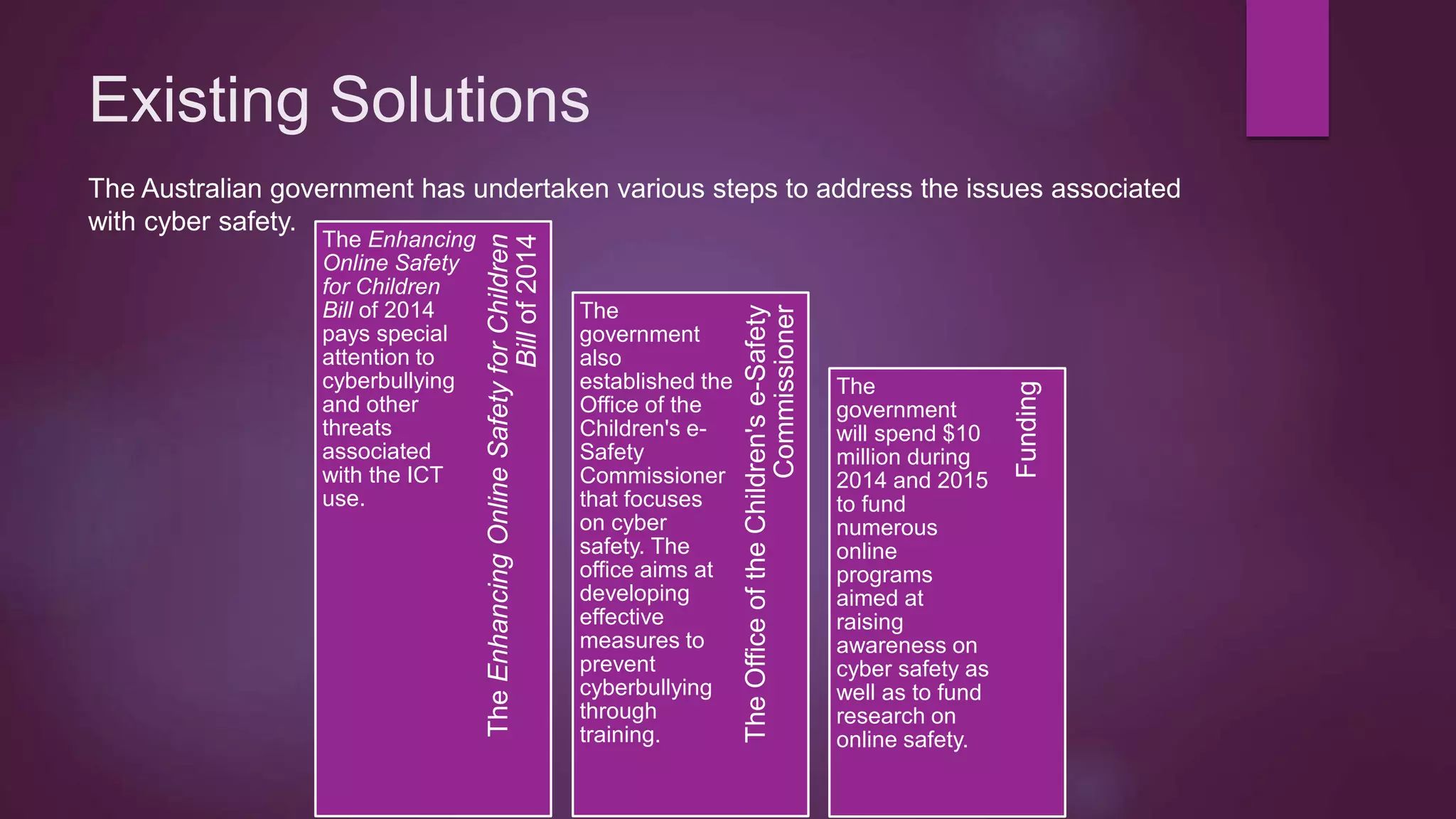
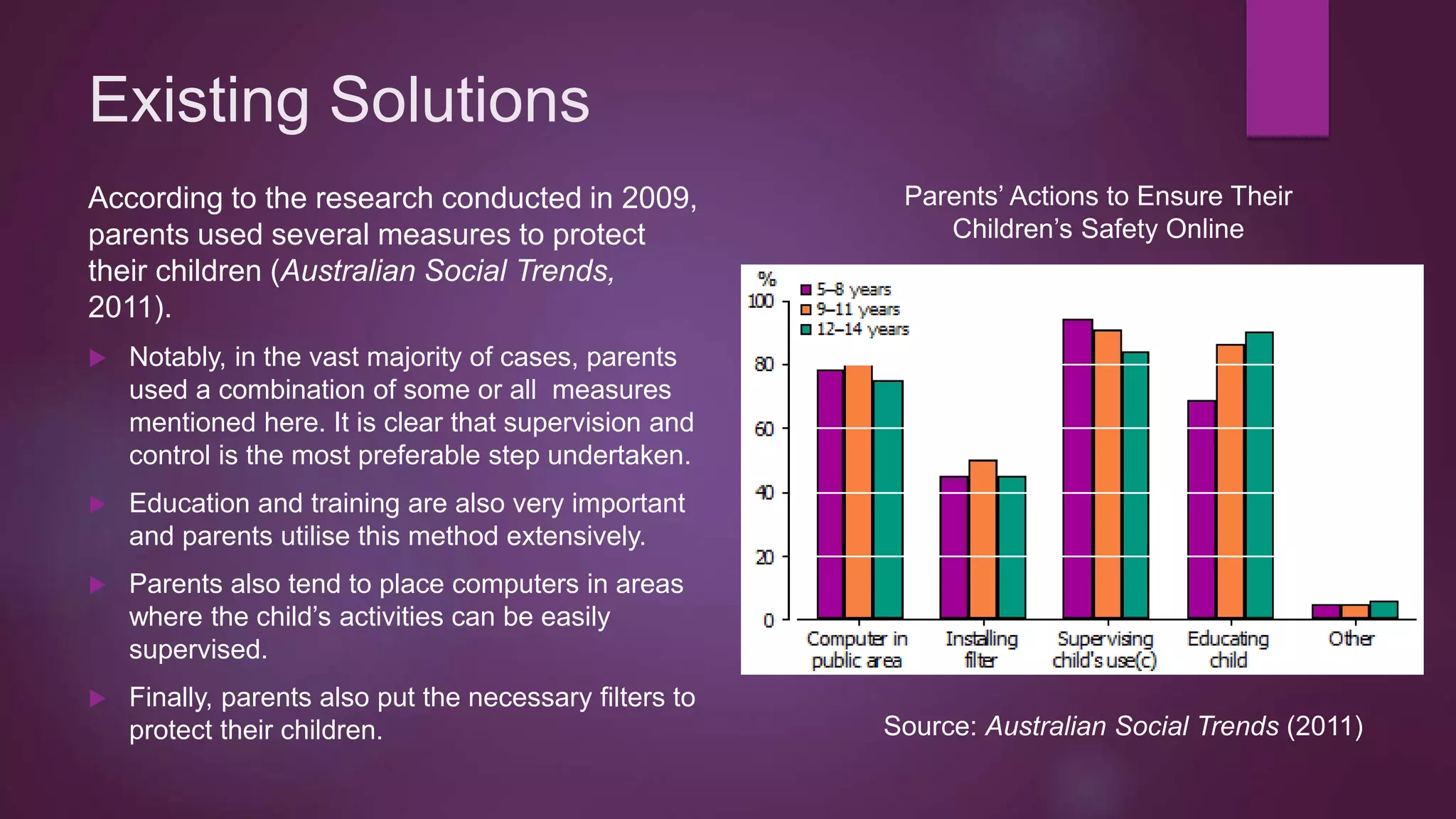
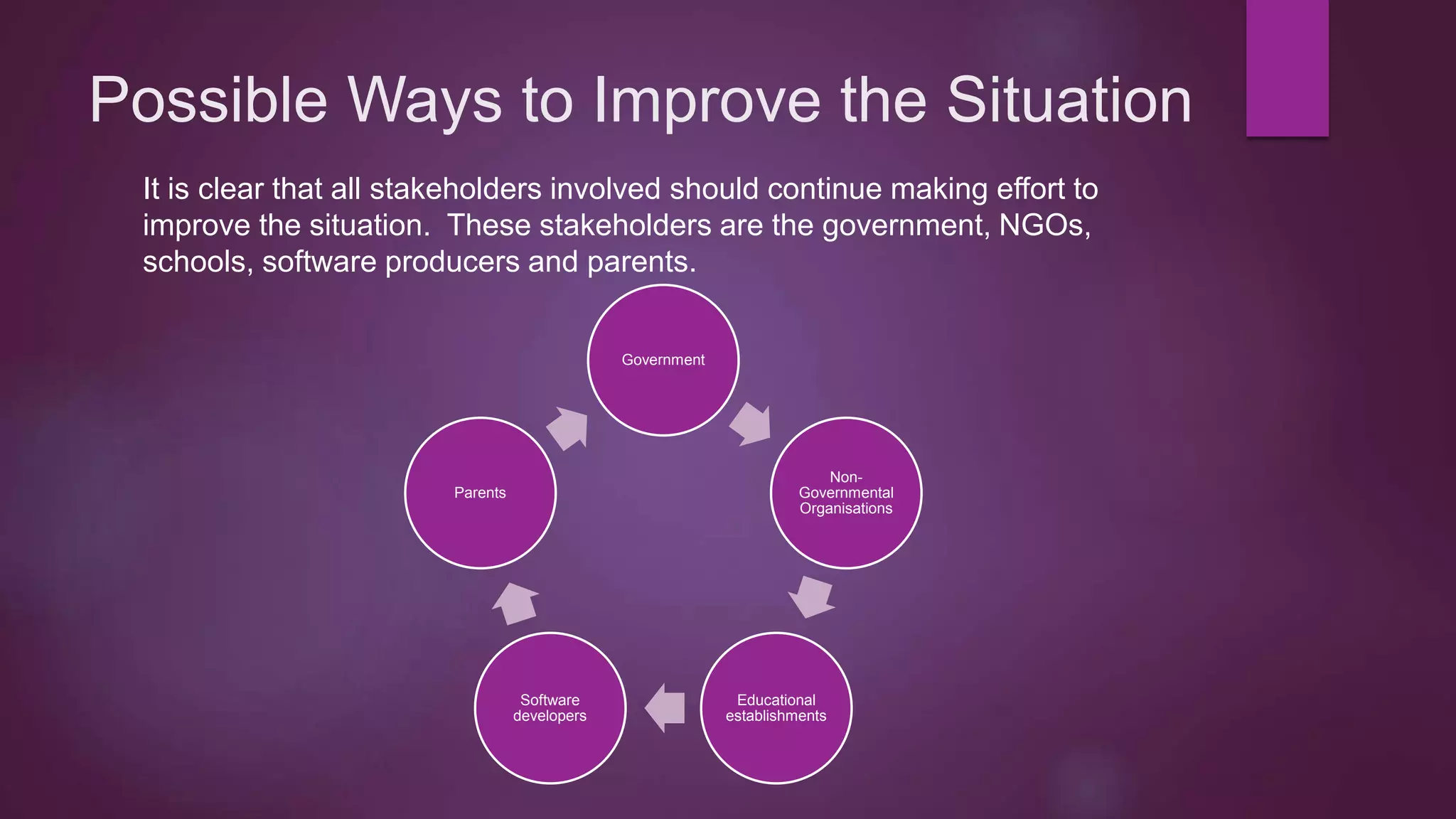
