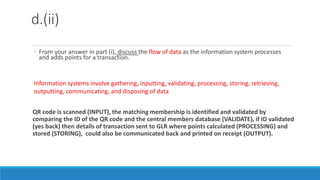
The Guest Loyalty Rewards information system aims to record transactions by members and track points awarded to customers. It stores member data such as name, contact details, transactions, points awarded and redemptions. Using QR codes on membership cards provides a convenient, efficient and reliable way to input transaction data compared to ledgers. Scanning the QR code inputs data which is then validated, processed by adding points, and stored. Additional security could involve requesting a PIN or photo verification when redeeming points. Reports showing points redemption patterns can help motel managers with planning by identifying popular locations. If a customer requests their data be removed, GLR must delete personal information while retaining transactional data for business purposes.