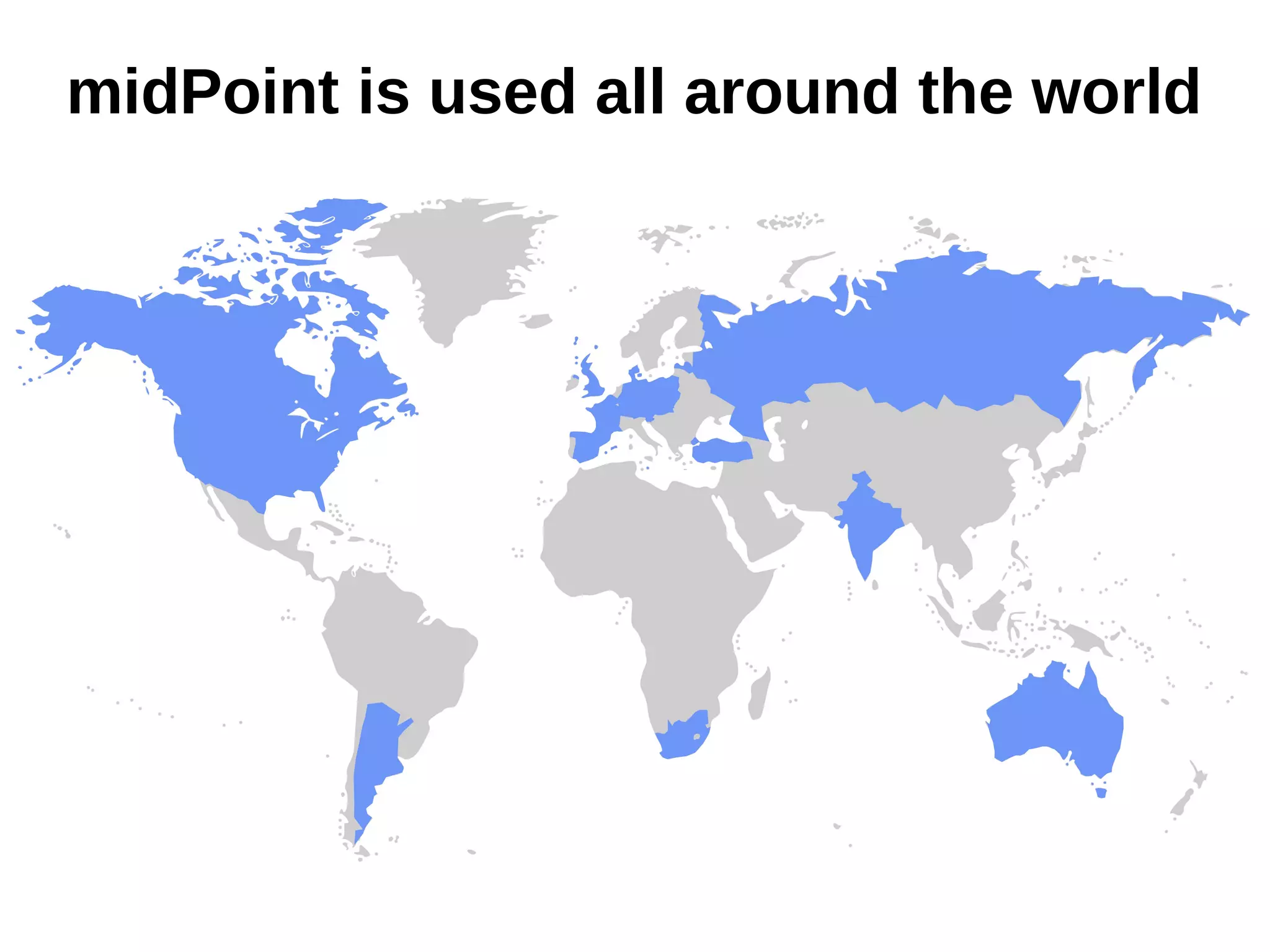
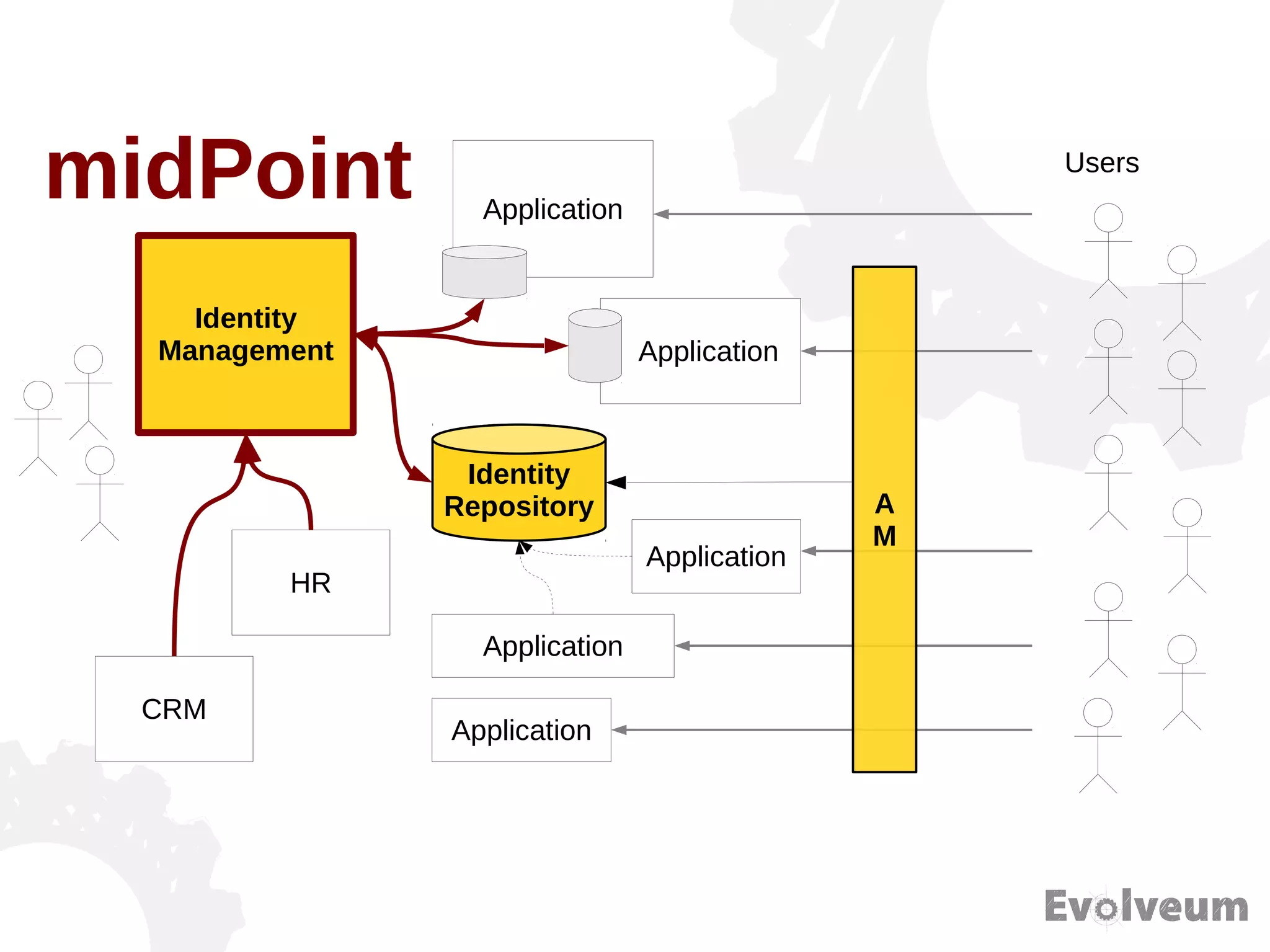
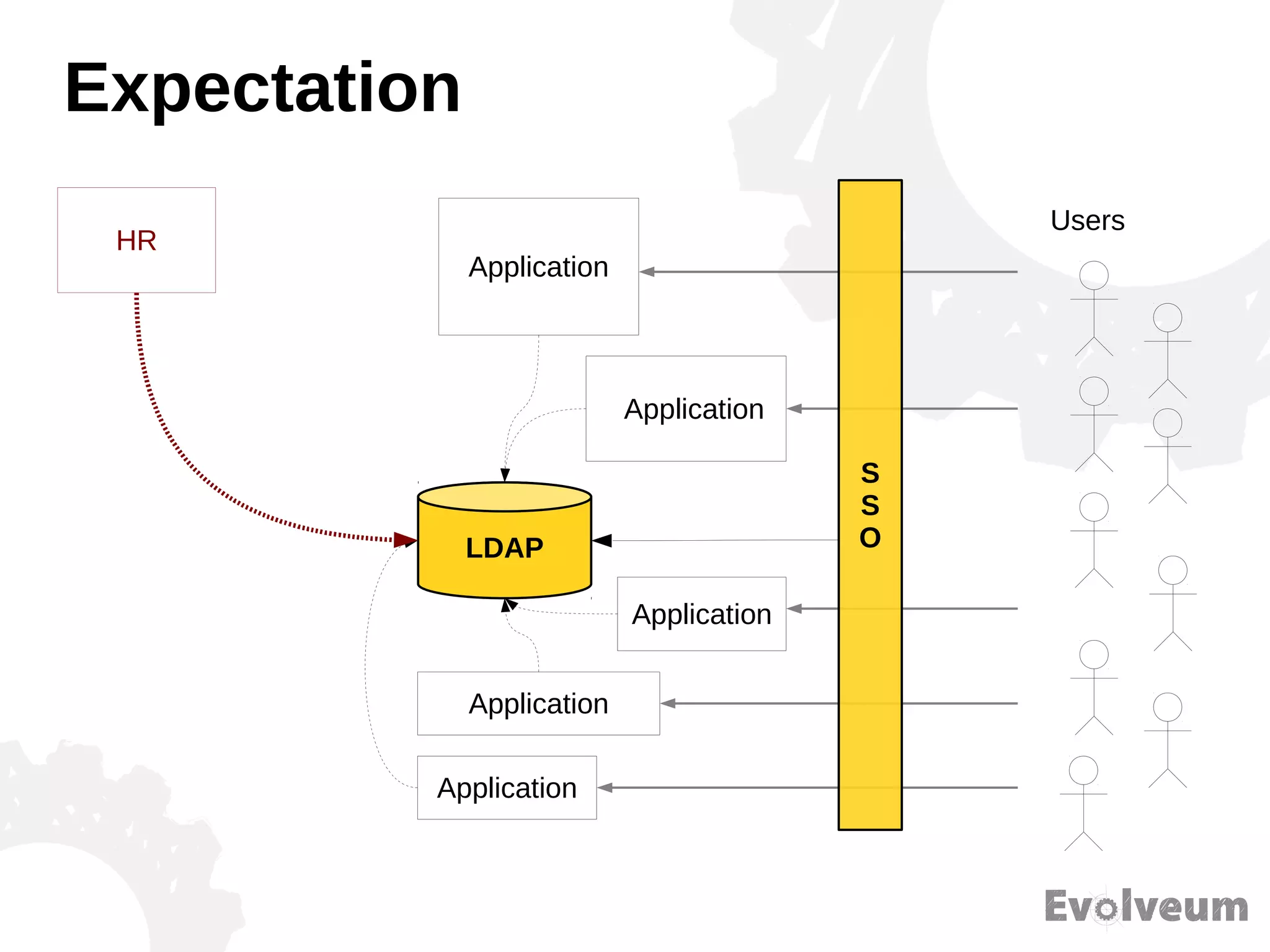
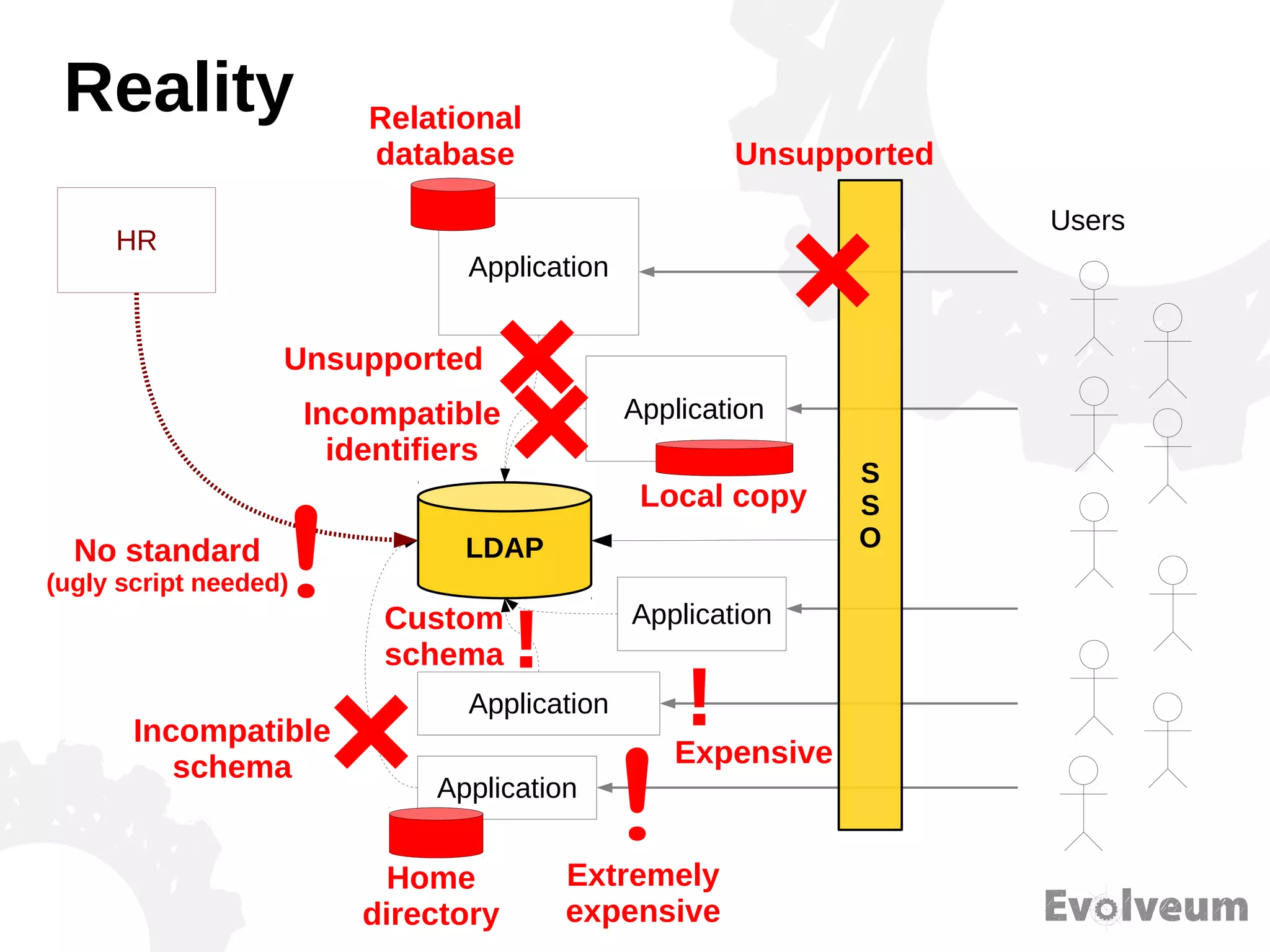
