Productivity Found: An Infographic View
•
0 likes•2,932 views
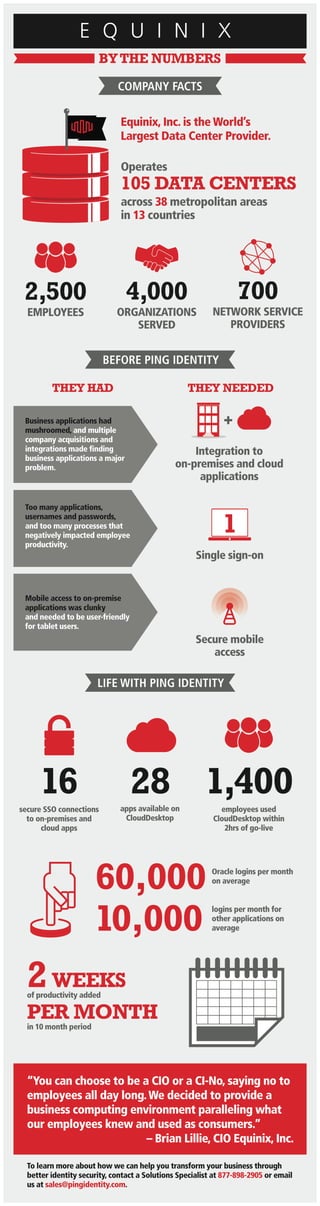
When a company operates 105 data centers that promise the fastest application performance and lowest latency routes worldwide, the simple act of entering a password can seem like a major slow down. Not to mention the implications around security. Here's a look at how Equinix, the world's largest data center provider, cleaned up its internal access controls and recaptured two-weeks of employee productivity per month.
Report
Share
Report
Share
Download to read offline
Recommended
Digital Transformation and the Role of IAM

We surveyed 200 IT decision makers across four countries
to learn where they are in their journey and the role that identity and access management (IAM) plays in the path to digital transformation.
How Aligned Are IT, Employees and Security Practices in Today's Mobile World?

Gartner projects almost 4 in 10 organizations will rely exclusively on BYOD by 2016, and 85 percent of businesses will allow some level of BYOD by 2020. If enterprises want peace of mind with regard to the security of their data and systems, they must understand employee perceptions and practices. Blurred lines between personal and work use impacts security and puts corporate data at risk.
The LinkedIn Guide to the Perfect #WorkSelfie

Your LinkedIn profile is 14x more likely to be viewed simply by adding a profile photo. Follow these tips to take the perfect #WorkSelfie for your LinkedIn profile.
Healthcare Patient Experiences Matter

Join your patient's journey and see critical touch points that impact revenue. These stats prove superb patient experiences move business forward.
Optimize Your Zero Trust Infrastructure

See how you can create seamless and secure experiences for your employees and customers by optimizing and adding intelligence to your Zero Trust infrastructure.
Ping’s Technology Partner Program

Scale your business by partnering with the leading intelligent cloud identity platform and expose your solution to thousands of Ping customers.
Remote Work Fuels Zero Trust Growth

See what Ping’s Executive Survey reveals about the security impacts of the shift to remote work.
Identity Verification: Who’s Really There? 

Customers are knocking on your digital front door, but who’s really there? Get the facts on why identity verification is now more important than ever.
Recommended
Digital Transformation and the Role of IAM

We surveyed 200 IT decision makers across four countries
to learn where they are in their journey and the role that identity and access management (IAM) plays in the path to digital transformation.
How Aligned Are IT, Employees and Security Practices in Today's Mobile World?

Gartner projects almost 4 in 10 organizations will rely exclusively on BYOD by 2016, and 85 percent of businesses will allow some level of BYOD by 2020. If enterprises want peace of mind with regard to the security of their data and systems, they must understand employee perceptions and practices. Blurred lines between personal and work use impacts security and puts corporate data at risk.
The LinkedIn Guide to the Perfect #WorkSelfie

Your LinkedIn profile is 14x more likely to be viewed simply by adding a profile photo. Follow these tips to take the perfect #WorkSelfie for your LinkedIn profile.
Healthcare Patient Experiences Matter

Join your patient's journey and see critical touch points that impact revenue. These stats prove superb patient experiences move business forward.
Optimize Your Zero Trust Infrastructure

See how you can create seamless and secure experiences for your employees and customers by optimizing and adding intelligence to your Zero Trust infrastructure.
Ping’s Technology Partner Program

Scale your business by partnering with the leading intelligent cloud identity platform and expose your solution to thousands of Ping customers.
Remote Work Fuels Zero Trust Growth

See what Ping’s Executive Survey reveals about the security impacts of the shift to remote work.
Identity Verification: Who’s Really There? 

