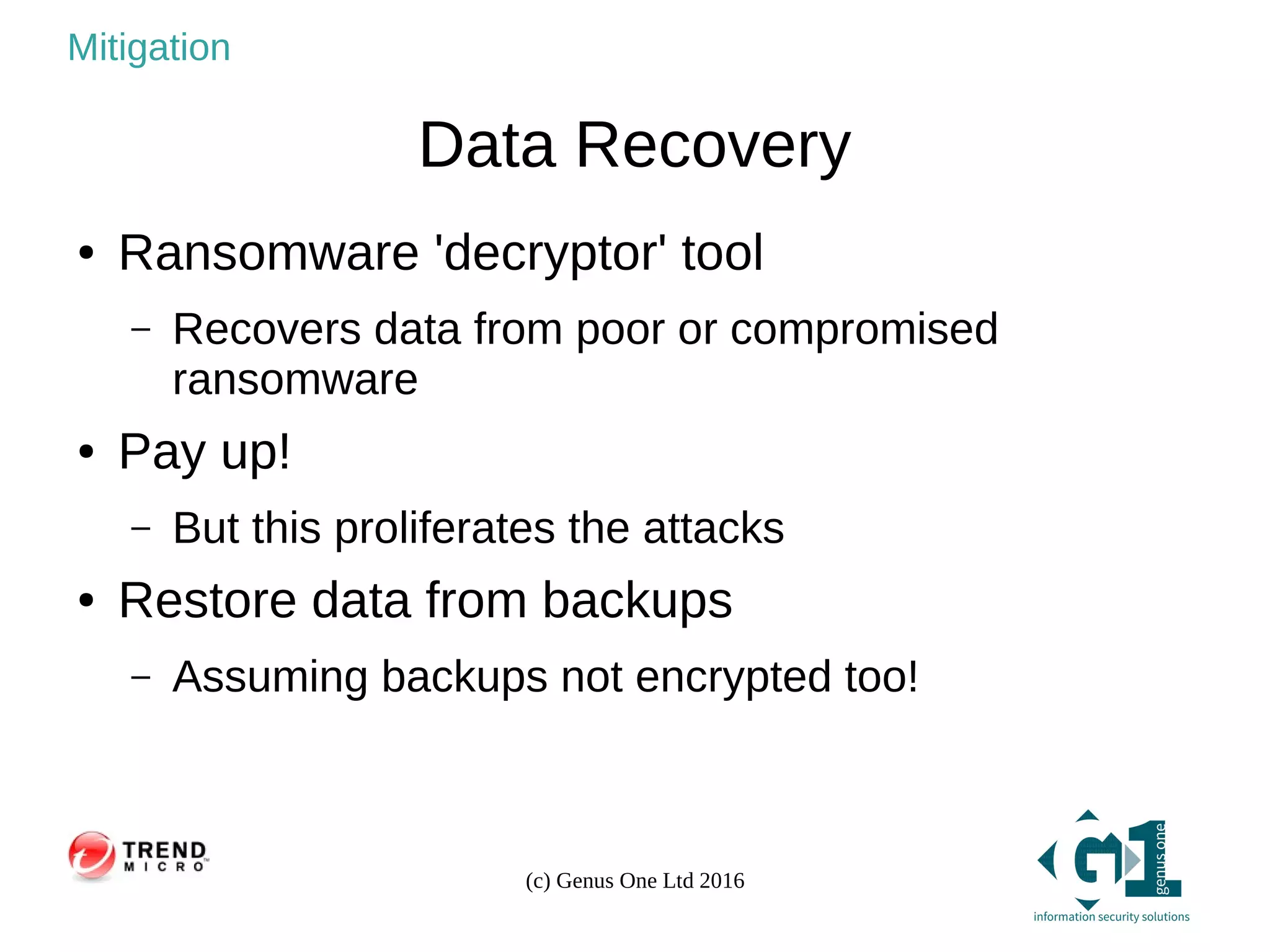
The document provides an overview of ransomware, its types, and methods of prevention. It highlights the prevalence of ransomware attacks, particularly in the UK, where many businesses and universities have been targeted. Mitigation strategies include data recovery options, anti-virus software, and robust information security management practices.