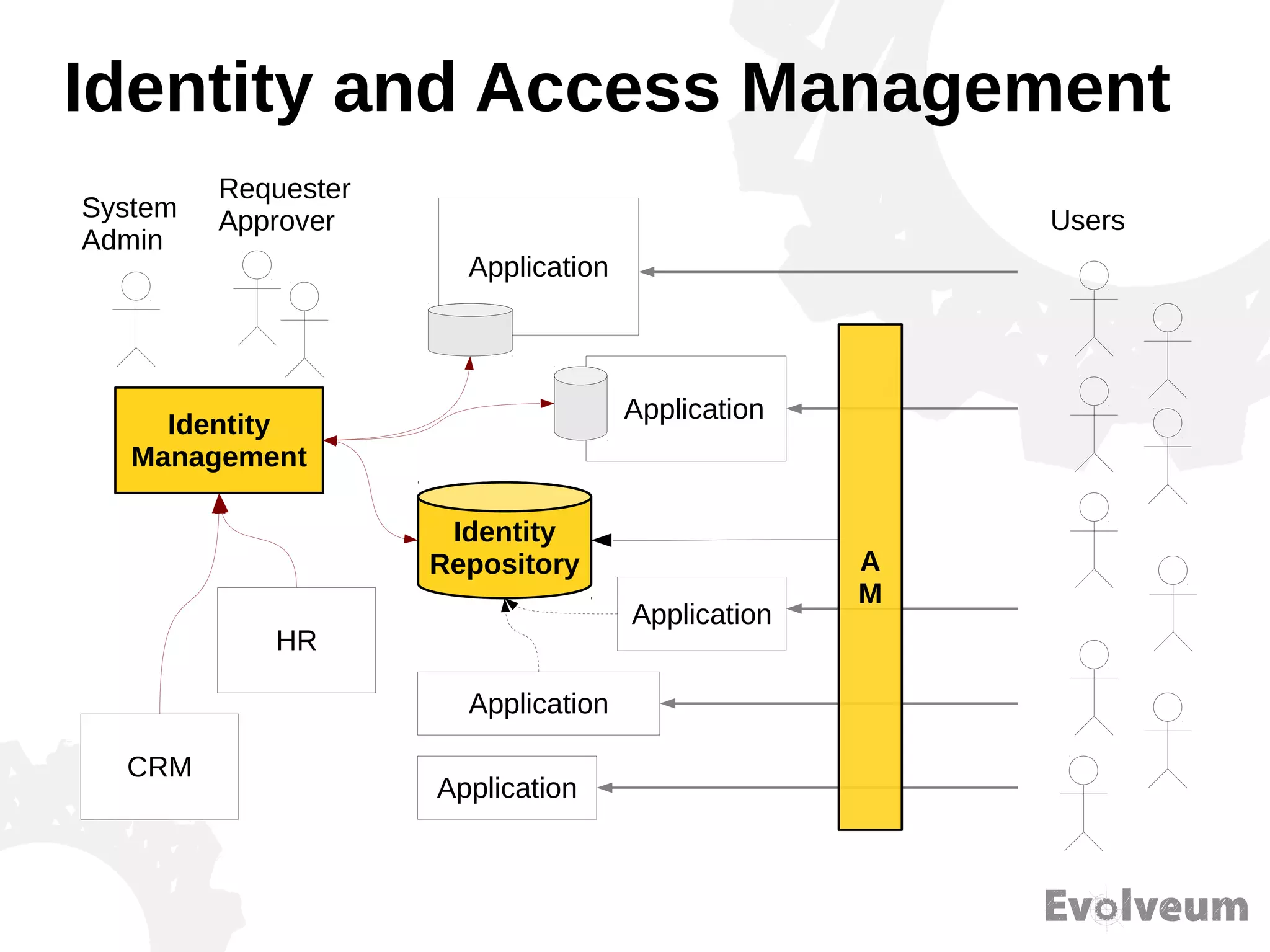
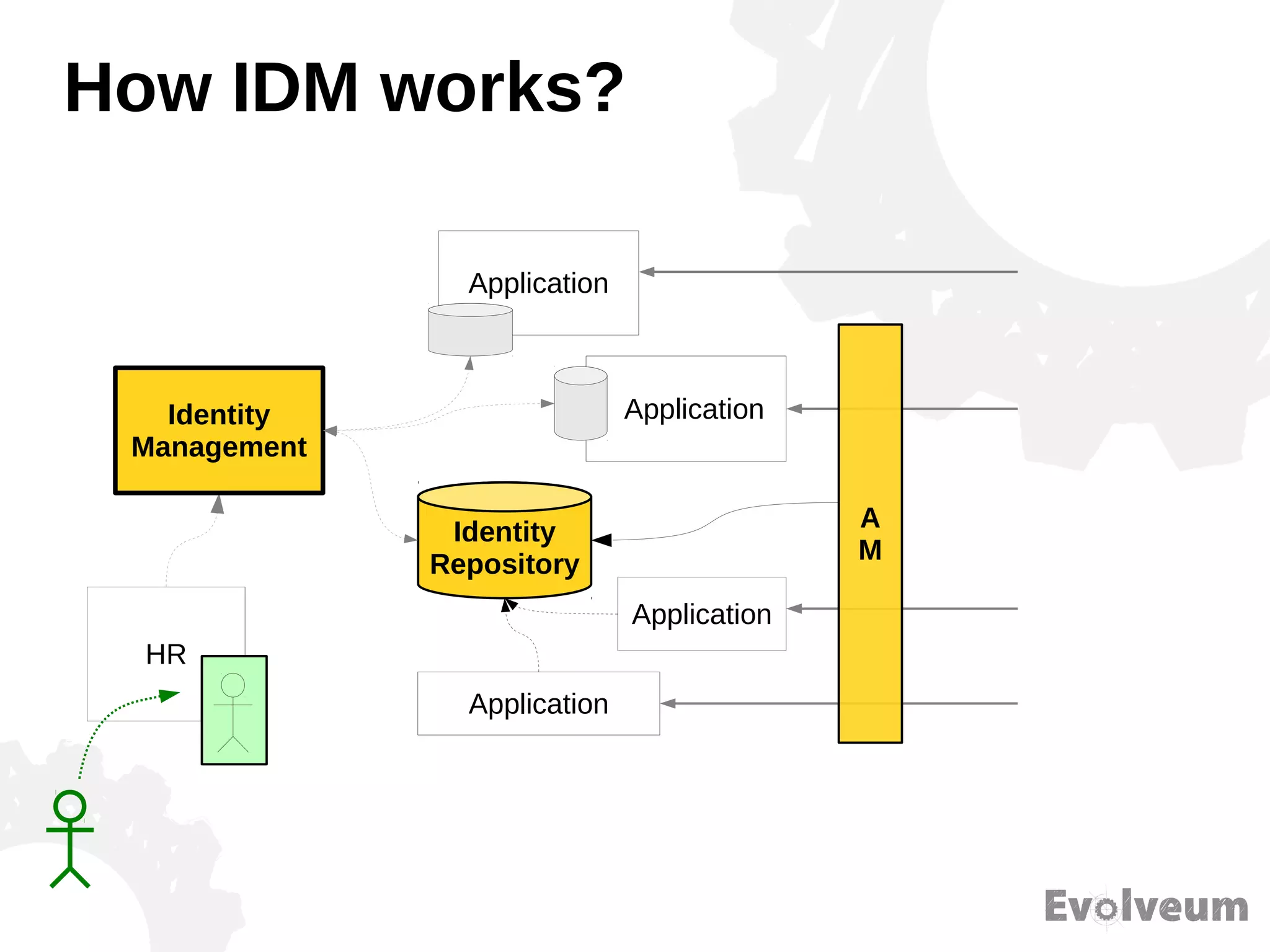
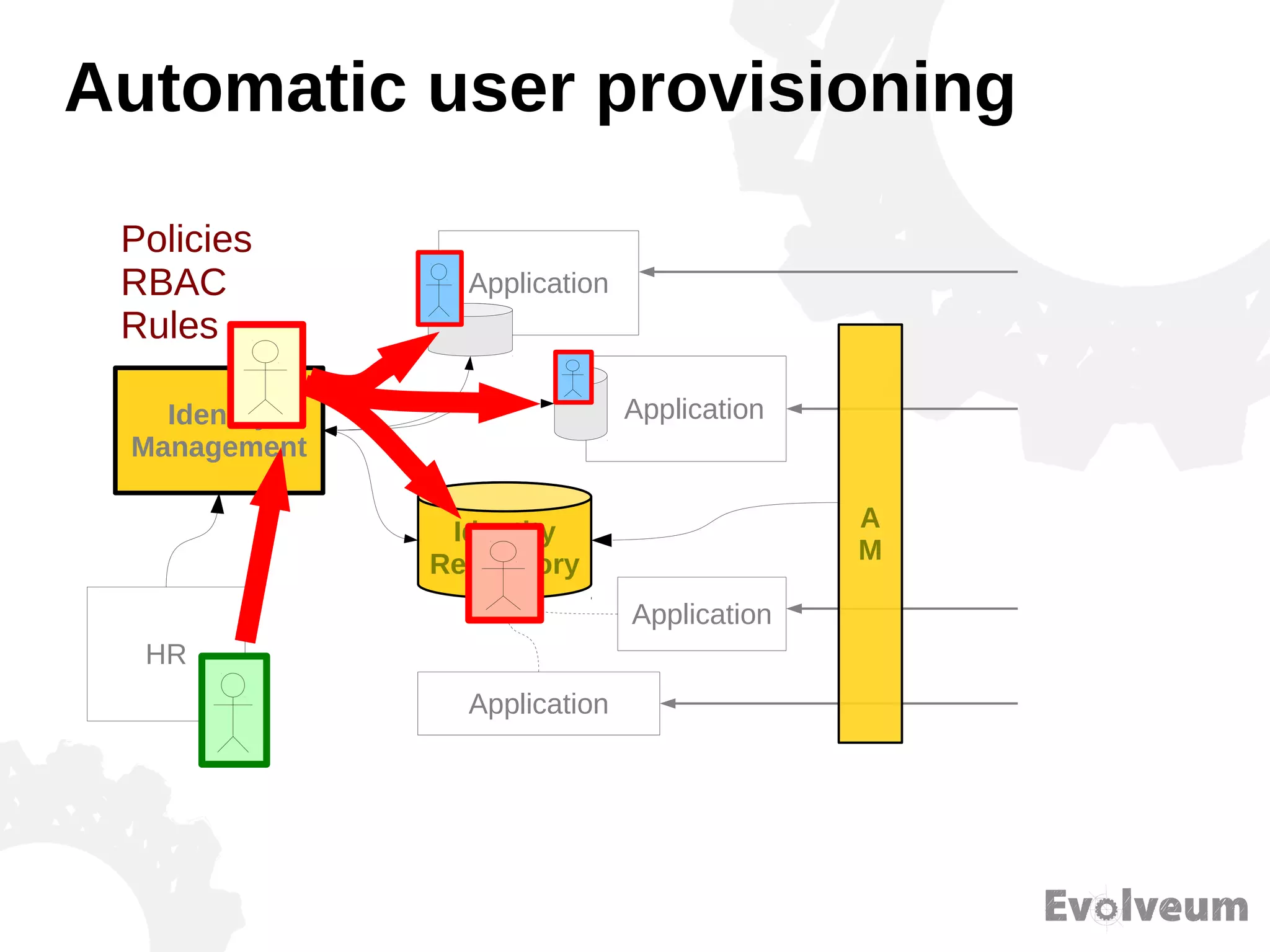
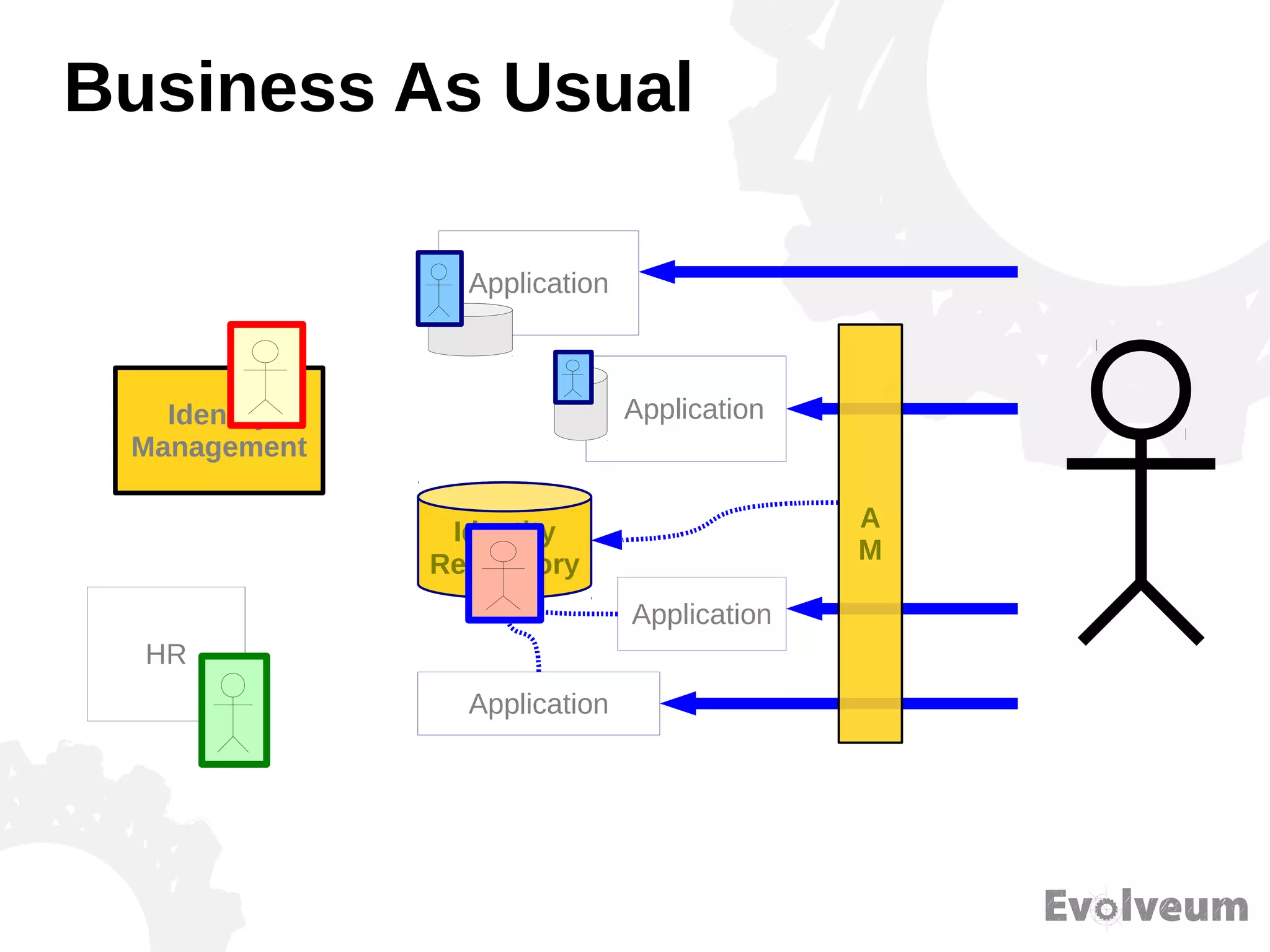