Customers are knocking on your digital front door, but who’s really there? Get the facts on why identity verification is now more important than ever.
Extraordinary Financial Customer Experiences

Join your financial customer’s journey and see critical touchpoints that impact revenue. These stats prove superb customer experiences move business forward.
Extraordinary Retail Customer Experiences

Join your retail customer’s journey and see critical touchpoints that impact revenue. These stats prove superb customer experiences move business forward.
Security Practices: The Generational Gap | Infographic

Ping Identity’s 2019 survey reveals that consumers of different ages have different responses to the rampant data misuse and data breaches that have become increasingly regular in today’s world. Check out the infographic to see how the generations differ in their security practices and trusting tendencies.
Security Concerns Around the World | Infographic

Ping Identity’s 2019 consumer survey reveals interesting insights about where residents of the U.S., Australia, France and Germany differ from one another in their cybersecurity concerns and behavioral trends. Check out the infographic to see which country’s respondents are most concerned about surveillance, which are least likely to sign-on to their accounts through a third-party service and more.
Hybrid IAM: Fuelling Agility in the Cloud Transformation Journey | Gartner IA...

Presenter: Loren Russon, VP Product Management at Ping Identity.
As your organisation evolves on its cloud transformation journey, your identity and access management (IAM) system must allow you to navigate multiple cloud environments, managing access to mobile, API and traditional applications. Modern identity services like multi-factor authentication (MFA) and identity intelligence help deliver secure and seamless access for any user, environment and use case. Learn how to transform your IAM system to a modern, API and cloud-first hybrid solution, enabling developers, administrators and users with the self-service applications and tools they need to keep pace with the accelerating demand for mobile and cloud-based applications.
LES ATTITUDES DES CONSOMMATEURS À L’ÈRE DES CYBERATTAQUES

Les consommateurs présents aux Etats-Unis, en France, en Allemagne et au Royaume-Uni montrent des préférences de sécurité et des comportements différents. Notre étude récente révèle comment chaque pays se démarque des autres.
WIE TICKEN VERBRAUCHER IM ZEITALTER DER DATENSCHUTZVERLETZUNGEN?

Wenn es um Themen wie Sicherheitsempfinden und Sicherheitspraktiken geht, haben die jüngere und die ältere Generation schon mal recht unterschiedliche Ansichten. So stellte eine aktuelle Verbraucherumfrage Abweichungen z. B. beim Markenvertrauen, bei der Bereitschaft, in Datenschutz zu investieren und bei der Akzeptanz biometrischer Sicherheitslösungen fest.
Consumer Attitudes in a Post-breach Era: The Geographical Gap

Ping Identity’s consumer survey on security perceptions and behavior revealed significant differences between residents of the U.S., France, Germany and the UK. Some are more carefree with their information, while others have less trust in brands.
Standard Based API Security, Access Control and AI Based Attack - API Days Pa...

As APIs continue to drive digital transformation efforts in the enterprise and support innovative customer experiences, securing them has never been more important.
Principal Regional Solution Architect, Philippe Dubuc introduces how to leverage OpenID Connect, OAuth2 and new emerging standards to protect APIs at API Days Paris on 11 December, 2018. In addition, Philippe goes over how the Intelligent Ping Identity Platform can be used to protect APIs in a pro-active way and how AI can help to protect against attacks.
Learn more: http://ow.ly/2Ojm30n1rCT
ATTITUDES DES CONSOMMATEURS A L’ERE DES PIRATAGES LE CONFLIT DE GENERATIONS

Concernant les attitudes et les pratiques en matière de sécurité, la jeune et l’ancienne génération ne sont pas toujours en phase. Une récente enquête révèle des différences marquées touchant la confiance envers les marques, la volonté de payer pour la protection des données, l’adoption de la biométrie, etc.
2018 Survey: Consumer Attitudes in a Post-Breach Era - The Generational Gap

Consumers under 35 and over 55 have significant differences in the way they think about security, willingness to share personal information, investment in data protection and use of technology like biometrics. Check out the infographic to see where Ping Identity’s survey revealed the biggest differences.
WIE TICKEN VERBRAUCHER IM ZEITALTER DER DATENSCHUTZVERLETZUNGEN? ALLES EINE F...

Wenn es um Themen wie Sicherheitsempfinden und Sicherheitspraktiken geht, haben die jüngere und die ältere Generation schon mal recht unterschiedliche Ansichten. So stellte eine aktuelle Verbraucherumfrage Abweichungen z. B. beim Markenvertrauen, bei der Bereitschaft, in Datenschutz zu investieren und bei der Akzeptanz biometrischer Sicherheitslösungen fest.
API Security Needs AI Now More Than Ever

API security is increasingly difficult for enterprise security teams to tackle. APIs are spreading fast and a tempting target for cyberattacks. Learn about the challenges overwhelming security teams today that can be overcome with an intelligent API security solution. Learn more: http://ow.ly/FEtG30lNsHm
Fishing for a CIAM Platform? 11 Question to Ask Before You Buy

On the hook to select a customer IAM platform? Be sure to ask these 11 questions before you settle on a solution. Or you could get in too deep. Read the infographic to discover why enlisting IT’s help early in the selection process will ensure your CIAM platform is watertight.
Criteria for Effective Modern IAM Strategies (Gartner IAM 2018)