![(c) Genus One Ltd 2016
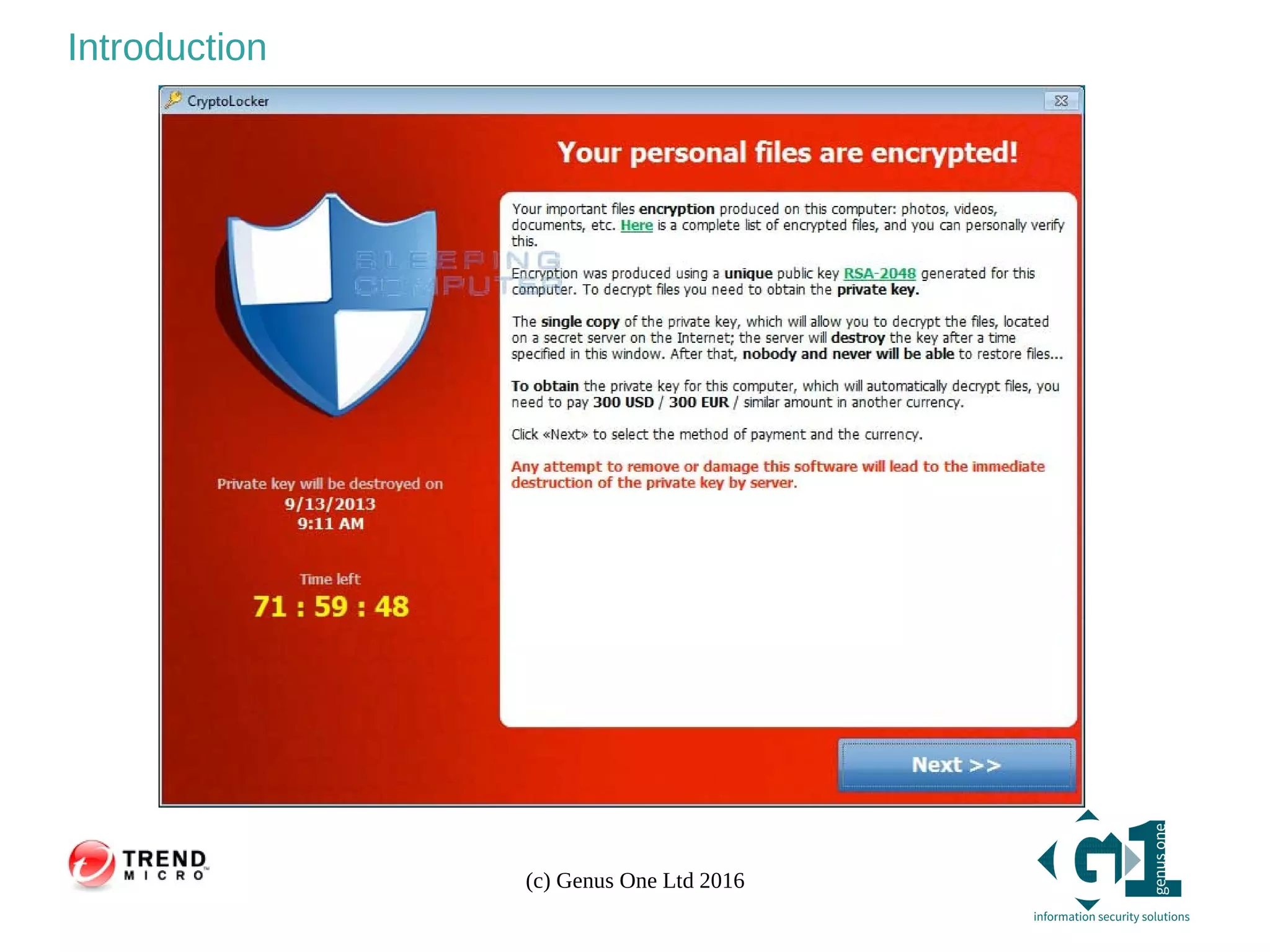
Introduction
Observations
“The researchers consulted
during this study widely hold the
opinion that cryptography is no
longer being used for
obfuscation of modern malware
and is of decreasing relevance”
● [What if] more
complex cryptography
were used - along the
lines described in this
report?
● Why isn't there more
ransomware?](https://image.slidesharecdn.com/ransomware-markchimelypdfversion-161018101121/75/Ransomware-Mark-Chimely-4-2048.jpg)
![(c) Genus One Ltd 2016
Introduction
New Age of Ransomware
● In Britain 54% of surveyed businesses have
been targeted with ransomware {Malwarebytes}
● Over 120 separate families of ransomware
● “... businesses which have spent hundreds of
millions of dollars on end-point security … are
still getting hit by [ransomware]” {Bromium}
● 56% of UK universities suffered a ransomware
attack in the past year {SentinelOne}](https://image.slidesharecdn.com/ransomware-markchimelypdfversion-161018101121/75/Ransomware-Mark-Chimely-6-2048.jpg)