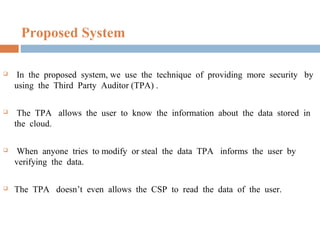
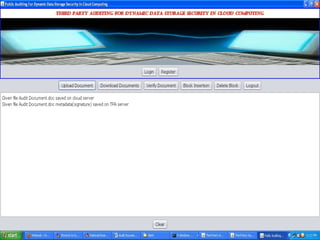
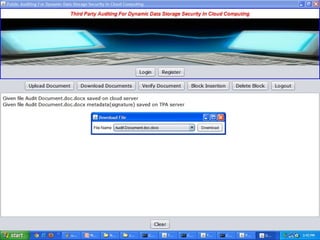
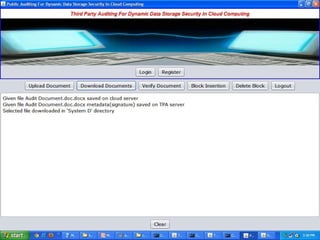
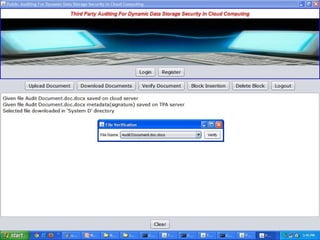
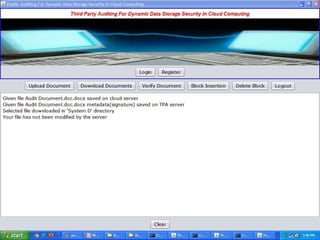
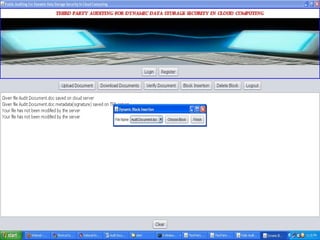
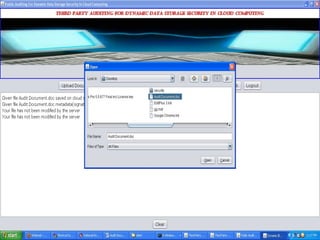
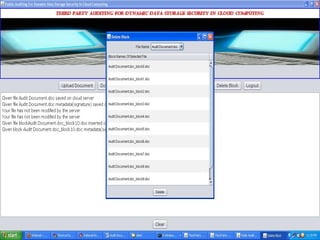
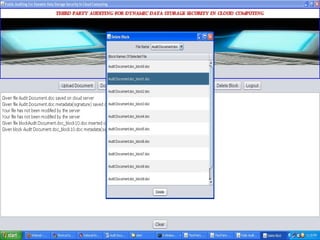
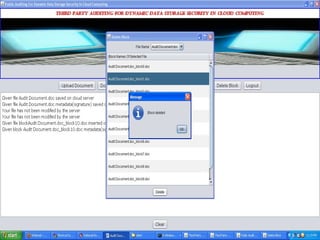
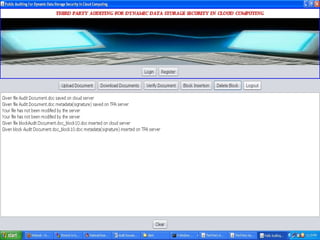
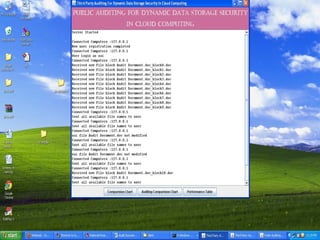
The document discusses a proposed system for enhancing data storage security in cloud computing through a Third Party Auditor (TPA) that enables public auditability. It highlights the existing system's vulnerabilities and the need for independent verification of data integrity. The conclusion emphasizes the importance of a TPA in ensuring service quality and the challenge of developing verification protocols for dynamic data files.