Presenter: Loren Russon, Ping Identity VP of Products Management and Design.
Managing digital identities and access control for users, applications and things remains one of the greatest challenges facing cloud computing today. This has led to a new cloud security service paradigm that requires your organization to reevaluate the criteria for designing and implementing identity and access management (IAM) services across data centers, and private and public cloud infrastructure. This new criteria addresses the continued transformation to the cloud, mobile and internet of things (IoT), and the increased demand for open business balanced by user data security found in initiatives such as GDPR, Open Banking and PSD2. In this session, you will learn about key requirements and design principles required for modern IAM systems, and how to effectively drive digital transformation, address user data security regulations and ensure you successfully manage your company’s transformation to the cloud.
Webinar: Three Steps to Transform Your Mobile App into a Security Factor

It’s your job to secure customer interactions with your brand. Enabling multi-factor authentication (MFA) for your customers can secure their data, even if their credentials get compromised elsewhere. You may be asking yourself, “doesn’t MFA add friction and detract from their customer experience?”
Join Pamela Dingle, Principal Technical Architect for Ping Identity, as she outlines three easy steps to transform your own mobile application into a second factor that is both secure and convenient. You will learn how to achieve transaction approvals, strong device-based mobile app authentication, and many other use cases from your own mobile app, with minimal impact on your existing authentication infrastructure.
Stay tuned for the webinar replay. To learn more, download the 'Multi-factor Authentication for Customers' white paper: http://www.bit.ly/2tusUA0
Webinar: Deep Diving Into the KuppingerCole IDaaS Leadership Compass 

While enterprises move to the cloud, they are pressured to keep security in mind without hindering user productivity with a cumbersome sign-on process. One solution that delivers both a secure and seamless experience for users with one-click access to SaaS applications is single sign-on (SSO). Many enterprises cannot simply rip and replace, so finding a solution provider that creates a hybrid environment between cloud and existing on-premise infrastructures is vital.
The 2017 KuppingerCole Leadership Compass is the industry leading recourse that deep dives into this market, rating identity-as-a-service (IDaaS) solution providers in areas like SSO cloud services for users including employees, business partners and customers.
Get the report: http://www.ow.ly/Rhht30eLbbD
Join Ping Identity’s Product Marketing Manager, Alex Babar, as he looks at the KuppingerCole Leadership Compass for IDaaS and at the capabilities they consider. He will also review Ping Identity product features focusing on core factors that led KuppingerCole to name Ping a leader in their Leadership Compass, such as outbound federation and single sign-on, authentication support, and access management.
Get the replay: http://bit.ly/2eK0I66
GDPR & Customer IAM: The Real Winners Won’t Stop At Compliance

Listen to the on-demand recorded webinar here: http://bit.ly/2synQpD.
In the recording you will learn how customer identity and access management (Customer IAM) solutions can help you meet GDPR requirements out of the box, while also providing a single, unified customer profile, and enabling secure, seamless and personalized customer experiences across all channels and applications.
Note, this is a recorded webinar which took place on 27 June, 2017. For more information on GDPR and how Ping's leading Customer IAM solution can turn a compliance challenge into an opportunity for your organization, visit www.pingidentity.com/GDPR.
Gartner IAM London 2017 Session - Security, Standards & User Experience: The ...

Ping Identity Principal Technical Architect, Pam Dingle’s slides on how organisations can meet PSD2 and Open Banking Standard requirements while delivering excellent customer experiences in today’s challenging digital business environments. Using software that’s based on the OAuth family of standards, organisations are protecting RESTful APIs, combining a critical blend of intuitive user interactions, highly scalable certification of clients and interoperability.
A Modern Identity Architecture for the Digital Enterprise: http://bit.ly/2lPNiCM
You Can't Spell Enterprise Security without MFA 

Sure, you can spell enterprise security without the letters M-F-A, but the modern digital enterprise isn't as secure without a strong multi-factor authentication (MFA) strategy. Enterprises are under attack, and credentials are a primary target. Many leading enterprises are enhancing their security and control with MFA, allowing them to move away from a high-risk, password-based security approach and to give their employees, partners, and customers a better user experience. View this slide deck for best practices for a MFA strategy.
PHP Frameworks: I want to break free (IPC Berlin 2024)

In this presentation, we examine the challenges and limitations of relying too heavily on PHP frameworks in web development. We discuss the history of PHP and its frameworks to understand how this dependence has evolved. The focus will be on providing concrete tips and strategies to reduce reliance on these frameworks, based on real-world examples and practical considerations. The goal is to equip developers with the skills and knowledge to create more flexible and future-proof web applications. We'll explore the importance of maintaining autonomy in a rapidly changing tech landscape and how to make informed decisions in PHP development.
This talk is aimed at encouraging a more independent approach to using PHP frameworks, moving towards a more flexible and future-proof approach to PHP development.
State of ICS and IoT Cyber Threat Landscape Report 2024 preview

