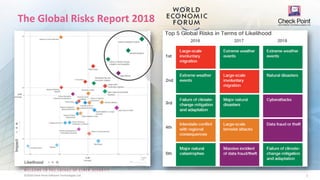
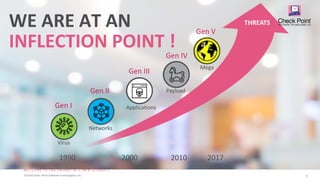
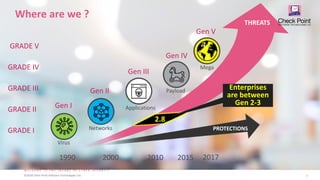
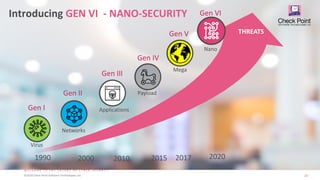
1. The document discusses the evolution of cyber attacks and protections from generations 1 through 5, and argues that organizations must adopt generation 5 "mega" protections to defend against modern large-scale attacks.
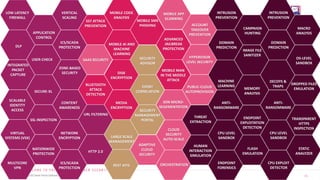
2. It then outlines the many security capabilities needed for a complete generation 5 protection, including things like machine learning, sandboxing, encryption, and mobile/cloud security controls.
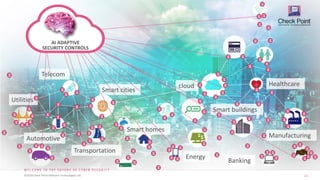
3. Finally, it speculates that with the rise of IoT, generation 6 "nano" attacks may emerge targeting interconnected devices, requiring adaptive AI security controls to prevent attacks at such a granular level.