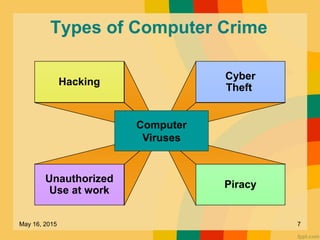
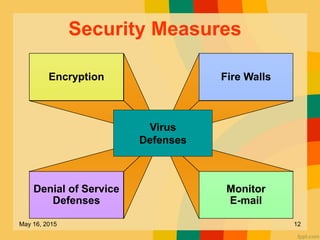
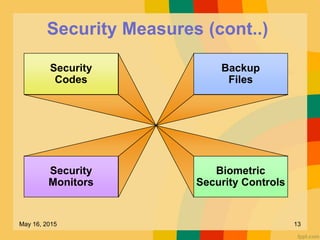
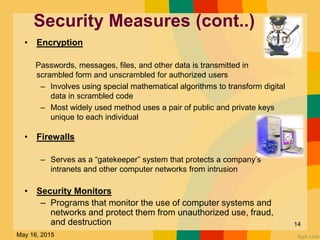
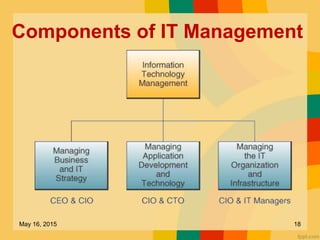
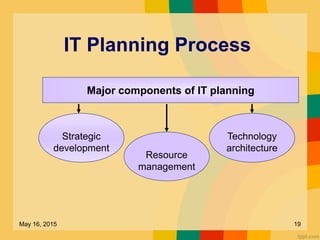
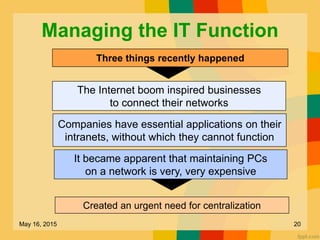
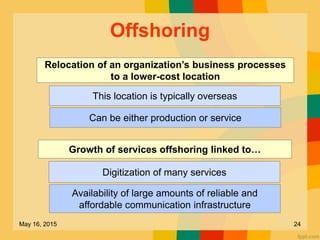
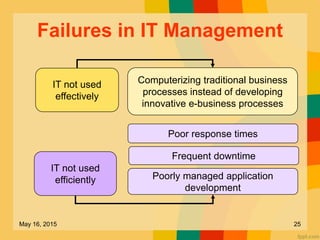
This document discusses several key issues related to information technology including computer crime, privacy concerns, challenges for employment, and security measures. It addresses types of computer crime such as hacking, cyber theft, and software piracy. Privacy issues focus on loss of control of information, risks to physical privacy, and lack of privacy protection online and in electronic communications. Employment challenges include potential job losses, computer monitoring, loss of individuality, and health issues from extensive computer use. The document also outlines various security measures used to enhance cybersecurity such as encryption, firewalls, virus defenses, security monitoring, and biometric authentication.