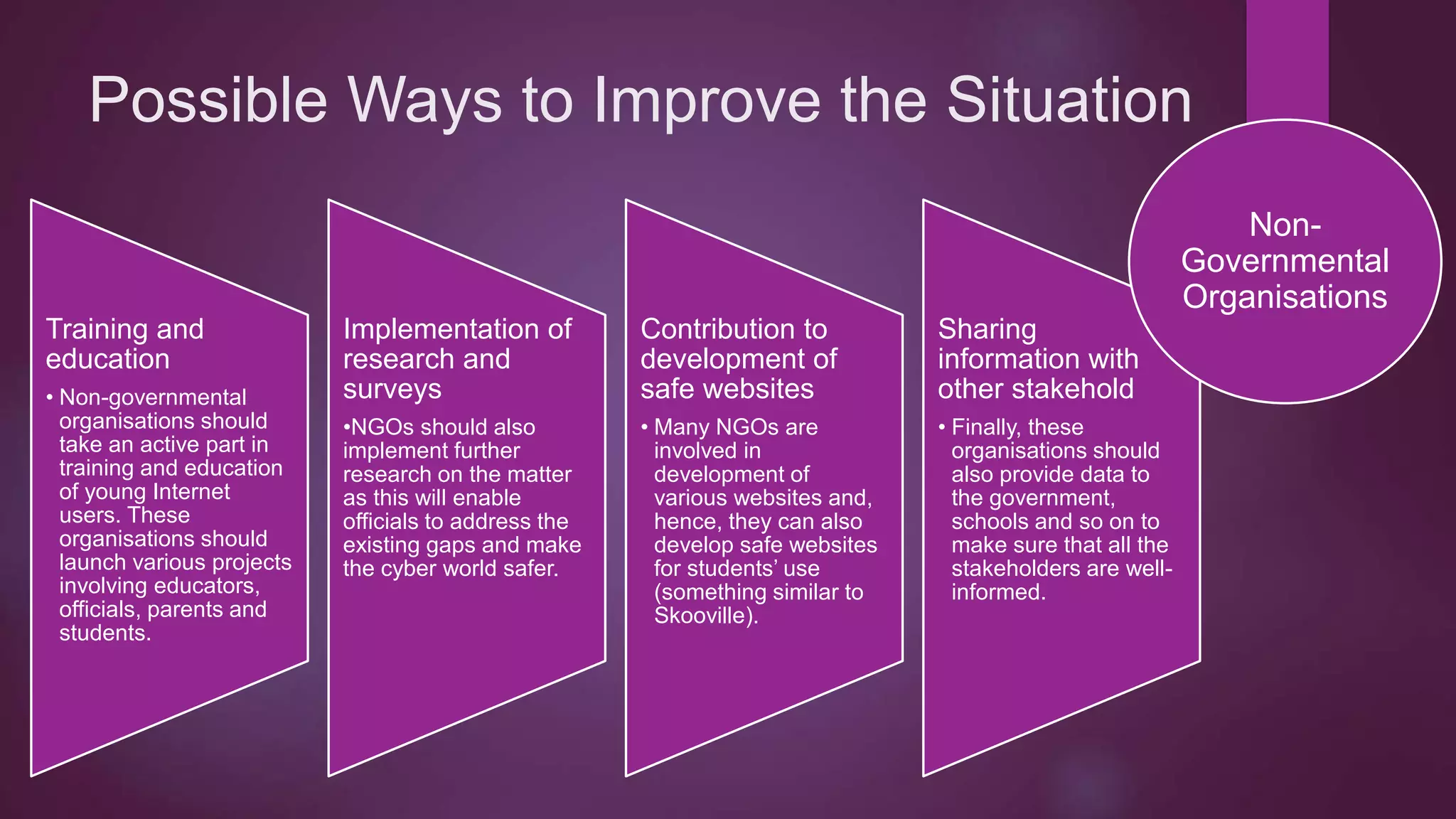
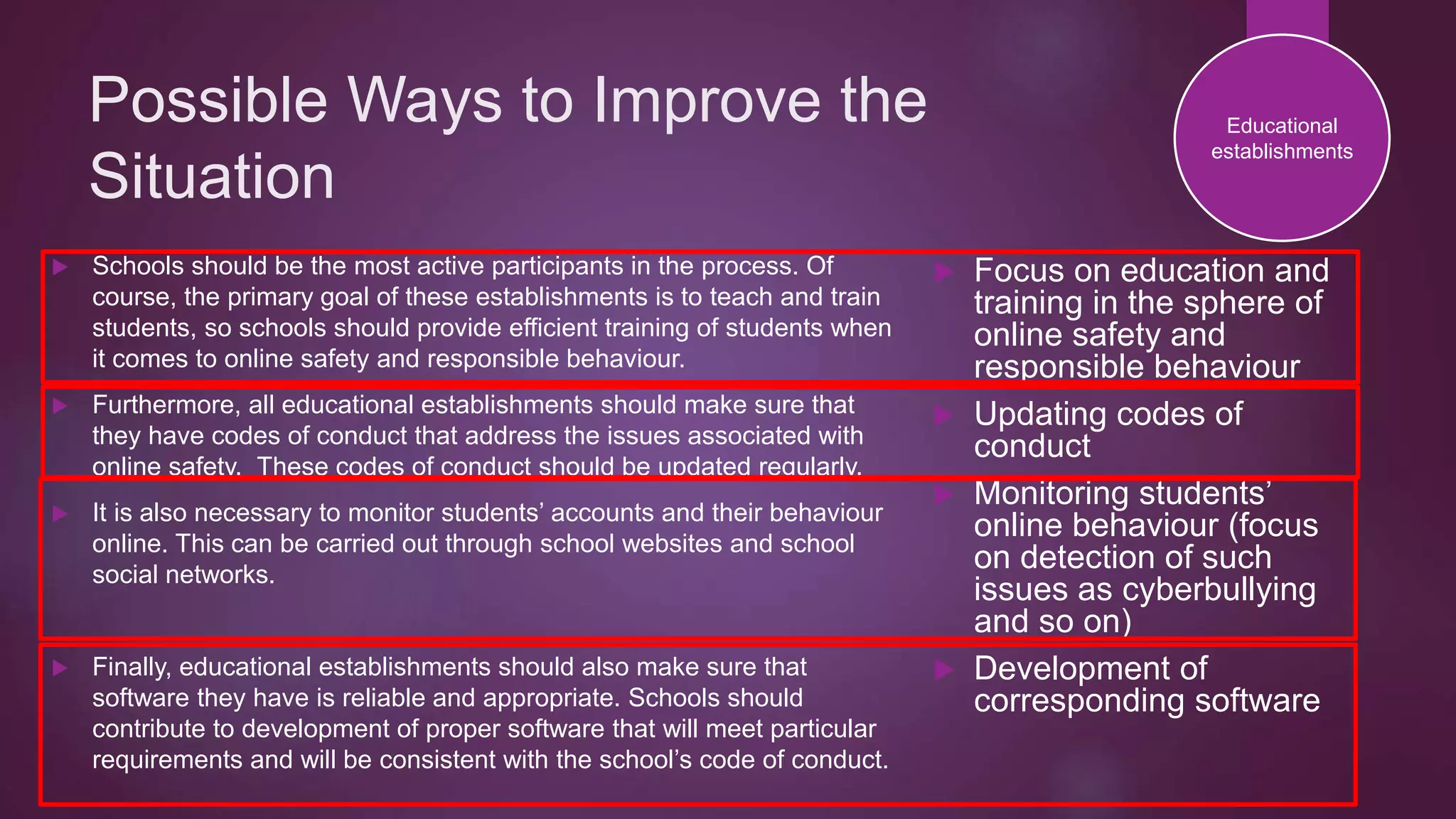
This document discusses protection of students online and existing threats and solutions. It outlines existing threats students face such as spam, fraud, identity theft, and cyberbullying. It also discusses existing solutions implemented by the Australian government, schools, parents, and websites designed to promote online safety. Potential ways to improve the situation are also suggested, including continued education and awareness efforts and collaboration between stakeholders.