The IoT and OT threat landscape report has been prepared by the Threat Research Team at Sectrio using data from Sectrio, cyber threat intelligence farming facilities spread across over 85 cities around the world. In addition, Sectrio also runs AI-based advanced threat and payload engagement facilities that serve as sinks to attract and engage sophisticated threat actors, and newer malware including new variants and latent threats that are at an earlier stage of development.
The latest edition of the OT/ICS and IoT security Threat Landscape Report 2024 also covers:
State of global ICS asset and network exposure
Sectoral targets and attacks as well as the cost of ransom
Global APT activity, AI usage, actor and tactic profiles, and implications
Rise in volumes of AI-powered cyberattacks
Major cyber events in 2024
Malware and malicious payload trends
Cyberattack types and targets
Vulnerability exploit attempts on CVEs
Attacks on counties – USA
Expansion of bot farms – how, where, and why
In-depth analysis of the cyber threat landscape across North America, South America, Europe, APAC, and the Middle East
Why are attacks on smart factories rising?
Cyber risk predictions
Axis of attacks – Europe
Systemic attacks in the Middle East
Download the full report from here:
https://sectrio.com/resources/ot-threat-landscape-reports/sectrio-releases-ot-ics-and-iot-security-threat-landscape-report-2024/
More Related Content
More from Ping Identity
Extraordinary Financial Customer Experiences

Join your financial customer’s journey and see critical touchpoints that impact revenue. These stats prove superb customer experiences move business forward.
Extraordinary Retail Customer Experiences

Join your retail customer’s journey and see critical touchpoints that impact revenue. These stats prove superb customer experiences move business forward.
Security Practices: The Generational Gap | Infographic

Ping Identity’s 2019 survey reveals that consumers of different ages have different responses to the rampant data misuse and data breaches that have become increasingly regular in today’s world. Check out the infographic to see how the generations differ in their security practices and trusting tendencies.
Security Concerns Around the World | Infographic

Ping Identity’s 2019 consumer survey reveals interesting insights about where residents of the U.S., Australia, France and Germany differ from one another in their cybersecurity concerns and behavioral trends. Check out the infographic to see which country’s respondents are most concerned about surveillance, which are least likely to sign-on to their accounts through a third-party service and more.
Hybrid IAM: Fuelling Agility in the Cloud Transformation Journey | Gartner IA...

Presenter: Loren Russon, VP Product Management at Ping Identity.
As your organisation evolves on its cloud transformation journey, your identity and access management (IAM) system must allow you to navigate multiple cloud environments, managing access to mobile, API and traditional applications. Modern identity services like multi-factor authentication (MFA) and identity intelligence help deliver secure and seamless access for any user, environment and use case. Learn how to transform your IAM system to a modern, API and cloud-first hybrid solution, enabling developers, administrators and users with the self-service applications and tools they need to keep pace with the accelerating demand for mobile and cloud-based applications.
LES ATTITUDES DES CONSOMMATEURS À L’ÈRE DES CYBERATTAQUES

Les consommateurs présents aux Etats-Unis, en France, en Allemagne et au Royaume-Uni montrent des préférences de sécurité et des comportements différents. Notre étude récente révèle comment chaque pays se démarque des autres.
WIE TICKEN VERBRAUCHER IM ZEITALTER DER DATENSCHUTZVERLETZUNGEN?

Wenn es um Themen wie Sicherheitsempfinden und Sicherheitspraktiken geht, haben die jüngere und die ältere Generation schon mal recht unterschiedliche Ansichten. So stellte eine aktuelle Verbraucherumfrage Abweichungen z. B. beim Markenvertrauen, bei der Bereitschaft, in Datenschutz zu investieren und bei der Akzeptanz biometrischer Sicherheitslösungen fest.
Consumer Attitudes in a Post-breach Era: The Geographical Gap

Ping Identity’s consumer survey on security perceptions and behavior revealed significant differences between residents of the U.S., France, Germany and the UK. Some are more carefree with their information, while others have less trust in brands.
Standard Based API Security, Access Control and AI Based Attack - API Days Pa...

As APIs continue to drive digital transformation efforts in the enterprise and support innovative customer experiences, securing them has never been more important.
Principal Regional Solution Architect, Philippe Dubuc introduces how to leverage OpenID Connect, OAuth2 and new emerging standards to protect APIs at API Days Paris on 11 December, 2018. In addition, Philippe goes over how the Intelligent Ping Identity Platform can be used to protect APIs in a pro-active way and how AI can help to protect against attacks.
Learn more: http://ow.ly/2Ojm30n1rCT
ATTITUDES DES CONSOMMATEURS A L’ERE DES PIRATAGES LE CONFLIT DE GENERATIONS

Concernant les attitudes et les pratiques en matière de sécurité, la jeune et l’ancienne génération ne sont pas toujours en phase. Une récente enquête révèle des différences marquées touchant la confiance envers les marques, la volonté de payer pour la protection des données, l’adoption de la biométrie, etc.
2018 Survey: Consumer Attitudes in a Post-Breach Era - The Generational Gap

Consumers under 35 and over 55 have significant differences in the way they think about security, willingness to share personal information, investment in data protection and use of technology like biometrics. Check out the infographic to see where Ping Identity’s survey revealed the biggest differences.
WIE TICKEN VERBRAUCHER IM ZEITALTER DER DATENSCHUTZVERLETZUNGEN? ALLES EINE F...