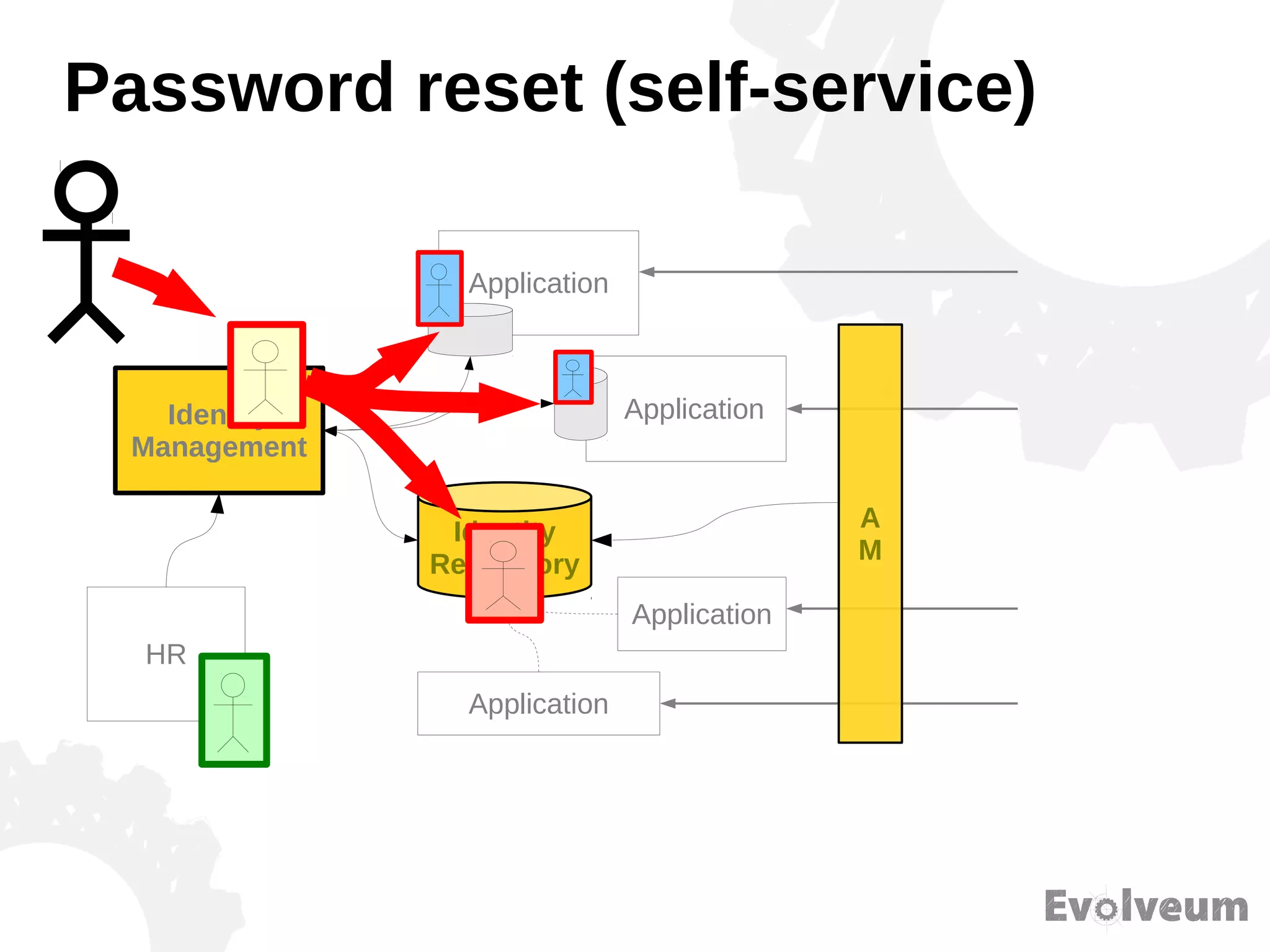
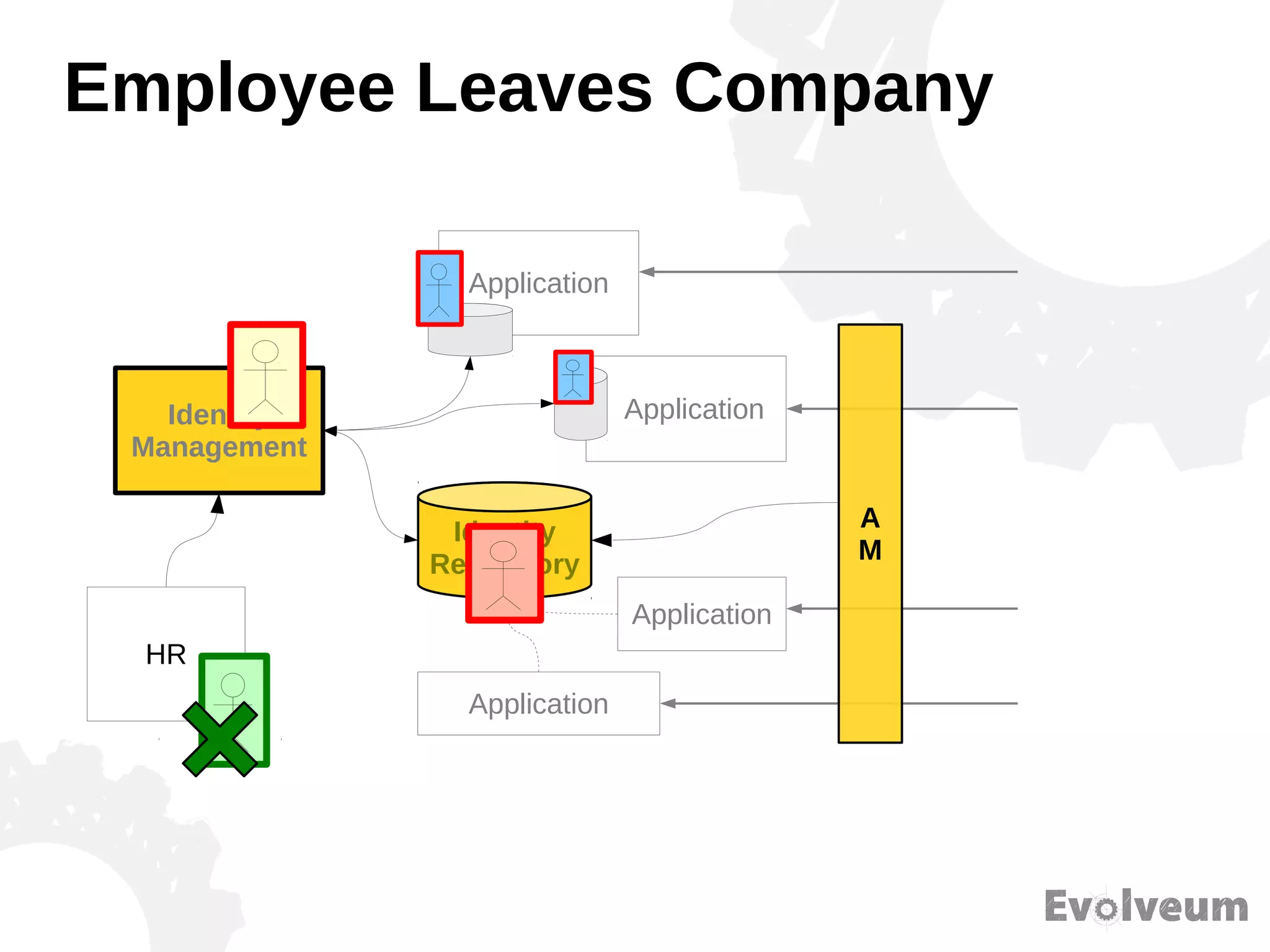
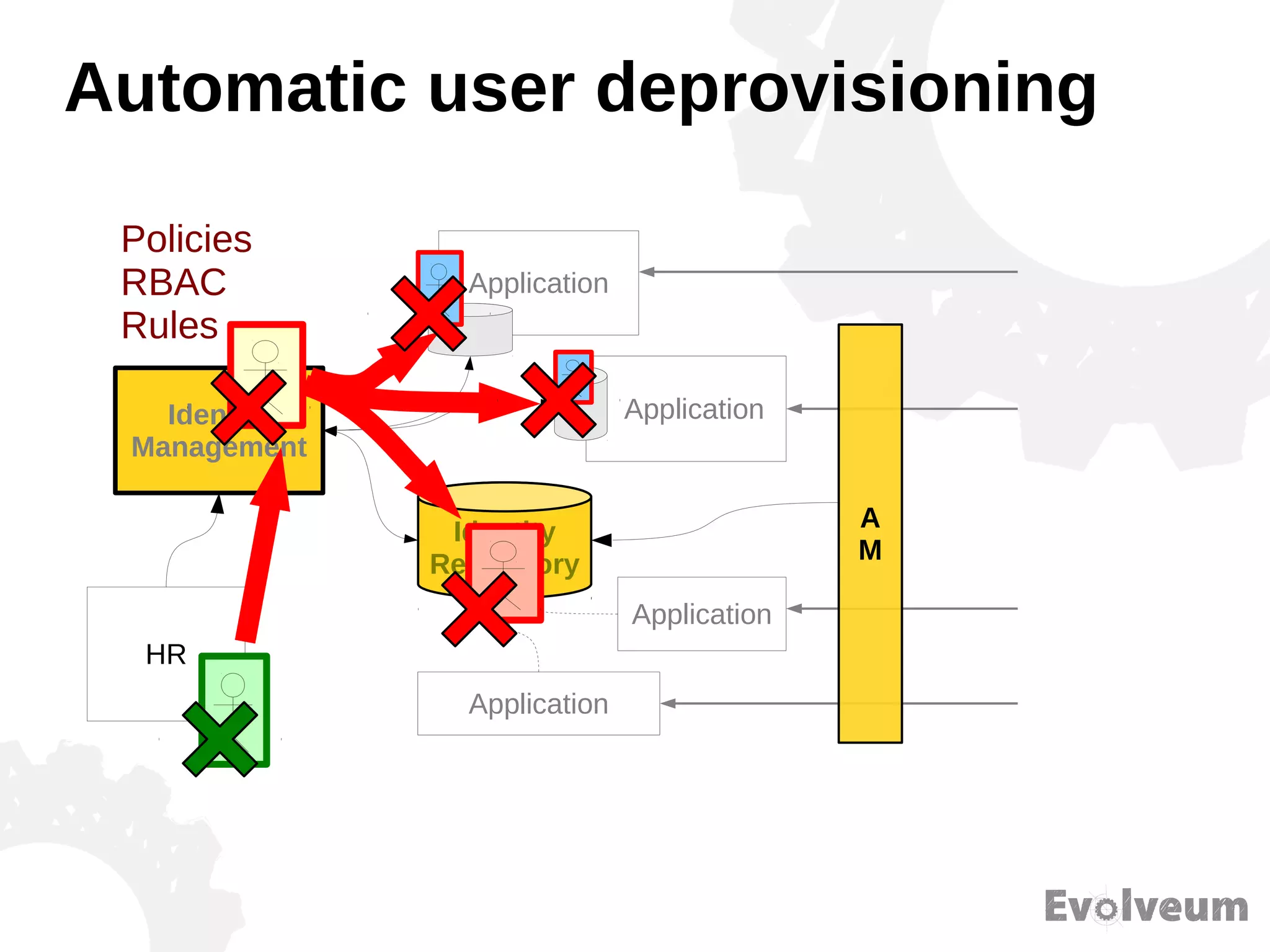
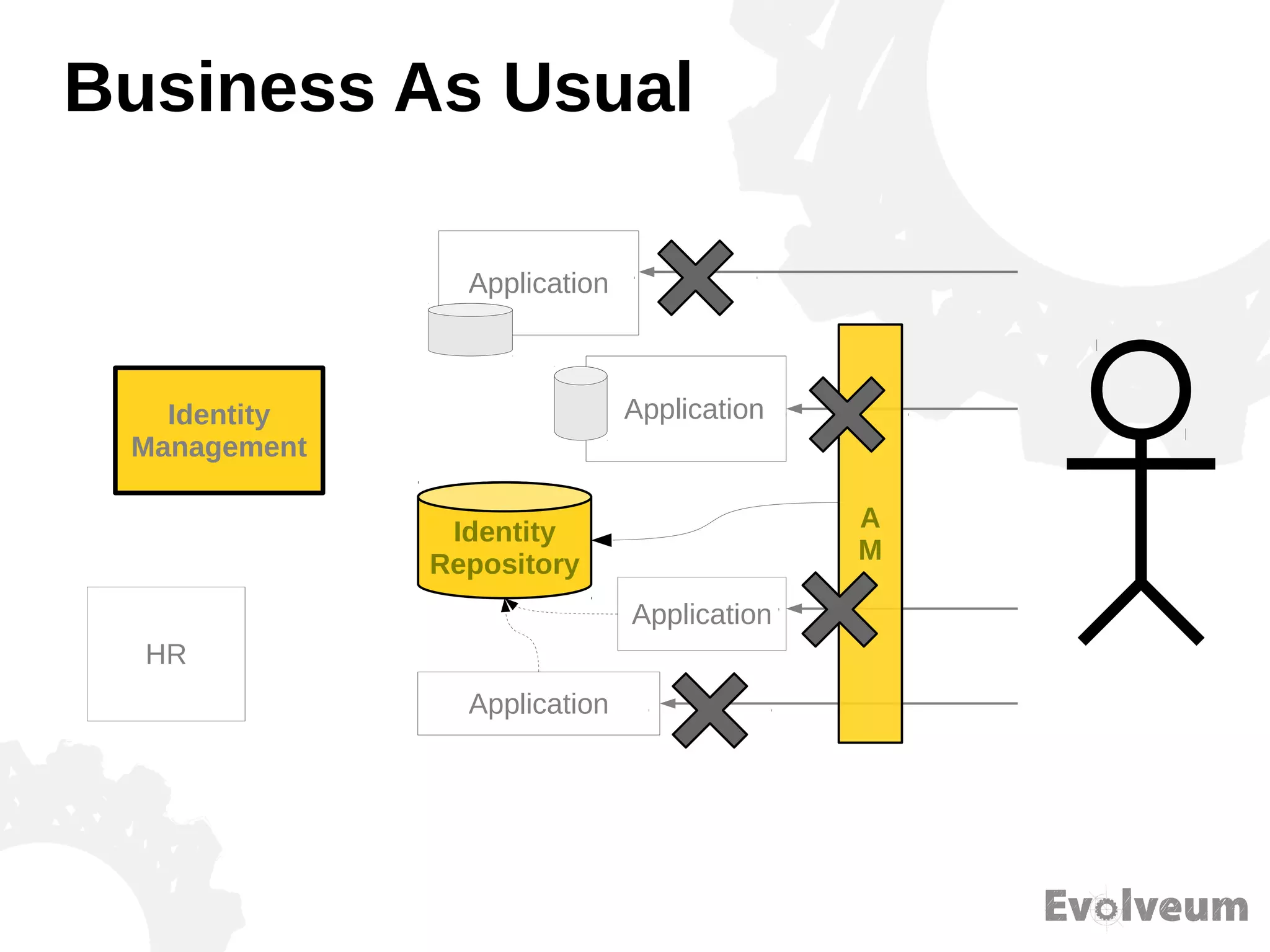
