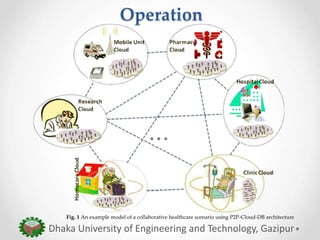
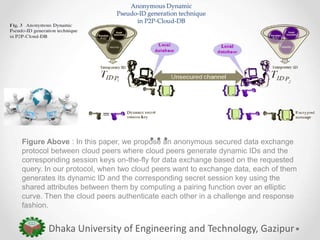
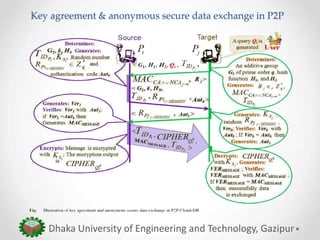
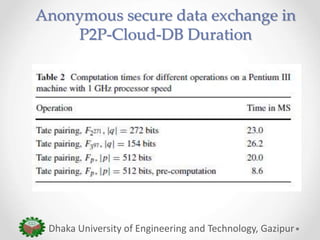
The paper proposes an anonymous and secure data exchange protocol for sharing medical data between organizations in a peer-to-peer cloud healthcare environment. The protocol allows cloud peers to dynamically generate temporary identities and session keys for each data exchange session. It is robust against various attacks such as man-in-the-middle, masquerade, and message manipulation attacks. The protocol aims to enable inter-organizational medical data sharing at scale while preserving privacy in an insecure network environment.