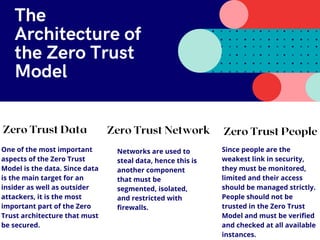
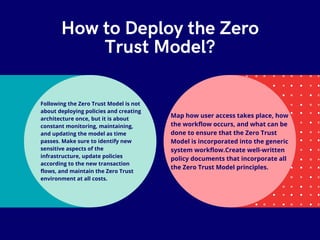
The zero trust model emphasizes that trust should never be assumed, requiring verified authentication and access restrictions to organizational resources. It focuses on limiting user access, logging all activities, and securing data, networks, and people to prevent unauthorized access. Continuous monitoring and policy updates are essential for maintaining the zero trust environment.