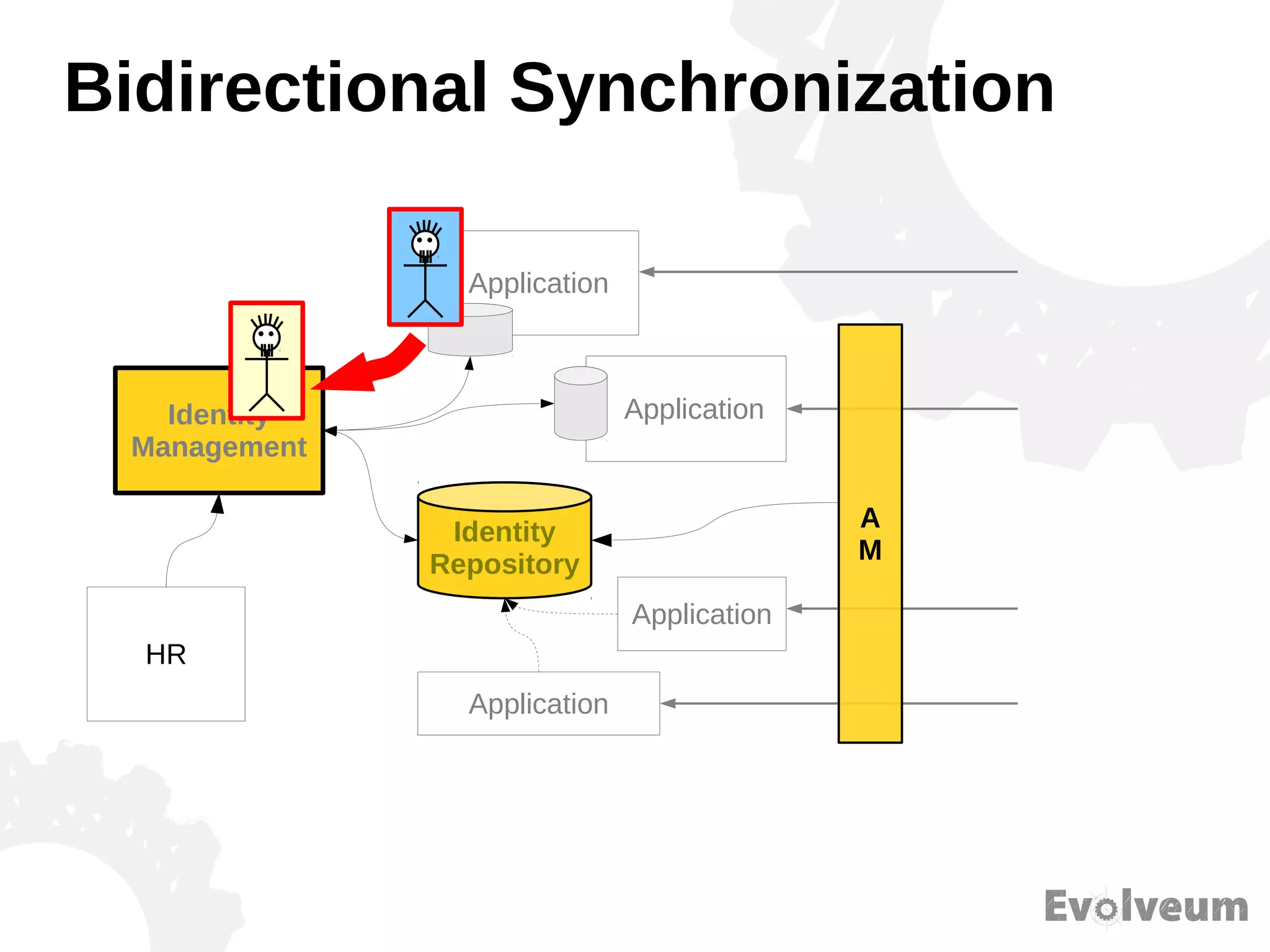
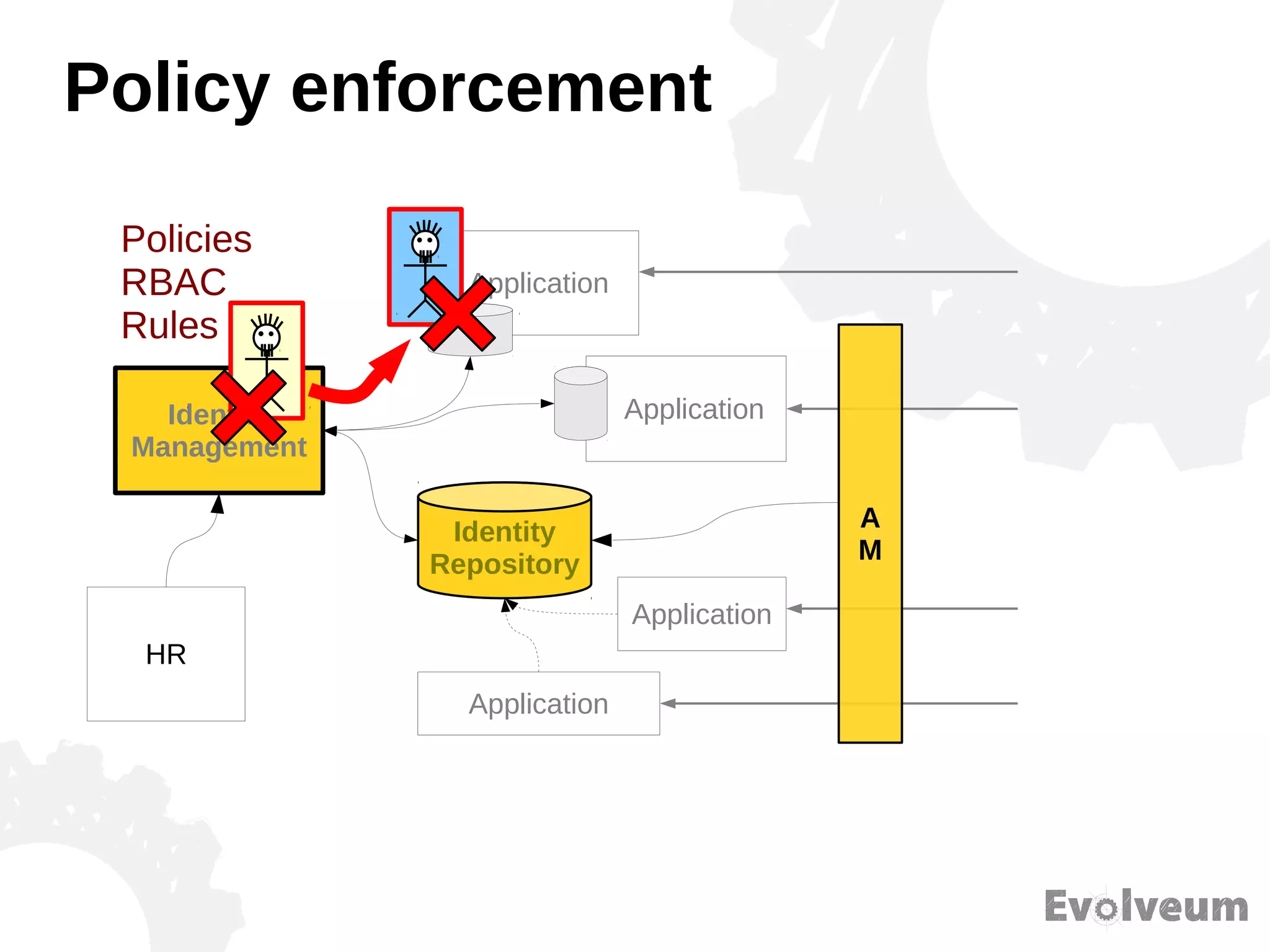
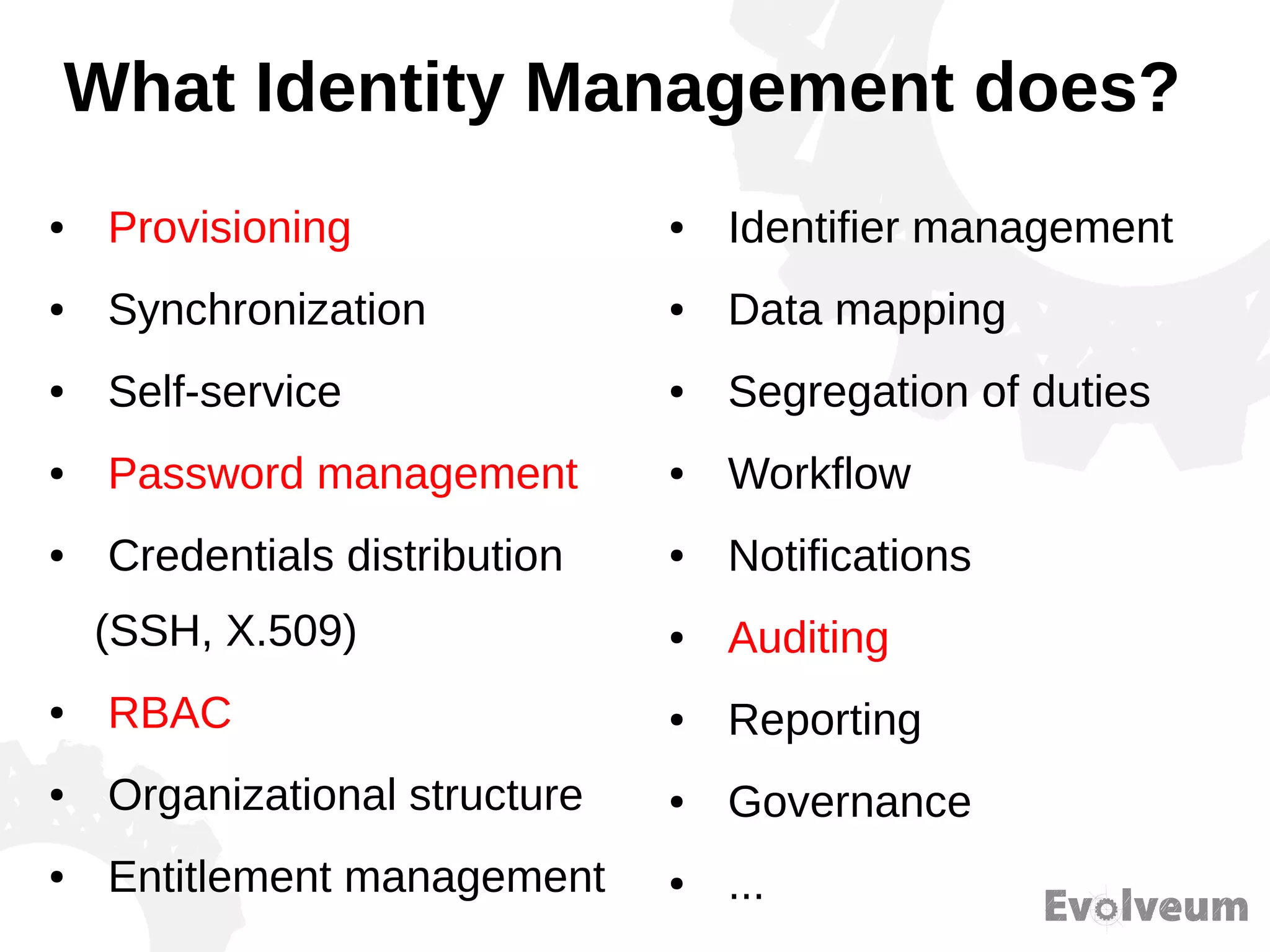
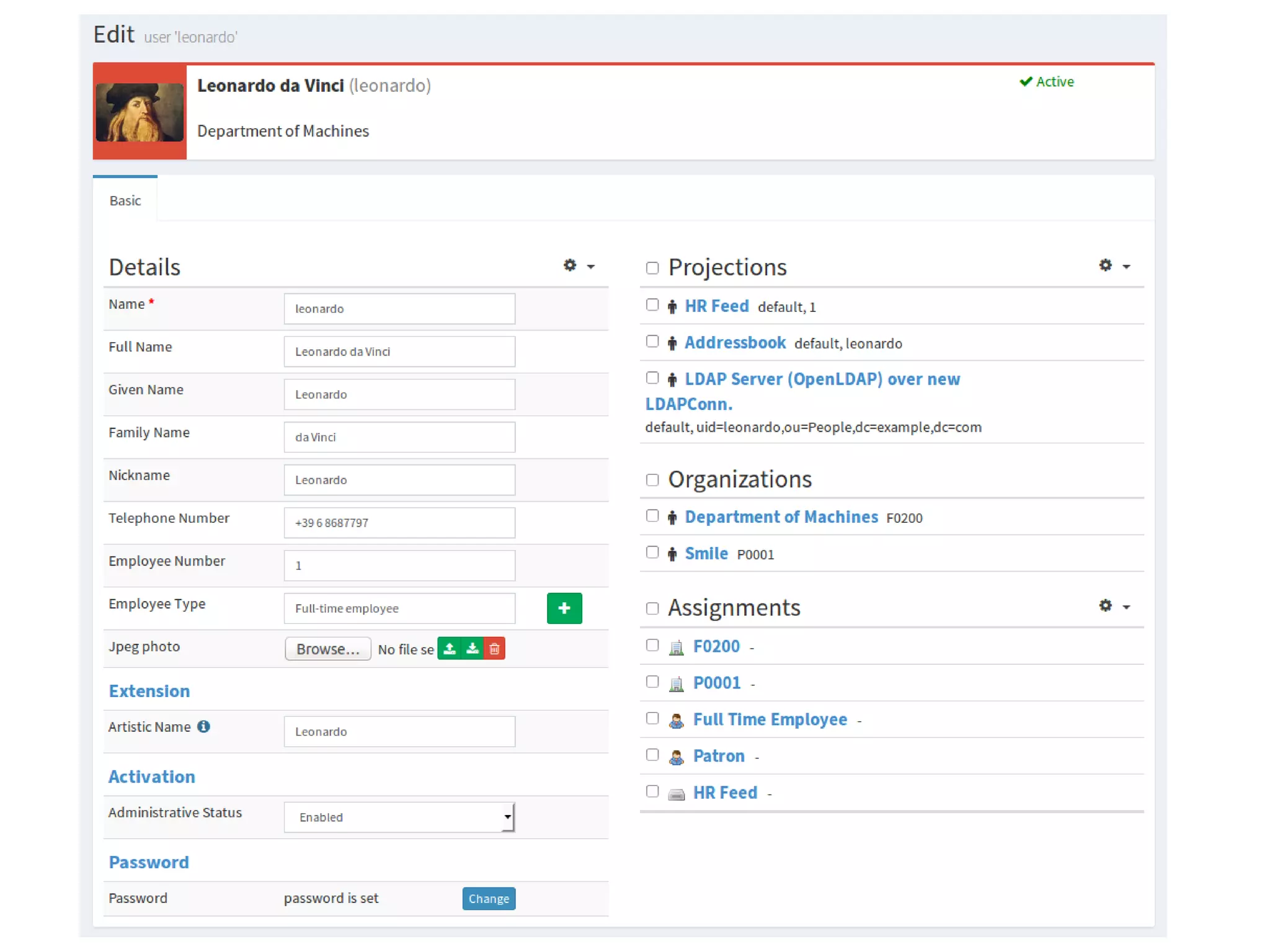
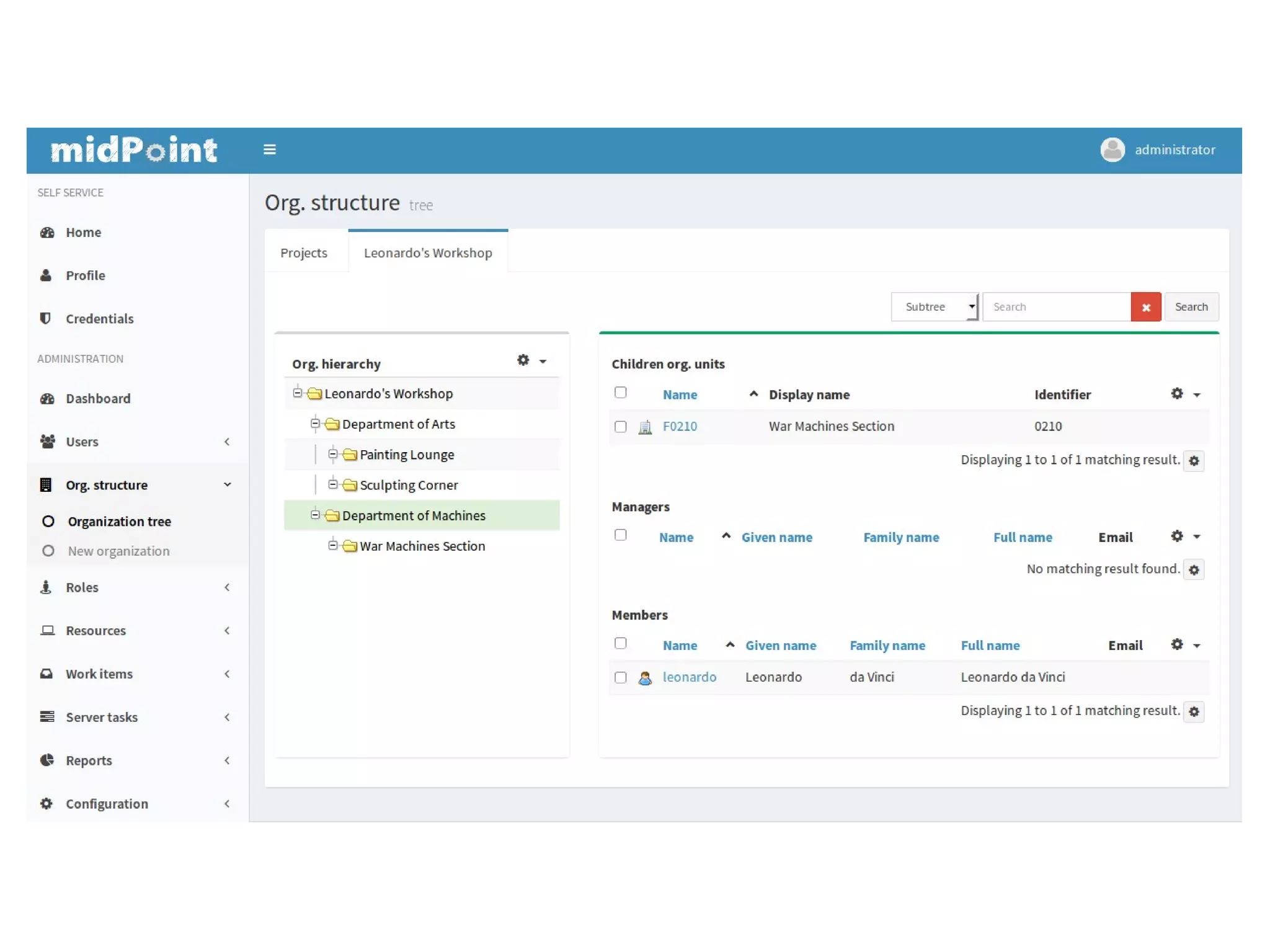