Wenn es um Themen wie Sicherheitsempfinden und Sicherheitspraktiken geht, haben die jüngere und die ältere Generation schon mal recht unterschiedliche Ansichten. So stellte eine aktuelle Verbraucherumfrage Abweichungen z. B. beim Markenvertrauen, bei der Bereitschaft, in Datenschutz zu investieren und bei der Akzeptanz biometrischer Sicherheitslösungen fest.
API Security Needs AI Now More Than Ever

API security is increasingly difficult for enterprise security teams to tackle. APIs are spreading fast and a tempting target for cyberattacks. Learn about the challenges overwhelming security teams today that can be overcome with an intelligent API security solution. Learn more: http://ow.ly/FEtG30lNsHm
Fishing for a CIAM Platform? 11 Question to Ask Before You Buy

On the hook to select a customer IAM platform? Be sure to ask these 11 questions before you settle on a solution. Or you could get in too deep. Read the infographic to discover why enlisting IT’s help early in the selection process will ensure your CIAM platform is watertight.
Criteria for Effective Modern IAM Strategies (Gartner IAM 2018)

Presenter: Loren Russon, Ping Identity VP of Products Management and Design.
Managing digital identities and access control for users, applications and things remains one of the greatest challenges facing cloud computing today. This has led to a new cloud security service paradigm that requires your organization to reevaluate the criteria for designing and implementing identity and access management (IAM) services across data centers, and private and public cloud infrastructure. This new criteria addresses the continued transformation to the cloud, mobile and internet of things (IoT), and the increased demand for open business balanced by user data security found in initiatives such as GDPR, Open Banking and PSD2. In this session, you will learn about key requirements and design principles required for modern IAM systems, and how to effectively drive digital transformation, address user data security regulations and ensure you successfully manage your company’s transformation to the cloud.
Webinar: Three Steps to Transform Your Mobile App into a Security Factor

It’s your job to secure customer interactions with your brand. Enabling multi-factor authentication (MFA) for your customers can secure their data, even if their credentials get compromised elsewhere. You may be asking yourself, “doesn’t MFA add friction and detract from their customer experience?”
Join Pamela Dingle, Principal Technical Architect for Ping Identity, as she outlines three easy steps to transform your own mobile application into a second factor that is both secure and convenient. You will learn how to achieve transaction approvals, strong device-based mobile app authentication, and many other use cases from your own mobile app, with minimal impact on your existing authentication infrastructure.
Stay tuned for the webinar replay. To learn more, download the 'Multi-factor Authentication for Customers' white paper: http://www.bit.ly/2tusUA0
Webinar: Deep Diving Into the KuppingerCole IDaaS Leadership Compass 

While enterprises move to the cloud, they are pressured to keep security in mind without hindering user productivity with a cumbersome sign-on process. One solution that delivers both a secure and seamless experience for users with one-click access to SaaS applications is single sign-on (SSO). Many enterprises cannot simply rip and replace, so finding a solution provider that creates a hybrid environment between cloud and existing on-premise infrastructures is vital.
The 2017 KuppingerCole Leadership Compass is the industry leading recourse that deep dives into this market, rating identity-as-a-service (IDaaS) solution providers in areas like SSO cloud services for users including employees, business partners and customers.
Get the report: http://www.ow.ly/Rhht30eLbbD
Join Ping Identity’s Product Marketing Manager, Alex Babar, as he looks at the KuppingerCole Leadership Compass for IDaaS and at the capabilities they consider. He will also review Ping Identity product features focusing on core factors that led KuppingerCole to name Ping a leader in their Leadership Compass, such as outbound federation and single sign-on, authentication support, and access management.
Get the replay: http://bit.ly/2eK0I66
GDPR & Customer IAM: The Real Winners Won’t Stop At Compliance

Listen to the on-demand recorded webinar here: http://bit.ly/2synQpD.
In the recording you will learn how customer identity and access management (Customer IAM) solutions can help you meet GDPR requirements out of the box, while also providing a single, unified customer profile, and enabling secure, seamless and personalized customer experiences across all channels and applications.
Note, this is a recorded webinar which took place on 27 June, 2017. For more information on GDPR and how Ping's leading Customer IAM solution can turn a compliance challenge into an opportunity for your organization, visit www.pingidentity.com/GDPR.
Gartner IAM London 2017 Session - Security, Standards & User Experience: The ...

Ping Identity Principal Technical Architect, Pam Dingle’s slides on how organisations can meet PSD2 and Open Banking Standard requirements while delivering excellent customer experiences in today’s challenging digital business environments. Using software that’s based on the OAuth family of standards, organisations are protecting RESTful APIs, combining a critical blend of intuitive user interactions, highly scalable certification of clients and interoperability.
A Modern Identity Architecture for the Digital Enterprise: http://bit.ly/2lPNiCM
You Can't Spell Enterprise Security without MFA 

Sure, you can spell enterprise security without the letters M-F-A, but the modern digital enterprise isn't as secure without a strong multi-factor authentication (MFA) strategy. Enterprises are under attack, and credentials are a primary target. Many leading enterprises are enhancing their security and control with MFA, allowing them to move away from a high-risk, password-based security approach and to give their employees, partners, and customers a better user experience. View this slide deck for best practices for a MFA strategy.
More from Ping Identity (20)
Security Practices: The Generational Gap | Infographic

Security Practices: The Generational Gap | Infographic
Hybrid IAM: Fuelling Agility in the Cloud Transformation Journey | Gartner IA...