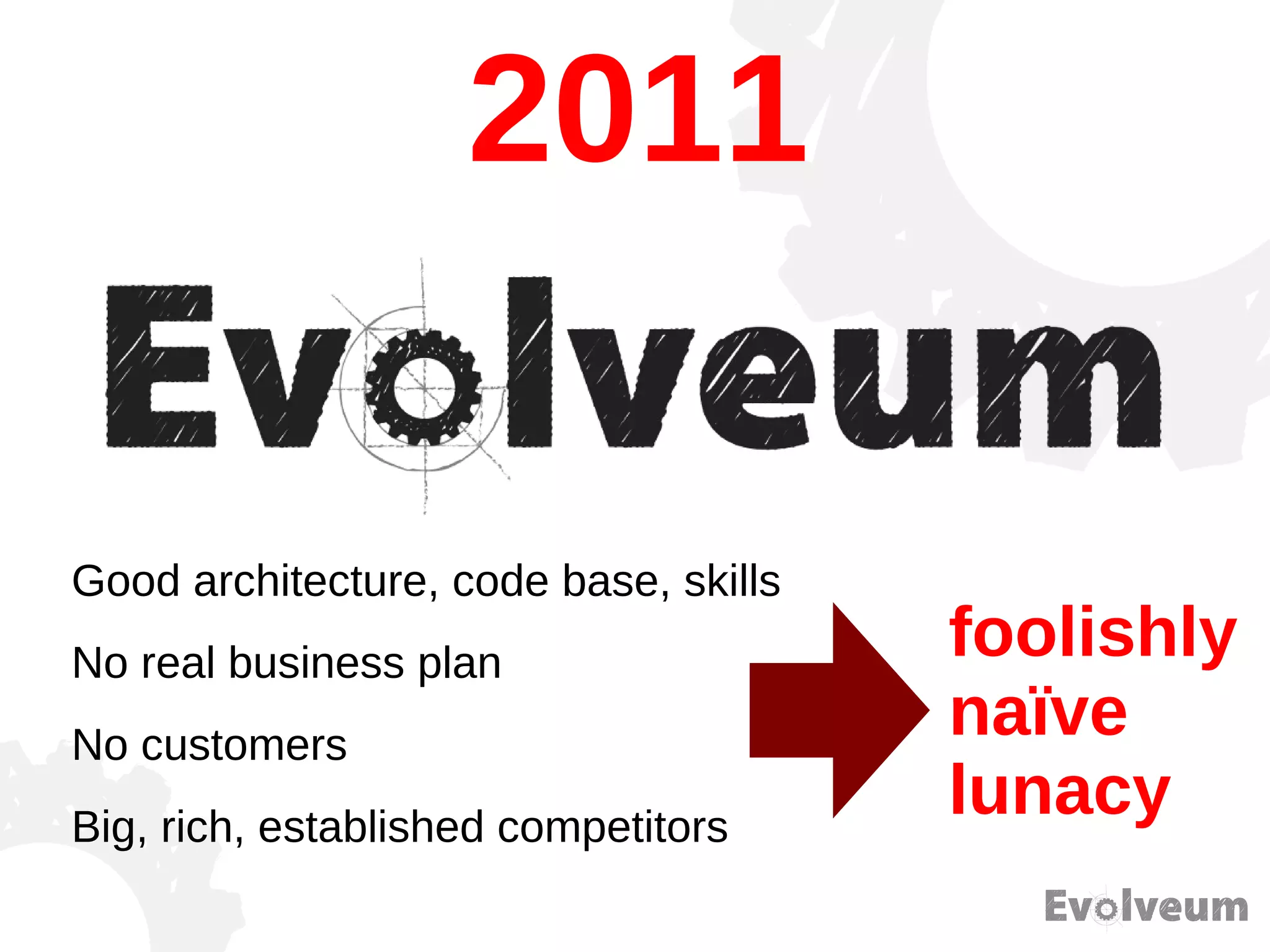
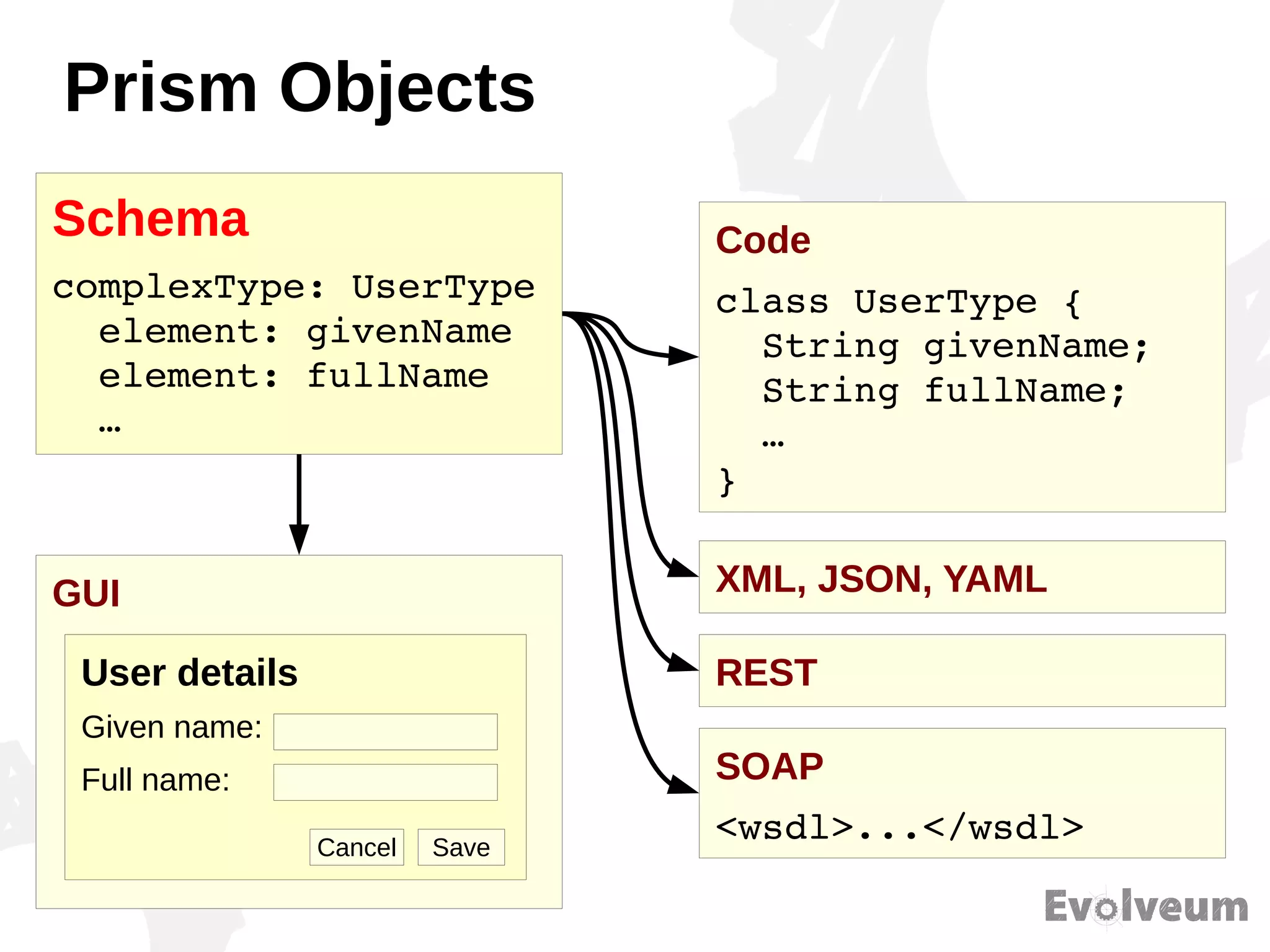
The document discusses the development and features of Midpoint, an open-source identity management product created over five years, which has gained global recognition for its capabilities in provisioning, synchronization, and governance. It highlights the challenges faced by the team in competing against established commercial IDM products and emphasizes the importance of technology, efficiency, and a good architectural foundation for success. Key lessons learned include focusing on a global market and allowing customers to find the product rather than actively seeking them out.