Hybrid IAM: Fuelling Agility in the Cloud Transformation Journey | Gartner IA...
LES ATTITUDES DES CONSOMMATEURS À L’ÈRE DES CYBERATTAQUES

LES ATTITUDES DES CONSOMMATEURS À L’ÈRE DES CYBERATTAQUES
WIE TICKEN VERBRAUCHER IM ZEITALTER DER DATENSCHUTZVERLETZUNGEN?

WIE TICKEN VERBRAUCHER IM ZEITALTER DER DATENSCHUTZVERLETZUNGEN?
Consumer Attitudes in a Post-breach Era: The Geographical Gap

Consumer Attitudes in a Post-breach Era: The Geographical Gap
Standard Based API Security, Access Control and AI Based Attack - API Days Pa...

Standard Based API Security, Access Control and AI Based Attack - API Days Pa...
ATTITUDES DES CONSOMMATEURS A L’ERE DES PIRATAGES LE CONFLIT DE GENERATIONS

ATTITUDES DES CONSOMMATEURS A L’ERE DES PIRATAGES LE CONFLIT DE GENERATIONS
2018 Survey: Consumer Attitudes in a Post-Breach Era - The Generational Gap

2018 Survey: Consumer Attitudes in a Post-Breach Era - The Generational Gap
WIE TICKEN VERBRAUCHER IM ZEITALTER DER DATENSCHUTZVERLETZUNGEN? ALLES EINE F...

WIE TICKEN VERBRAUCHER IM ZEITALTER DER DATENSCHUTZVERLETZUNGEN? ALLES EINE F...
Fishing for a CIAM Platform? 11 Question to Ask Before You Buy

Fishing for a CIAM Platform? 11 Question to Ask Before You Buy
Criteria for Effective Modern IAM Strategies (Gartner IAM 2018)

Criteria for Effective Modern IAM Strategies (Gartner IAM 2018)
Webinar: Three Steps to Transform Your Mobile App into a Security Factor

Webinar: Three Steps to Transform Your Mobile App into a Security Factor
Webinar: Deep Diving Into the KuppingerCole IDaaS Leadership Compass 

Webinar: Deep Diving Into the KuppingerCole IDaaS Leadership Compass
GDPR & Customer IAM: The Real Winners Won’t Stop At Compliance

GDPR & Customer IAM: The Real Winners Won’t Stop At Compliance
Gartner IAM London 2017 Session - Security, Standards & User Experience: The ...

Gartner IAM London 2017 Session - Security, Standards & User Experience: The ...
Recently uploaded
PHP Frameworks: I want to break free (IPC Berlin 2024)

In this presentation, we examine the challenges and limitations of relying too heavily on PHP frameworks in web development. We discuss the history of PHP and its frameworks to understand how this dependence has evolved. The focus will be on providing concrete tips and strategies to reduce reliance on these frameworks, based on real-world examples and practical considerations. The goal is to equip developers with the skills and knowledge to create more flexible and future-proof web applications. We'll explore the importance of maintaining autonomy in a rapidly changing tech landscape and how to make informed decisions in PHP development.
This talk is aimed at encouraging a more independent approach to using PHP frameworks, moving towards a more flexible and future-proof approach to PHP development.
State of ICS and IoT Cyber Threat Landscape Report 2024 preview

The IoT and OT threat landscape report has been prepared by the Threat Research Team at Sectrio using data from Sectrio, cyber threat intelligence farming facilities spread across over 85 cities around the world. In addition, Sectrio also runs AI-based advanced threat and payload engagement facilities that serve as sinks to attract and engage sophisticated threat actors, and newer malware including new variants and latent threats that are at an earlier stage of development.
The latest edition of the OT/ICS and IoT security Threat Landscape Report 2024 also covers:
State of global ICS asset and network exposure
Sectoral targets and attacks as well as the cost of ransom
Global APT activity, AI usage, actor and tactic profiles, and implications
Rise in volumes of AI-powered cyberattacks
Major cyber events in 2024
Malware and malicious payload trends
Cyberattack types and targets
Vulnerability exploit attempts on CVEs
Attacks on counties – USA
Expansion of bot farms – how, where, and why
In-depth analysis of the cyber threat landscape across North America, South America, Europe, APAC, and the Middle East
Why are attacks on smart factories rising?
Cyber risk predictions
Axis of attacks – Europe
Systemic attacks in the Middle East
Download the full report from here:
https://sectrio.com/resources/ot-threat-landscape-reports/sectrio-releases-ot-ics-and-iot-security-threat-landscape-report-2024/
GraphSummit Singapore | Graphing Success: Revolutionising Organisational Stru...

Sudheer Mechineni, Head of Application Frameworks, Standard Chartered Bank
Discover how Standard Chartered Bank harnessed the power of Neo4j to transform complex data access challenges into a dynamic, scalable graph database solution. This keynote will cover their journey from initial adoption to deploying a fully automated, enterprise-grade causal cluster, highlighting key strategies for modelling organisational changes and ensuring robust disaster recovery. Learn how these innovations have not only enhanced Standard Chartered Bank’s data infrastructure but also positioned them as pioneers in the banking sector’s adoption of graph technology.
Communications Mining Series - Zero to Hero - Session 1

This session provides introduction to UiPath Communication Mining, importance and platform overview. You will acquire a good understand of the phases in Communication Mining as we go over the platform with you. Topics covered:
• Communication Mining Overview
• Why is it important?
• How can it help today’s business and the benefits
• Phases in Communication Mining
• Demo on Platform overview
• Q/A
UiPath Test Automation using UiPath Test Suite series, part 5

Welcome to UiPath Test Automation using UiPath Test Suite series part 5. In this session, we will cover CI/CD with devops.
Topics covered:
CI/CD with in UiPath
End-to-end overview of CI/CD pipeline with Azure devops
Speaker:
Lyndsey Byblow, Test Suite Sales Engineer @ UiPath, Inc.
Transcript: Selling digital books in 2024: Insights from industry leaders - T...

The publishing industry has been selling digital audiobooks and ebooks for over a decade and has found its groove. What’s changed? What has stayed the same? Where do we go from here? Join a group of leading sales peers from across the industry for a conversation about the lessons learned since the popularization of digital books, best practices, digital book supply chain management, and more.
Link to video recording: https://bnctechforum.ca/sessions/selling-digital-books-in-2024-insights-from-industry-leaders/
Presented by BookNet Canada on May 28, 2024, with support from the Department of Canadian Heritage.
A tale of scale & speed: How the US Navy is enabling software delivery from l...

Rapid and secure feature delivery is a goal across every application team and every branch of the DoD. The Navy’s DevSecOps platform, Party Barge, has achieved:
- Reduction in onboarding time from 5 weeks to 1 day
- Improved developer experience and productivity through actionable findings and reduction of false positives
- Maintenance of superior security standards and inherent policy enforcement with Authorization to Operate (ATO)
Development teams can ship efficiently and ensure applications are cyber ready for Navy Authorizing Officials (AOs). In this webinar, Sigma Defense and Anchore will give attendees a look behind the scenes and demo secure pipeline automation and security artifacts that speed up application ATO and time to production.
We will cover:
- How to remove silos in DevSecOps
- How to build efficient development pipeline roles and component templates
- How to deliver security artifacts that matter for ATO’s (SBOMs, vulnerability reports, and policy evidence)
- How to streamline operations with automated policy checks on container images
Alt. GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using ...

Effective Application Security in Software Delivery lifecycle using Deployment Firewall and DBOM
The modern software delivery process (or the CI/CD process) includes many tools, distributed teams, open-source code, and cloud platforms. Constant focus on speed to release software to market, along with the traditional slow and manual security checks has caused gaps in continuous security as an important piece in the software supply chain. Today organizations feel more susceptible to external and internal cyber threats due to the vast attack surface in their applications supply chain and the lack of end-to-end governance and risk management.
The software team must secure its software delivery process to avoid vulnerability and security breaches. This needs to be achieved with existing tool chains and without extensive rework of the delivery processes. This talk will present strategies and techniques for providing visibility into the true risk of the existing vulnerabilities, preventing the introduction of security issues in the software, resolving vulnerabilities in production environments quickly, and capturing the deployment bill of materials (DBOM).
Speakers:
Bob Boule
Robert Boule is a technology enthusiast with PASSION for technology and making things work along with a knack for helping others understand how things work. He comes with around 20 years of solution engineering experience in application security, software continuous delivery, and SaaS platforms. He is known for his dynamic presentations in CI/CD and application security integrated in software delivery lifecycle.
Gopinath Rebala
Gopinath Rebala is the CTO of OpsMx, where he has overall responsibility for the machine learning and data processing architectures for Secure Software Delivery. Gopi also has a strong connection with our customers, leading design and architecture for strategic implementations. Gopi is a frequent speaker and well-known leader in continuous delivery and integrating security into software delivery.
GraphRAG is All You need? LLM & Knowledge Graph

Guy Korland, CEO and Co-founder of FalkorDB, will review two articles on the integration of language models with knowledge graphs.
1. Unifying Large Language Models and Knowledge Graphs: A Roadmap.
https://arxiv.org/abs/2306.08302
2. Microsoft Research's GraphRAG paper and a review paper on various uses of knowledge graphs:
https://www.microsoft.com/en-us/research/blog/graphrag-unlocking-llm-discovery-on-narrative-private-data/
UiPath Test Automation using UiPath Test Suite series, part 4

Welcome to UiPath Test Automation using UiPath Test Suite series part 4. In this session, we will cover Test Manager overview along with SAP heatmap.
The UiPath Test Manager overview with SAP heatmap webinar offers a concise yet comprehensive exploration of the role of a Test Manager within SAP environments, coupled with the utilization of heatmaps for effective testing strategies.
Participants will gain insights into the responsibilities, challenges, and best practices associated with test management in SAP projects. Additionally, the webinar delves into the significance of heatmaps as a visual aid for identifying testing priorities, areas of risk, and resource allocation within SAP landscapes. Through this session, attendees can expect to enhance their understanding of test management principles while learning practical approaches to optimize testing processes in SAP environments using heatmap visualization techniques
What will you get from this session?
1. Insights into SAP testing best practices
2. Heatmap utilization for testing
3. Optimization of testing processes
4. Demo
Topics covered:
Execution from the test manager
Orchestrator execution result
Defect reporting
SAP heatmap example with demo
Speaker:
Deepak Rai, Automation Practice Lead, Boundaryless Group and UiPath MVP
GraphSummit Singapore | The Art of the Possible with Graph - Q2 2024

Neha Bajwa, Vice President of Product Marketing, Neo4j
Join us as we explore breakthrough innovations enabled by interconnected data and AI. Discover firsthand how organizations use relationships in data to uncover contextual insights and solve our most pressing challenges – from optimizing supply chains, detecting fraud, and improving customer experiences to accelerating drug discoveries.
The Art of the Pitch: WordPress Relationships and Sales

Clients don’t know what they don’t know. What web solutions are right for them? How does WordPress come into the picture? How do you make sure you understand scope and timeline? What do you do if sometime changes?
All these questions and more will be explored as we talk about matching clients’ needs with what your agency offers without pulling teeth or pulling your hair out. Practical tips, and strategies for successful relationship building that leads to closing the deal.
Video Streaming: Then, Now, and in the Future

In his public lecture, Christian Timmerer provides insights into the fascinating history of video streaming, starting from its humble beginnings before YouTube to the groundbreaking technologies that now dominate platforms like Netflix and ORF ON. Timmerer also presents provocative contributions of his own that have significantly influenced the industry. He concludes by looking at future challenges and invites the audience to join in a discussion.
Removing Uninteresting Bytes in Software Fuzzing

Imagine a world where software fuzzing, the process of mutating bytes in test seeds to uncover hidden and erroneous program behaviors, becomes faster and more effective. A lot depends on the initial seeds, which can significantly dictate the trajectory of a fuzzing campaign, particularly in terms of how long it takes to uncover interesting behaviour in your code. We introduce DIAR, a technique designed to speedup fuzzing campaigns by pinpointing and eliminating those uninteresting bytes in the seeds. Picture this: instead of wasting valuable resources on meaningless mutations in large, bloated seeds, DIAR removes the unnecessary bytes, streamlining the entire process.
In this work, we equipped AFL, a popular fuzzer, with DIAR and examined two critical Linux libraries -- Libxml's xmllint, a tool for parsing xml documents, and Binutil's readelf, an essential debugging and security analysis command-line tool used to display detailed information about ELF (Executable and Linkable Format). Our preliminary results show that AFL+DIAR does not only discover new paths more quickly but also achieves higher coverage overall. This work thus showcases how starting with lean and optimized seeds can lead to faster, more comprehensive fuzzing campaigns -- and DIAR helps you find such seeds.
- These are slides of the talk given at IEEE International Conference on Software Testing Verification and Validation Workshop, ICSTW 2022.
Recently uploaded (20)
PHP Frameworks: I want to break free (IPC Berlin 2024)

PHP Frameworks: I want to break free (IPC Berlin 2024)
State of ICS and IoT Cyber Threat Landscape Report 2024 preview

State of ICS and IoT Cyber Threat Landscape Report 2024 preview
GraphSummit Singapore | Graphing Success: Revolutionising Organisational Stru...

GraphSummit Singapore | Graphing Success: Revolutionising Organisational Stru...
Communications Mining Series - Zero to Hero - Session 1

Communications Mining Series - Zero to Hero - Session 1
FIDO Alliance Osaka Seminar: Passkeys at Amazon.pdf

FIDO Alliance Osaka Seminar: Passkeys at Amazon.pdf
UiPath Test Automation using UiPath Test Suite series, part 5

UiPath Test Automation using UiPath Test Suite series, part 5
FIDO Alliance Osaka Seminar: Passkeys and the Road Ahead.pdf

FIDO Alliance Osaka Seminar: Passkeys and the Road Ahead.pdf
Transcript: Selling digital books in 2024: Insights from industry leaders - T...

Transcript: Selling digital books in 2024: Insights from industry leaders - T...
A tale of scale & speed: How the US Navy is enabling software delivery from l...

A tale of scale & speed: How the US Navy is enabling software delivery from l...
FIDO Alliance Osaka Seminar: FIDO Security Aspects.pdf

FIDO Alliance Osaka Seminar: FIDO Security Aspects.pdf
Alt. GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using ...

Alt. GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using ...
UiPath Test Automation using UiPath Test Suite series, part 4

UiPath Test Automation using UiPath Test Suite series, part 4
GraphSummit Singapore | The Art of the Possible with Graph - Q2 2024

GraphSummit Singapore | The Art of the Possible with Graph - Q2 2024
The Art of the Pitch: WordPress Relationships and Sales

The Art of the Pitch: WordPress Relationships and Sales
